Security professionals had a hectic start to 2018 with the discovery of two critical processor bugs—Meltdown and Spectre. Without diving too far into the details, these bugs can be described as a family of vulnerabilities that allow processes to access data;that is normally inaccessible to them.* Theoretically, hackers can leverage these flaws to access confidential data,including passwords, email IDs, cryptographic keys, and more.
See what industry experts have to say with respect to Meltdown and Spectre, Download ManageEngine Experts Digest and get a vendor neutral approach towards these CPU bugs.
These vulnerabilities have put computers and mobile devices using Intel processors and some AMD and ARM processors (i.e. most systems) at risk of data leaks. Luckily, operating system vendors have released patches that can help protect endpoints from both Meltdown and Spectre.
The only true fix for these bugs is to replace the affected processors but this is a tall and unrealistic order for enterprises.Leading operating system vendors including Microsoft, Apple, and Google have already released updates to fix Meltdown, but Spectre has proven more difficult to patch and will continue to cause issues until further security updates are released from these vendors.
Apple has already handled this exploit in iOS 11.2.2, macOS 10.13.2, and tvOS 11.2.However Apple has not yet released an update for Safari or macOS Server.
Mozilla has released a security update for its browser Firefox to mitigate both Meltdown and Spectre attacks.
Linux has also already released patches for the kernel in versions 4.14.11 and 4.9.74. The complete list of versions and their updates can be found here.
Cloud vendors like VMware, AWS, Citrix, and Azure have also released fixes.
Microsoft was the first to respond releasing an emergency security update for Windows 10.
Note: You shouldn't install this security update if your computer is running incompatible antivirus software. Read more
According to Google, mobile devices that are running the latest version of Android, released January 5th as a part of Android's January security patch, are safe from this exploit. So users with Google-branded phones running the latest version of Android safe. However, Android users on other devices will have to wait until device manufacturers roll out their own patches.
In the case of Chrome, patches for Meltdown and Spectre will be released on January 23, 2018, with Chrome 64. This update will help protect users from both desktop and mobile-based web attacks.
Our patch management solutions can automate security updates for you, simplifying the process of patching multiple operating systems and programs. Download either our exclusive patch management or endpoint management solution to resolve these exploits automatically.
Follow the steps below to patch both Meltdown and Spectre.
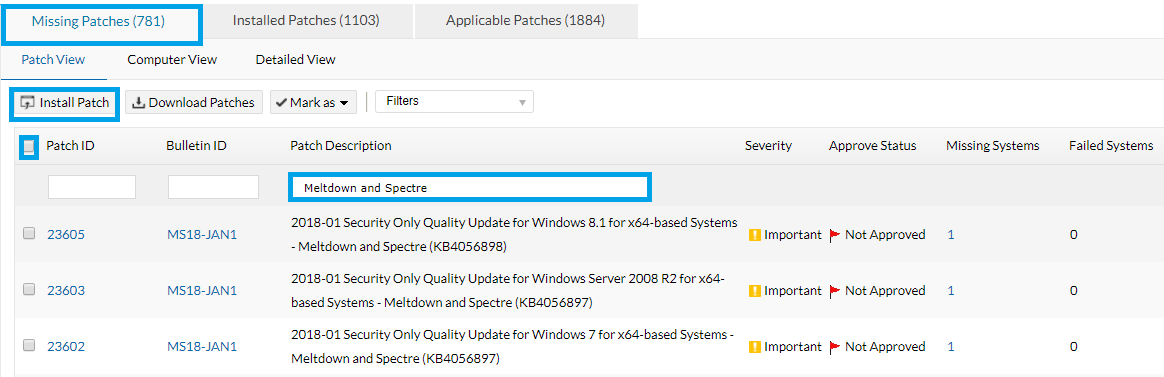
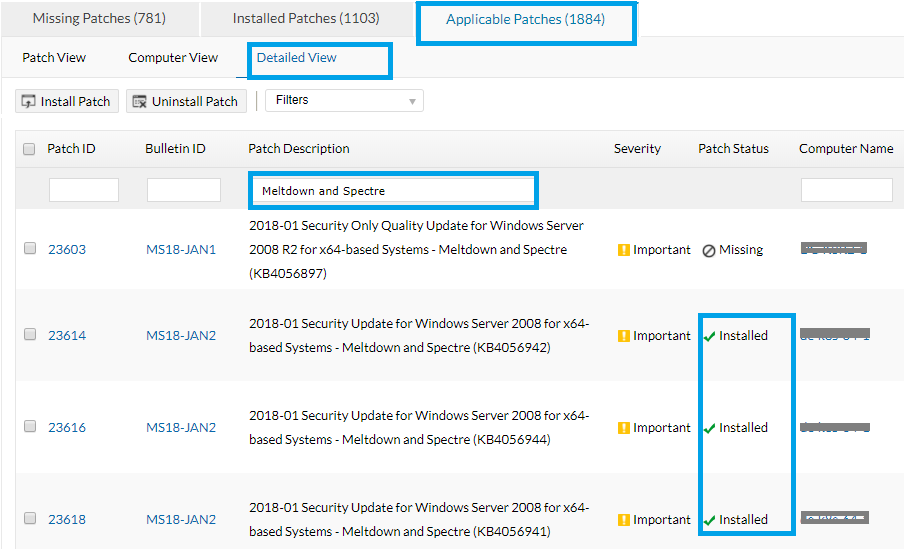
Do you still have questions? Check the FAQ's on Meltdown and Spectre.
FAQ's*Here's a full description on Meltdown and Spectre from the experts.