Automate your log management processes and stay on top of network activities.
Find out how EventLog Analyzer can simplify log management for your enterprise.
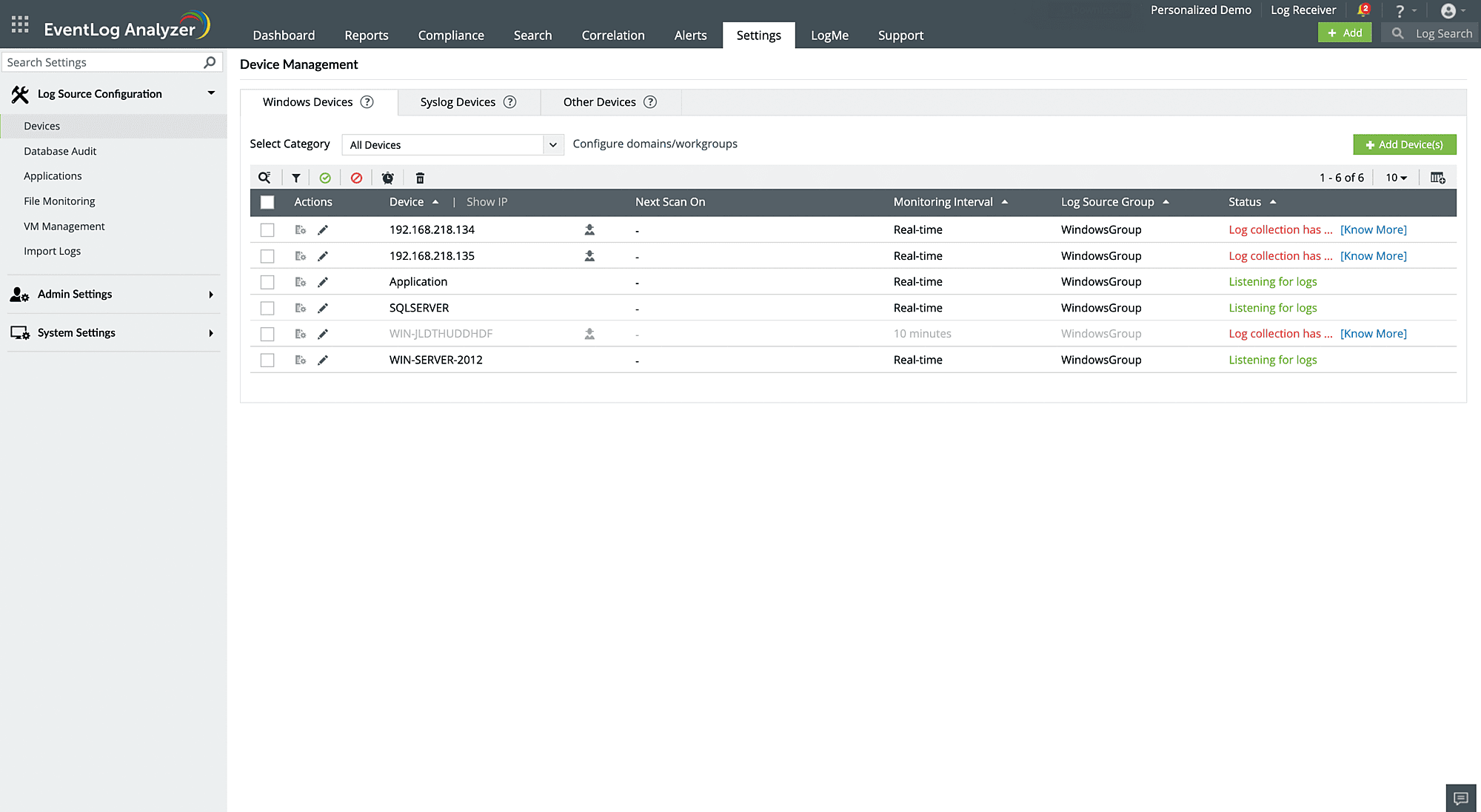
Centralize logs from different sources across the network for security and compliance needs with EventLog Analyzer. The log management solution automates and centralizes the logging process and offers support for over 750 log formats, including Windows and Unix/Linux systems; applications such as databases and web severs; network security tools such as firewalls, IDS/IPS, endpoint detection and response (EDR) tools, proxy servers, and more.
EventLog Analyzer can automatically scan and discover the devices in your network and provides an option to configure those devices from within its console to ease the central log collection. This tool supports both agentless and agent-based log collection mechanisms. You can also import log files or schedule log file import to automate the centralized log collection mechanism. The collected logs are automatically parsed and normalized for better log analysis. Furthermore, the custom log parser extends the logging support for applications that don't follow standard logging services and stores the logs as text files.

Centralize logs from different sources across the network for security and compliance needs with EventLog Analyzer. The log management solution automates and centralizes the logging process and offers support for over 750 log formats, including Windows and Unix/Linux systems; applications such as databases and web severs; network security tools such as firewalls, IDS/IPS, endpoint detection and response (EDR) tools, proxy servers, and more.
EventLog Analyzer can automatically scan and discover the devices in your network and provides an option to configure those devices from within its console to ease the central log collection. This tool supports both agentless and agent-based log collection mechanisms. You can also import log files or schedule log file import to automate the centralized log collection mechanism. The collected logs are automatically parsed and normalized for better log analysis. Furthermore, the custom log parser extends the logging support for applications that don't follow standard logging services and stores the logs as text files.
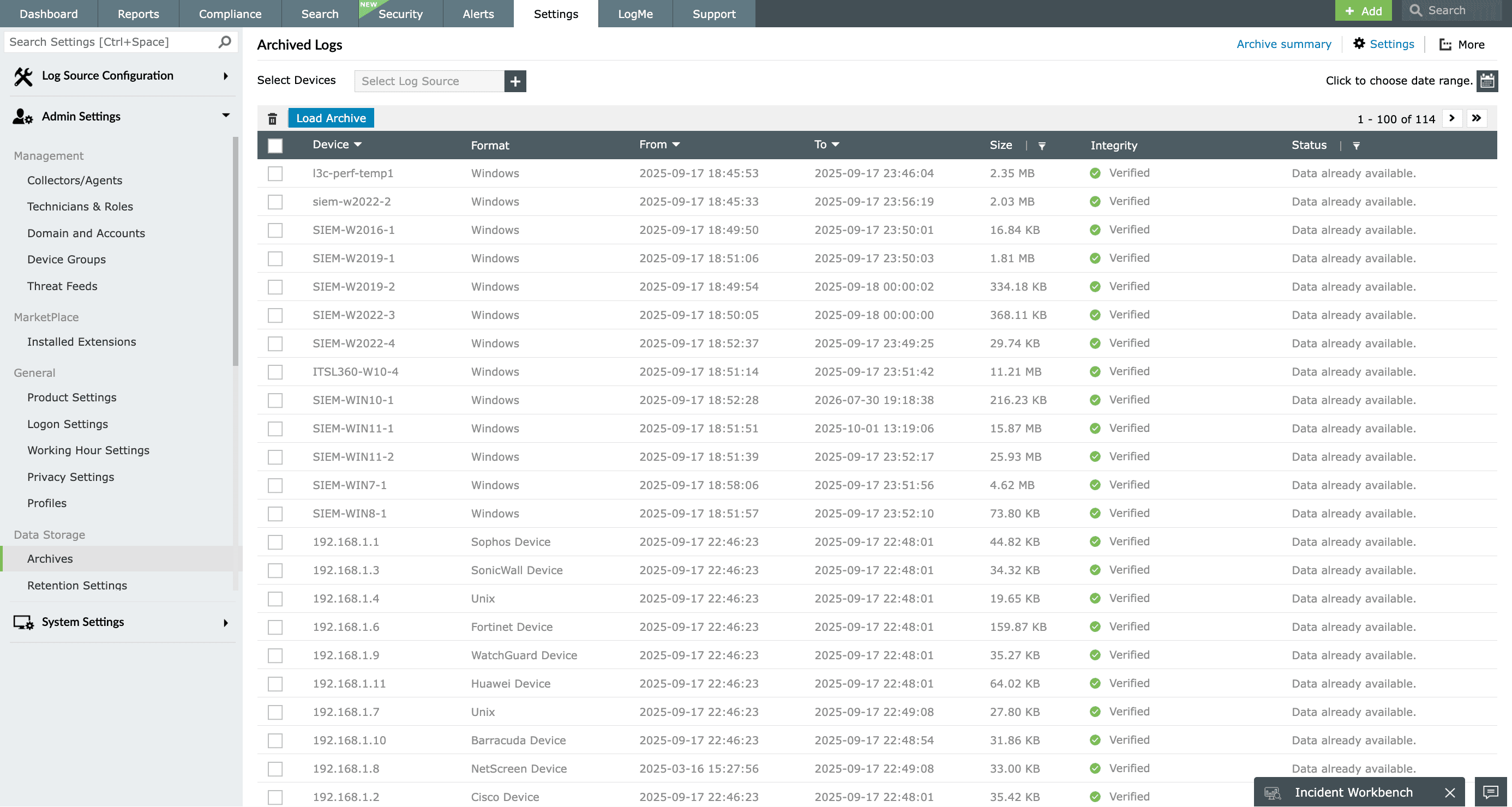
The processed log files should be archived periodically for internal, forensic, and IT regulatory compliance requirements. EventLog Analyzer servers as a log archival solution by automatically and securely archiving the event log and syslog data collected from the enterprise log sources.
This log management software securely stores the log by adopting encryption, hashing, and time stamping techniques to make the log archives tamper proof and ensure its integrity. The log files are archived and easily retrievable based on their time of creation, size details, and the device information. You can also configure the log archival interval and storage location based on your requirement or choose to disable log archival completely.

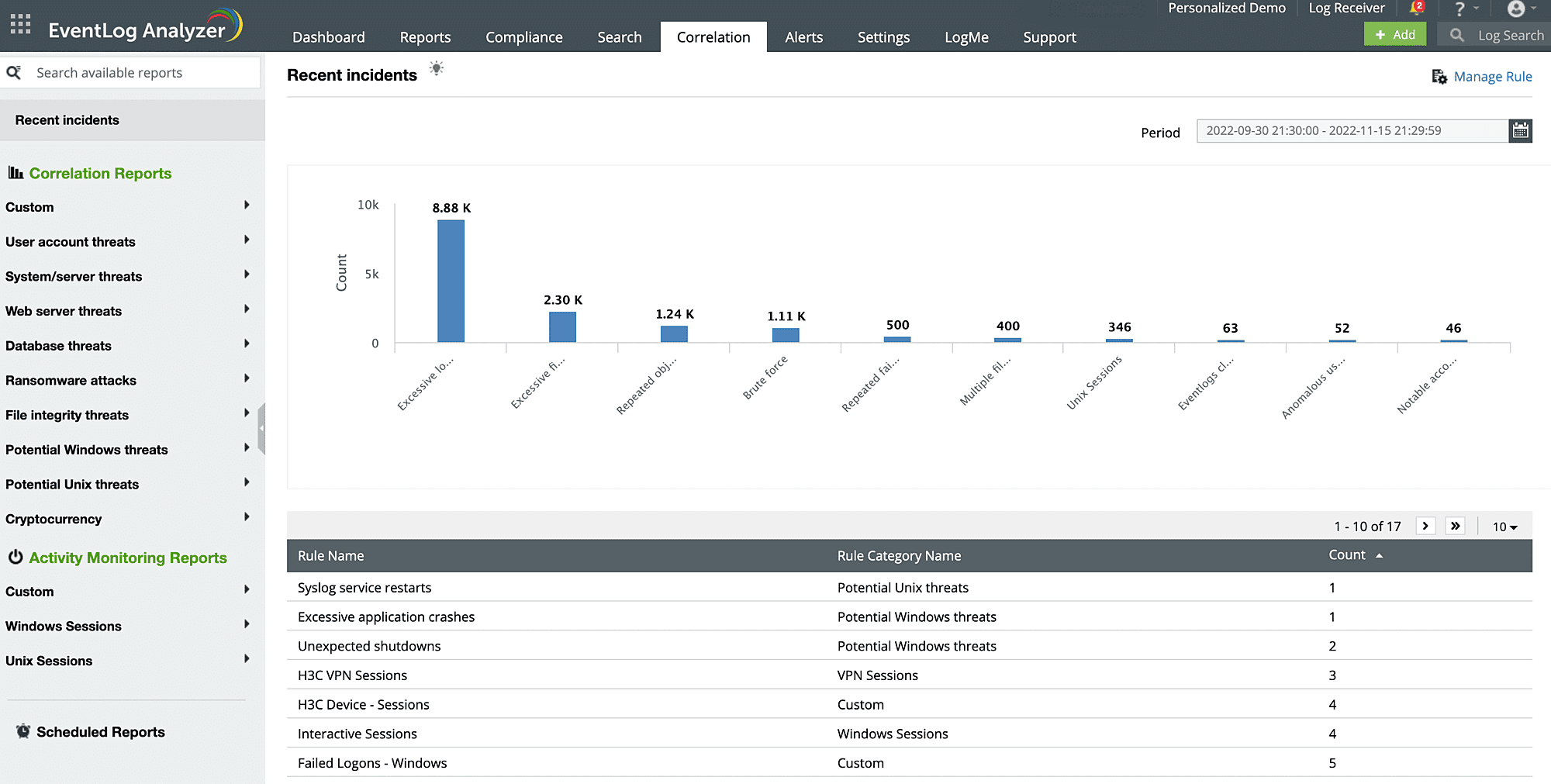
Your enterprise logs need to be analyzed to get a full picture of the network security events. This log analyzer tool correlates data from across multiple devices to provide a comprehensive view of your network events. The log correlation feature detects and alerts you on real-time security attacks such as ransomware attacks, brute force attempts, malware installations, SQL injections, unauthorized backup activities, etc.
EventLog Analyzer's threat intelligence console with built-in threat IP database and STIX/TAXII feed processor identifies malicious inbound and outbound traffic, instantly blocks them from interacting with the network through automated workflow profiles, and mitigates attack attempts effectively. You can also detect malicious activities such as insider attacks, privilege escalations, and unauthorized modifications to sensitive data.
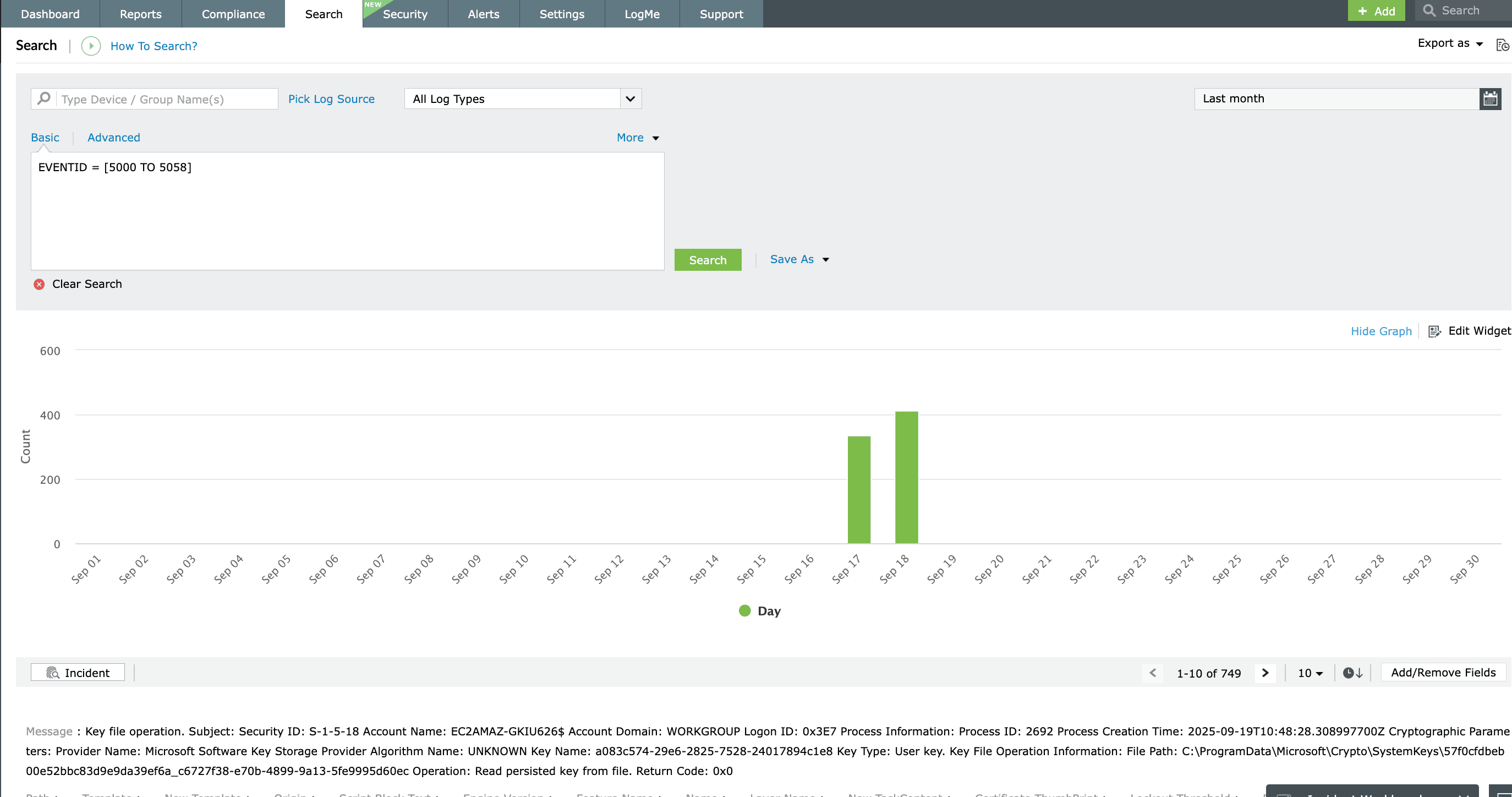
Drilling down raw logs relevant to any event of interest can be a cumbersome task, considering the enormity of logs generated every day. EventLog Analyzer's advanced log search engine provides both basic and advanced log search options that allow you to build search queries with wild-card, phrases, and Boolean operators for conducting log forensic and root cause analysis.
The intuitive search console provides click-based and range searches, simplifying the process of narrowing down to exact log entries within a few clicks. You can also conduct searches using event IDs, username, source, IP address, and event severity. The Search console offers the option to save the search query as an alert profile and then export the results as an incident report.
Reduce detection and response time to security incidents in your network with EventLog Analyzer's automated incident response and management system. The console allows you to set predefined workflow rules and send alerts regarding security events of interest. You can configure the solution to notify relevant administrators, create tickets from alerts automatically, and assign them to the right administrator based on the device or device group that generated the alert.
The log monitoring software also helps you visualize the log data with intuitive graphs, interactive dashboards, and predefined report templates. You can gain actionable insights and meet the security and auditing requirements of your organization with ease.

Reduce detection and response time to security incidents in your network with EventLog Analyzer's automated incident response and management system. The console allows you to set predefined workflow rules and send alerts regarding security events of interest. You can configure the solution to notify relevant administrators, create tickets from alerts automatically, and assign them to the right administrator based on the device or device group that generated the alert.
The log monitoring software also helps you visualize the log data with intuitive graphs, interactive dashboards, and predefined report templates. You can gain actionable insights and meet the security and auditing requirements of your organization with ease.
Organizational networks can be complex, consisting of a large number of interconnected systems, applications, and devices. Each of these components generates a vast amount of log data, capturing detailed information about system events, user activity, and network traffic. The sheer volume of log data generated can make it challenging to manage and analyze effectively.
Log management is the process of collecting, analyzing, and storing log data generated by various systems and applications in an organization. The main purpose of log management is to enable IT and security teams to not only monitor and troubleshoot issues in their infrastructure, but to detect and respond to security incidents as well. It is vital to use a powerful log management tool to automate log collection, correlate network events, analyze logs, and respond to security events in real time.
Effective log management can help organizations improve system performance, reduce downtime, and enhance their security posture.
Choose EventLog Analyzer for advanced log management.
Get your free trial