Error 65005 - The application required resource access list does not contain applications discoverable by the resource or The client application has requested access to resource, which was not specified in its required resource access list or Graph service returned bad request or resource not found.
About Azure Activity sign-in activity reports:
Azure Active Directory's (renamed as Entra ID) reporting tool generates 'Sign-in activity' reports that give you insights on who has performed the tasks that are enlisted in the Audit logs.
- All Sign-in activity reports can be found under the Activity section of Azure Active Directory.
- The default list view of Audit logs can be customized by adding additional fields.
- The reports can also be filtered to let you view only the activities that are relevant.
- Here is an example of how a sign-in activity report looks like:
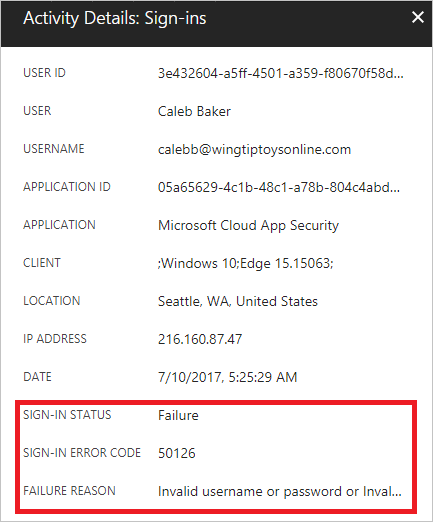
Error description:
Cause 1:The resource access list required for the application does not contain any application that is discoverable by the resource.
Cause 2:The client application has requested access to resource, which was not specified in its required resource access list.
Cause 3:The graph service returned bad request or resource was not found.
Cause 4:If the application supports SAML, you may have configured the application with the wrong Identifier (Entity).
Steps to add a Identifier value :
- Open the Azure portal and sign in as a Global Administrator or Co-admin.
- Open the Azure Active Directory Extension by clicking All services at the top of the main left-hand navigation menu.
- Type in “Azure Active Directory” in the filter search box and select the Azure Active Directory item.
- Click Enterprise Applications from the Azure Active Directory left-hand navigation menu.
- Click all applications to view a list of all your applications. If you do not see the application you want show up here, use the Filter control at the top of the All Applications List and set the Show option to All Applications.
- Select the application you have configured single sign-on.
- Once the application loads, click on the Single sign-on from the application’s left-hand navigation menu.
- Under the Domain and URL section, check on the Show advanced URL settings.
- In the Identifier textbox type a unique identifier for the application.
- Save the configuration.
Auditing Azure AD environments with ADAudit Plus:
ADAudit Plus offers change monitoring for your Azure AD environment with the following features:
- Correlated view across hybrid environments
- Real-time alerts
- Schedulable reports
- Autonomous change remediation
- Comprehensive search
- Out-of-the-box compliance reports
Explore Active Directory auditing and reporting with ADAudit Plus.
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- EventLog Analyzer Real-time Log Analysis & Reporting
- ADSelfService Plus Self-Service Password Management
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
