SAML stands for Security Assertion Markup Language. It's an open standard authentication process that simplifies the user information verification by enabling web single sign on (SSO). With a single digital signature, SAML allows users to trade user information between an Identity provider(IDP) and a service.There are various IdPs for SAML, the most popular of the lot include Okta, MS ADFS, Azure, JumpCloud, and OneLogin.
With Applications Manager's support for the SAML authentication process, users can now set up an SAML SSO authenticator with the help of federated identity management solutions. Applications Manager authenticates the user identity behind the scenes and reopens a session where the resource or the URL can be monitored without any hassle.
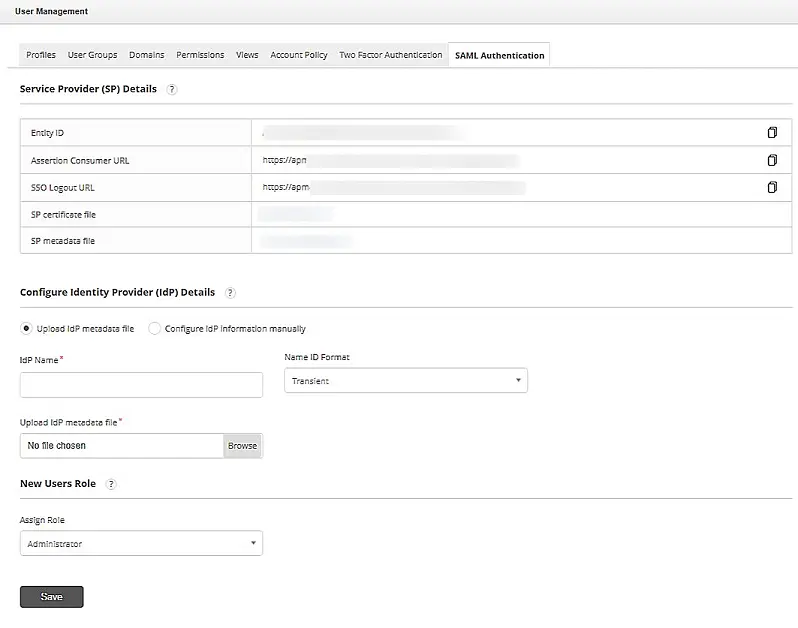
SAML is adopted widely across all areas, especially in enterprises. Since the identity provider stores all login information, the service provider does not need to store any user credentials on their system thereby decreasing the chances of a security breach by concealing the user information. It improves the user's experience by speeding up the authentication process. Applications Manager understands the necessity of security and seamless user experience which is why you can now log in to your resources with a single set of credentials.
SAML authentication process comprises of three primary components:
An Identity Provider is a service that manages and stores user information and signatures on a digital platform. Applications Manager supports all IdPs including Okta, ADFS, Azure, JumpCloud, and OneLogin. A Service Provider is a system that provides a service in the form of an application to the end user. In our case, Applications Manager is the Service Provider and the End User is the entity which requests a service from the service provider.
When a user requests a service or in our case, a resource to be monitored, assuming that the user has an account in the service with valid credentials, Applications Manager checks for an IdP in the background and responds with a token to access the user information which is then relayed to the SSO service. IdP validates the service and responds back with the necessary digital identities. After authenticating the identity, a session with the user login is created where the user can monitor the resource freely.
For guidance to set up SAML authentication in your Applications Manager setup, refer this.
Check out the KBs for assistance regarding configuring popular IDPs:
It allows us to track crucial metrics such as response times, resource utilization, error rates, and transaction performance. The real-time monitoring alerts promptly notify us of any issues or anomalies, enabling us to take immediate action.
Reviewer Role: Research and Development