Adding Users Manually
Password Manager Pro allows administrators to create users manually and assign different user roles to them based on the level of access they need. Once created, the users will get an email with the details of their account and login credentials. While adding users manually, administrators can tailor the access levels and individual preferences such as GUI language, based on the organization's requirements.
Note: User addition can be carried out only by Administrators, or Privileged Administrators, or by users with custom roles having similar permissions.
Steps Required
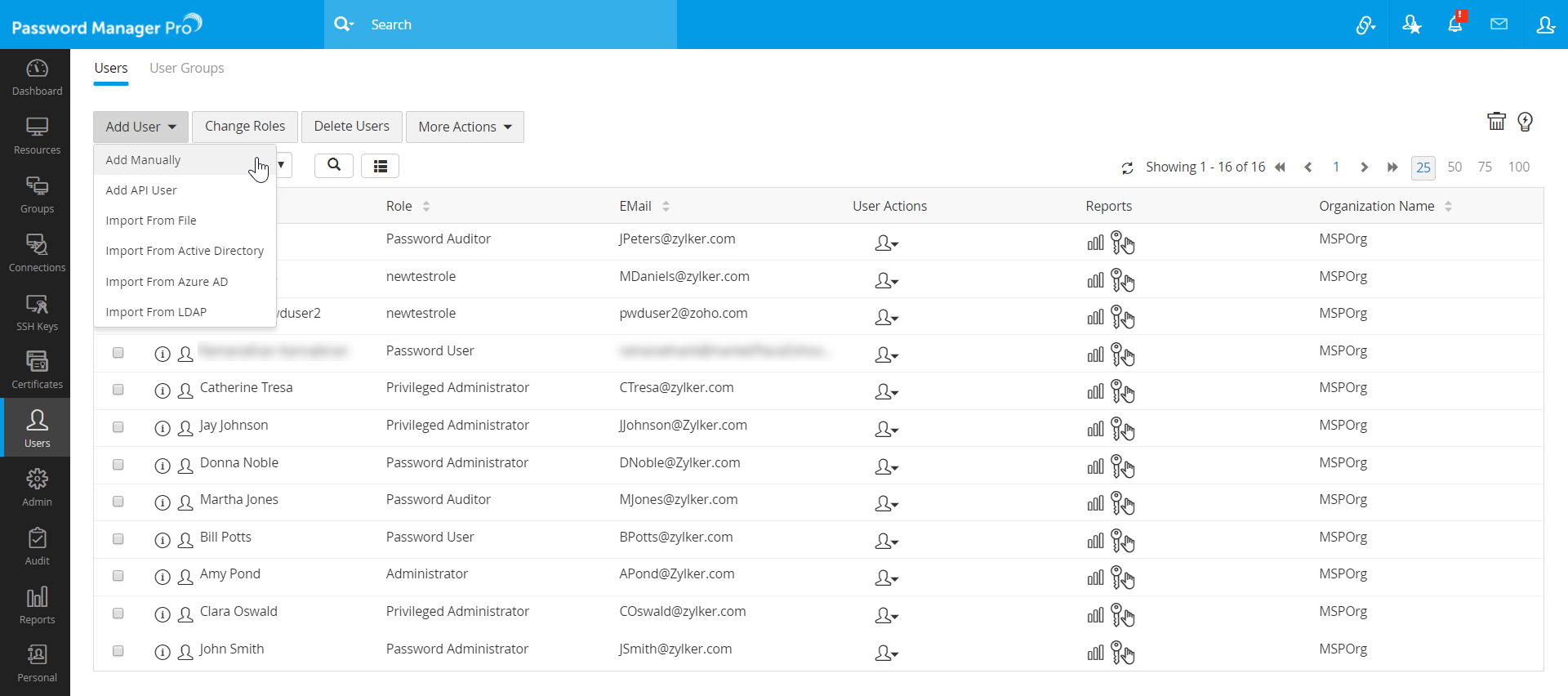
- Navigate to the Users tab, click the Add User button and select Add Manually from the drop down.
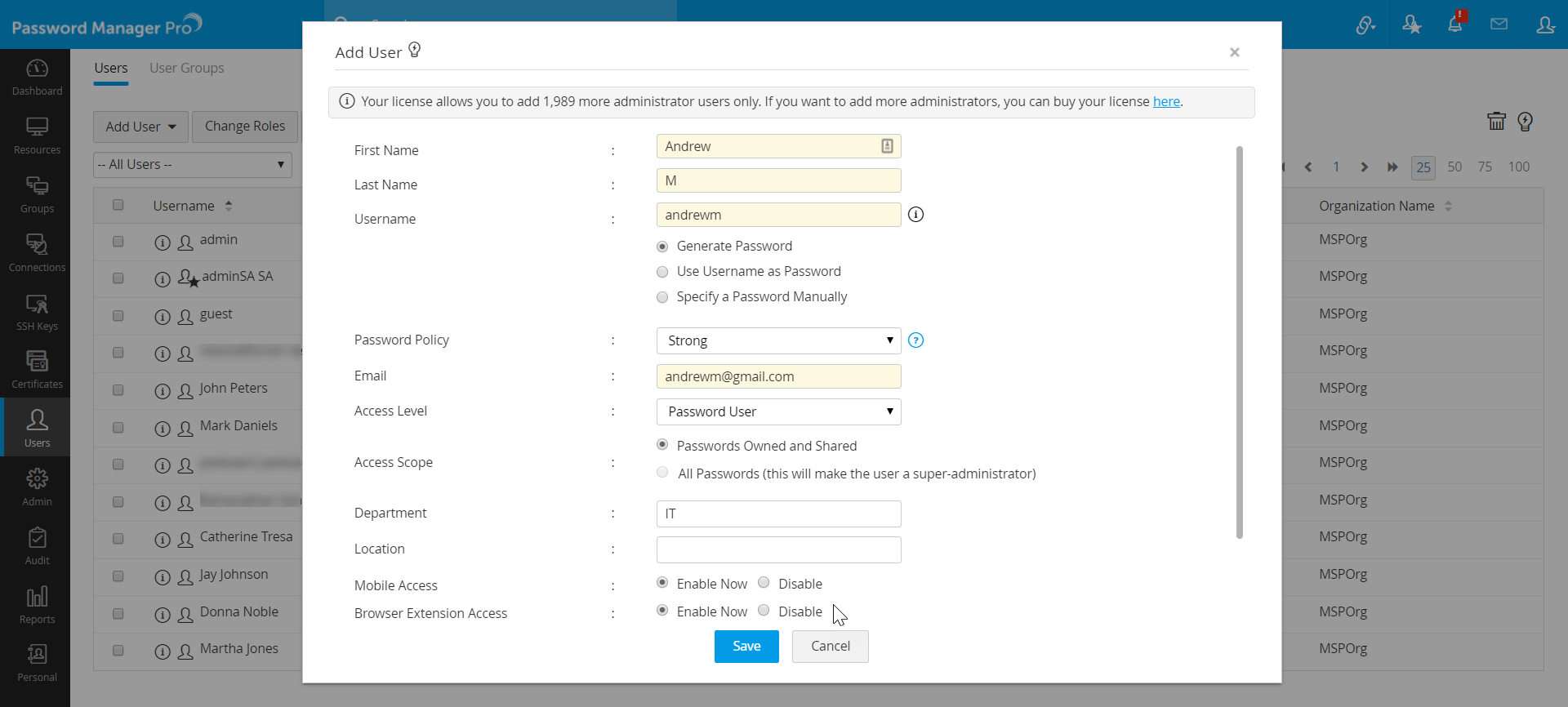
- In the Add User window, enter the following attributes:
- First Name and Last Name - Enter the user's first and last names in the respective fields. This field is mandatory.
- Username - Enter a unique username with which the user can login to Password Manager Pro. This field is also mandatory.
- For the password, choose from three options:
- Generate Password - If this option is selected, Password Manager Pro will randomly generate a password for the account based on the password policy selected in the next step.
- Use Username as Password - The password will be the same as the username provided.
- Specify a Password Manually - Enter a password manually in the text field.
- Password Policy - Select a password policy from the drop down.
- Email - Enter the user's email address. Login credentials for Password Manager Pro will be emailed to this address once the account is created.
- Access Level - Select an appropriate access level for the user from the drop down, this will determine the type of role this user will have in Password Manager Pro.
- Access Scope - Use this option to change an Administrator/Password Administrator/Privileged Administrator into a Super Administrator by choosing the option All Passwords in the system. When you do so, they will be able to access all passwords in Password Manager Pro without any restriction. Click here to learn more about super administrators in Password Manager Pro. Conversely, choose the Passwords Owned and Shared option to revert a Super Administrator to their earlier role of Administrator/Password Administrator/Privileged Administrator.
- Department and Location - These fields are not mandatory fields. However, populating valid data in these fields with the correct values will be helpful for searching and grouping the resources.
- Mobile Access & Browser Extension Access - Choose Enable Now for both the fields if you wish to allow the user to access Password Manager Pro via the Password Manager Pro mobile app and browser extensions.
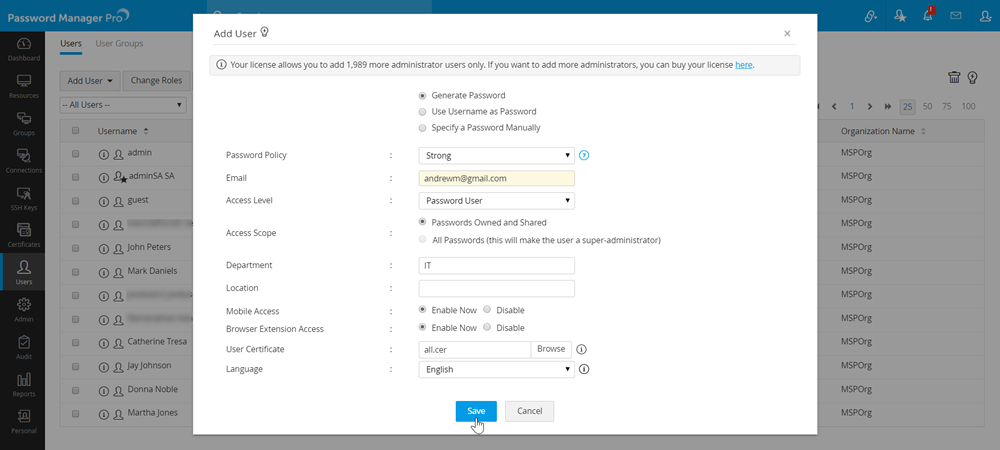
- User Certificate - Browse and add a certificate for smart card/PKI-based authentication. Click here for more information on that.
- Language - Choose a GUI language for the user from the drop down.
- Click Save to create the user.
Notes:
- All local users will be forced to reset their local login password during their first login to Password Manager Pro.
- The login page of Password Manager Pro has the CAPTCHA functionality to protect against scripted Denial of Service (DoS) attacks.