Kerberos Pre-Authentication Failures (Event ID 4771) Causing Account Lockouts?
When Kerberos pre-authentication fails, it’s rarely just noise. These failures—logged under Event ID 4771—can point to stale credentials, misconfigured time settings, or the early stages of a brute-force attack. Whether it’s an expired service account or a bad actor testing passwords, keeping tabs on these events gives you a critical edge in securing Active Directory.
*Fully functional 30 day free trial. No Credit Card Required
Thanks!
Your download is in progress and it will be completed in just a few seconds!
If you face any issues, download manually here
What is Event ID 4771?
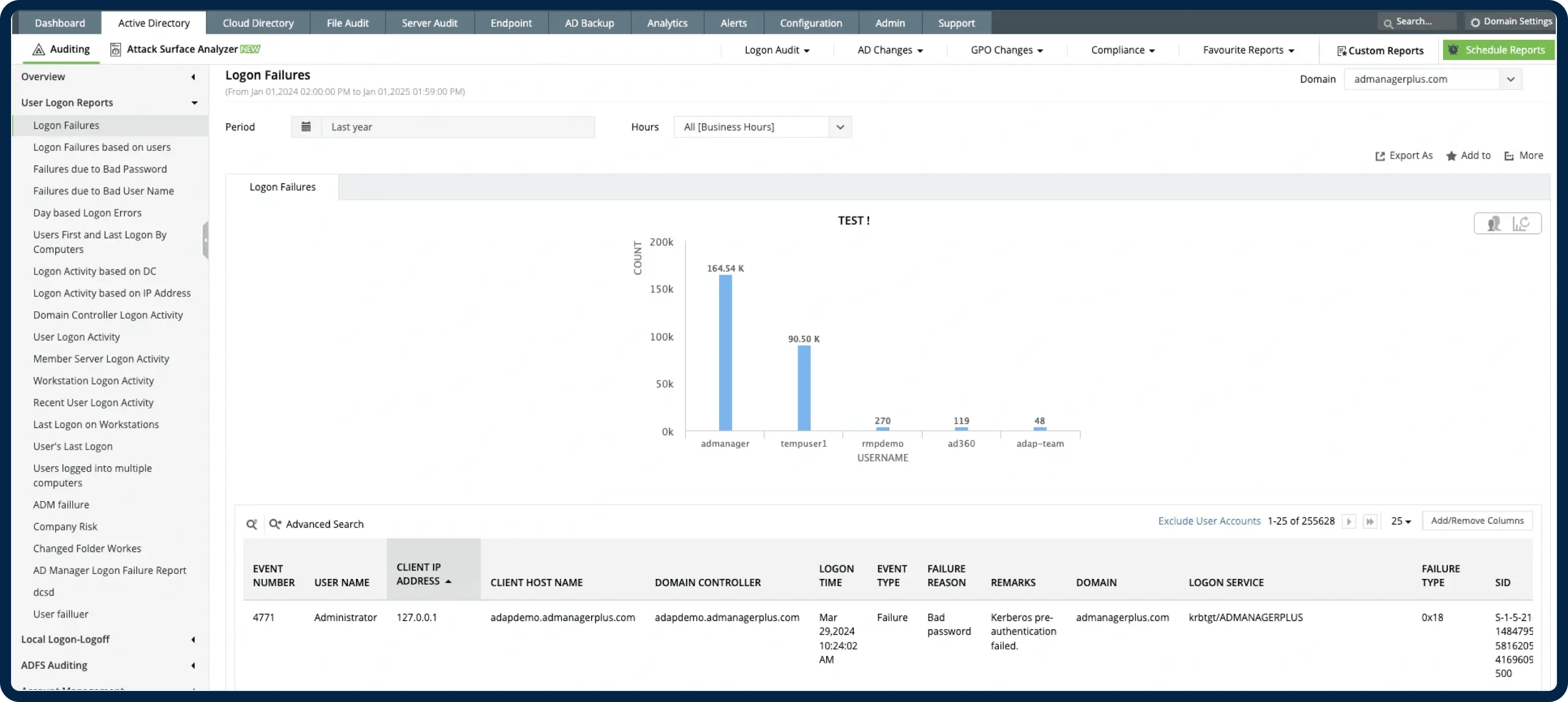
Event ID 4771 logs a Kerberos pre-authentication failure on domain controllers—indicating that a Ticket-Granting Ticket (TGT) request failed due to incorrect credentials, expired passwords, disabled accounts, clock skew, or other issues. These failures can reflect both malicious activity and legitimate configuration problems. Monitoring these helps uncover early signs of compromise and operational gaps.
Why Monitoring Event Code 4771 Matters
Attackers leverage Kerberos pre-auth failures as reconnaissance or brute-force vectors. Additionally, misconfigured systems (e.g., unsynced clocks) can flood systems with 4771 event IDs, creating noise and masking true threats.
- Nearly 100,000+ 4771 failures in 24 hours often stem from password changes in active RDP sessions or desynced clocks—rather than malicious attacks.
- Government guidance highlights that attackers exploit failed pre-auth patterns to evade detection before initiating AS-REP roasting or ticket forgery.
Monitoring kerberos authentication event ID 4771 helps you:
- Detect brute-force or password-spray attacks early
- Identify clock or certificate issues triggering failures
- Separate benign misconfigurations from malicious activity
- Generate audit trails aligned with NIST, PCI DSS, and CIS requirements
According to Verizon DBIR 2024 "70% of breaches begin with compromised credentials"
—making event codes like 4624 your only early clue.
How ADAudit Plus Enhances Event 4771 Visibility
Native tools lack the context and correlation needed. ADAudit Plus provides:
Real-time alerts for high-frequency pre-auth failures
Notify when failure counts spike, occur off hours, involve service accounts or originate from unusual sources.
Centralized 4771 dashboard
Aggregate pre-auth failures across domain controllers. Filterable by user, client IP, timestamp, and failure code.
Cross-event correlation
Link Event ID 4771 with 4768/4769 (Kerberos ticket requests), 4625 (failed logons), and 4672 (privileged activity) to trace attack progress.
Behavior analytics to reduce noise
Identify patterns such as recurring failures due to clock drift or credential stale sessions, and suppress benign activity while highlighting true threats.
Compliance-ready reports and retention
Use built-in templates to produce audit-friendly logs on Kerberos pre-authentication failures. Automate archiving to meet retention policies.
*Fully functional 30 day free trial. No Credit Card Required
Manual Logging vs ADAudit Plus
Trusted by IT Teams Globally
Trusted by over
18,000+ IT teams
worldwide
Gartner Peer Insights Customers' Choice
Compliance-ready platform with ISO 27001 standards
Over 280,000 organizations across 190 countries trust ManageEngine to manage their IT.




Monitor Kerberos Pre-Auth Failures with Context –
Start Tracking Event ID 4771 Today
- 30-day fully functional free trial.
- No user limits.
- Free 24*5 tech support.
*Fully functional 30 day free trial. No Credit Card Required
