As a crucial component of network security, database auditing is essential for safeguarding sensitive corporate data, strengthening security measures, and ensuring compliance with regulatory requirements.
ManageEngine EventLog Analyzer aids in database auditing by seamlessly collecting and monitoring logs from various database servers. The solution delivers comprehensive reporting and analysis of database activity across platforms such as Microsft SQL, Oracle, MySQL, and IBM DB2 by correlating and investigating log data. It also provides user activity tracking, change management, server activity tracking, and detection of database security attacks like SQL injection.
Enterprises seeking connections among diverse logs from multiple sources can rely on EventLog Analyzer's advanced correlation capabilities. With EventLog Analyzer, you can:
Additionally, the tool features a specialized log data search segment, enabling you to swiftly pinpoint raw SQL logs, network irregularities, application glitches, and more.
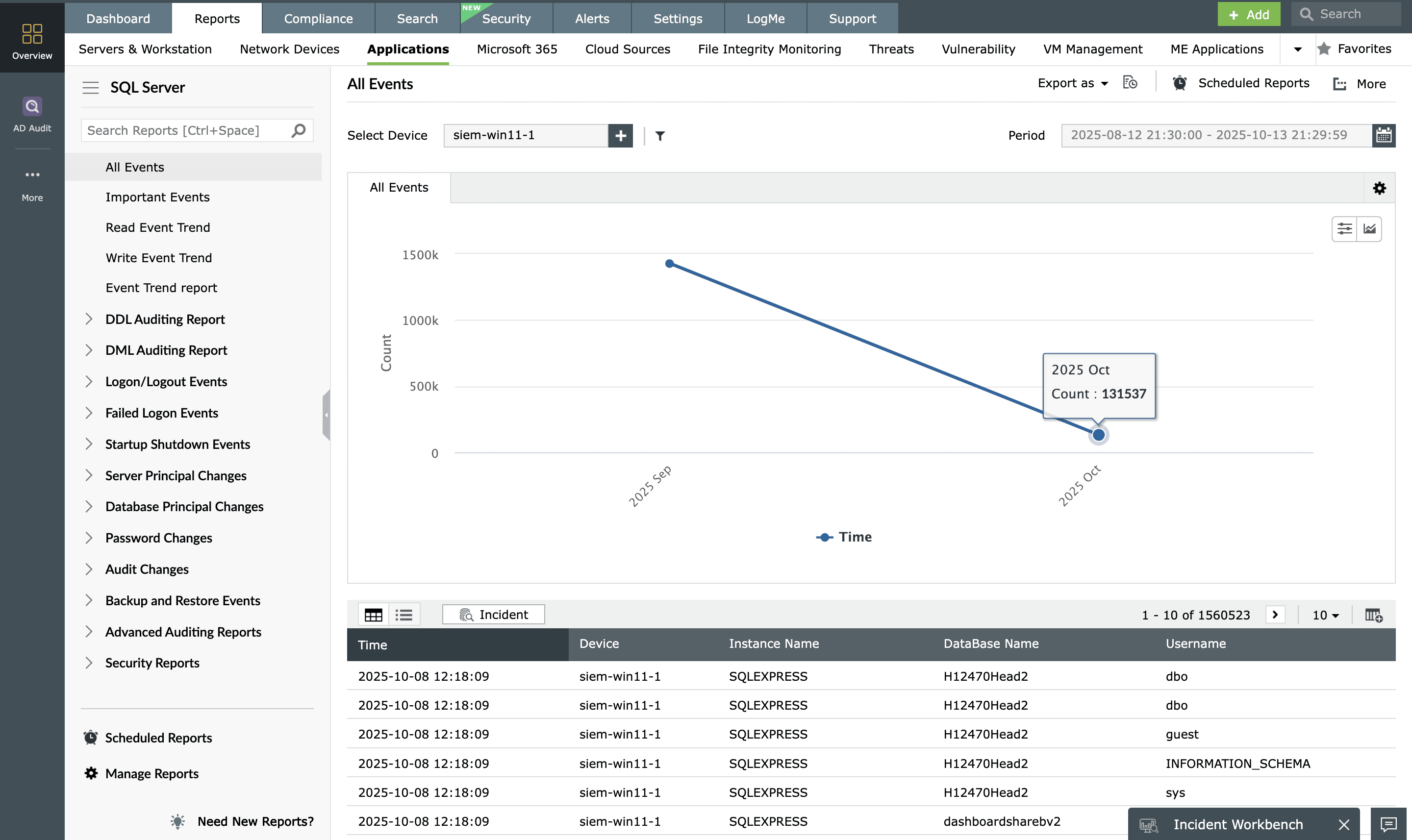
EventLog Analyzer is a comprehensive database log management solution that streamlines the collection of database logs from across your network. It simplifies log analysis by providing preconfigured reports for various database activities, including account management, user changes, server security, and more. Not only does it compile these reports, but it also keeps you informed in real-time about security events through instant alerts. EventLog Analyzer ensures the secure archiving of logs, adding an extra layer of protection.
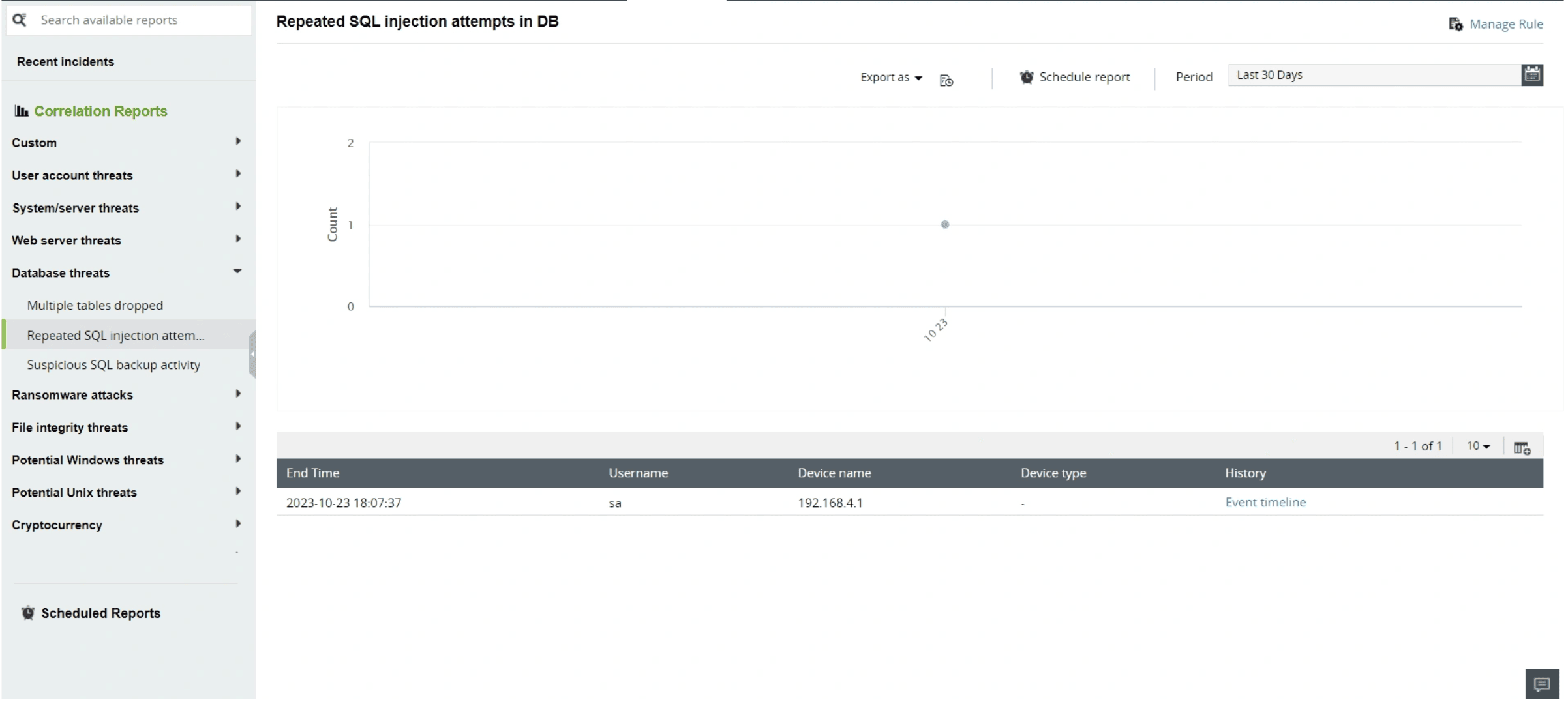
EventLog Analyzer provides real-time monitoring to alert on prominent database attacks like SQL injection, maintains an audit trail for compliance and investigations, identifies complex attack patterns through correlation of events, and provides prebuilt reports for regulatory compliances, including HIPAA, PCI DSS, FISMA, and SOX.
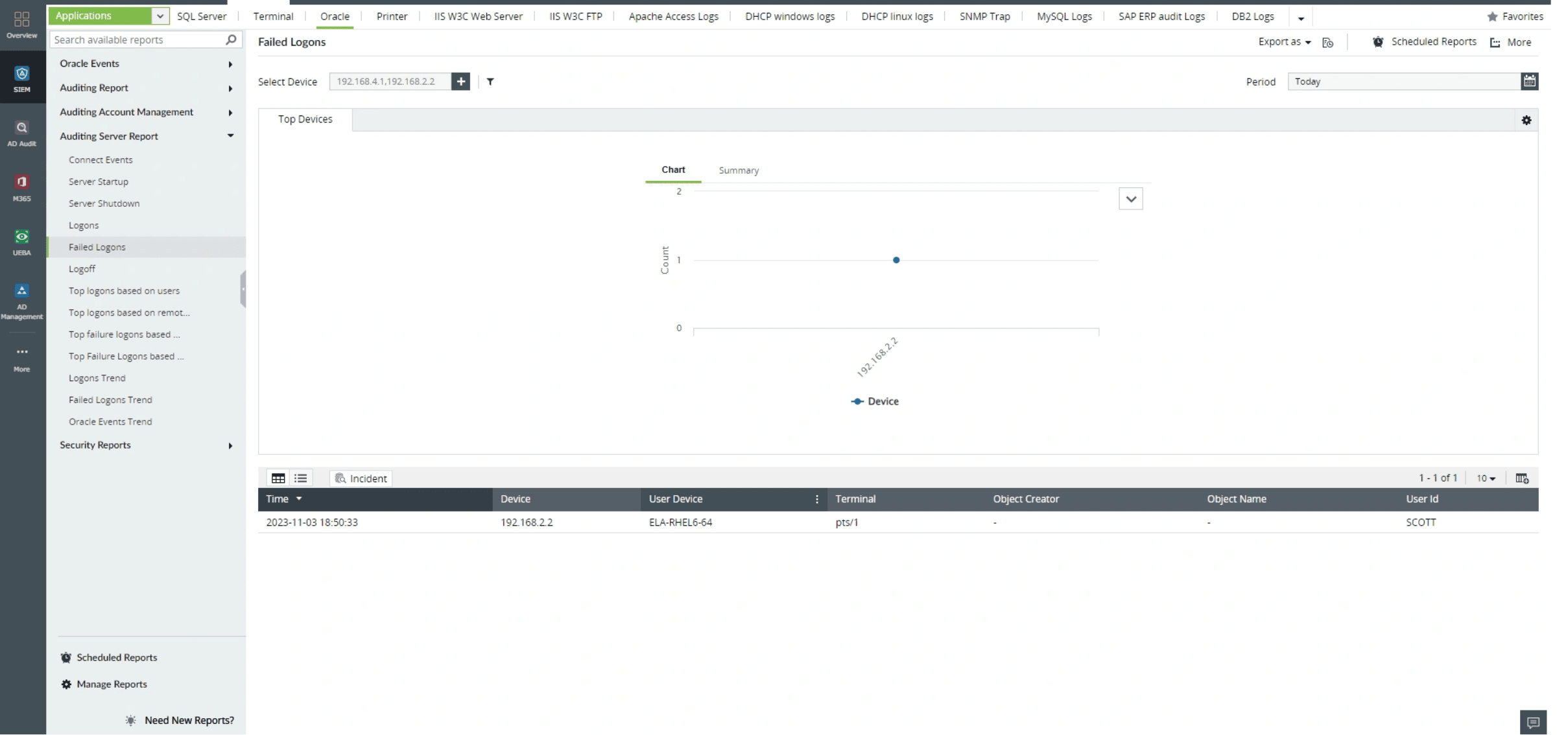
EventLog Analyzer offers in-depth analysis capabilities by providing reports specifically designed for database server log analysis. These reports provide insights into users who logged in the most or users who failed logons the most, enabling a more comprehensive understanding of database server activity. By utilizing these reports, you can derive valuable insights from your logs, identify patterns, and trends in server activities, and make data-driven decisions to enhance database security and performance. This deeper analysis helps to address issues proactively and optimize database operations for improved efficiency and security.

Database activity monitoring is essential for maintaining data security. It enables comprehensive tracking and issues instant alerts about security events in the database, including crucial database transactions like change in DDL and DML statements. With this capability, you can identify and monitor who accesses the database and track the specific actions they perform, ensuring accountability and data integrity. By promptly detecting any suspicious or unauthorized activities, this monitoring contributes to enhanced security and compliance with regulatory standards.

EventLog Analyzer is a comprehensive Microsoft SQL database monitoring tool that helps you monitor all database activities, access attempts, and server account changes in your Microsoft SQL Server database. It automatically discovers all the SQL servers present in your network.
Beyond monitoring, EventLog Analyzer tracks changes made at the database's structural level, such as changes to the tables, views, procedures, triggers, schema, and more. With intuitive graphical reports, get the details of who made a specific change, when it was made, and its origin. Our solution also reports on successful and failed logon events.
EventLog Analyzer provides a comprehensive view of your databases, providing detailed insights into activities, queries, and performance metrics, ensuring you stay informed.
EventLog Analyzer enables detailed incident investigations through advanced historical analysis, providing a precise timeline for forensic examination of security incidents.
Identify intricate attack patterns within SQL servers, detecting potential threats like privilege abuse, credential theft, and SQL injection attempts.
EventLog Analyzer delivers detailed insights into privileged user activity, generating graphical reports for both device-specific and user-centric events.
Database auditing is a process of monitoring and tracking activities, and granting access to a database to ensure data security, compliance with regulations, and the integrity of the information stored within the database. This practice involves recording and analyzing events and actions related to the database management system (DBMS) and the data it contains
To audit data in a database, set clear objectives, enable auditing (either through the database's native features or third-party tools), configure what to audit, and regularly review logs for unauthorized activities. Take necessary actions, secure audit data, generate compliance reports, and adapt the auditing configuration as the database evolves.
The purpose of a database audit is to safeguard data security, uphold regulatory compliance, and verify data integrity. It involves systematically tracking and recording actions related to a database and its management system. This process helps detect security breaches, unauthorized access, and data tampering, ensuring the protection and authenticity of data. Furthermore, it aids in demonstrating adherence to legal and industry standards, supports forensic investigations, and offers insights for optimizing database performance.
Within a SQL database management system, SQL database auditing involves monitoring and recording activities to:
To implement SQL database auditing, enable auditing, capture relevant data, store it in audit logs, regularly review logs, and take necessary actions. This can be accomplished using built-in DBMS features or third-party tools, depending on the complexity and requirements of the database environment.