-
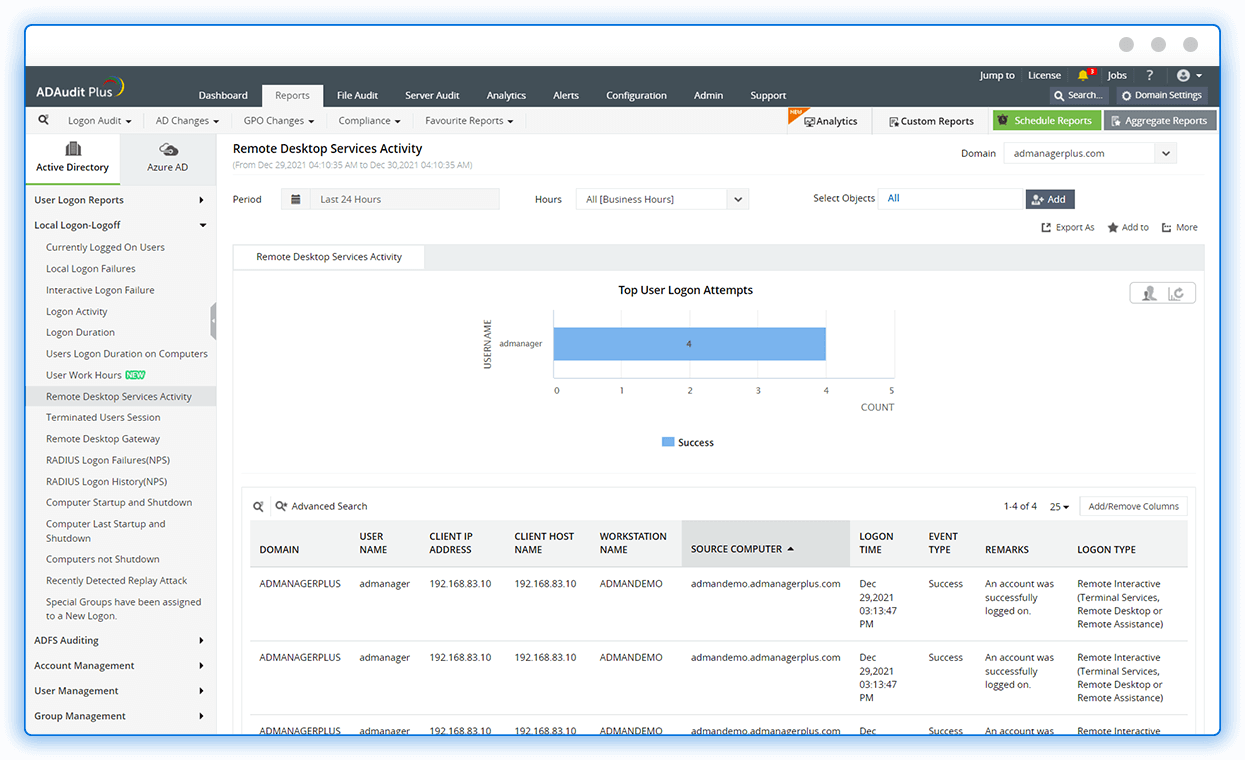
Investigate failed logons
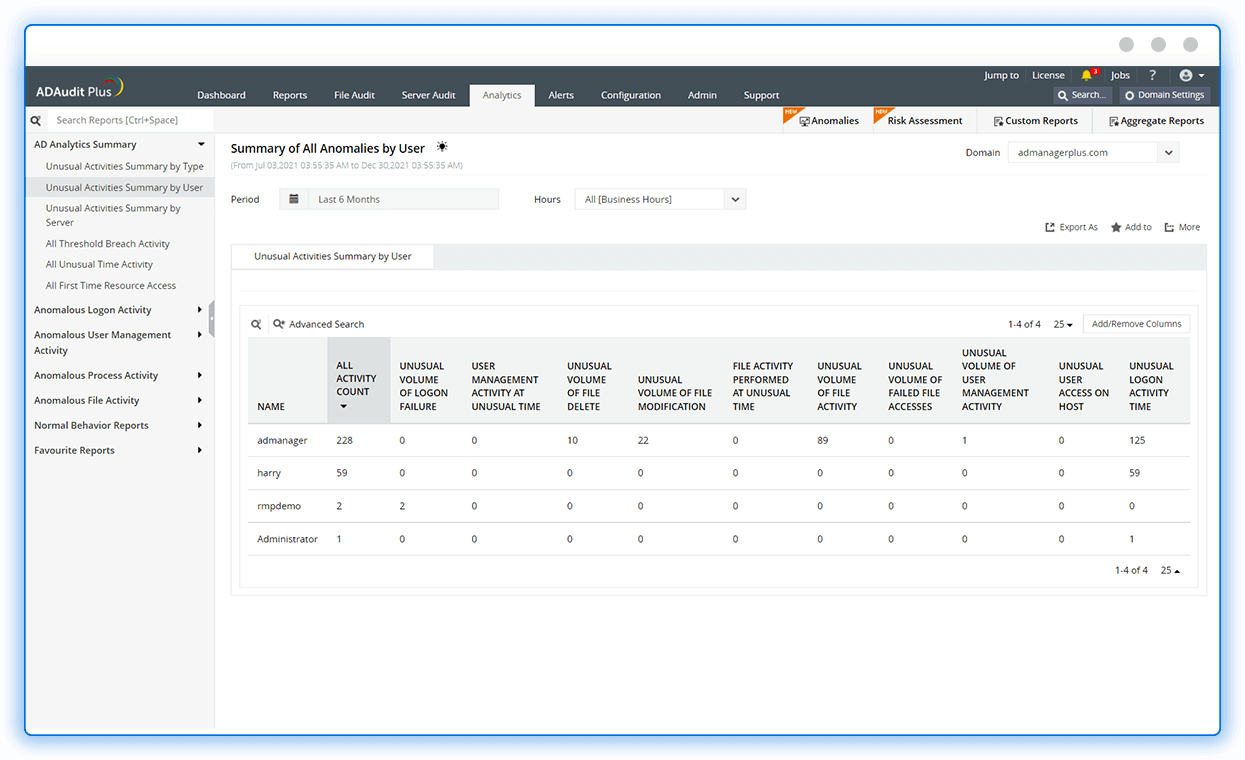
Detect abnormal logon activities, identify the source of logon failures, and find user accounts with excessive account lockouts.
-
Track privileged user actions
Audit privilege use and investigate critical events like unauthorized user management, password resets, and privilege escalations.
-
Detect suspicious file activity
Track unusual file activities such as multiple failed attempts to access critical files, unwarranted file modifications, and excessive file deletions.
-
Actively respond to threats
Get real-time alerts when anomalies are detected and instantly execute automated threat responses to security incidents.
Subdue insider threats in your AD using our insider threat detection software.