Let's Encrypt Integration with Password Manager Pro
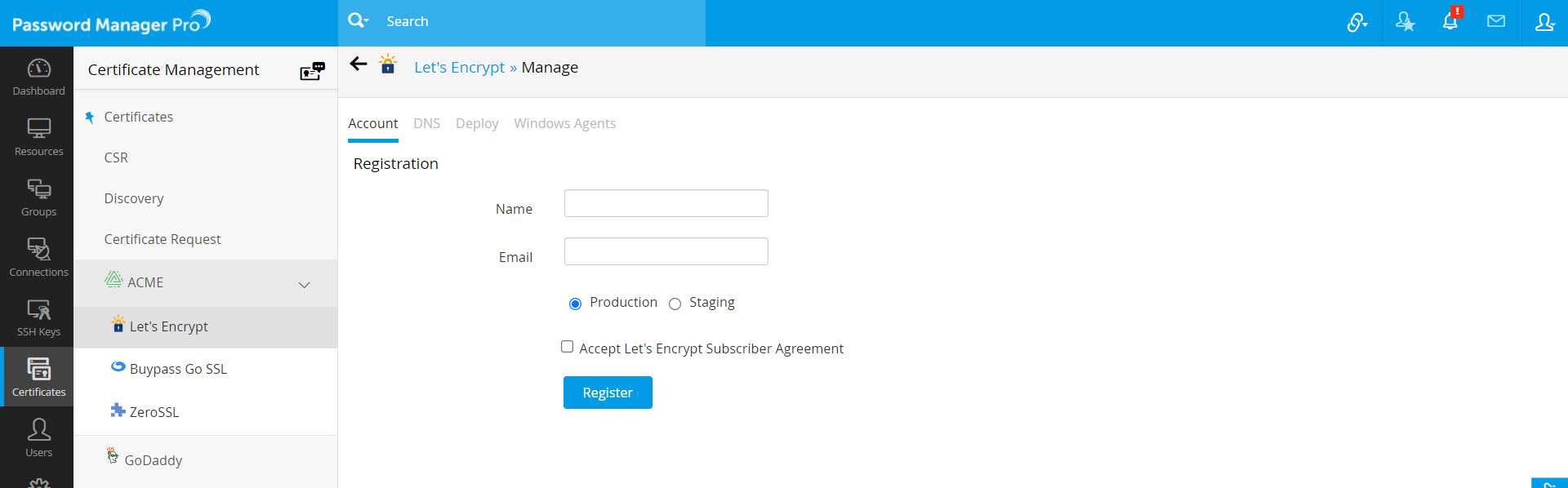
- Navigate to Certificates >> Acme >> Let's Encrypt >> Manage.
- Under Account tab, click New Registration.
- In the UI that opens, provide an account name and specify a valid email address. Choose Production or Staging, based on your requirement.
- Accept the Let's Encrypt Subscriber Agreement by enabling the check-box.
- Click Register.
- An account with Let's Encrypt is created.
1. Overview
Maintaining a threat-free network requires much more than just securing your domains with SSL certificates. For organizations that deal with a large SSL environment, the process of purchasing, deploying and renewing SSL certificates often proves to be cumbersome, time-consuming and has hardly been straightforward. Oversight, manual errors, improper configuration, weak ciphers, and expiration often lead to downtimes, compliance issues and security breaches. Certificate life-cycle management is a practice that streamlines certificate management process by automating acquisition, issue, deployment, re-issue, renewal and revoking of certificates. Password Manager Pro facilitates end-to-end certificate life-cycle management for your public facing websites by integrating with the renowned open Certificate Authority, Let's Encrypt. This means you can procure domain validated certificates from Let's Encrypt for your public domains, deploy, track, request alerts on expiry, renew certificates; everything done entirely from the product interface.
You can request, procure, deploy, monitor, track and renew certificates from Let's Encrypt CA directly from Password Manager Pro interface.
Before you proceed with the integration, complete the following step as a prerequisite:
Prerequisite
Add the following base URL and port as an exception in your firewall or proxy to ensure Password Manager Pro is able to connect to Let's Encrypt's CA Services.
Production URL: https://acme-v02.api.letsencrypt.org/directory
Staging URL: https://acme-staging-v02.api.letsencrypt.org/directory
Port: 443
Follow the step-by-step procedure below to integrate Let's Encrypt with Password Manager Pro:
2. Create a Let's Encrypt Account
The first step in requesting for certificates from Let's Encrypt CA is creating an account with Let's Encrypt. This is a one-time process and can be done from the Password Manager Pro interface itself.
To create Let's Encrypt account, follow the below steps:
Once your account is created, you can update the account email address, delete it from Password Manager Pro, or deactivate the account entirely. Please note that deleting the account only removes it from Password Manager Pro. Even if you delete the account here, it will still be active in the Let's Encrypt portal. To add the same account back to Password Manager Pro, export the key and use the Add Account option with the same details used before. However, if you select the Deactivate option while deleting the account, then the Let's Encrypt account will be removed completely and you cannot add it back to Password Manager Pro with the same details.
- Account creation privileges are available only for administrators and only one Let's Encrypt account can be created from Password Manager Pro.
- Click the Update Mail ID option in the top bar to edit the email ID associated with the Let's Encrypt user account.
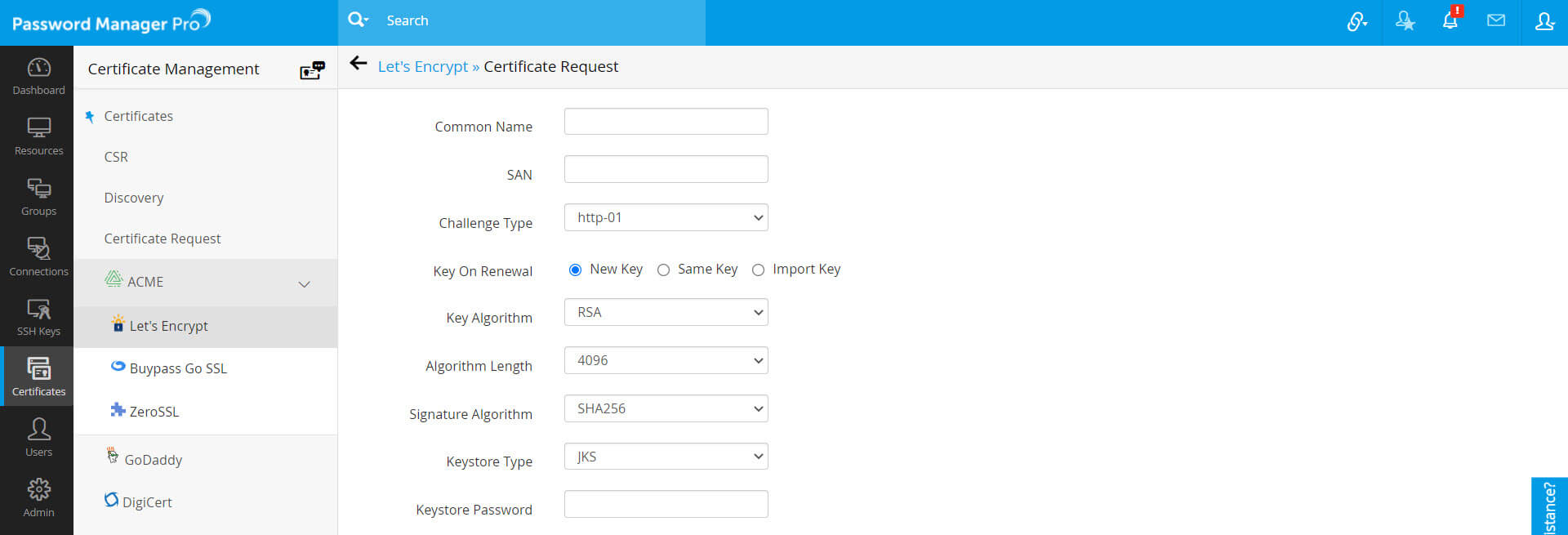
- Navigate to Certificate >> Let's Encrypt >> Certificate Request.
- Fill in the domain name, choose the Key Algorithm, Algorithm Length, Signature Algorithm, Keystore Type, enter the Keystore Password and click Create.
- For dns-01 challenge type, you can choose and assign a DNS account from the drop-down if you have already configured your DNS credentials. This will be used for automatic challenge verification for all the domains specified in the request.
- Also, you have options to change the private key whenever the certificate is renewed.
- If you need to change the key, use New Key. This option will generate a new key every time the certificate is renewed.
- If you want to retain the same key on renewal, use the Same Key option.
- To use your own key, use the Import Key option. This key will be used for the first time when the certificate is generated and also for subsequent renewals.
- Navigate to Let's Encrypt >> Manage.
- Switch to the DNS tab.
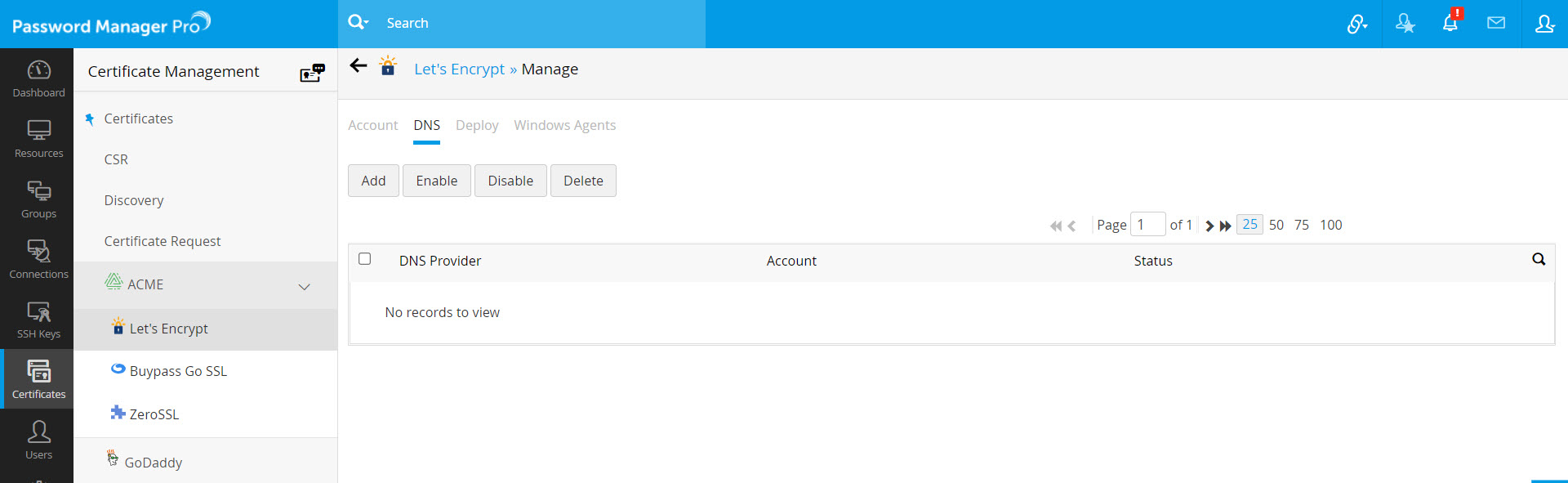
- Here, you can add a maximum of one DNS account for each DNS provider supported. Password Manager Pro currently supports automatic challenge verification for Azure, Cloudflare DNS, Amazon route 53 DNS, RFC2136 DNS update (nsupdate), ClouDNS, GoDaddy DNS.
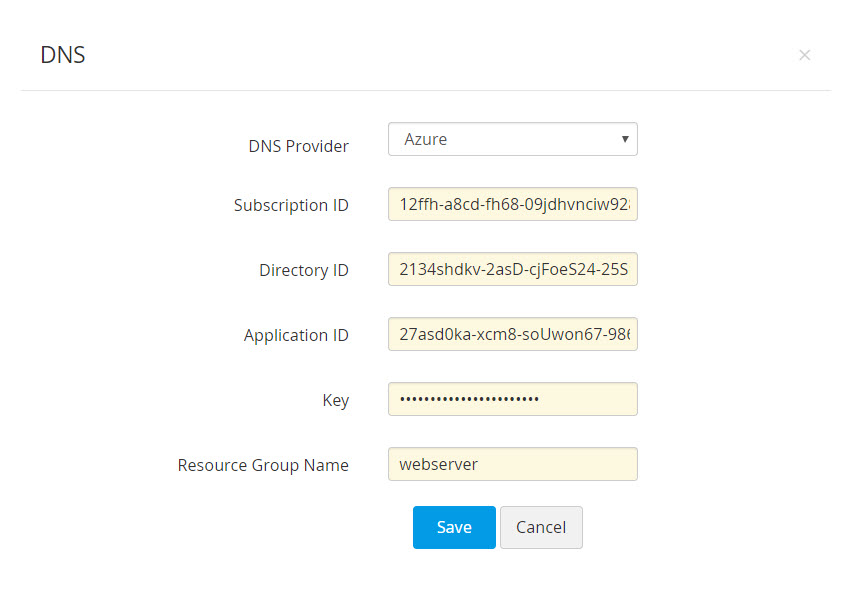
- Click Add. In the pop-up that opens, choose the DNS provider.
- Provide the Subscription ID, which is available in the Overview page of the Azure DNS zone.
- Provide the Directory ID, which is available in Entra ID >> Properties.
- If you have an already existing Azure application, provide its Application ID and Key. If not, follow the steps mentioned below to create the Azure application and key, and give the application access to the DNS zones for making API calls.
- To create the Azure application and key,
- Navigate to App registrations >> New application registration.
- Provide the application name, select the application type Web app / API and provide the sign-on URL. Click Create.
- After successful creation, you are directed to a window that displays the Application ID.
- To get the application key, navigate to Keys and create a key.
- Provide the key description, duration and click Save.
- Once the key is saved, key value is displayed. Copy and save the key value for future references.
- To give the application access to DNS zones,
- Navigate to the resource group where all DNS zones or created or switch to a specific DNS zone.
- Switch to Access Control (IAM) and click Add.
- Choose the role as Contributor, assign access to Entra ID user, group or application, search and select the application created in Azure Directory and click Save.
- The created Azure application is now given access to DNS zones for making API calls.
- Finally, enter the Resource Group Name, which is the group name in which you have created the DNS zone and click Save.
- Your DNS account details are saved and listed under Manage >> DNS.
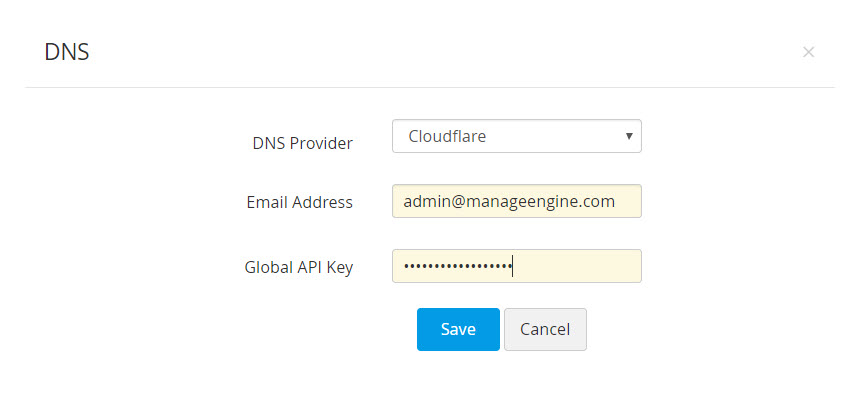
- In the Email address field, specify the email address associated with the Cloudflare account.
- For Global API Key, use the 'Generate API' key option in the domain overview page of the Cloudflare DNS to generate the key and paste the value in this field.
- Click Save. Your DNS account details are saved and listed under Manage >> DNS.
- Generate and specify the Access Key ID and Secret associated with your AWS account.
- If you do not have an AWS account, create one and generate the Access Key ID and Secret by following the steps given below:
- Login to the AWS console and navigate to IAM Services >>Users.
- Click Add user.
- Provide the user name and select the access type as Programmatic access.
- Switch to the next tab, click Attach existing policies directly under Set Permissions and search for "AmazonRoute53FullAccess".
- Assign the policy that is listed and switch to the next tab.
- In the tags section, add appropriate tags (optional) and switch to the next tab.
- Review all the information entered and click Create user.
- The user account is created and subsequently, an access key ID and a secret is generated. Copy and save the key ID and secret in a secure location for it will not be displayed again.
- If you already have an AWS user account, you have to grant "AmazonRoute53FullAccess" permission to the user and generate the access key if the user doesn't have one. And if the user account has an access key associated already, it is just enough to ensure the required permission is granted.
- Navigate to the Permissions tab, select the required user account and click Add Permission.
- Click Attach existing policies directly under Set Permissions and search for "AmazonRoute53FullAccess".
- Assign the listed policy and hit Save.
- To generate the access key,
- Select the particular user account and navigate to the Security Credentials tab.
- In the window that opens, click Create access key.
- An access key ID and a secret is generated. Copy and save the key ID and secret in a secure location for it will not be displayed again.
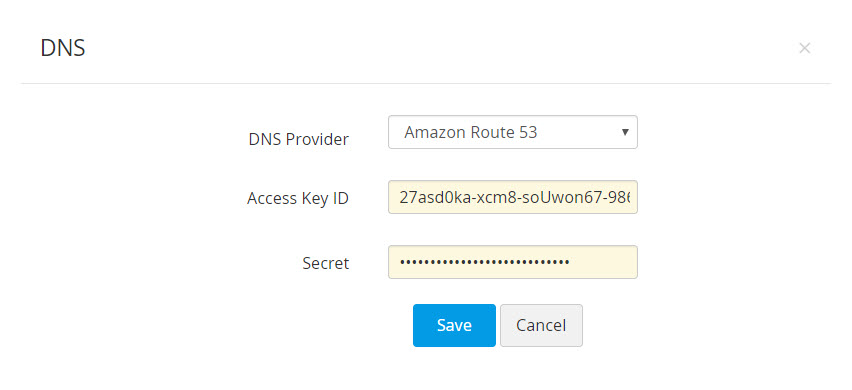
- The DNS Server IP / Hostname represents the server name / IP address in which the DNS server is installed or running.
- The server details are found in the server installation directory. For instance, in the case of Bind9 DNS server, you can find these details in the file named.local.conf in the server installation directory.
- Provide the Key Secret, which is the key content found in the server installation directory.
-
Provide a name for the key, choose the signature algorithm and click Save.
- Go to the GoDaddy developer portal and switch to the API keys tab.
- Log in to your GoDaddy account if you aren't logged in already.
- Once you log in, you will be redirected to the API keys page where you can create and manage API keys. Click Create New API key.
- Provide your application name, choose the environment type as Production and click Next.
- The API key and its secret is generated. Copy and save the secret in a secure location, as it will not be displayed again.
- Navigate to Certificates >> Acme >> Let's Encrypt and click Manage from the right most corner.
- Switch to the DNS tab and click Add.
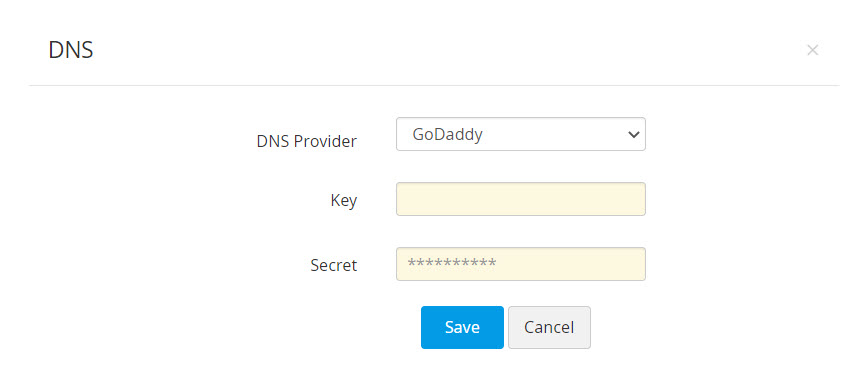
- Choose GoDaddy from the DNS Provider drop-down menu.
- Enter the Key and Secret that was previously generated from the GoDaddy portal. Click Save.
- Log in to your ClouDNS account and go to Reseller API.
- If you have already created an API user id, you will find it under API Users. If not, click Create API to generate a new one.
- Navigate to Certificates >> Acme >> Let's Encrypt and click Manage from the right most corner.
- Switch to the DNS tab and click Add.
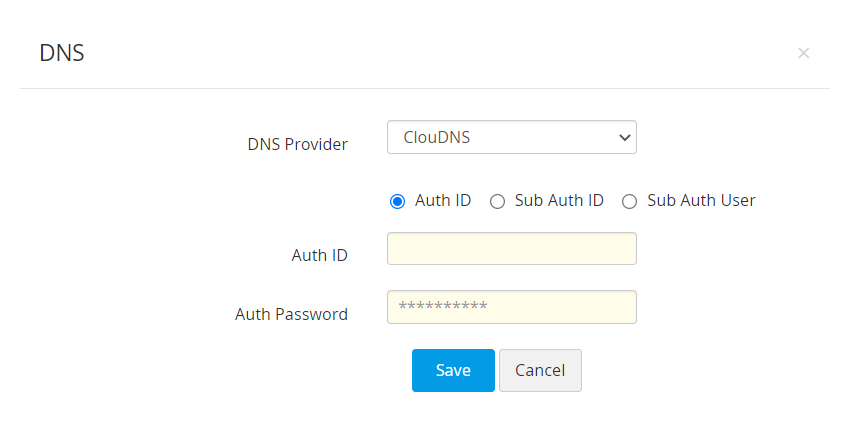
- Choose ClouDNS from the DNS Provider drop-down.
- Choose one of the following options: Auth ID, Sub Auth ID, Sub Auth User.
- Enter the chosen ClouDNS Auth ID, its respective Auth Password, and click Save.
- One certificate can secure up to 100 domains. You can enter a maximum of 100 names in the 'domain name' field out of which the first name is considered as the common name and the rest are treated as Subject Alternative Names (SAN).
- Password Manager Pro supports http-01 and dns-01 based domain validations. Choose the challenge type based on your requirements.
- For dns-01 based domain validation, if you are using your configured DNS account for challenge verification, make sure that the status of the chosen DNS account is marked Enabled under Manage >> DNS.
- Option to change the private key currently works only with the RSA key algorithm.
- A window opens displaying the challenge to be fulfilled.
- Click the Agent mapping icon.
- A pop up will open. If the domain server is a Linux machine, fill in the required details and click Save.
- If the domain server is a Windows machine, download and install the KMP agent for Windows server using the steps mentioned below:
- Navigate to Certificates >> Acme >> Let's Encrypt tab, and click Manage button in the top right corner.
- Switch to the Windows Agent tab.
- Download the KMP agent from the top right corner of the window based on your server compatibility (32 bit or 64 bit).
- Open the command prompt and navigate to the Password Manager Pro installation directory.
- Execute the command 'AgentInstaller.exe start.'
- Open the command prompt and navigate to the Password Manager Pro installation directory.
- Execute the command 'AgentInstaller.exe stop.'
- If the domain server is a Windows machine, download and install the Windows agent on the domain server. Navigate to Manage >> Windows Agents, download and install the agent on the domain server.
- Once, the above agent mapping settings are configured (agent mapping is a one-time configuration), Password Manager Pro automatically handles the verification of challenges presented by Let's Encrypt.
- After configuring agent mapping, click Pending on the pending requests and click Verify. The challenge is verified and the certificate request is submitted to Let's Encrypt CA.
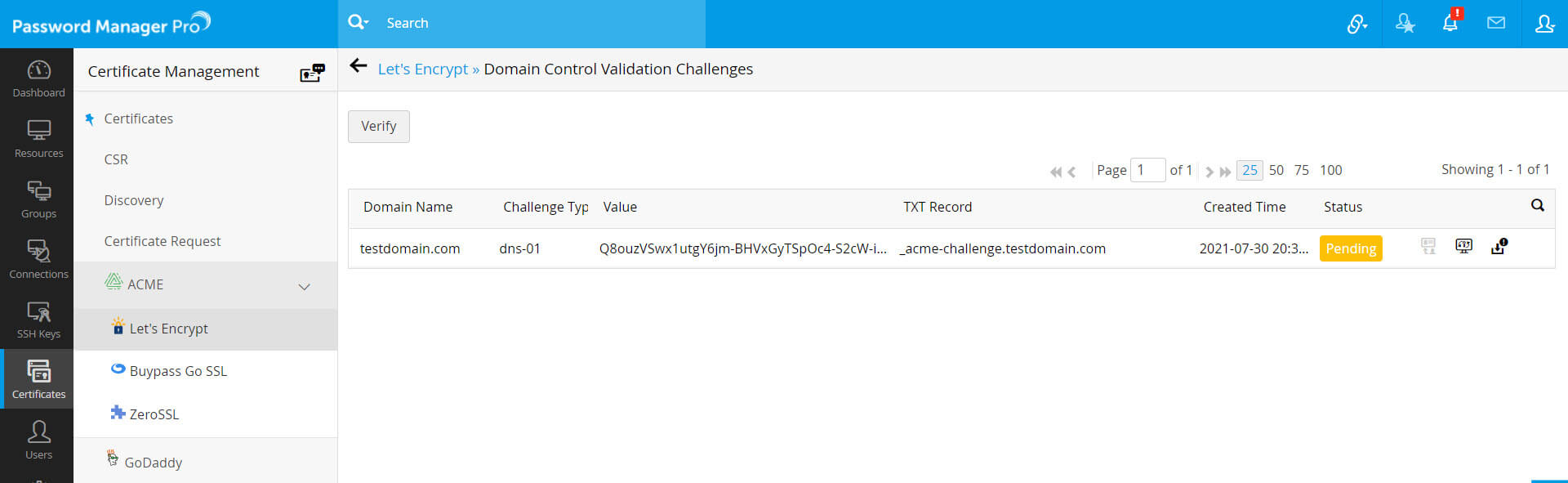
- Switch to Let's Encrypt tab and click the request status (Pending) corresponding to the certificate request.
- You'll be directed to a window that displays the DNS challenge value and TXT record.
- If you have already configured your DNS account details and have opted for DNS while creating the certificate request, you can assign the DNS account to the request.
- Select the request, choose Assign DNS from More top menu and select the required DNS account.
- In cases where you do not have a DNS account configured or have not opted for it when raising the certificate request, Password Manager Pro provides an option for automating DNS-01 challenge verification through Agent Mapping.
- Click the Agent Mapping icon present to the left side of the request. Agent mapping is a one-time configuration.
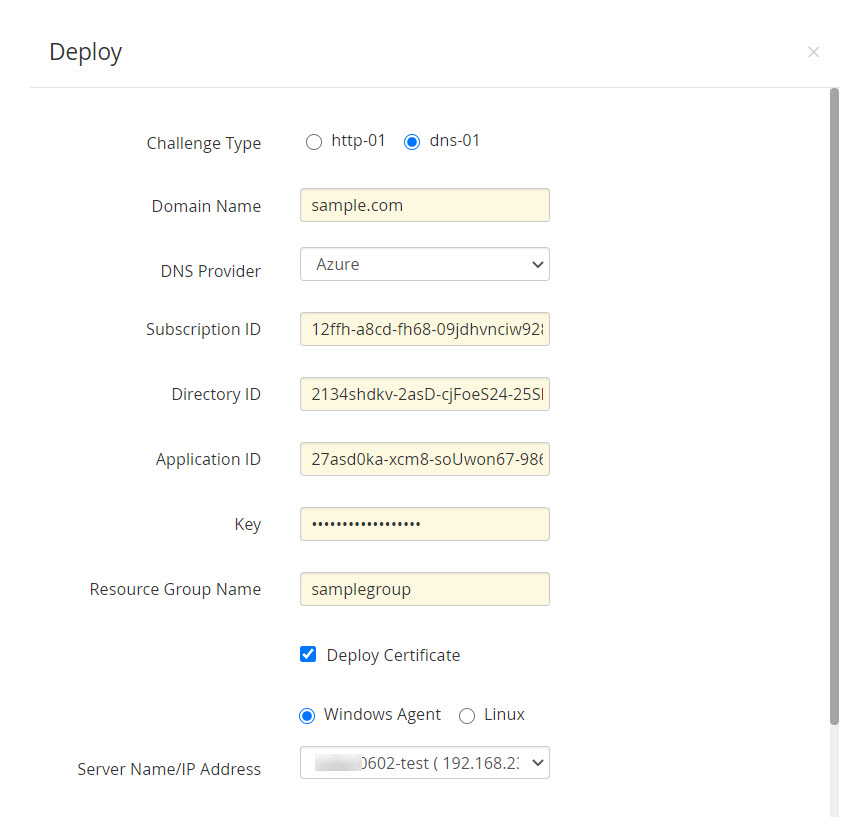
- Choose your DNS provider. For Azure DNS, provide the required details—Subscription ID, Directory ID, Application ID, Application Key and Resource Group Name.
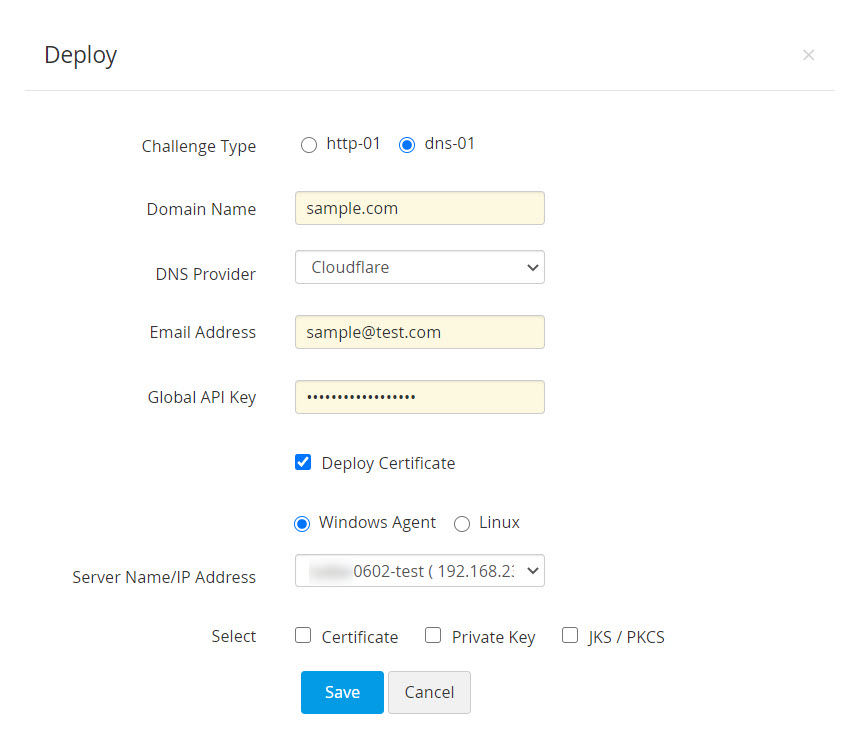
- For Cloudflare DNS, enter the email address associated with your Cloudflare account and the Global API key.
- For Amazon Route 53 DNS, enter the Access Key ID and Secret associated with your AWS account. Similarly, you can also deploy DNS challenge for RFC-2136 Update and GoDaddy DNS.
- Enable the Deploy Certificate check-box to automate deployment of the certificate to their corresponding end-servers after domain validation and after successive renewals.
- For Linux end-servers provide the required details, while for Windows end-servers download and install the Windows agent using the same procedure as mentioned for http-01 challenge.
- After filling in the details, click Save. The end-server details are successfully mapped and stored in Password Manager Pro, which you can view or edit from Manage >> Deploy tab.
- You can request and acquire certificates only for public domains using Let's Encrypt integration.
- The handling of challenges can also be done manually without automation. Copy and paste the challenge values / text records manually in your domain server. Then in the Password Manager Pro server, navigate to Pending Requests page and click Verify. The challenge is verified and certificate is issued.
- Password Manager Pro automates challenge verification using DNS for a certificate request only when Agent mapping is not available. Challenge verification is automated through agents, if agent details are available in Manage >> Deploy tab.
- Currently, KMP agent is only available for Windows servers.
- If you have chosen Global DNS configuration for RFC2136 DNS update, the domain name itself acts as the zone name (Global DNS configuration is possible only if you are using the same Key Secret for all zones). Whereas, if you have chosen domain-agent mapping, you have to provide the Zone name, Key Name, and Key Secret for each domain separately.
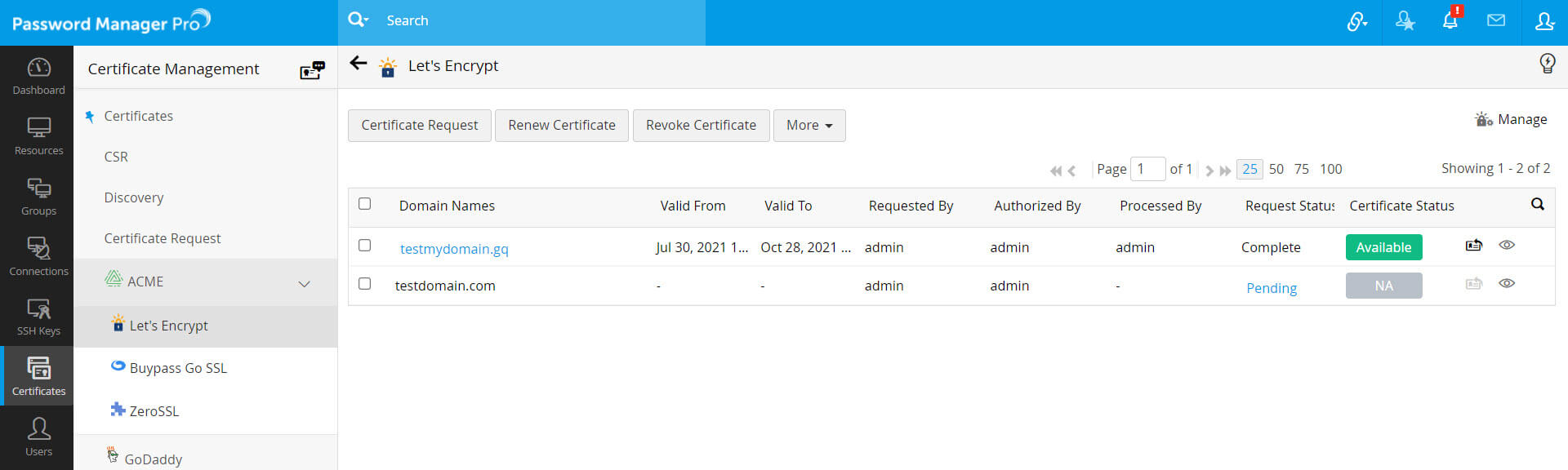
- On successful verification, Let's Encrypt issues the requested certificate.
- The window automatically redirects to a page which displays the certificate and its status (status is marked Available, if the challenge verification is successful and Failed if the challenge verification fails).
- Click the Available button to save the certificate in Password Manager Pro repository, e-mail or export it.
- If the challenge fails, click New challenge(

 ) to obtain another set of challenges and repeat the above process.
) to obtain another set of challenges and repeat the above process. - On saving, the certificate gets added to the Password Manager Pro repository which can be viewed from the Certificates>> Certificates tab.
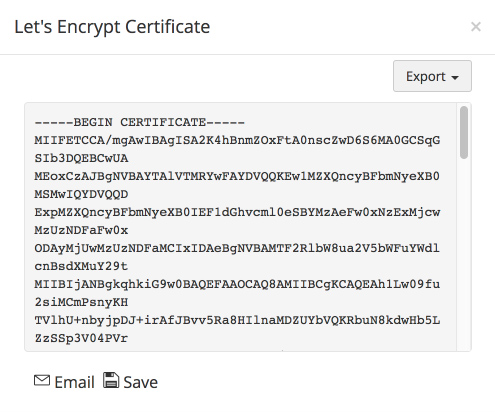
- Navigate to Certificates >> Acme >> Let's Encrypt.
- Select the certificate that you want to renew and click Renew Certificate button.
- The certificate is renewed and the Certificate Status bar displays Renewed.
- Click the status bar to save the renewed version of the certificate to Password Manager Pro certificate repository.
- History on renewal can be inferred by clicking on the certificate history() button from the Certificates >> Certificates tab.
- Navigate to Certificates >> Acme >> Let's Encrypt tab.
- Select a certificate you want to revoke and click Revoke Certificate.
- The certificate is revoked and is no longer valid.
- Navigate to Certificates >> Acme >> Let's Encrypt tab.
- Select the certificate you want to delete and click Delete.
- The certificate is deleted from the Password Manager Pro database.
3. Raising a Certificate Request
After creating an account with Let's Encrypt, you have to generate a certificate request. You are then presented with a challenge which you have to fulfill for Let's Encrypt to validate your domain and issue the certificate.
3.1 Configuring the DNS Account
3.1.i For Azure DNS
3.1.ii For Cloudflare DNS
3.1.iii For AWS Route 53 DNS
To grant the required permissions, follow the below steps:
3.1.iv For RFC2136 DNS Update
If you are using open source DNS servers such as Bind, PowerDNS etc., that support RFC2136 DNS update, follow the steps below to automate DNS-based domain control validation procedure using Password Manager Pro:
3.1.v GoDaddy DNS
If you are using GoDaddy DNS for DNS validation, follow the steps below to automate DNS-based domain control validation procedure using Password Manager Pro.
Steps to Obtain GoDaddy API Credentials:
Now, in the Password Manager Pro interface, follow the below steps to add GoDaddy DNS to the Let's Encrypt certificate repository:
3.1.vi ClouDNS
If you are using ClouDNS for DNS validation, follow the steps below to automate the DNS-based domain control validation procedure using Password Manager Pro:
Steps to Obtain ClouDNS API Credentials:
Click here to learn more about ClouDNS API Auth IDs.
Now, in the Password Manager Pro interface, follow the below steps to add ClouDNS to Let's Encrypt CA:
4. Let's Encrypt Challenge Verification
Password Manager Pro expedites domain validation through automatic verification of HTTP-01 and DNS-01 challenges (currently Azure, Cloudflare, Amazon Route 53, RFC2136 DNS update, GoDaddy DNS). For the automation to take effect, you have to initially map the end-server details to Password Manager Pro, which is a one-time process.
4.1 Domain Validation Through HTTP-01 Challenge Verification
For domain validation through http-01 challenge
Downloading KMP Agent for Windows servers:
The KMP agent package is a zip file comprising of the necessary executables, configuration files required for automatic verification of Let's Encrypt challenges through automatic domain validation. You have to just unzip and install the agent on your Windows domain server after download. To download the agent,
Installing KMP agent for Windows server:
To install KMP agent as a Windows service,
To stop the agent and uninstall the Windows service,
4.2 Domain Validation through DNS-01 Challenge Verification
For DNS-01 challenge verification from Password Manager Pro,
Agent Mapping
In the Deploy window that opens, carry out the following operations to map and save your end-server details in Password Manager Pro.
5. Procuring and Saving the Certificate
6. Renewing Certificates
Certificates issued by Let's Encrypt have a life-time of ninety days after which they are not valid. Also, as mentioned above, the domain authentication validity period is sixty days, which means that the user has to fulfill the challenges once in every sixty days in order to prove his ownership of the domain.
Certificate renewals can be carried out manually or automatically through automatic domain validation. To renew a certificate manually,
Note: The certificate should be saved after renewal in order to be updated in the certificate repository. Else, only the old version of the certificate will continue to remain in repository.
6.1 Automatic Renewals through Automatic Domain Validation
If agent mapping is been configured, the certificate renewal process will be done automatically without manual intervention. All the certificates in your organization procured from Let's Encrypt is automatically renewed after every 75 days. i.e., 15 days before its expiry and a notification is sent to the account holder's e-mail address.
Note: Automatic renewals are applicable only for those certificates saved in Password Manager Pro repository. i.e., after procuring a certificate from Let's Encrypt, you have to save it in order for the automatic renewal to take effect.
7. Revoking Certificates
Revoking a certificate renders the certificate invalid and immediately removes the HTTPS from the website.
To revoke a certificate, follow the below steps:
8. Deleting Certificates
Deleting a certificate removes the certificate from the Password Manager Pro repository, but the certificate still remains valid.
To delete a certificate, follow the below steps:
9. About Let's Encrypt
Let's Encrypt is a free, automated and open Certificate Authority developed by the Internet Security Research group (ISRG) with a main motive to reduce the complexity involved in establishing HTTPS connection and smoothen the overall certificate installation process. Till date, Let's Encrypt issues only domain validated certificates. Organization validation and extended validation are not available and are not being planned to be distributed anytime in the near future. All certificates issued by Let's Encrypt have a life time of ninety days after which they are not valid. Also, the domain authentication validity for a certificate is sixty days. i.e., for every domain you secure, you'll have to fulfill the challenges once in sixty days in order to prove your ownership of the domain. The main purpose of domain validation is to ensure security and Let's Encrypt is planning to reduce this domain authentication validity period to seven days. For more information about Let's Encrypt, click here