How to monitor activities performed on a computer?
Written by Mahidhar Adarsh, IT security team, ManageEngine Updated on June 2025
When anything goes wrong on a computer, the first question is "who did it, and when". Microsoft understands this and provides a powerful event logging and auditing tool to answer this question. Use it wisely to track every action performed on a computer.
Configure your audit policy:
- Logon to your computer as an administrator.
- Run → gpedit.msc
- Computer configuration → Windows Settings → Security Settings → Local Policies → Audit Policies.
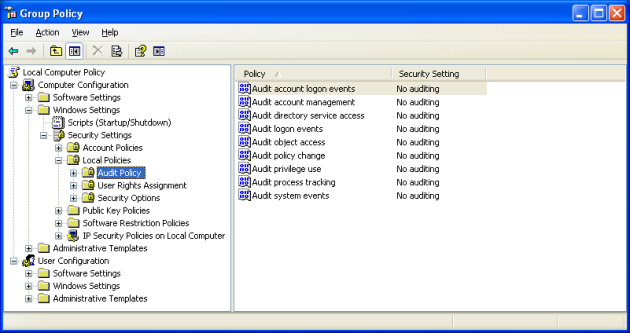
- Open each of these policies and select the Success and Failure checkboxes to ensure every single action and event is audited.
Track every user's activity:
If there's any particularly sensitive file or folder that you want to protect, configure the security settings such that every user's action on that object is logged.
Open the object's properties → Security tab → click Advanced → Auditing and add Everyone to the list, then select both Delete checkboxes. This is to make sure nobody tampers with this object and erases all trace of it.
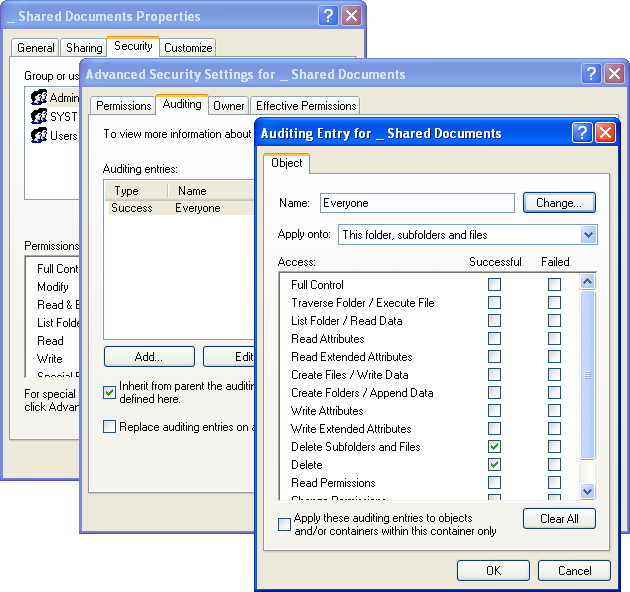
Keep an eye on the event logs:
If there ever comes a time where you have to trace back to the source of a problem, just turn to the event logs.
- Run → eventvwr.msc
- Open Security event log.
- Right-click event log and select the View → Filtercommand.
- Watch through the filtered event list taking into account the following information fields inside each record:
- Object Name. The name of missing file or folder.
- Image File Name. The name of executable which was used to delete the object in question.
- Accesses. A set of accessed privileges.
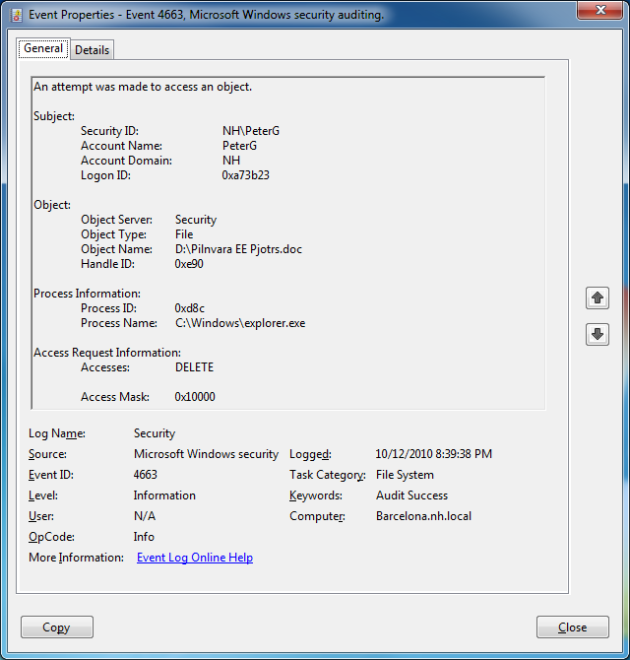
Now you can see every action performed on an object, who did it, and when they did it.
With the above policies configured, every activity performed on a computer can be recorded and monitored.
Explore Active Directory auditing and reporting with ADAudit Plus.
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- EventLog Analyzer Real-time Log Analysis & Reporting
- ADSelfService Plus Self-Service Password Management
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
