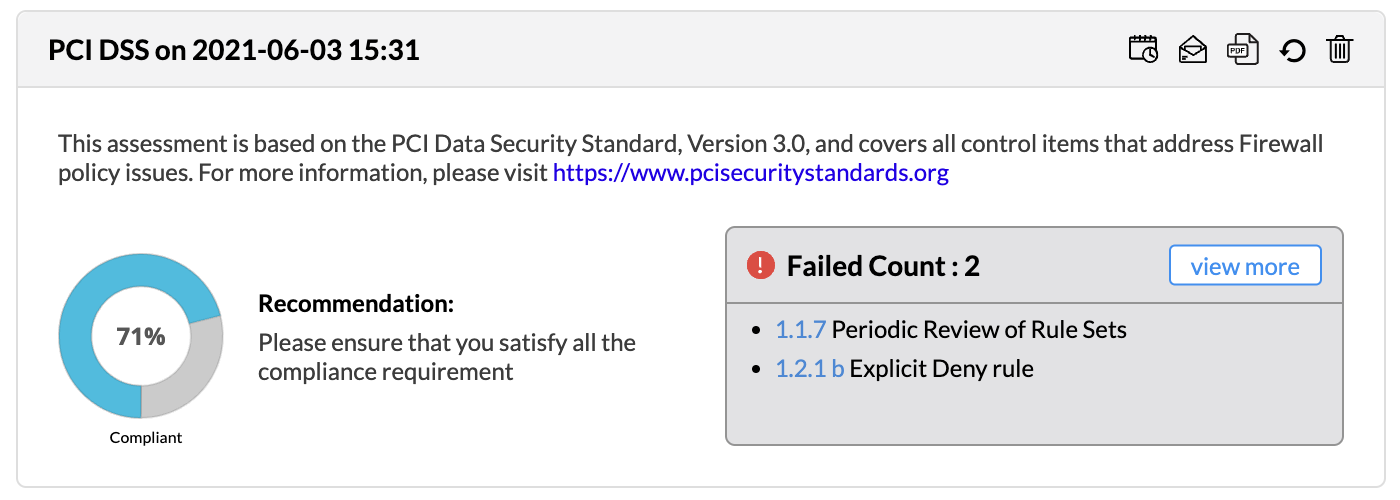
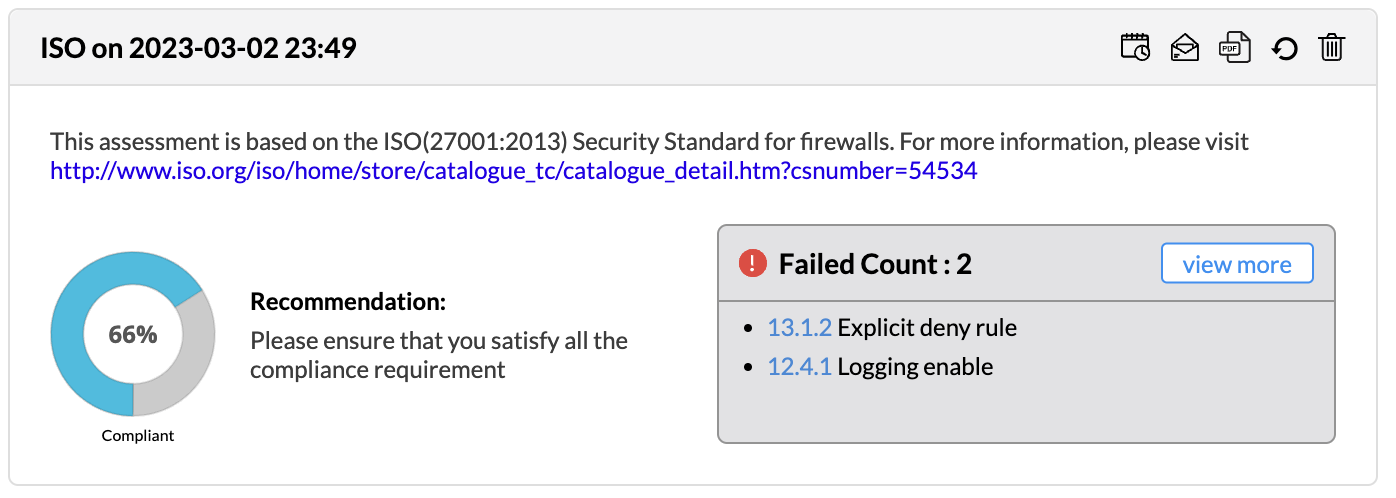
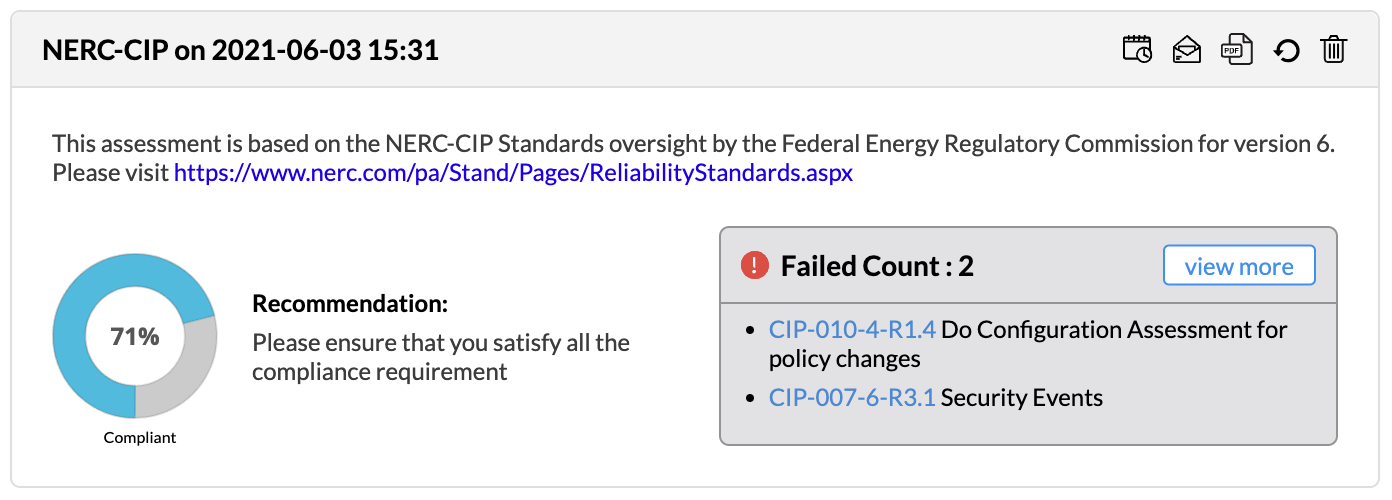
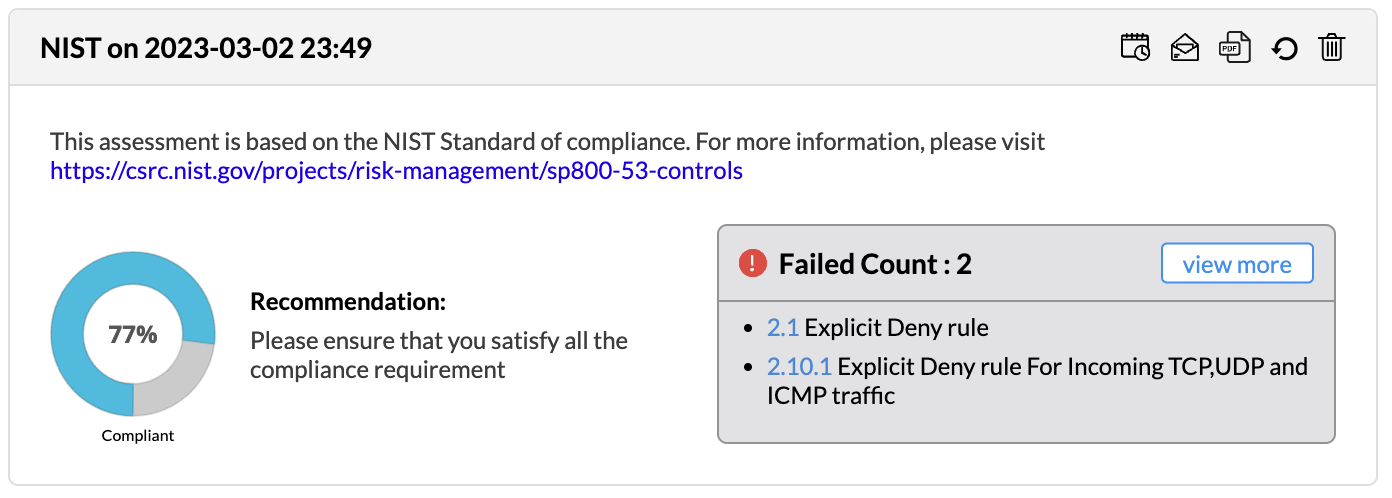
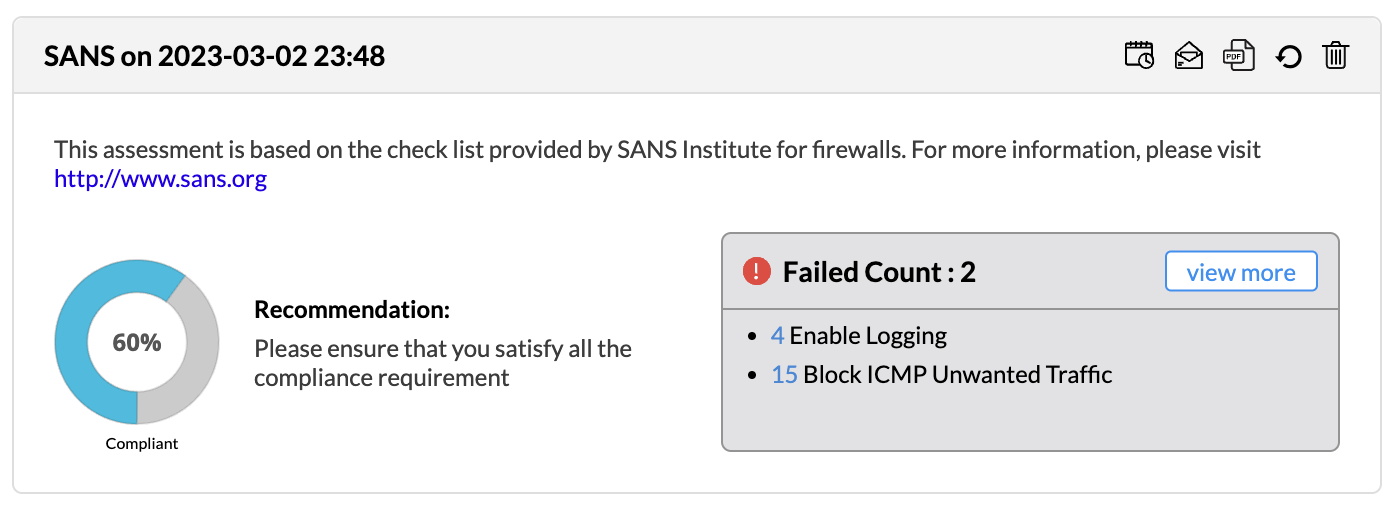
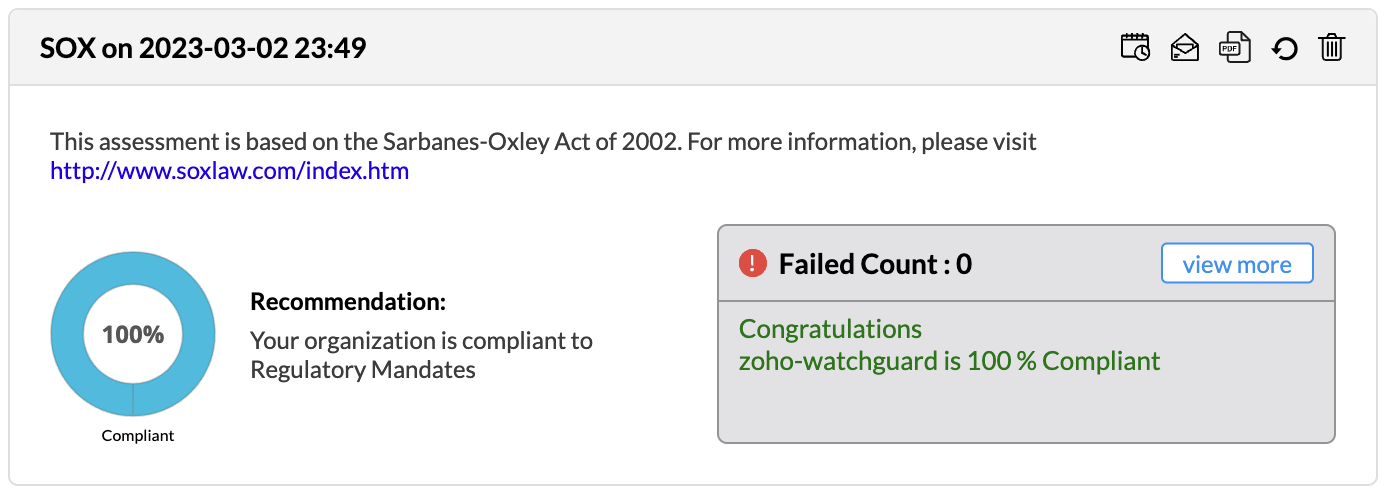
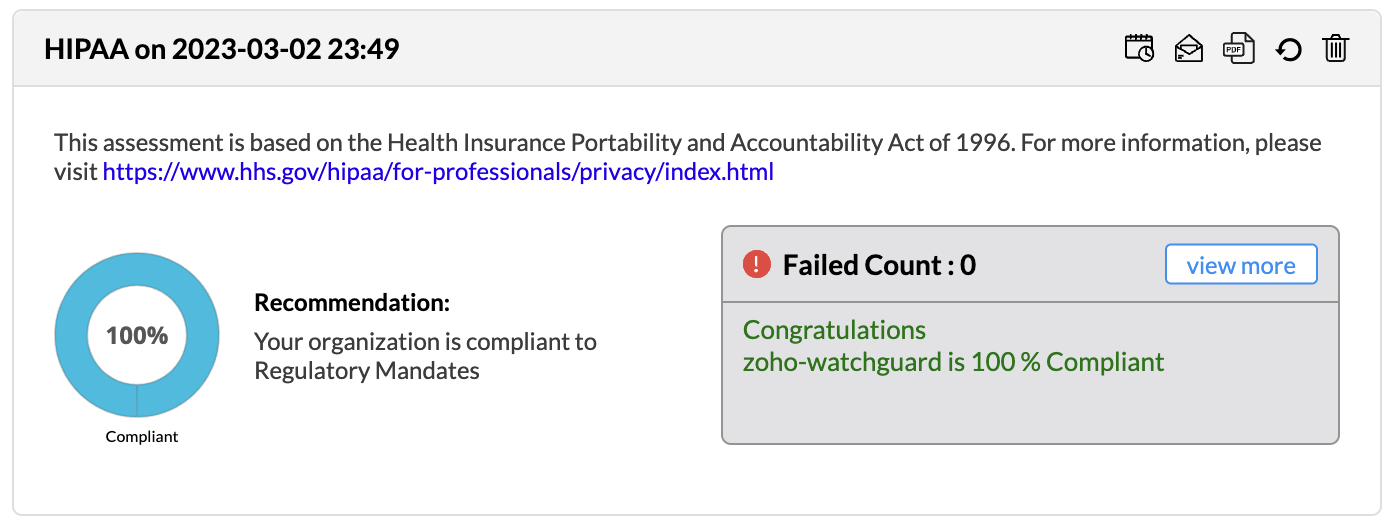
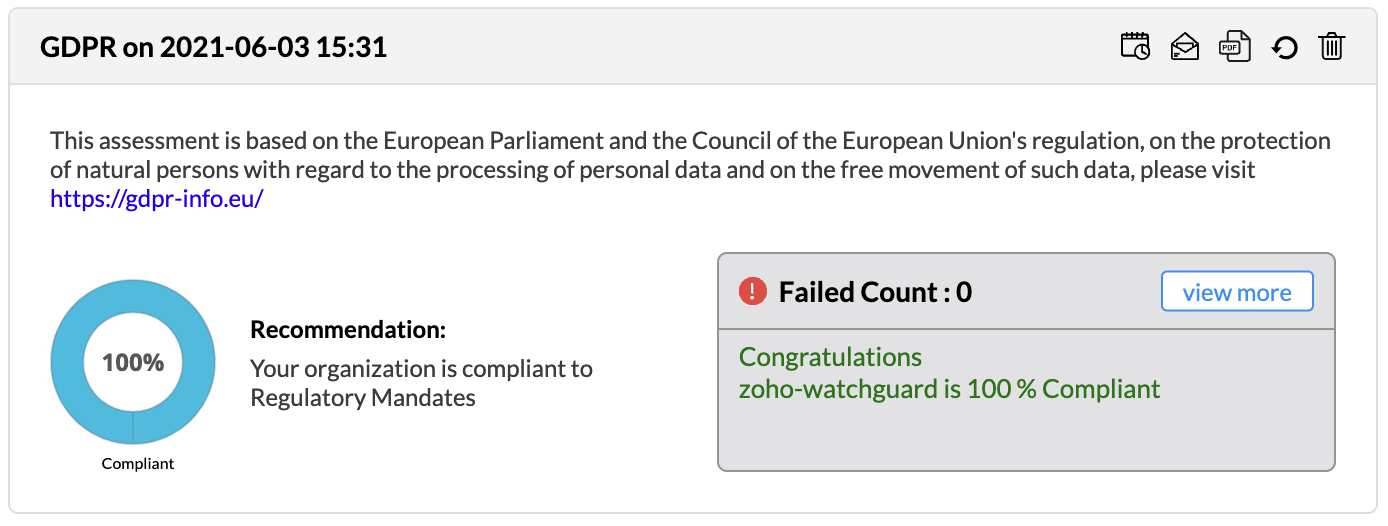
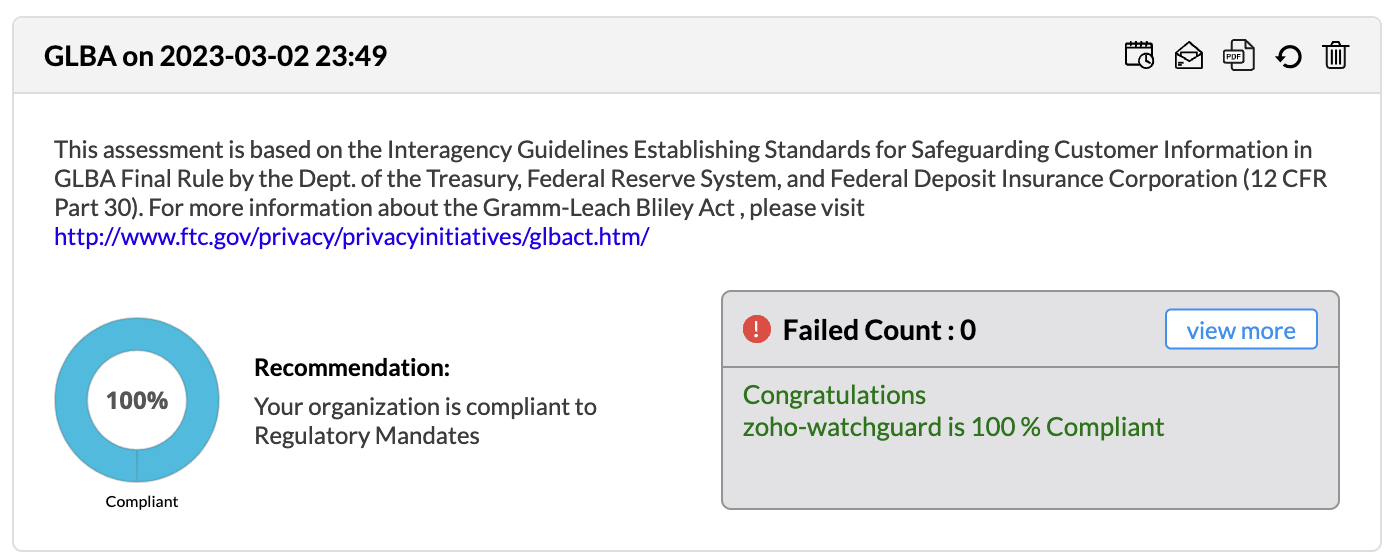
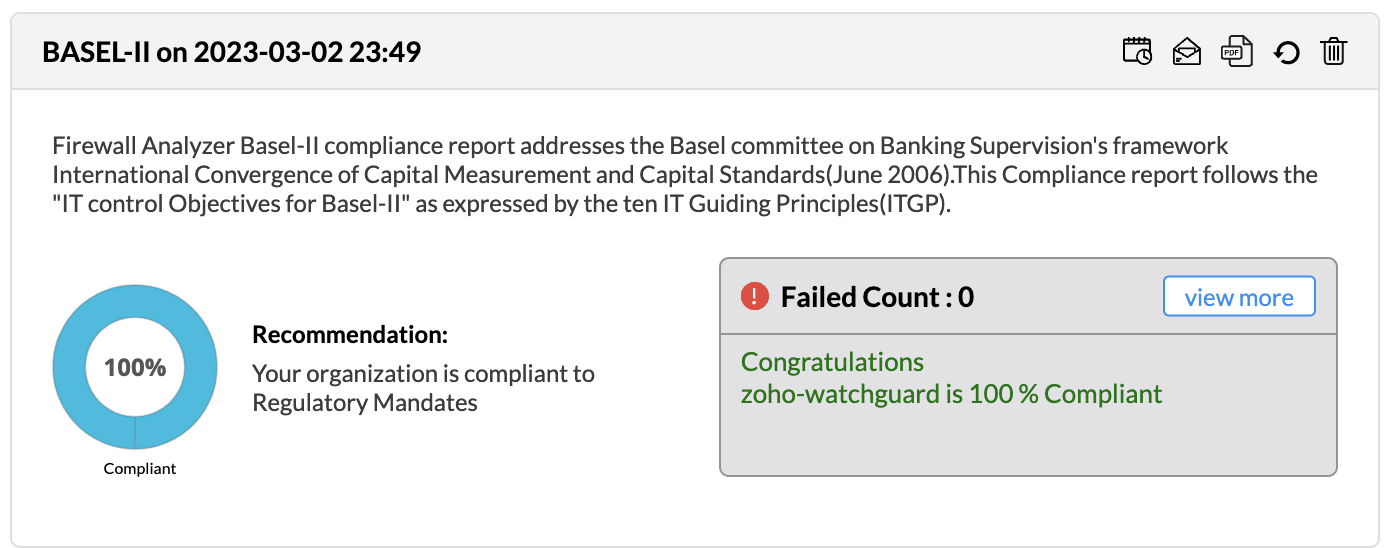
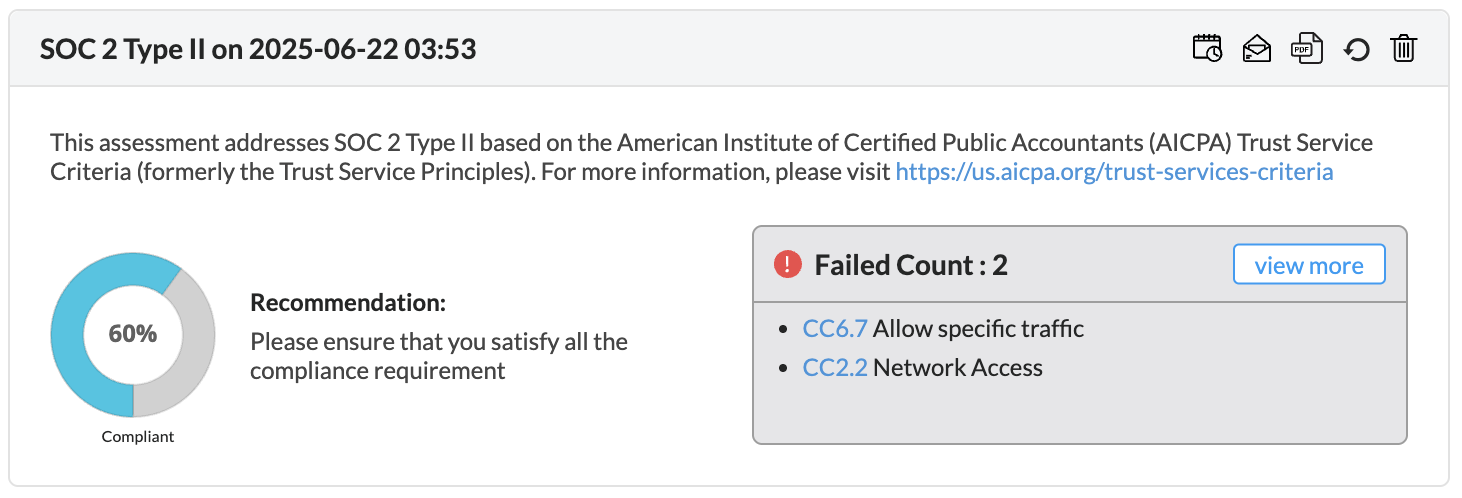
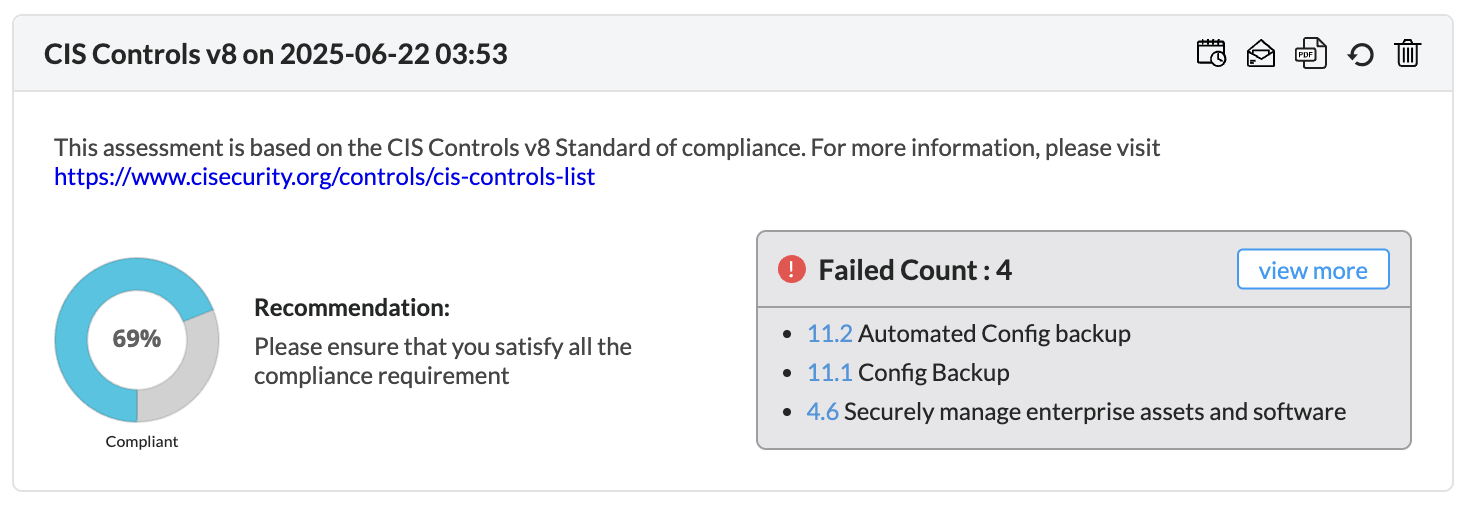
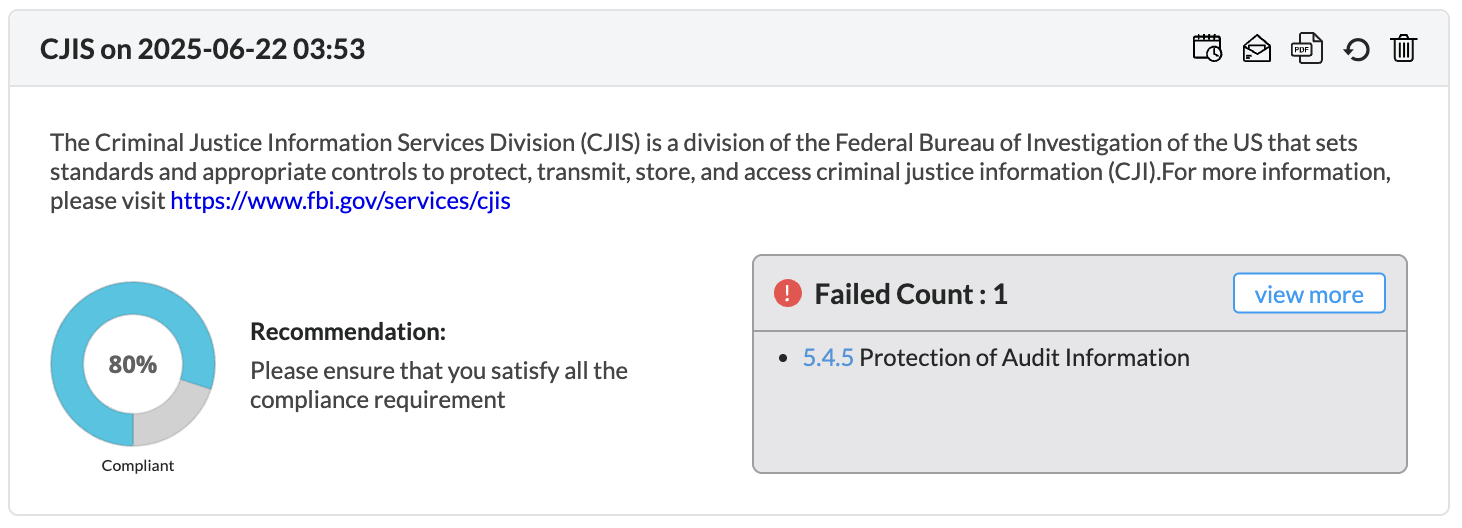
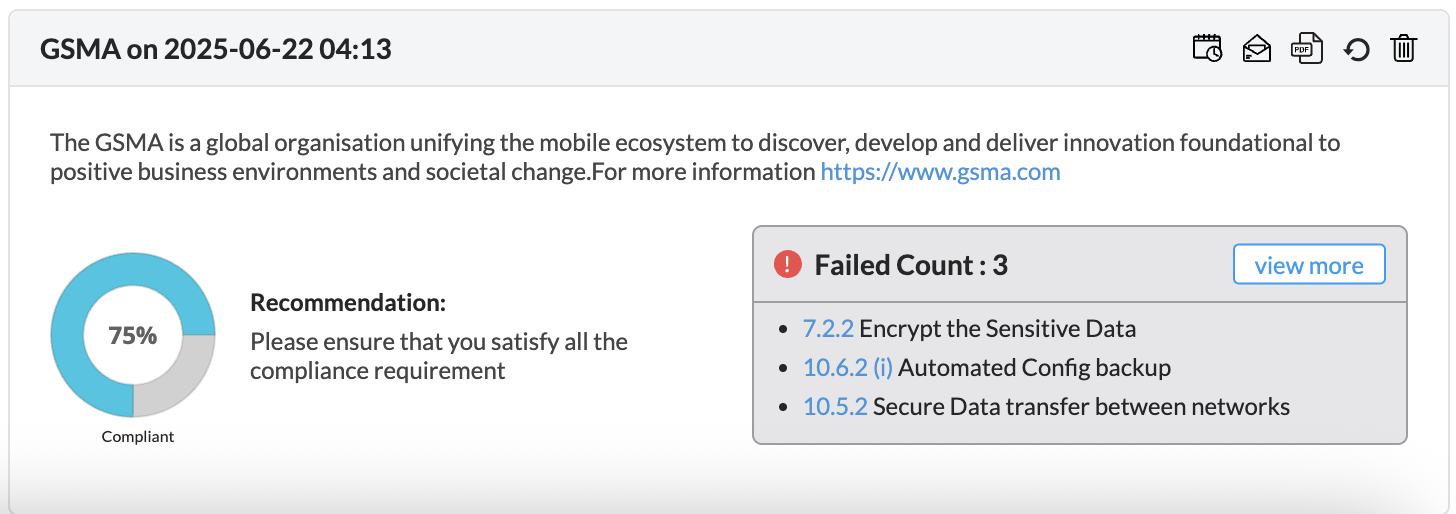
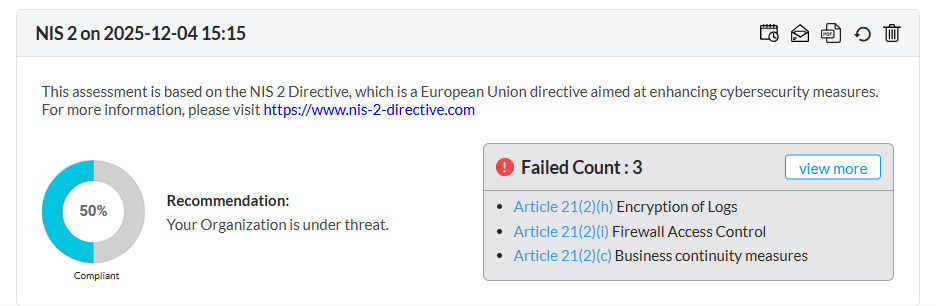
Firewall Analyzer offers an exhaustive set of Firewall compliance reports that help to address the various regulatory audit requirements. It presents the % of compliance in a Pie chart graph and the respective compliance act sections which are met.
Refer the list of devices for which the Standards compliance report is supported.
The following regulatory compliance reports are displayed in Pie chart graph of % complied and the details are listed in the table
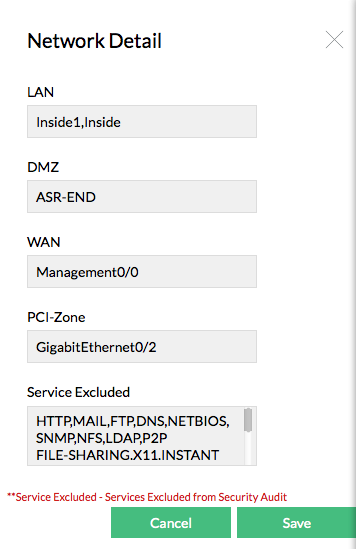
Click Edit Settings and configure the Network Detail for the particular firewall with the menu.
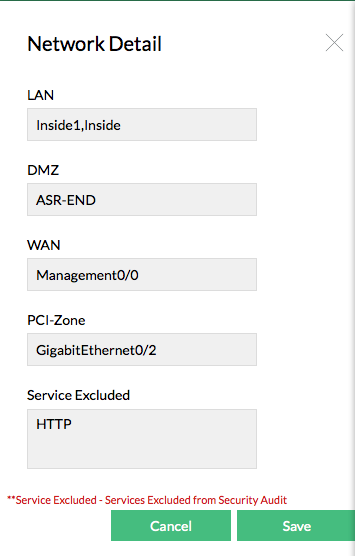
You have to configure the settings to ensure that the compliance reports are generated properly for rules governing the interfaces and services excluded.
| Note: | If the Services Excluded are configured, it will be dropped from audit. It is applied globally across all Firewalls and all the compliance reports generated for them |
In two other places of PCI-DSS compliance report, you can mark the Services Excluded as false positives. From here, it will be added to the exclusion list and will be removed from audit. This also will be applied globally across all the compliance reports of all firewalls.
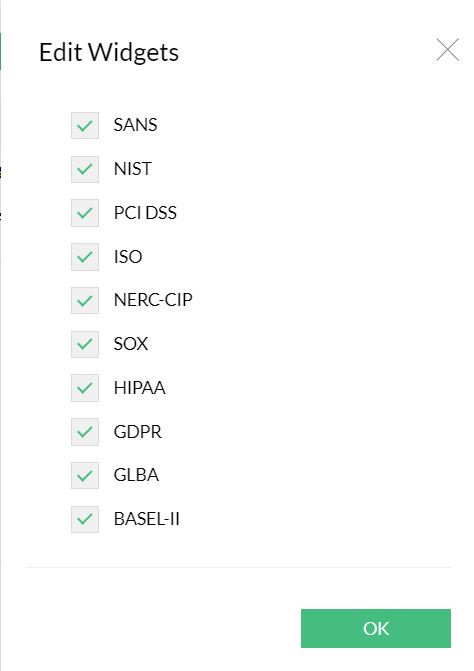
The compliance reports are displayed as widgets and they can be edited with Edit Widgets menu. The widgets can be enabled or disabled to be displayed in the screen.
All the compliance reports can be scheduled from the widget to generate reports automatically. The individual compliance report can be exported to PDF format. The Refresh icon regenerates the compliance report. The individual compliance report widget can be removed from display. The widget can dragged and dropped to any position in the screen.
Thank you for your feedback!