SQL injection (SQLi) is a prevalent attack technique where attackers use malicious SQL queries to access sensitive business information without proper authorization. To detect and mitigate SQLi attack, you need a comprehensive network security tool that analyzes and correlates log data from your web servers and databases. EventLog Analyzer, an SQL injection attack detection and mitigation tool, can alert you to the attack and quickly mitigate it before the data leaves your network.
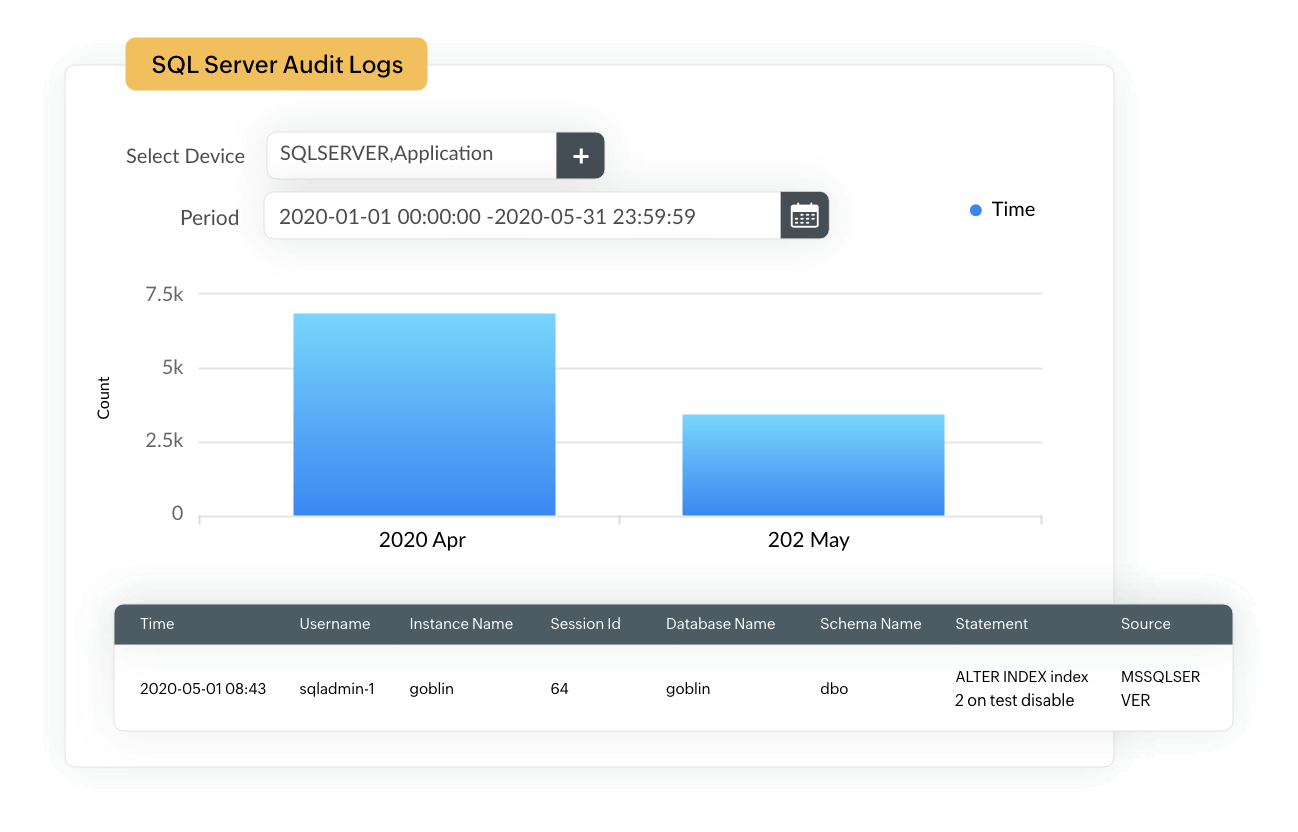
Protect your network from data breaches by detecting traces of SQL injection attacks through real-time monitoring of database and web server activities. EventLog Analyzer serves as an SQL injection prevention tool and runs regular audit trails on web server and database server activities. You get in-depth insights into server usage, access patterns, permission changes, activity trends, and attack attempts in the forms of graphs and reports.
EventLog Analyzer's attack reports provide information on SQL injection attack attempts detected on your IIS and Apache web servers. Our solution also comes with prebuilt alert profiles that can be configured to trigger instant alerts when such attacks are detected.
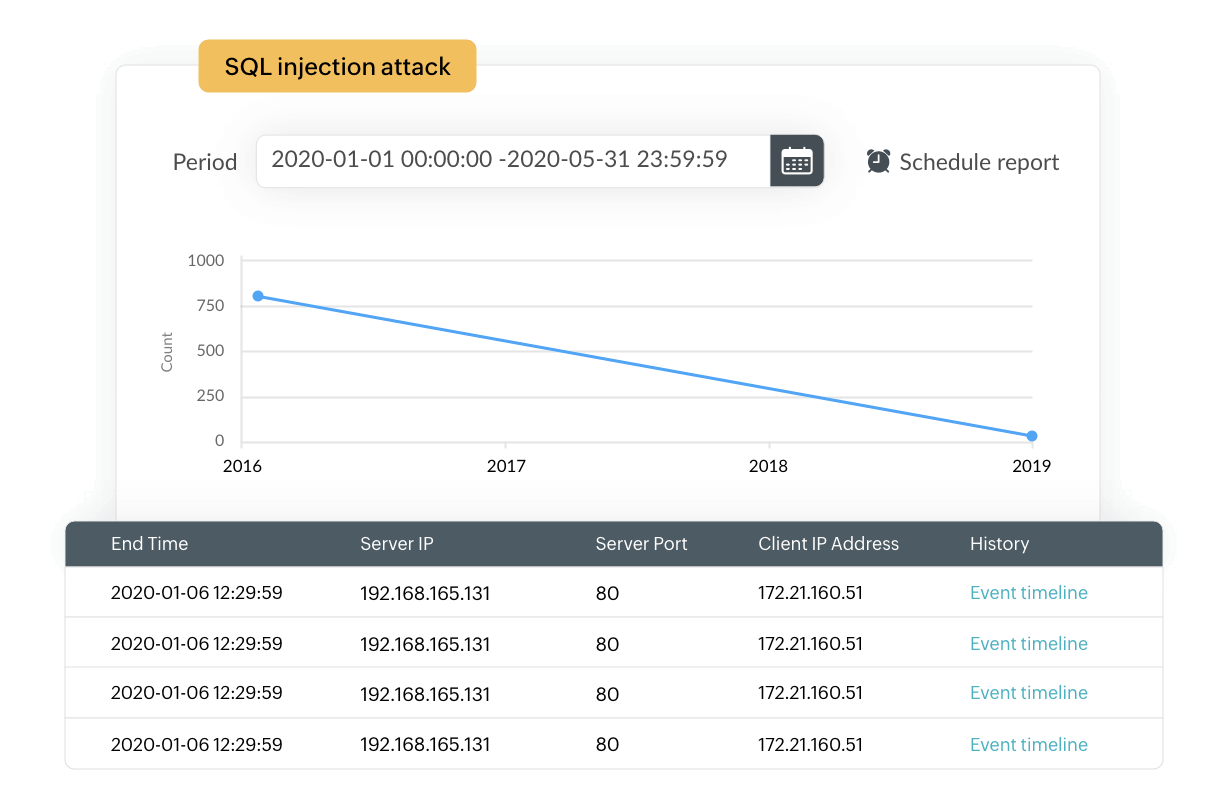
The powerful correlation engine of EventLog Analyzer is built to detect signs of suspicious activities in the network based on predefined correlation rules. The incident timeline report for every rule gives detailed insights into the sequence of events that caused the solution to trigger the correlation alert. This will give you a clear understanding of where the attack originated and how the attacker progressed through the network.
Our solution facilitates this breakdown with predefined correlation rules that are formulated to spot attack vectors in common cyberattacks, including SQLi. EventLog Analyzer's correlation rules encompass database events, web server events, Microsoft SQL Server security incidents, Oracle security incidents, IIS web server events, and Apache web server events for SQLi detection. You can configure the threshold limit and the time span of SQLi attempt logs from the same device type and name. Once the limit is reached, the solution triggers an alert.
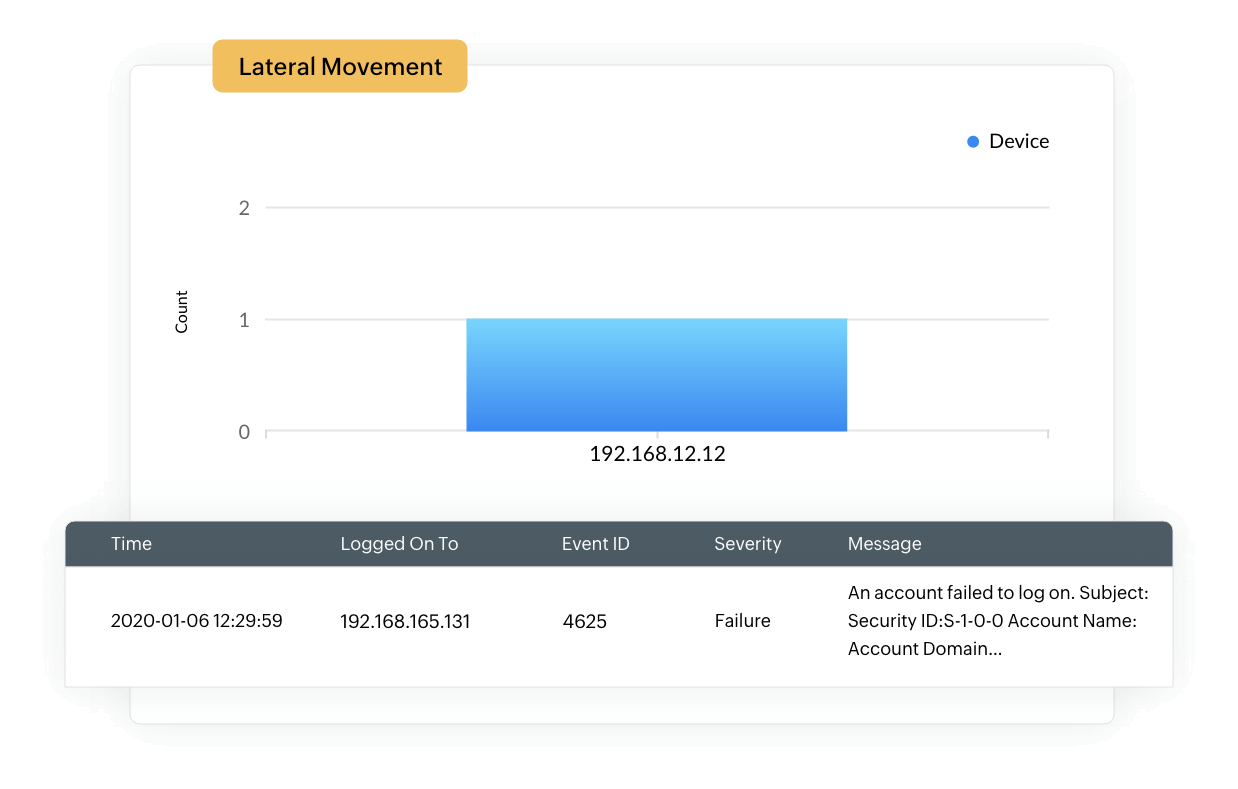
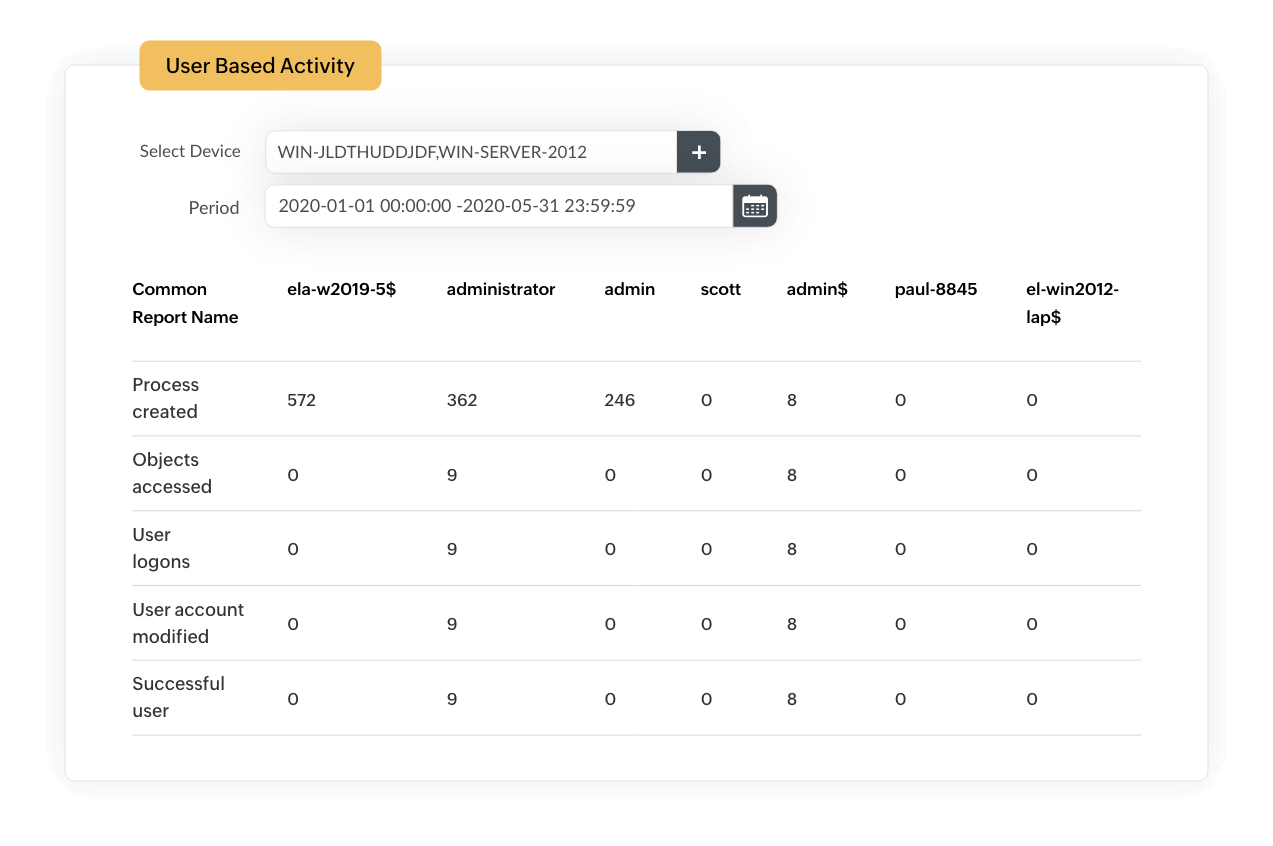
If an attacker gains access to the network, they tend to move laterally, access database servers with system privileges, and use these permissions to enter other sensitive systems in the network. EventLog Analyzer uses its threat intelligence and correlation capabilities to analyze the behavioral patterns of specific users. If a user logs on outside of work hours, changes access permissions, and modifies or exfiltrates sensitive data, our SQLi attack mitigation tool raises an alert to drive your attention to this sequence of actions.
Additionally, our solution's integrity audit reports monitor for column integrity in database tables. If you mark sensitive columns in the table, EventLog Analyzer will raise an alert when the values in that column are altered.

If an attacker gains access to the network, they tend to move laterally, access database servers with system privileges, and use these permissions to enter other sensitive systems in the network. EventLog Analyzer uses its threat intelligence and correlation capabilities to analyze the behavioral patterns of specific users. If a user logs on outside of work hours, changes access permissions, and modifies or exfiltrates sensitive data, our SQLi attack mitigation tool raises an alert to drive your attention to this sequence of actions.
Additionally, our solution's integrity audit reports monitor for column integrity in database tables. If you mark sensitive columns in the table, EventLog Analyzer will raise an alert when the values in that column are altered.
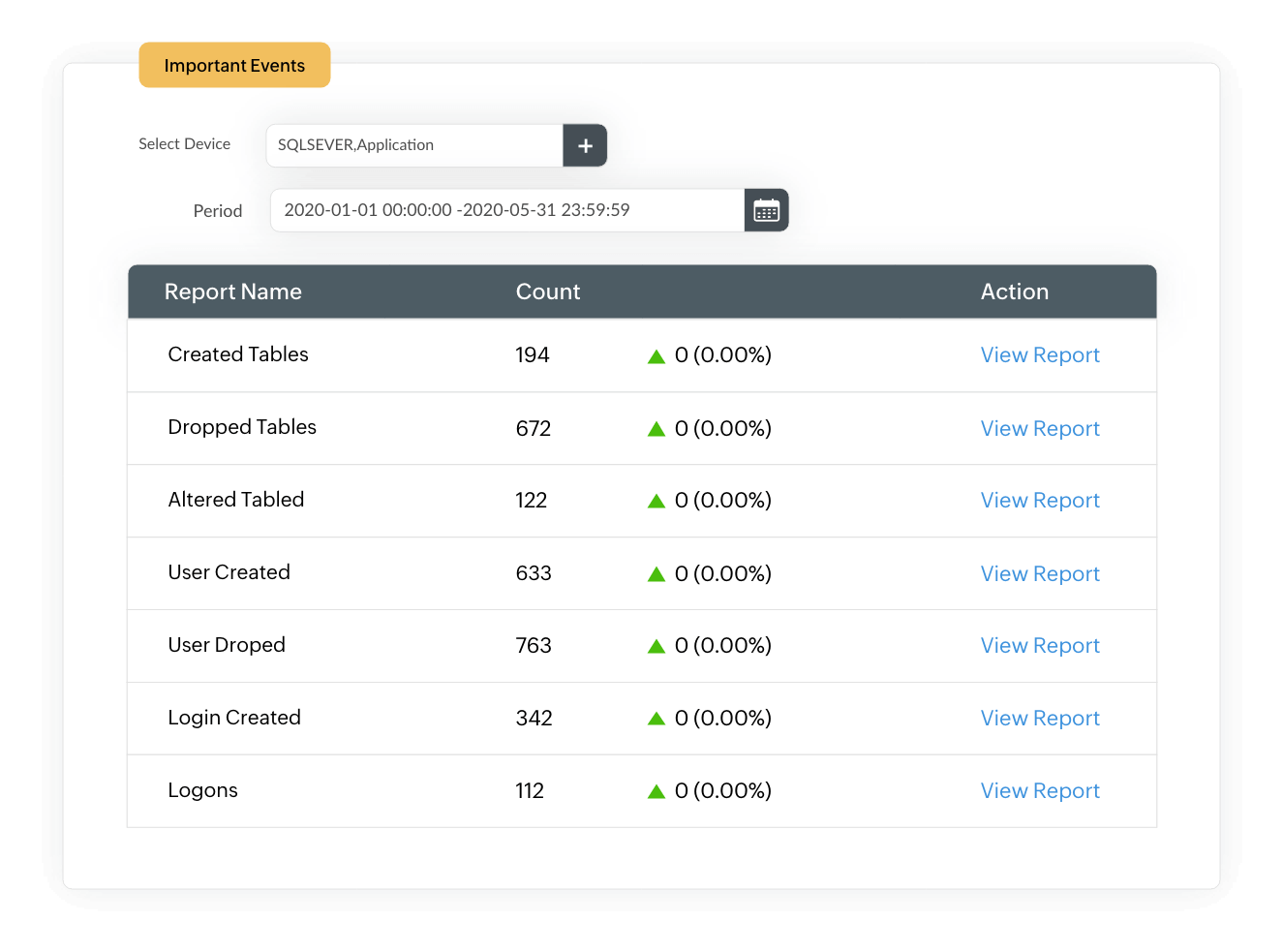
If an attacker gains unrestricted access to confidential data on your SQL severs, they can tamper with the existing data by altering, adding, and deleting entries or dropping entire tables. With EventLog Analyzer, you can audit DDL and DML activities to track functional- and structural-level changes in your databases.
The exclusive audit trails on your Microsoft SQL servers and other databases provide insights into additions, deletions, or modifications to tables, views, procedures, triggers, schemata, and data. They also present the data intuitively in the form of graphical reports to help administrators perform quick forensic analysis when required.
If an attacker gains unrestricted access to confidential data on your SQL severs, they can tamper with the existing data by altering, adding, and deleting entries or dropping entire tables. With EventLog Analyzer, you can audit DDL and DML activities to track functional- and structural-level changes in your databases.
The exclusive audit trails on your Microsoft SQL servers and other databases provide insights into additions, deletions, or modifications to tables, views, procedures, triggers, schemata, and data. They also present the data intuitively in the form of graphical reports to help administrators perform quick forensic analysis when required.
Identify attack attempts at the first sign of compromise and automate remediation with predefined workflows to mitigate security attacks effectively.
Many organizations offer multiple dynamic, data-driven web applications to their users. These applications are dependent on databases for storing and protecting data. This can include business-critical data, confidential data, customer records, financial records, and the privileged or personal information of an organization. Generally, these applications use standard SQL queries, which are formed based on user inputs, to communicate with the database.
An SQL injection attack, also known as SQLi, is a common attack that threatens databases through web applications. A malicious user with sufficient knowledge of SQL can manipulate the inputs provided in the application to retrieve data to which they should not have access. An organization can face serious privacy and legal implications if data is stolen via a vulnerability in its application.
While applications usually run checks on the inputs to ensure a data leak does not happen, sophisticated attackers may still find vulnerable points in the application. Regularly auditing the database server and the web server that hosts the applications is therefore necessary to make sure the data is always protected. EventLog Analyzer's predefined reports and alerts make this audit and security process easy.
An SQL injection attack is a type of security exploit that allows hackers to manipulate vulnerabilities in a network's SQL database. You can minimize the risk of being a victim of this attack by following several SQL injection prevention best practices:
EventLog Analyzer provides out-of-the-box SQLi correlation rules for the following:
Additionally, you can create custom correlation rules to monitor any other specific events across your network.