- Related Products
- Log360
- AD360
- ADManager Plus
- ADAudit Plus
- ADSelfService Plus
- Exchange Reporter Plus
 Click here to expand
Click here to expand
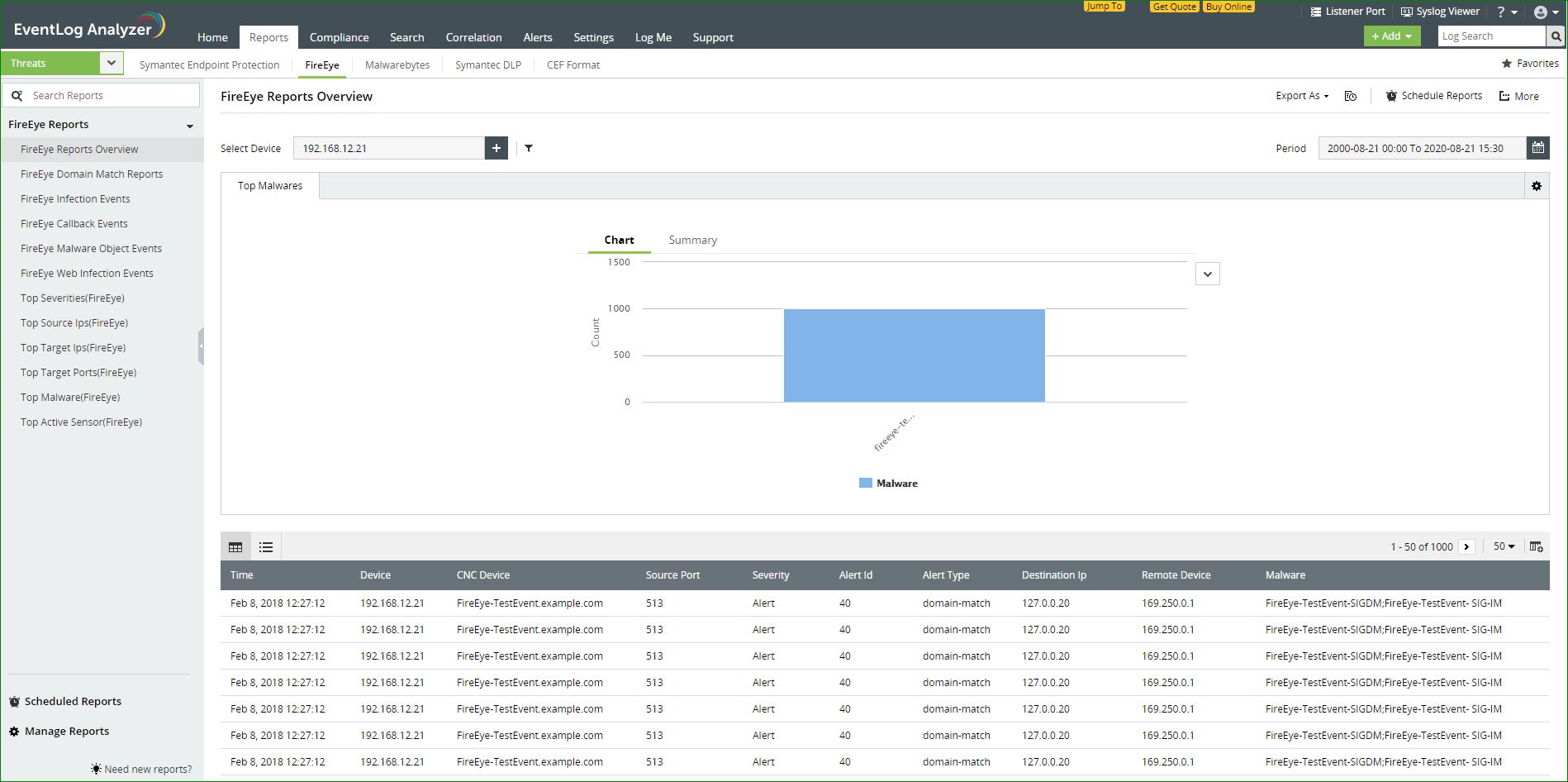
EventLog Analyzer can process log data from FireEye and present the data in the form of graphical reports. For the solution to start collecting log data from FireEye, it has to be added as a threat source.
To add a FireEye device as a threat source, the syslog service has to be configured on the FireEye device.
Once the device is added in EventLog Analyzer, it should then be listed as a threat source. This can be done in a few simple steps.
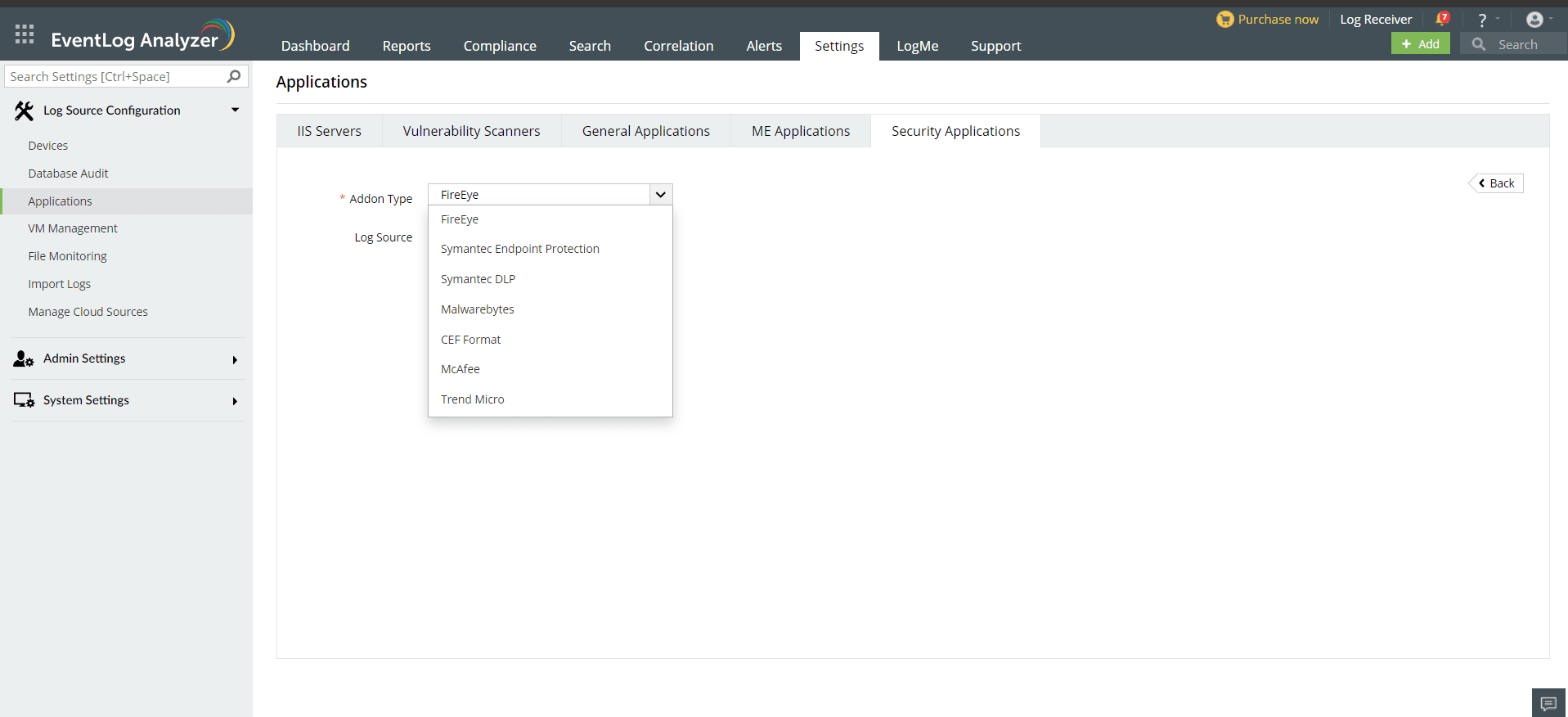
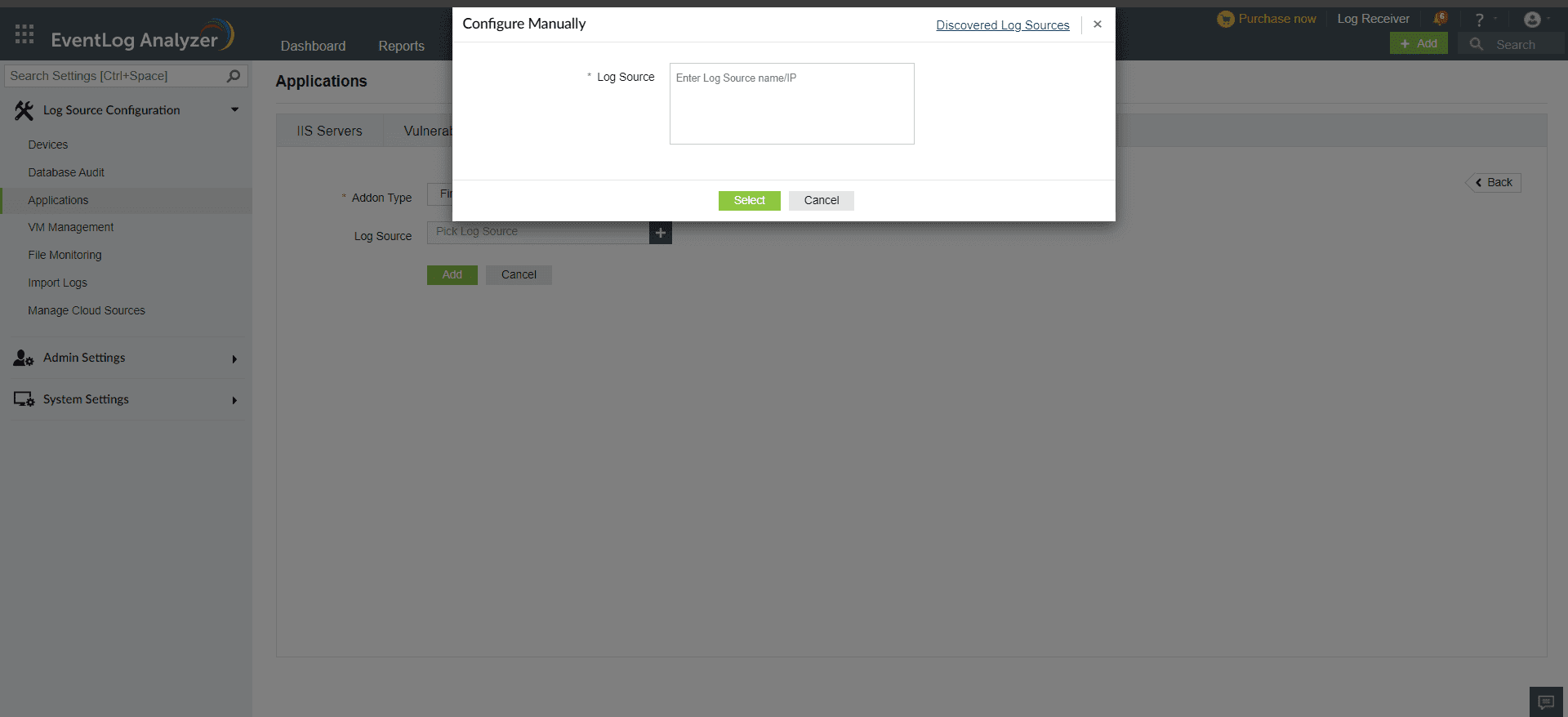
Once the threat source is added, EventLog Analyzer will start parsing the fields in the logs. This log data can now be viewed in the form of reports.
The reports provide information on:
EventLog Analyzer also provides reports that give information on the top:
Copyright © 2020, ZOHO Corp. All Rights Reserved.