-
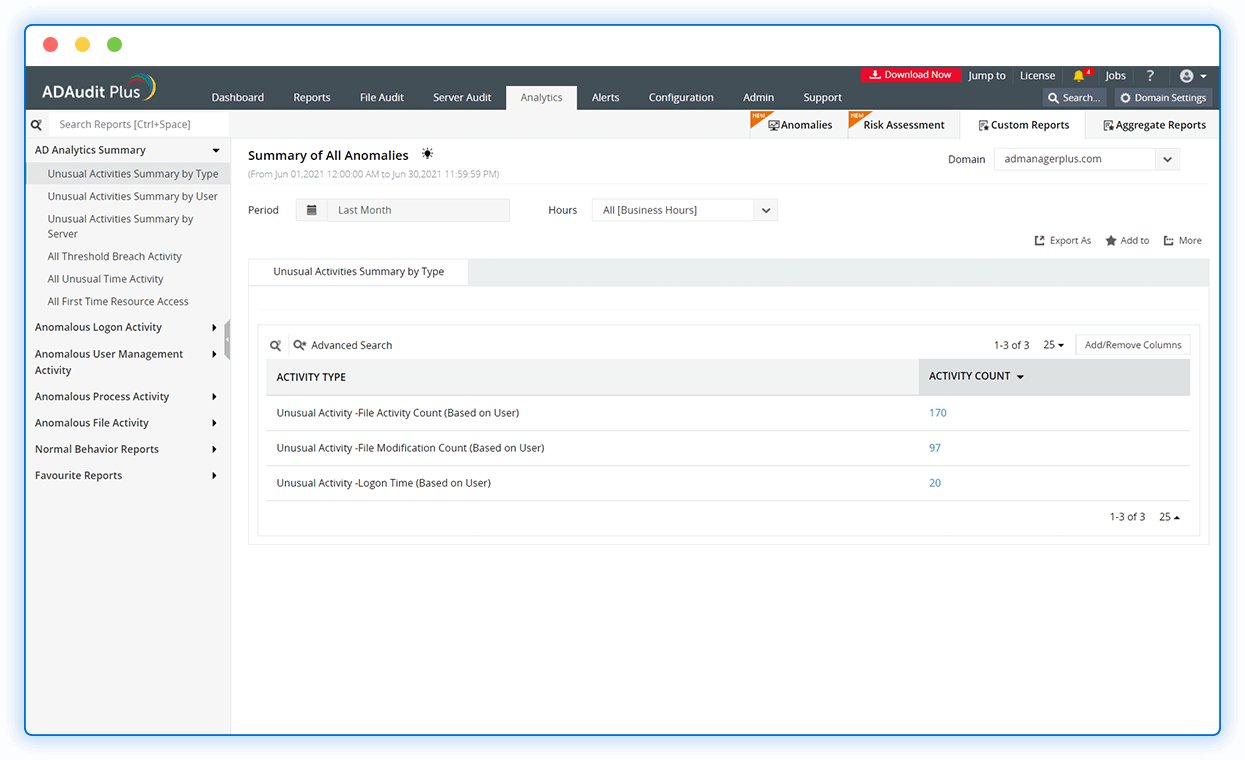
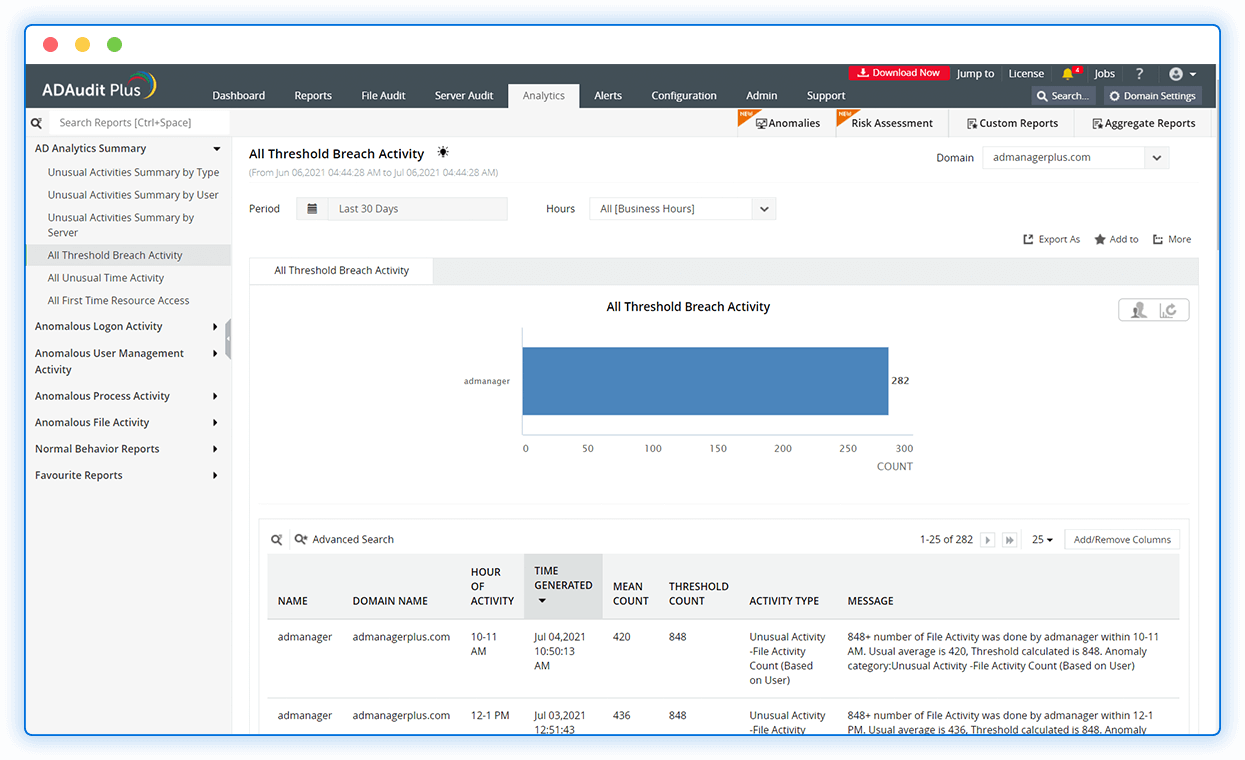
UBA-driven threat detection
Quickly spot excessive logon failures, anomalous logon activity, privilege abuse, data exfiltration, and more with UBA.
-
Identify suspicious file activity
Detect and respond to unauthorized deletion of critical files, file activity at unusual times, sudden surge in file access, and other anomalies.
-
Detect lateral movement
Spot telltale signs of lateral movement such as unusual remote desktop activity, or execution of new processes.
-
Automated response
Respond to threats instantly by executing scripts to end user sessions, shut down machines, prevent logons, and other remedial actions.
Combat insider threats in your Active Directory using our insider threat monitoring tool.