Standardize and streamline privilege management.
While creating or managing identities, many IT administrators worry that assigning excessive permissions to users and groups could lead to grave consequences like insider attacks or data breaches. These security risks could be even more worrisome if there are no predefined permission sets for each role.
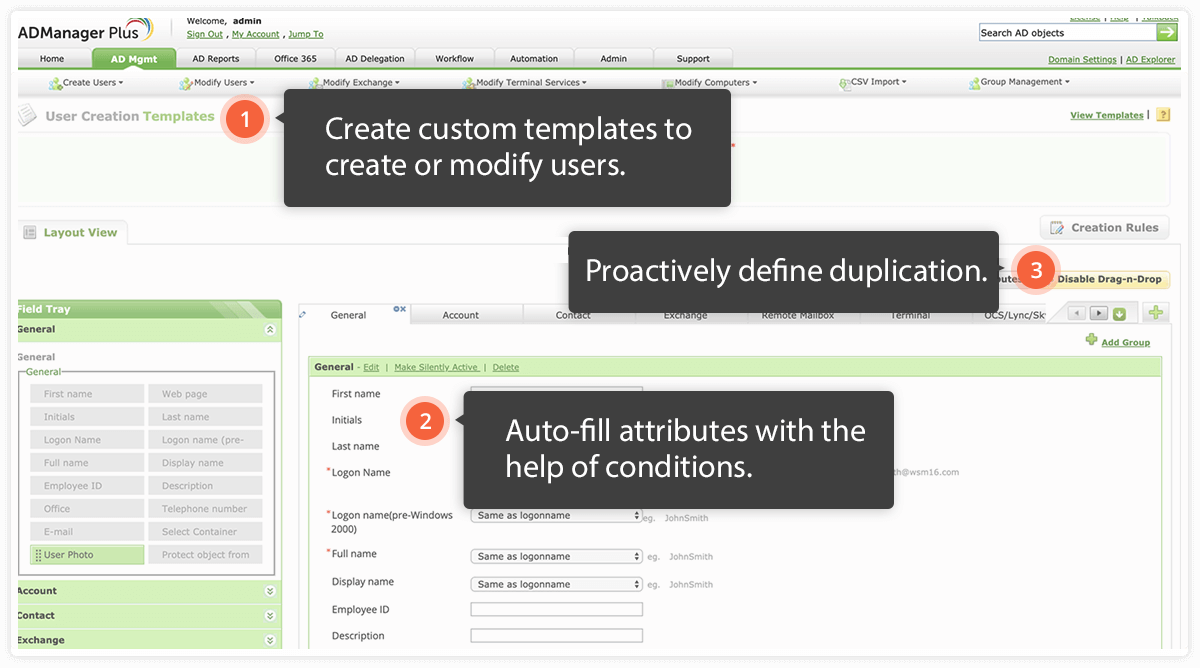
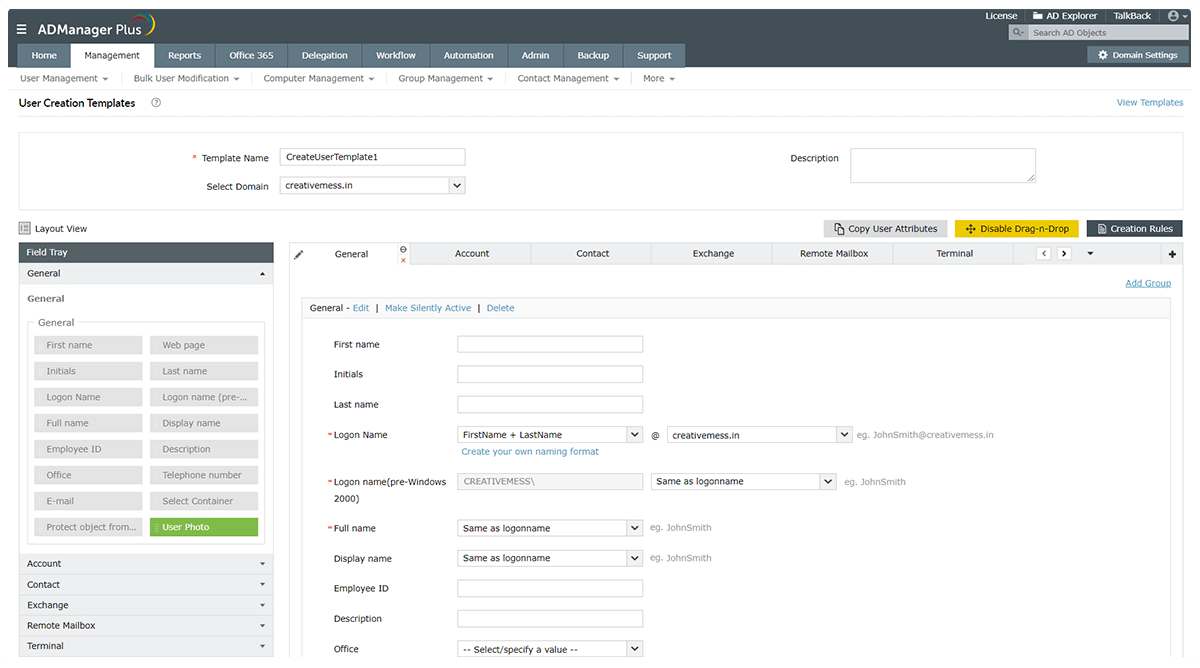
A simple remedy is to design standard templates with the required permissions, as well as group memberships for all roles, especially the privileged roles. You can use this template whenever you create or modify a user account.
Assign only the permissions needed, only when needed.
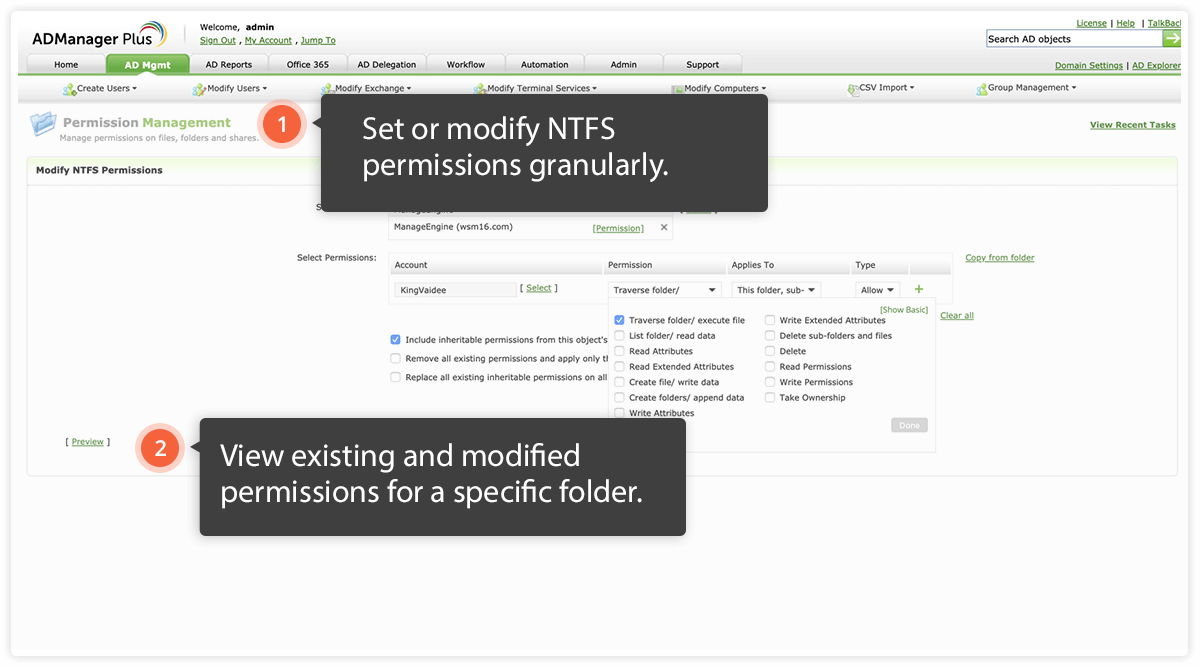
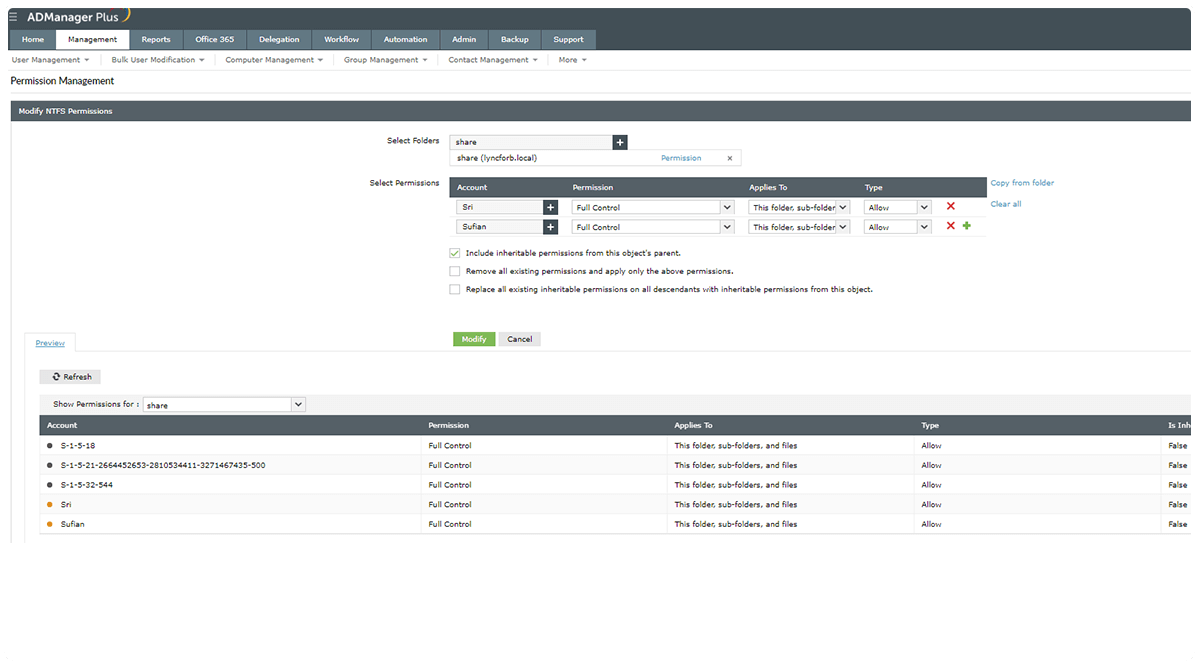
When it comes to permissions and rights management, many IT admins face the dilemma of "How much is too much?" But this situation can't be ignored; incorrectly assigning permissions can lead to disastrous consequences if sensitive data ends up in the wrong hands.
To avoid this, follow this rule of thumb: assign minimal permissions, and remove additional privileges when they are no longer needed or after a specific period of time. To decide what the minimum permissions are and how long special permissions are required, consult the business process owners, or the HRs. Using a solution that helps you automatically assign permissions and revoke them after a specific period makes permissions management easier.
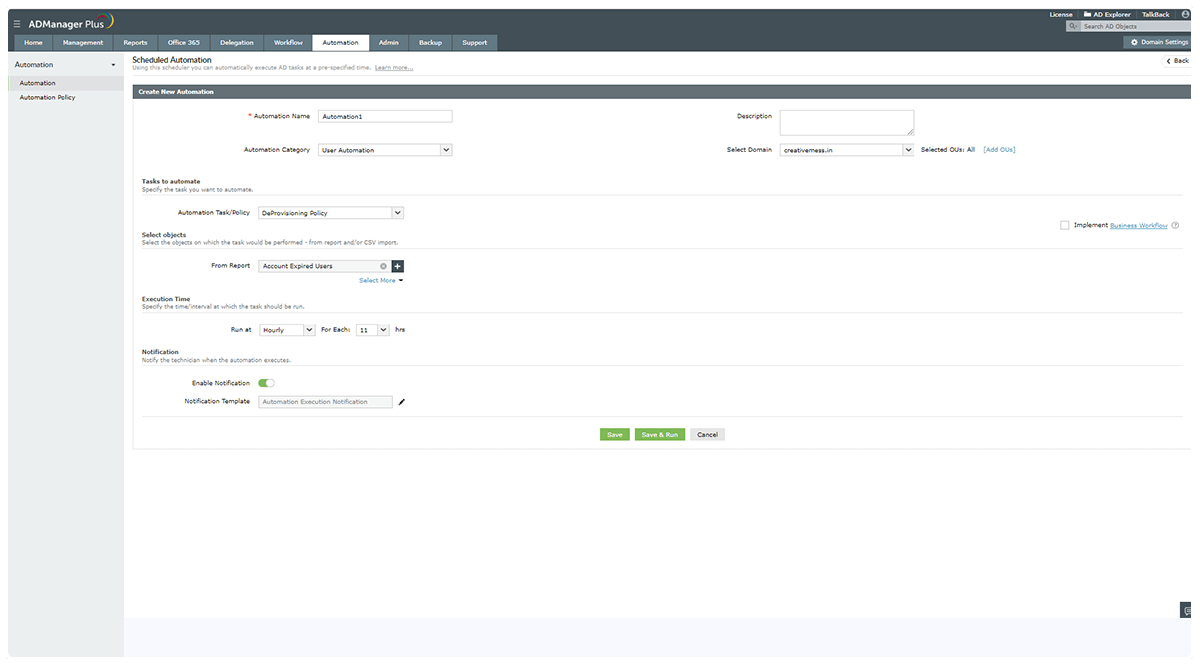
Automate cleanup of stale accounts.
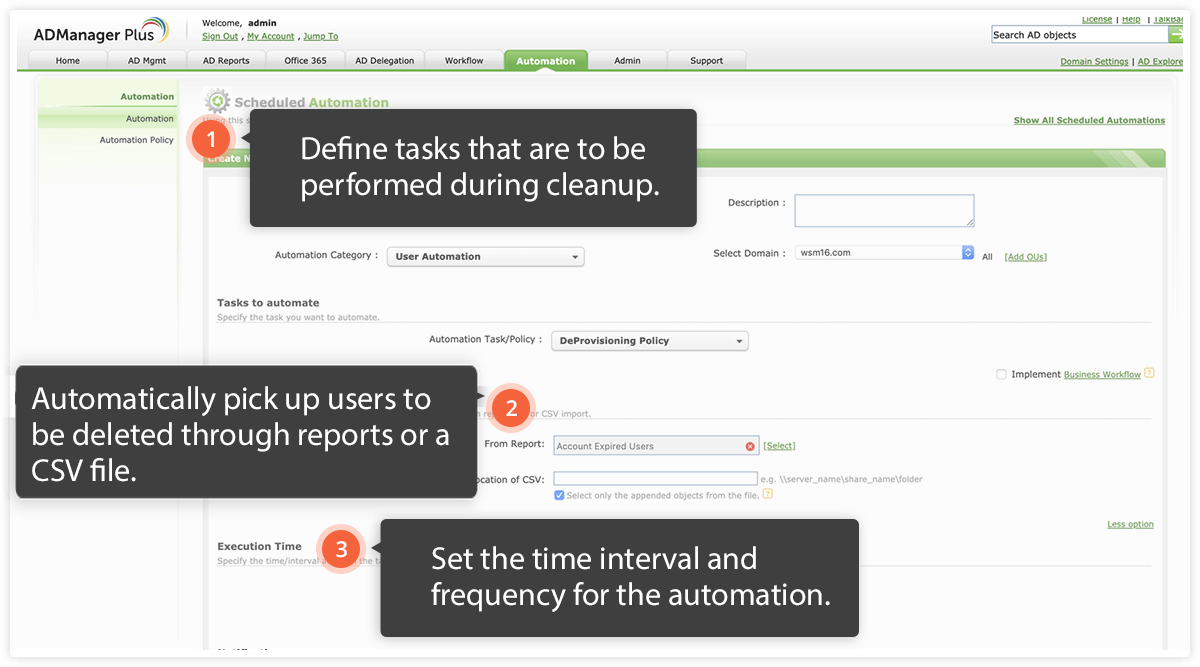
If your offboarding process is not rigidly enforced, ex-employees might retain access to user accounts and critical resources. Infrequent or irregular deprovisioning could lead to excessive stale accounts, which could prove detrimental to your organization's security.
Running automated deprovisioning schedules at frequent intervals keeps your AD environment devoid of stale accounts. You should also sync your AD with your HR software or database so that when a user account is deleted from either of these tools, it is also deleted from AD.
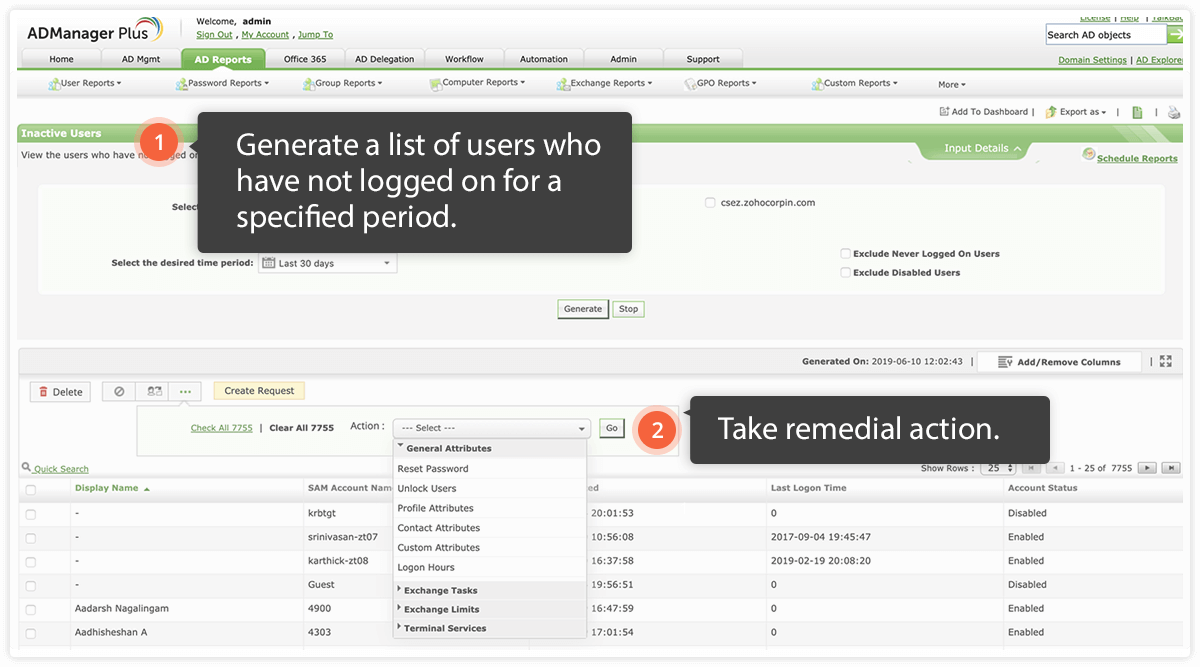
Check for and quarantine inactive users regularly.
User inactivity can occur when an employee goes on extended leave, or an IT admin forgets to disable a former employee’s account. To streamline the onboarding process, some organizations create user accounts with the same passwords before employees join the organization. This can lead to inactive accounts that are easily misused by existing employees. It's essential to track user inactivity and disable the respective accounts to prevent insider attacks; user accounts should either be disabled, or stripped of unnecessary privileges to prevent misuse.
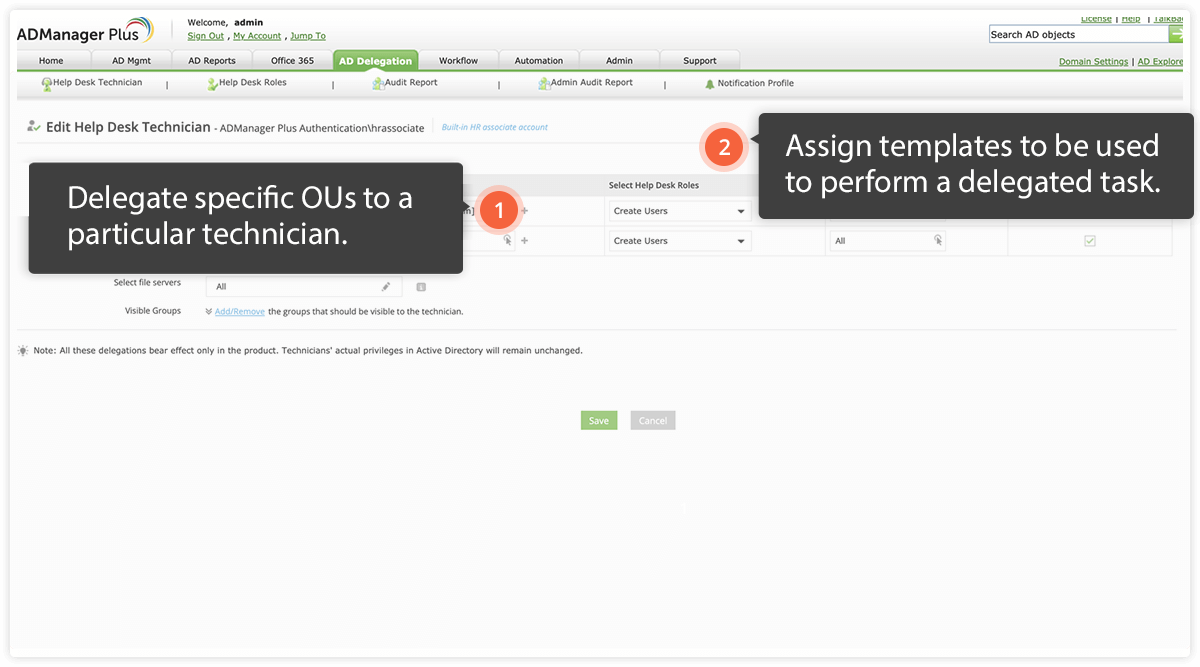
Decentralize IAM securely
Overloading an IT admin with IAM tasks can place an excessive amount of security responsibilty on one person. This can lead to errors due to fatigue, like typos, and might result in modifications to the wrong accounts, misallocation of permissions, and more.
A best practice is to delegate IAM tasks to different IT technicians for different departments. Even better is monitoring an IT technician's everyday activities and rectifying inappropriate ones.