How to enable file and folder access auditing in Windows Server
Get it Done with ADAudit PlusNative auditing
Enable auditing at the server level
- Start → Administrative tools → Local security policy snap-in.
- Expand Local policy → Audit policy.
- Go to Audit object access.
- Select Success/Failure (as needed).
- Confirm your selections, and click OK.
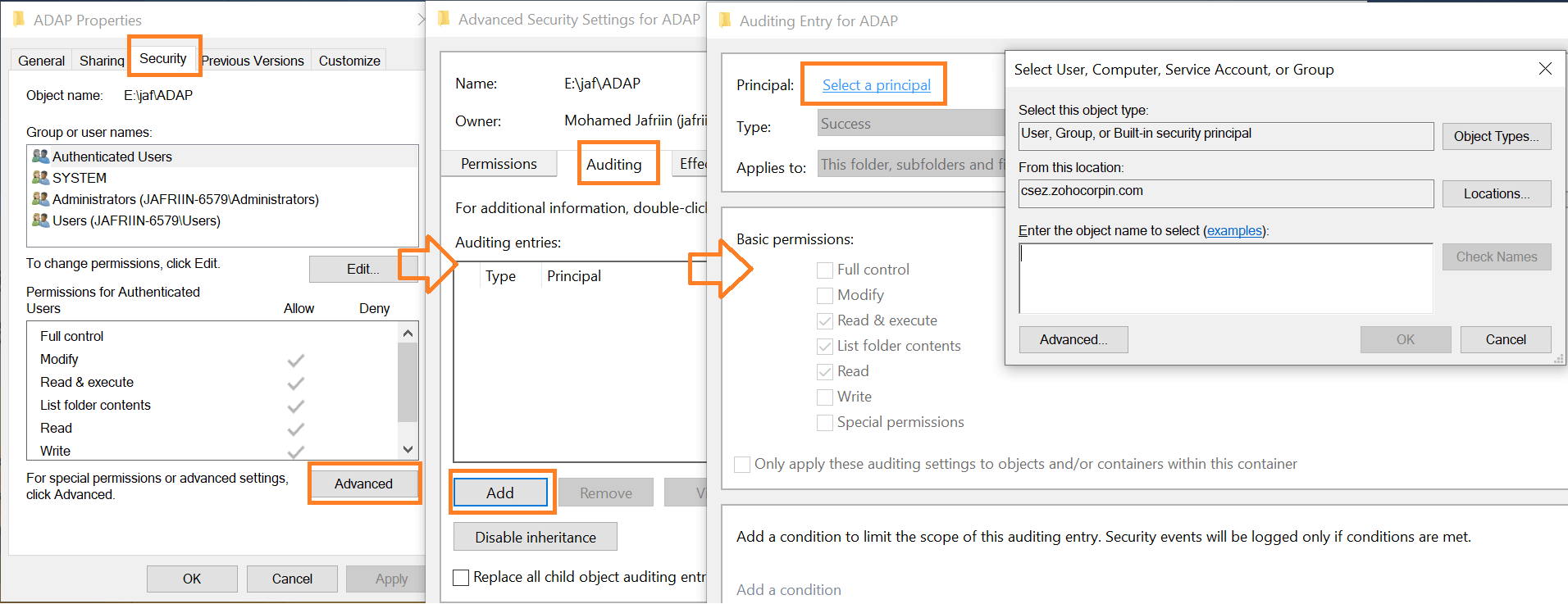
Enable auditing at the object level
- Navigate Windows Explorer to the file you want to monitor.
- Right-click on the target folder/file, and select Properties.
- Security → Advanced.
- Select the Auditing tab.
- Click Add.
- Select the Principal you want to give audit permissions to.
- In the Auditing Entry dialog box, select the types of access you want to audit.
- You have to select the options to audit successful and failed events separately.
- Click OK when you're done.
Auditing file and folder access with ADAudit Plus
Native tools require you to filter out file/folder access events from the clutter of logs in the Event Viewer or run Powershell scripts to do the same. Due to limited storage, the logs you require may also be rewritten.
During an investigation or for compliance audits, getting a clear picture of who accessed a file/folder is cumbersome using native tools. ADAudit Plus lets you pull up complete access trails of any file/folder with a single click. Real-time reports to monitor all attempts to access files or folders in your file servers are provided. These reports can be archived and saved anywhere locally, so you don't need to worry about limitations in storage like with native tools. This way, logs from past events can be stored for as long as needed to be used for forensics and compliance.
Log in to ADAudit Plus, and go to the File Audit tab. Under File Audit Reports, navigate to the File Read Access report.
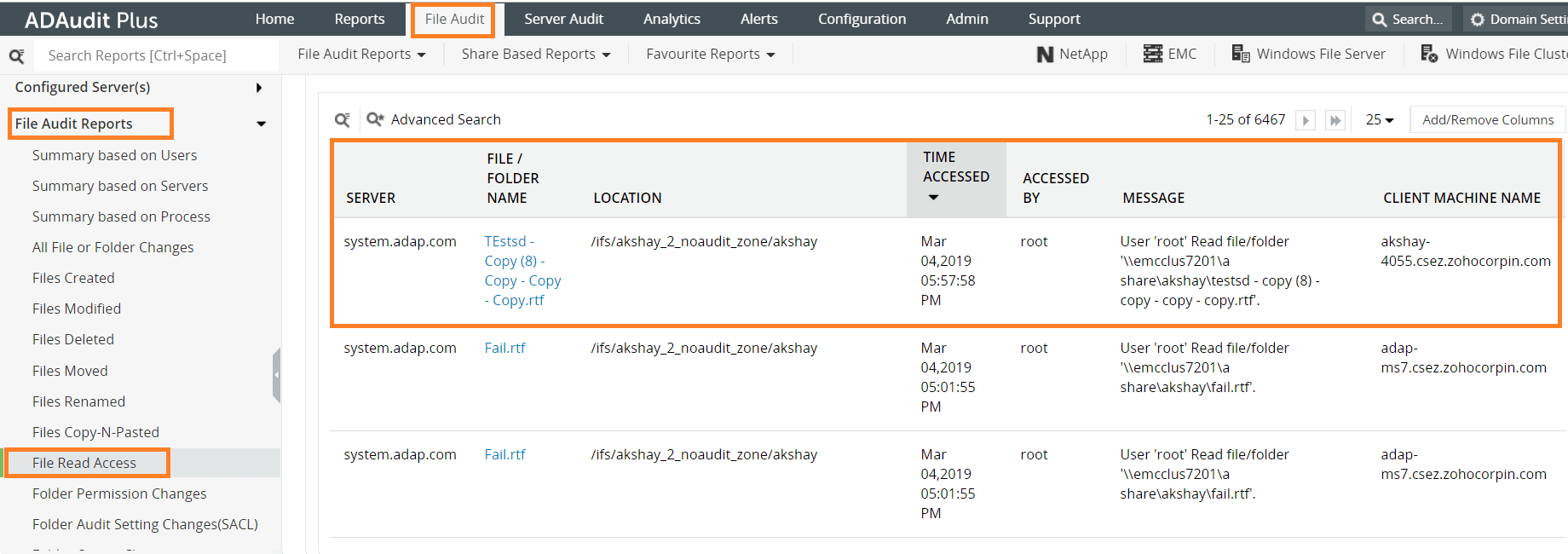
The details you can obtain from this report are:
- Which file was accessed
- Who accessed the file
- When the file was accessed
- Which client machine was used to access the file
- The name of the server in which the file is located
You can also pull up the failed attempts to read, write, or delete a file. The reports contain the following details:
- The name of the file
- The name of the user whose request had failed
- The time at which the request was made
- The name of the server in which the file is located
You can configure these reports to be automatically generated and emailed to you at specified intervals. Instant alerts can also be sent to your email/phone when critical files/folders are accessed. These reports can be exported as a CSV, PDF, XLS, or HTML file.
With a record of all attempts made to access a file (including the failed ones), investigations in case of a data breach become much easier. You can track down all the users who accessed a file in order to rule out possible suspects. It can also help in identifying the client machine from which failed attempts were made, which can indicate a compromised system.
Native auditing becoming a little too much?
Simplify file server auditing and reporting with ADAudit Plus.
Download for Free