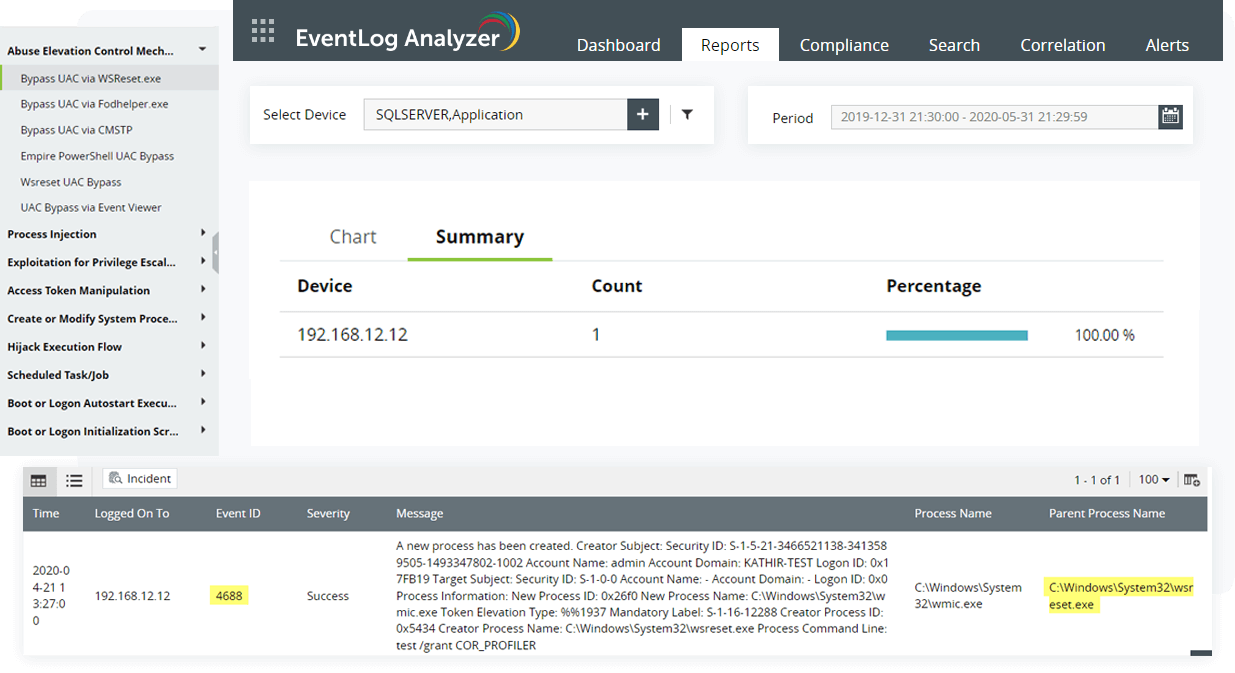
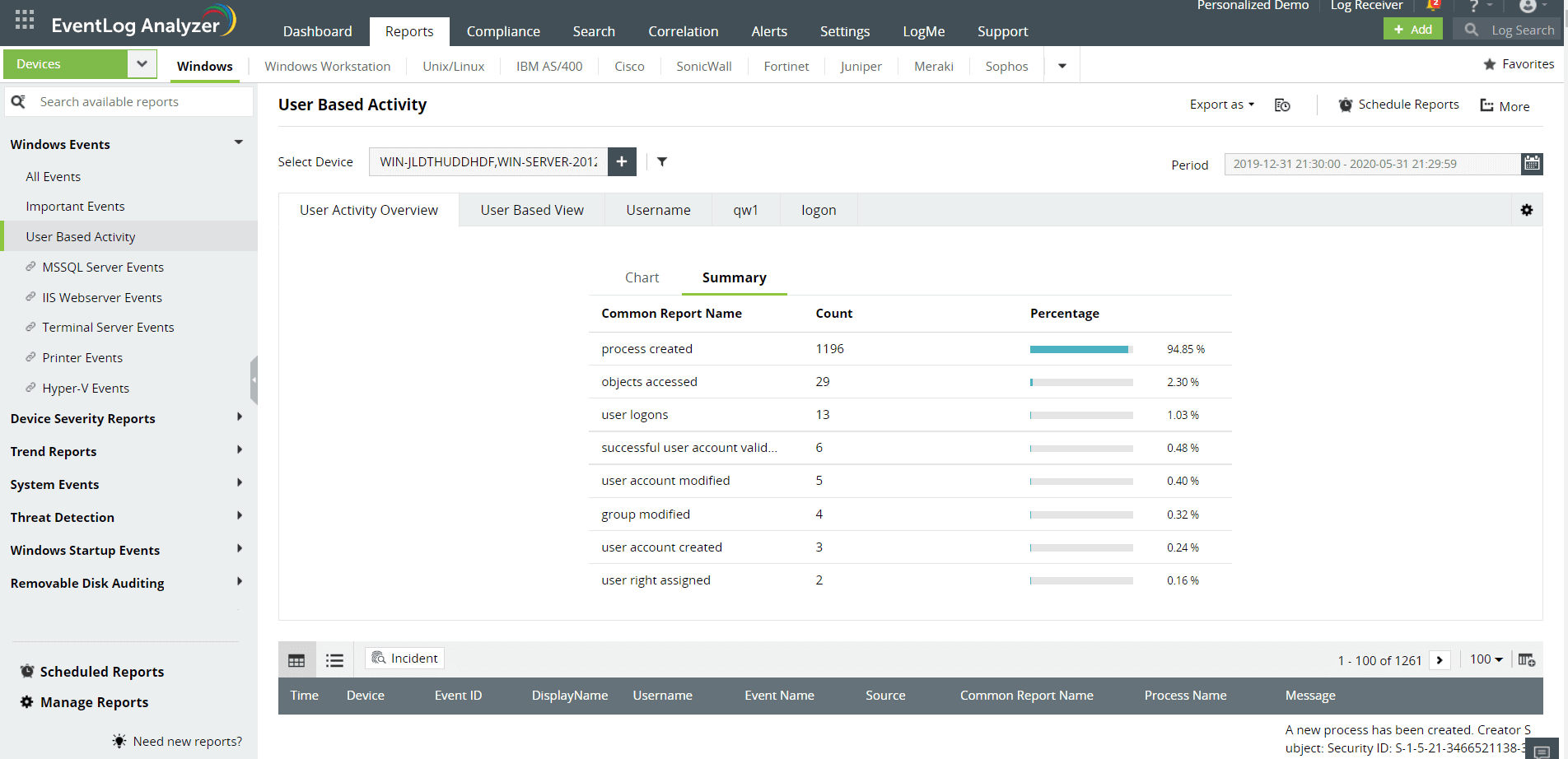
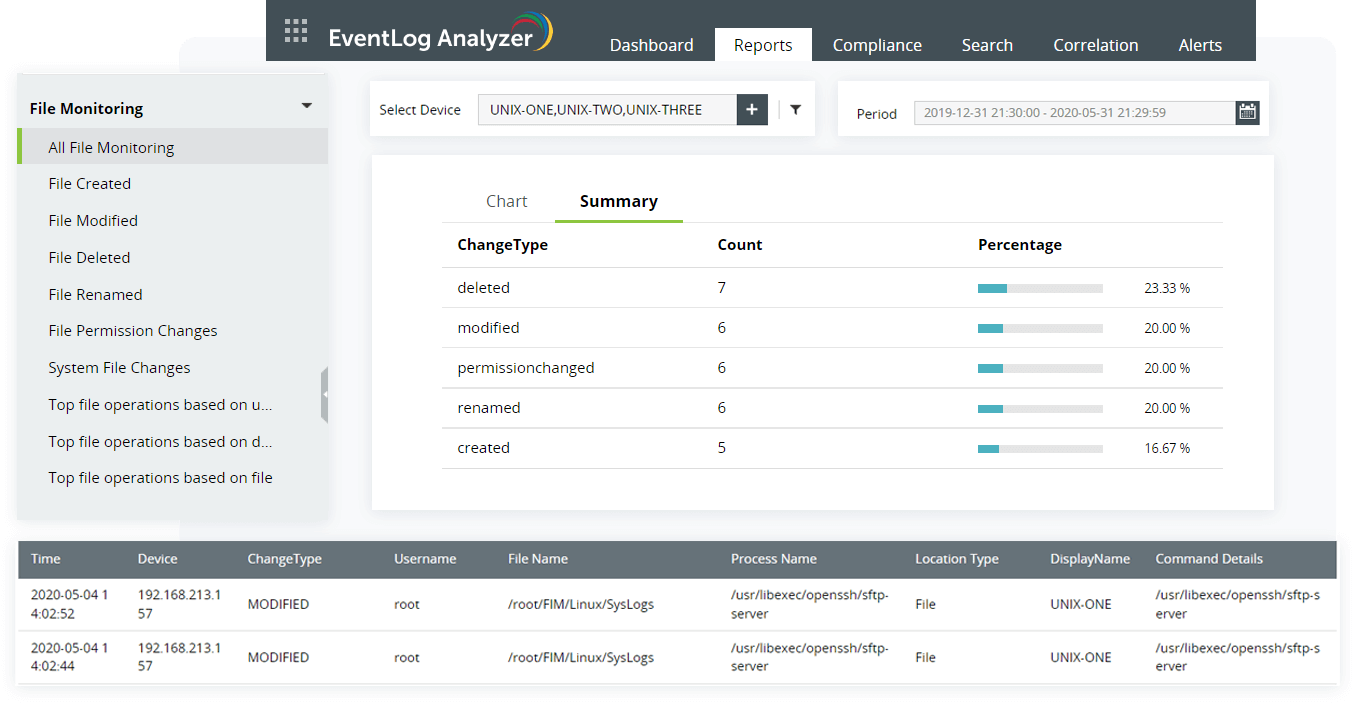
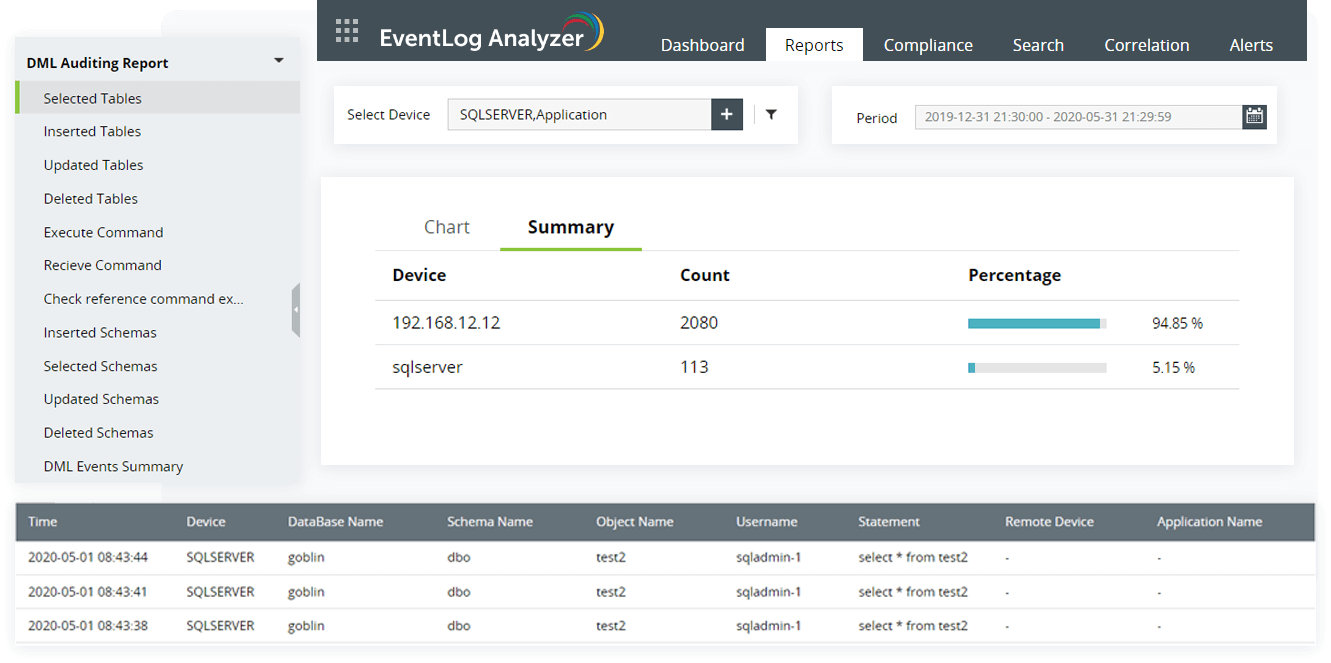
-
Credit Union of Denver has been using EventLog Analyzer for more than four years for our internal user activity monitoring. EventLog Analyzer provides great value as a network forensic tool and for regulatory due diligence. This product can rapidly be scaled to meet our dynamic business needs.Benjamin ShumakerVice President of IT / ISOCredit Union of Denver
-
The best thing, I like about the application, is the well structured GUI and the automated reports. This is a great help for network engineers to monitor all the devices in a single dashboard. The canned reports are a clever piece of work.Joseph Graziano, MCSE CCA VCPSenior Network EngineerCitadel
-
EventLog Analyzer has been a good event log reporting and alerting solution for our information technology needs. It minimizes the amount of time we spent on filtering through event logs and provides almost near real-time notification of administratively defined alerts.Joseph E. VerettoOperations Review Specialist
Office of Information SystemFlorida Department of Transportation -
Windows Event logs and device Syslogs are a real time synopsis of what is happening on a computer or network. EventLog Analyzer is an economical, functional and easy-to-utilize tool that allows me to know what is going on in the network by pushing alerts and reports, both in real time and scheduled. It is a premium software Intrusion Detection System application.Jim LloydInformation Systems ManagerFirst Mountain Bank