Let's take the pulse of your AD security.
This risk assessment will help you unveil the mysteries within your AD environment, guiding you through the essential elements that define a robust defense.
Ready to conquer the risks?
Fill in the below details
to start the quiz
What is the primary objective of performing risk assessments of an organization's directory service?
-
A To generate user activity reports
-
B To assess the risk posture of the directory environment
-
C To achieve compliance with the GDPR and PCI DSS
-
D To streamline the process of security misconfigurations
You’re right!
Sorry, that’s wrong!
A risk assessment aims to evaluate the overall risk posture of the directory environment by identifying potential risk indicators and suggesting remediation measures.
When does the need for a risk assessment of AD arise?
-
A When there is an audit
-
B When there is a security breach
-
C When there is a lack of visibility into security gaps
-
D When you want to improve incident management
You’re right!
Sorry, that’s wrong!
A lack of visibility into security gaps may lead to unidentified risks, making it crucial for organizations to assess and understand their AD threat landscape comprehensively. Conducting a risk assessment allows organizations to proactively address security issues before they escalate.
Which of the following is generally not considered a common risk indicator in a directory environment?
-
A Inactive users
-
B Privileged computers
-
C Empty groups
-
D Unlinked GPOs
You’re right!
Sorry, that’s wrong!
Privileged computers are not commonly mentioned as a standard risk indicator in a directory environment. Instead, the focus is usually on risks related to users, group memberships, permissions, and configurations that might expose the directory to security threats.
Every risk has a 100% likelihood of happening. True or false?
-
A True
-
B False
You’re right!
Sorry, that’s wrong!
The likelihood of occurrence is not universal for all risks; it varies based on factors such as preventive measures and external influences. Not every risk is guaranteed to occur, and the likelihood can differ significantly.
Of the following, which is a critical severity in the context of AD security?
-
A Inactive users
-
B Members of privileged groups
-
C Disabled users
-
D Users with the "Password not required" option enabled
You’re right!
Sorry, that’s wrong!
User accounts with no password requirement can be easily compromised by attackers, allowing access to critical resources and data. They also result in noncompliance and legal consequences. Risk assessments play a crucial role in identifying and addressing such vulnerabilities.
NIST SP 800-30 provides guidelines for conducting risk assessments of federal information systems and organizations. True or false?
-
A True
-
B False
You’re right!
Sorry, that’s wrong!
NIST SP 800-30: Guide for Conducting Risk Assessments provides an overview of how risk management fits into the system development life cycle and describes how to conduct risk assessments and mitigate risks.
What is a common security concern related to user accounts in AD environments that directly impacts risk assessments?
-
A A lack of multi-factor authentication
-
B Unauthorized access
-
C Inactive user accounts
-
D Inadequate firewall protection
You’re right!
Sorry, that’s wrong!
Inactive user accounts, such as those with low activity or no recent logins, pose a security concern in AD environments. Identifying and addressing such a vulnerability is crucial for maintaining a secure environment, emphasizing the importance of risk assessments.
In the screenshot below, can you guess how the weight is assigned to a particular risk indicator?
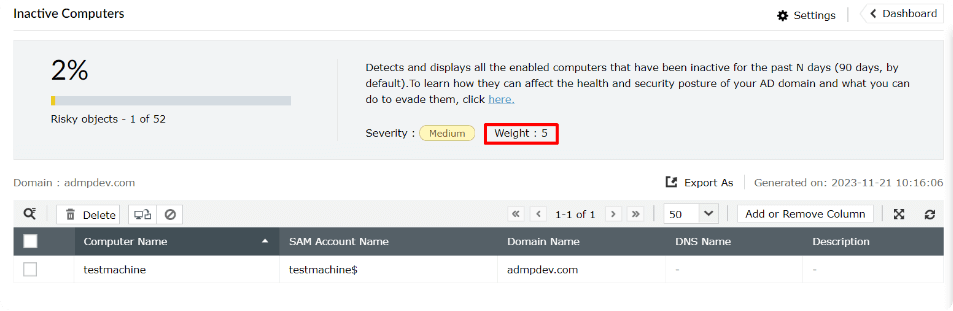
-
A Based on the impact of the risk
-
B Based on the severity of the risk
-
C Both A and B
-
D Based on the risk exposure
You’re right!
Sorry, that’s wrong!
Each risk indicator is assigned a weight based on its impact and severity. The weight scale ranges from 1 to 10.
Can you guess how the risk score in the Identity Risk Assessment report below is determined?
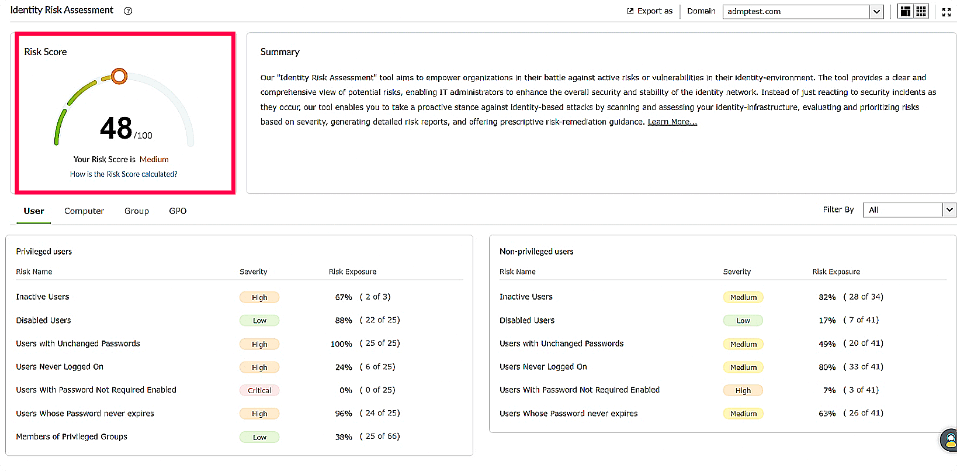
-
A Based on the number of security policies in place
-
B Based on the severity of the identified risk indicators
-
C Based on compliance with IT regulations
-
D Based solely on the organization's overall AD health
You’re right!
Sorry, that’s wrong!
The severity takes into account the potential impacts and consequences associated with each risk, providing a weighted assessment. This approach allows organizations to prioritize and address high-severity risks that pose a more significant threat to the security and integrity of the AD environment.
What are the benefits of performing risk assessments?
-
A Foreseeing AD-related attacks and mitigating them
-
B Improving incident management
-
C Achieving compliance
-
D Strengthening your risk posture
-
E All of the above
You’re right!
Sorry, that’s wrong!
ADManager Plus' risk assessment helps you do all these and more for free. Foresee and mitigate AD-related attacks, ensure compliance with industry standards, elevate your incident management capabilities, strengthen your overall risk posture, and gain invaluable insights for proactive cybersecurity measures.
You aced the risk assessment quiz!
We hope you understood the critical role of risk assessments in fortifying your AD security. Now, let’s turn this knowledge into action.
Because in cybersecurity,
being a step ahead is the real victory!
2024 Zoho Corporation Pvt. Ltd. All rights reserved.