- Related Products
- Log360
- AD360
- ADManager Plus
- ADAudit Plus
- ADSelfService Plus
- Exchange Reporter Plus
 Click here to expand
Click here to expand
Network administrators are always in need of more information and insights from their log data. There are times when an IT administrator would identify some log information which is useful and would like to have it indexed automatically as a new field. Having more fields being indexed makes your log data more useful while conducting log forensics analysis and creating network security reports.
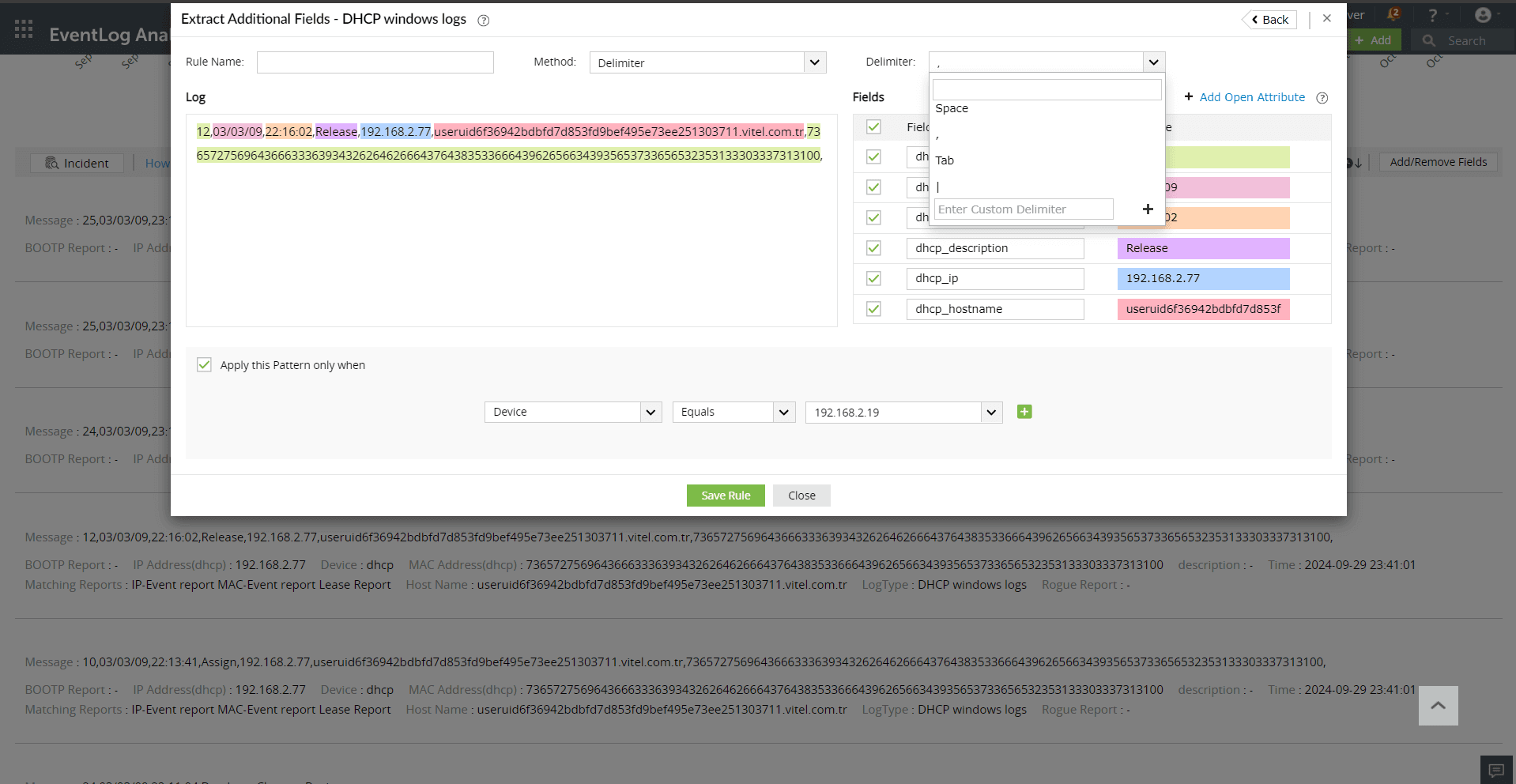
EventLog Analyzer allows administrators to create custom (new) fields or extract fields from raw logs by using the interactive Field Extraction UI to create regular expression (RegEx) patterns to help EventLog Analyzer to identify, parse and index these custom fields from new logs it receives from network systems and applications.
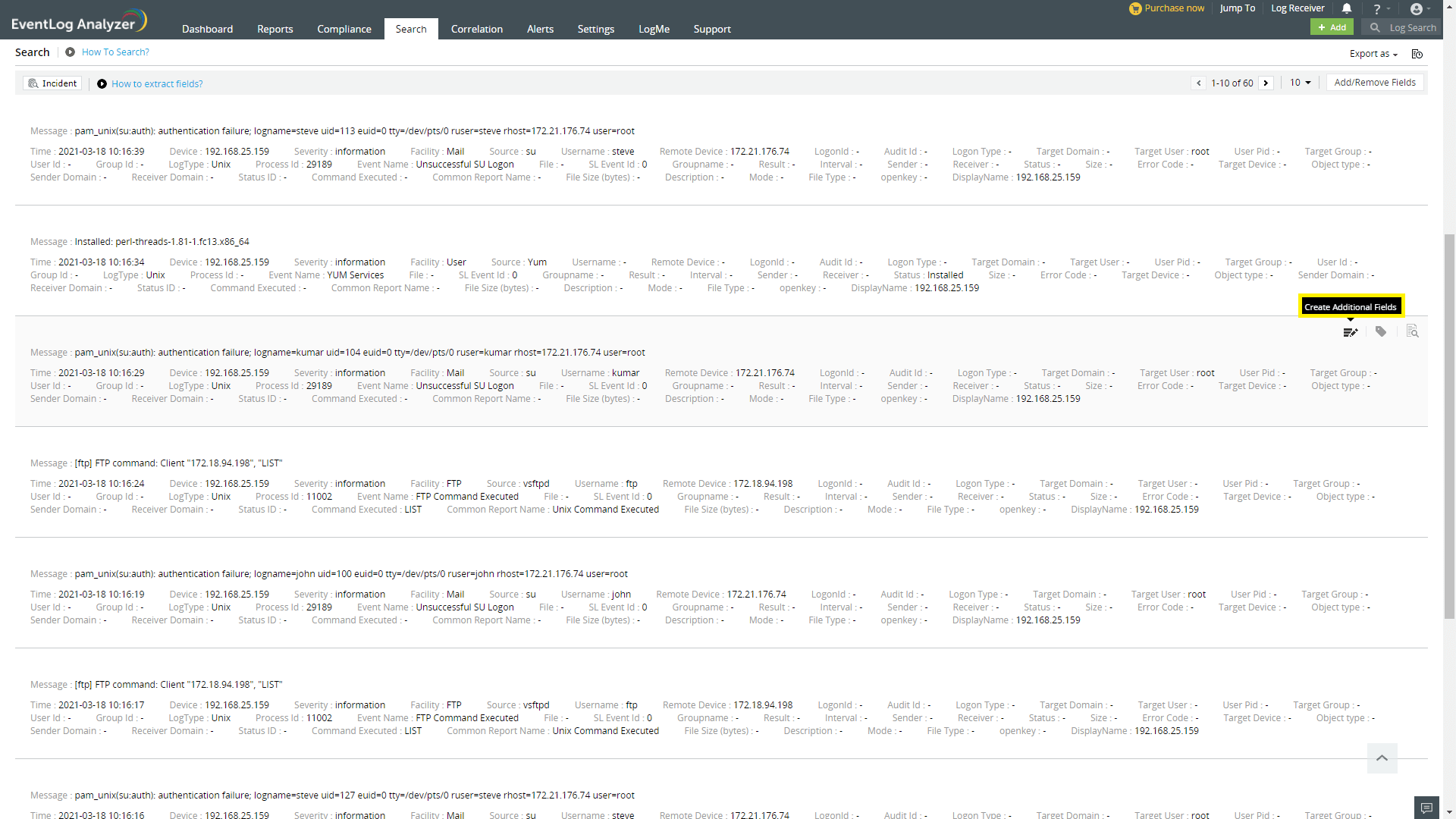
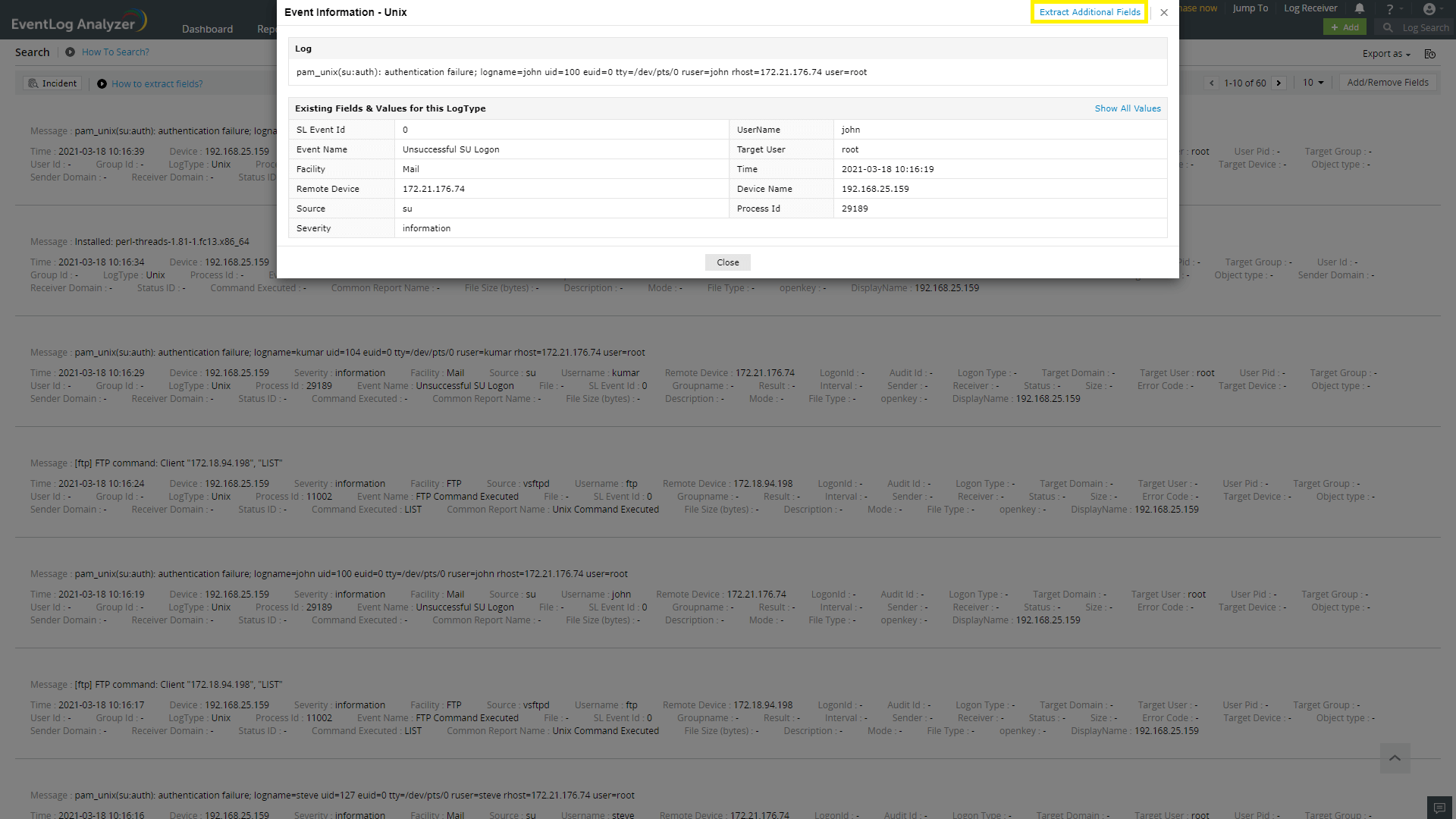
There are two methods by which custom fields can be specified viz.
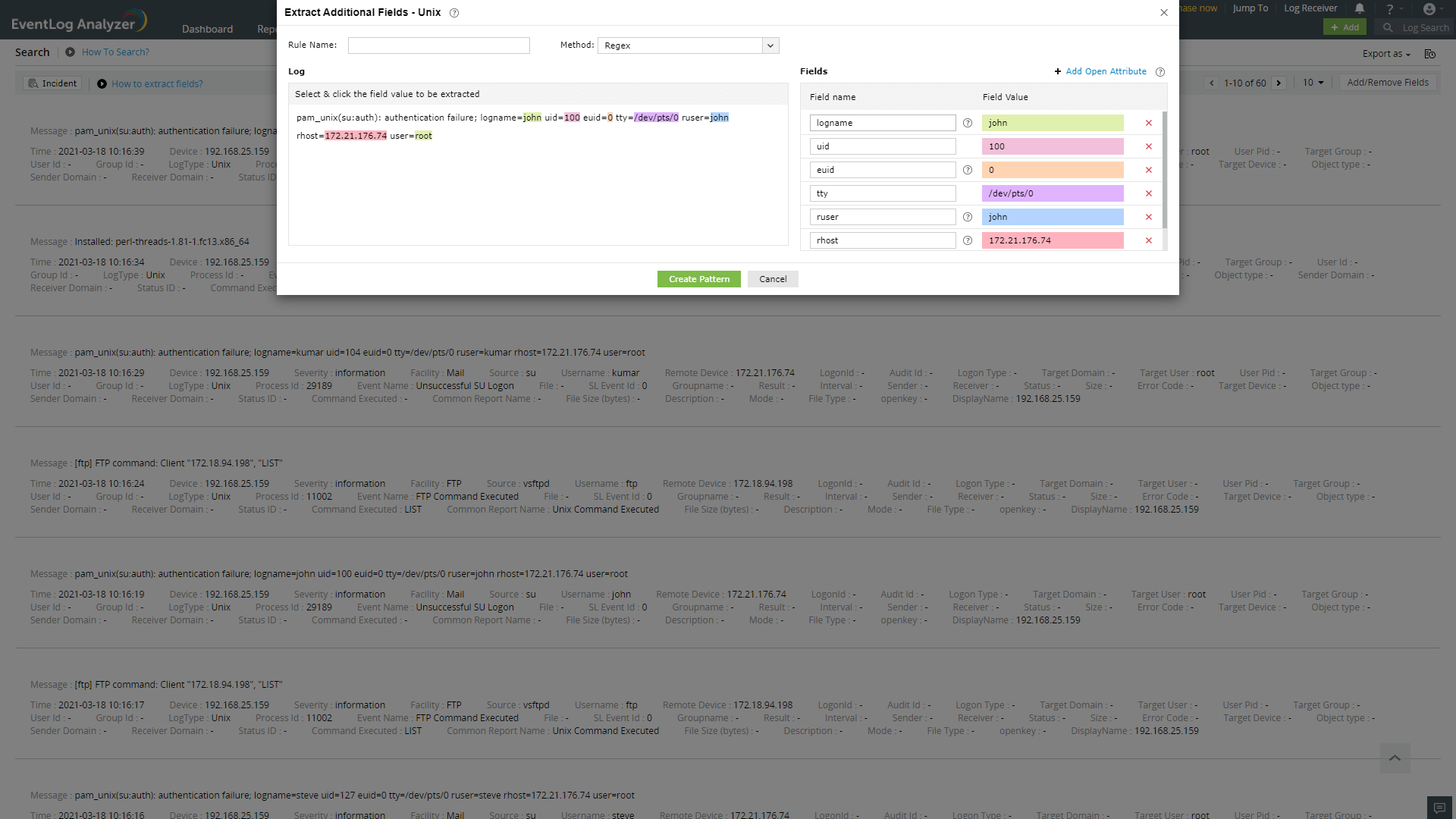
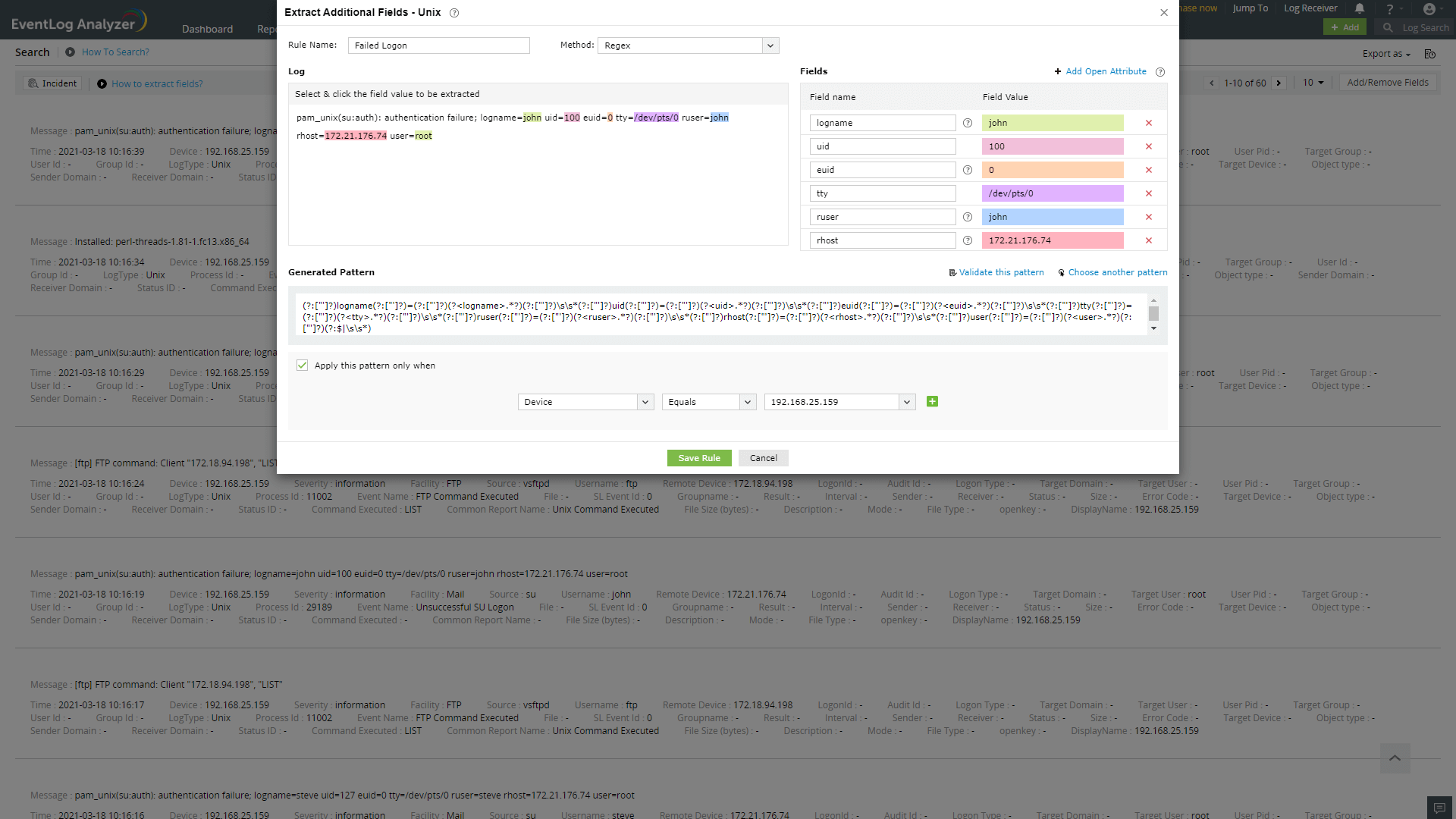
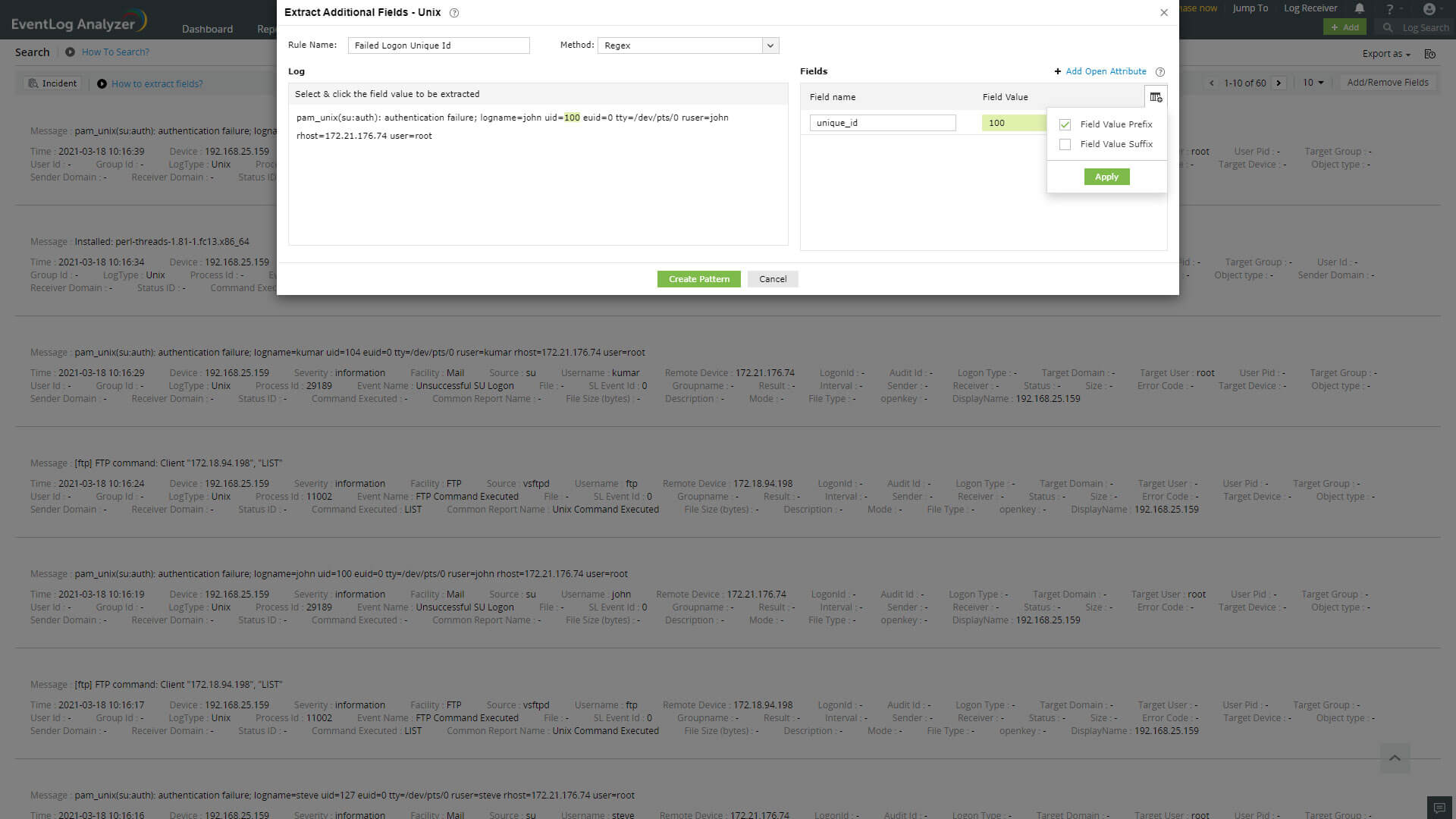
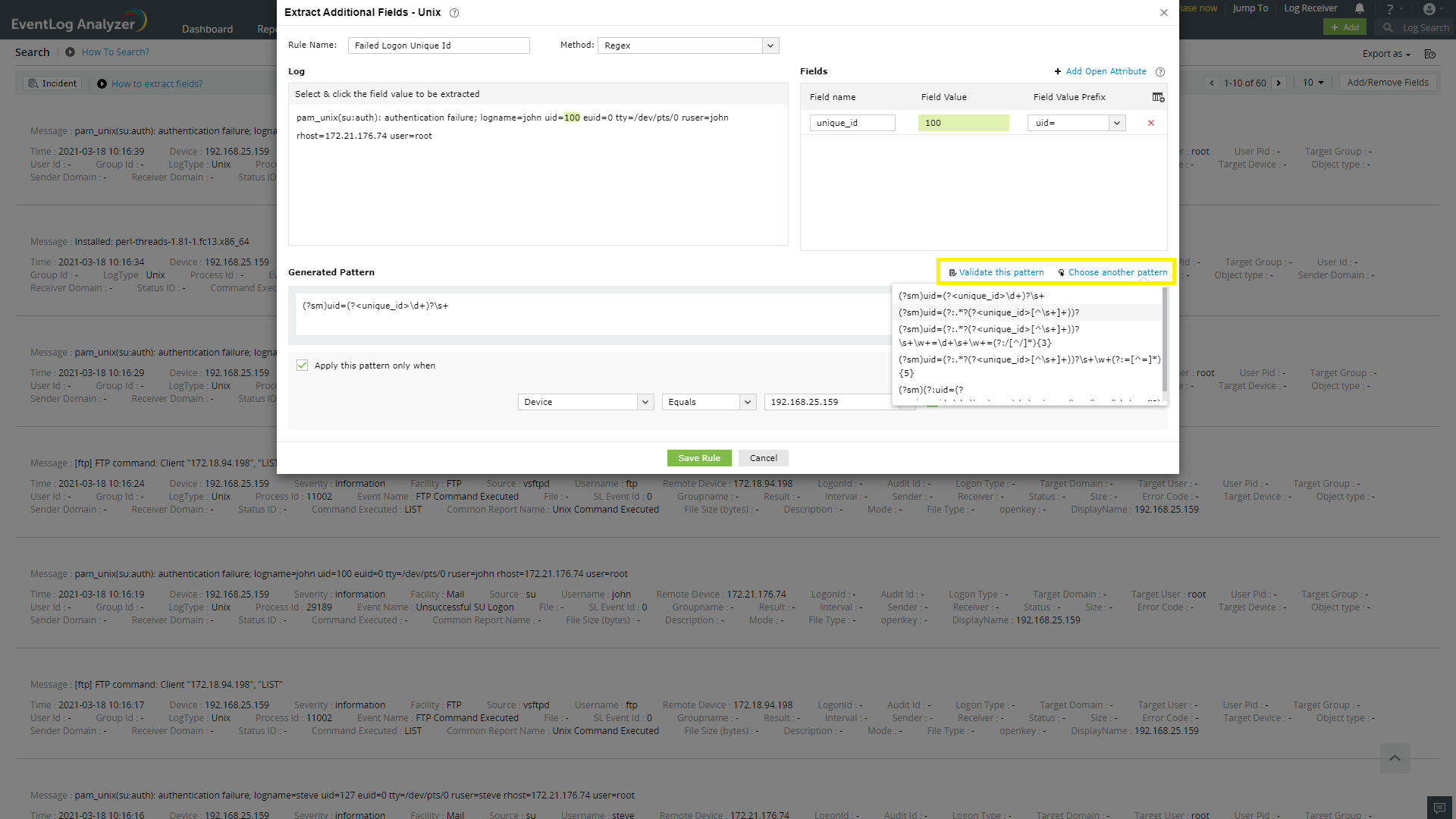
A parser rule pattern is created using the field definition. You can edit the generated pattern manually, if you are familiar with regular expressions.
Validate link is used to test the generated pattern against the previous search results. You can manually check the suitability of the pattern by analyzing the 'Matched Log Messages' and 'Unmatched Log Messages' displayed.
Copyright © 2020, ZOHO Corp. All Rights Reserved.