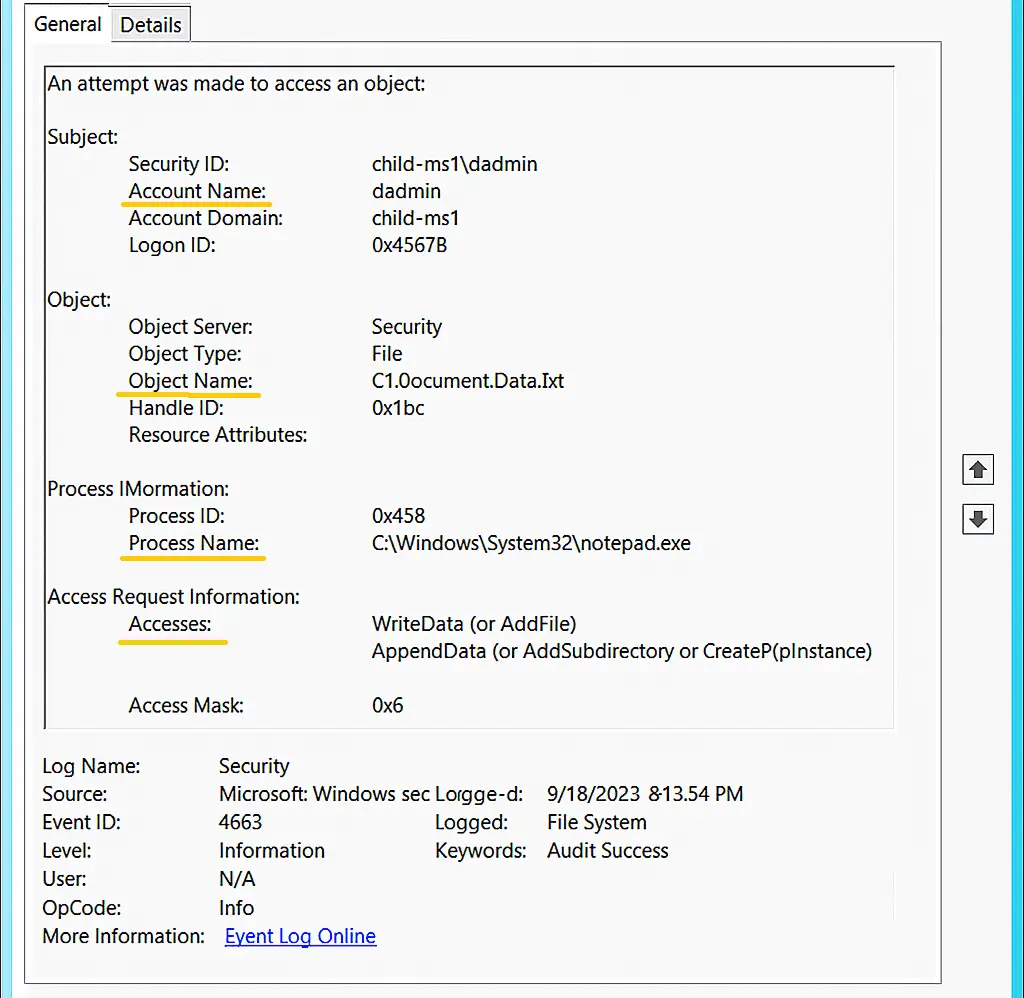
Every time a user tries to access or change a file or folder, Event ID 4663 is generated. It records details such as the user name, file path, access type, and process name.
In Active Directory (AD) environments, unauthorized or unplanned file changes can pose significant security and compliance risks. Administrators must be able to determine who made the change, when it occurred, and where fromwhether it was a malicious actor or an accidental alteration of a critical file.
This page explains how to use native Windows Event Viewer, which logs file modification activities under event ID 4663 and ManageEngine ADAudit Plus, which automatically gathers and reports file access and modification events across your servers to effectively determine who changed a file or folder in Windows.
Why tracking file modifications matters:
- Detect unauthorized or accidental changes to sensitive data.
- Investigate potential insider threats or policy violations.
- Meet compliance requirements such as SOX, HIPAA, and GDPR by maintaining detailed access audit trails.
- Native auditing
- ADAudit Plus
Steps to enable file modification auditing using Group Policy:
- Open the Group Policy Management Console (GPMC) or run the command gpmc.msc.
- If you want to audit all the accounts in the domain, right-click the domain name and click Create a GPO in this domain, and Link it here. If you want to audit accounts in a specific organizational unit (OU), right-click the OU and click Create a GPO in this domain, and Link it here.
- Provide a relevant name for the GPO, right-click it, choose Edit, and navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Object Access > Audit File System. In the Audit File System Properties window,
select the Success and Failure checkboxes, and click OK.
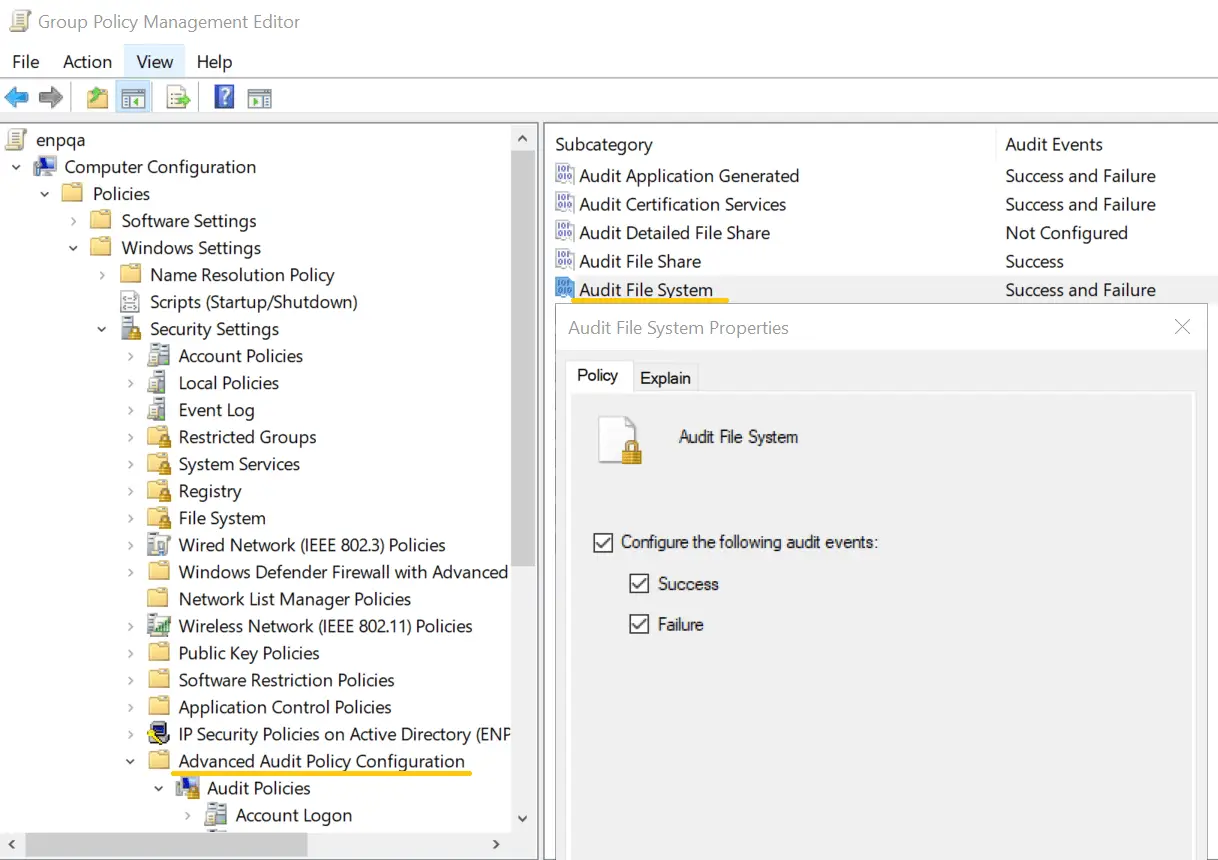
- Go back to the GPMC, right-click the OU or domain in which the GPO was linked, and click Group Policy Update. This step makes sure the new Group Policy settings are applied instantly instead of waiting for the next scheduled refresh.
Steps to configure object-level auditing on a specific file or folder:
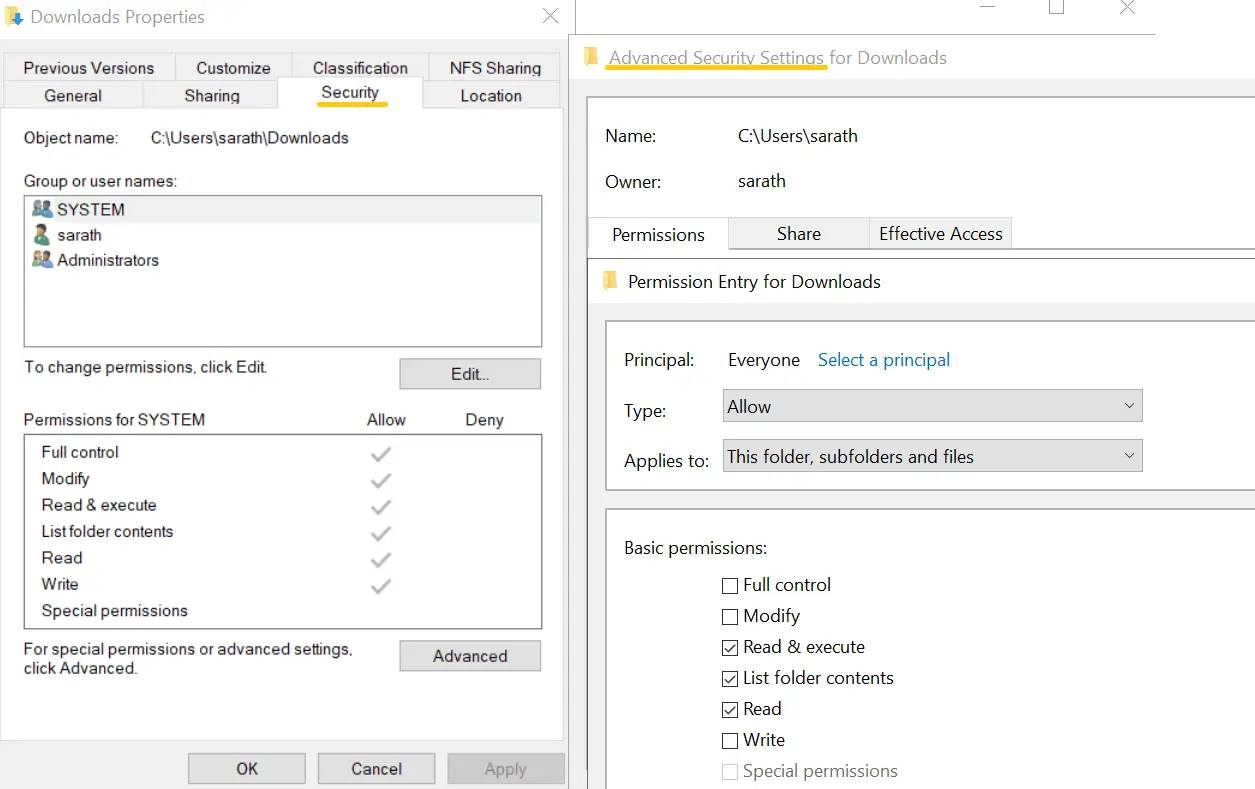
- Right-click the file or folder you want to audit, and select Properties.
- Navigate to Security > Advanced > Auditing.
Click Add, select Principal as Everyone, and choose the actions you want to audit such as Create files, Write attributes, Delete, etc.
Click OK to save the changes.Click OK to save the changes.
Once the above steps are complete, file and folder access attempts (including modifications) will be recorded as event logs.
Steps to see who modified a file in Windows Event Viewer:
- Open the Event Viewer. On the left pane, navigate to Windows log > Security.
- On the right pane, navigate to Security > Filter current log.
- In the pop-up window, enter the 4663 in the field labeled <All Event IDs>. This will provide you with a list of occurrences of Event ID 4663. Double-click the Event ID to view its properties.
Important information that can be derived from Event ID 4663 includes:
- Account Name: The user who accessed or modified the file.
- Object Name: The full path of the file or folder.
- Accesses: The type of access, or action the user tried to perform on the file or folder.
- Process Name: The program that performed the modification.
5 file access types you’ll see most, explained in simple terms:
| Access type | Explanation | Example |
|---|---|---|
| ReadData | Someone opened or read the file’s contents. | A user opened a text document. |
| WriteData | Someone changed or overwrote the file’s contents. | A user saved edits to a Word or Excel file. |
| AppendData | Someone added new data to the end of the file without replacing existing content. | A program added new lines to a log file. |
| ReadAttributes | Someone checked the file’s basic info, like its size or modified date. | File Explorer displayed the file’s details. |
| WriteAttributes | Someone changed file properties such as the timestamp. | A script modified the “last modified” date. |
Steps to see who modified a file or folder in Windows:
- Ensure Audit File System audit policy is enabled via GPO.
- Download and install ADAudit Plus.
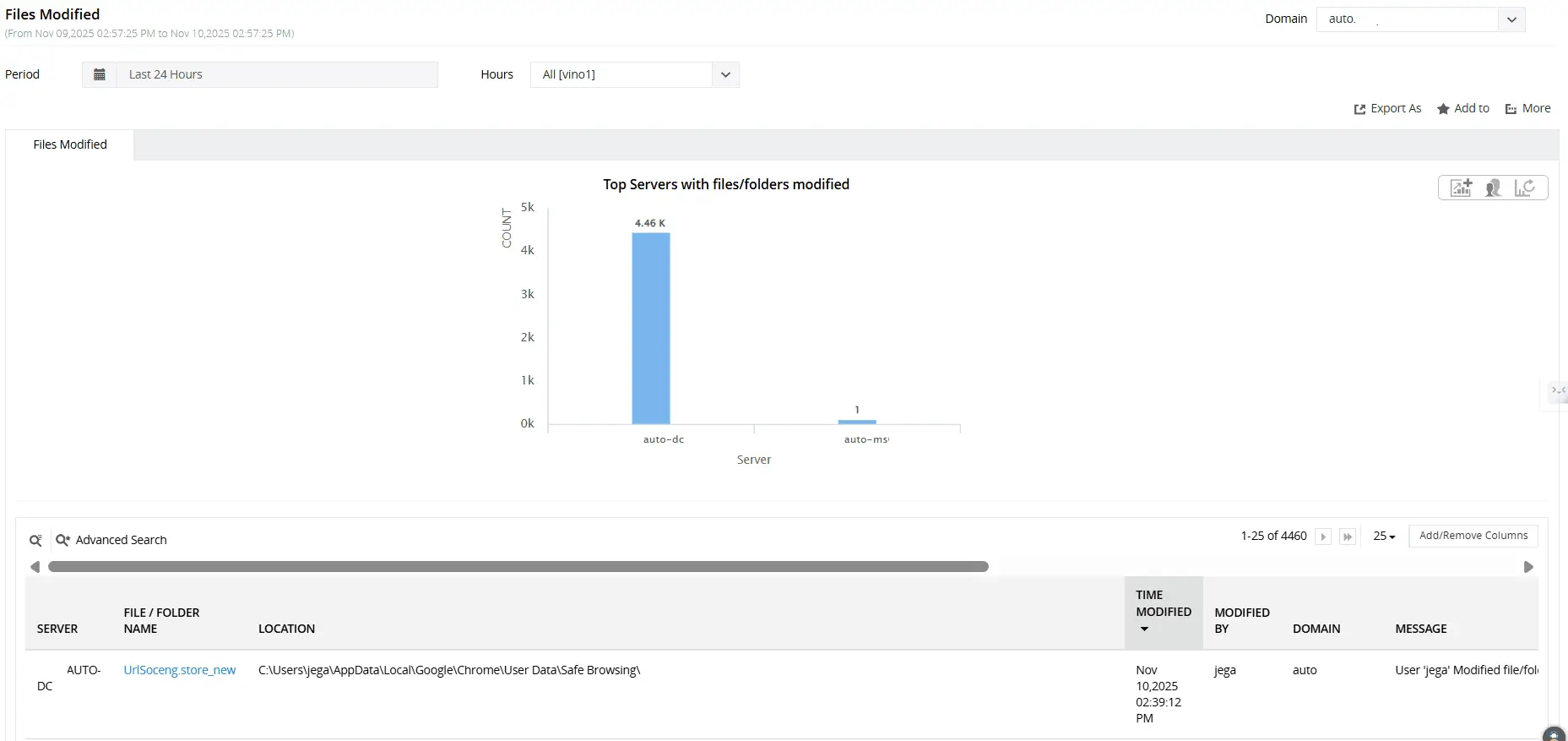
- Log in to ADAudit Plus, navigate to File Audit > File Auditing > File Audit Reports > Files modified.
Select the Domain and Period. Filter the report by Server, File or Folder Name, Modified by, or Client Machine Name to quickly see who modified a file or folder.
Bridging the gaps in native auditing with ADAudit Plus
Native Windows auditing is time-consuming, requires expertise, and lacks some capabilities—making third-party tools like ADAudit Plus essential. ADAudit Plus helps with:
- Centralized auditing: Collects logs from all computers without the complexity of Windows Event Forwarding.
- Threat mitigation: Detects suspicious patterns such as an unusual volume of file modifications using correlation and machine learning, unlike Task Scheduler's limited event alerts.
- Compliance reporting: Consolidates fragmented event data into a complete audit trail and helps meet compliance requirements.
For more information on how ADAudit Plus helps organizations overcome the limitations of native Windows auditing tools, check out this e-book.
A one-stop solution for all your IT auditing, compliance, and security needs
ADAudit Plus provides capabilities like change auditing, logon monitoring, file tracking, compliance reporting, attack surface analysis, response automation, and backup and recovery for diverse IT systems.
FAQ
Yes. File activity across various NAS file servers, including Windows, NetApp, EMC, Synology, Hitachi, Huawei, Amazon FSx, QNAP, Azure, CTERA, Nutanix and more, can be tracked with ADAudit Plus.
For the full list of different NAS file servers that ADAudit Plus helps audit, their supported versions, and the activities audited on them, check out this page.
Experience
ADAudit Plus for free
With ADAudit Plus, you can:
- Get full visibility into file changes
- Audit multi-vendor NAS file servers
- Detect anomalous file activities
- Generate file audit trails
- And much more