Setting up Two-Factor Authentication - Microsoft Authenticator
Microsoft Authenticator is a software-based authentication token developed by Microsoft. The token provides a six-digit number that users must enter as the second factor of authentication. You need to install the Microsoft Authenticator app on your smart phone or tablet devices. It generates a six-digit number, which changes every 30 seconds. With the app, you don’t have to wait a few seconds to receive a text message. Here's the sequence of events involved in using Microsoft Authenticator as the second level of authentication to login to Password Manager Pro:
- A user tries to access Password Manager Pro web-interface.
- Password Manager Pro authenticates the user through Active Directory or LDAP or locally (first factor).
- Password Manager Pro requests for the second factor credential through Microsoft Authenticator.
- The user has to enter the six-digit token that they see on the Microsoft Authenticator app GUI.
- Password Manager Pro grants the user access to the web-interface.
Summary of Steps
- Configuring two-factor authentication in Password Manager Pro.
- Enforcing two-factor authentication for required users.
- Connecting to Password Manager Pro web interface when TFA via Microsoft Authenticator is enabled.
1. Configuring two-factor authentication in Password Manager Pro
- Navigate to Admin >> Authentication >> Two-factor Authentication.
- Choose the option Microsoft Authenticator, and click Save.
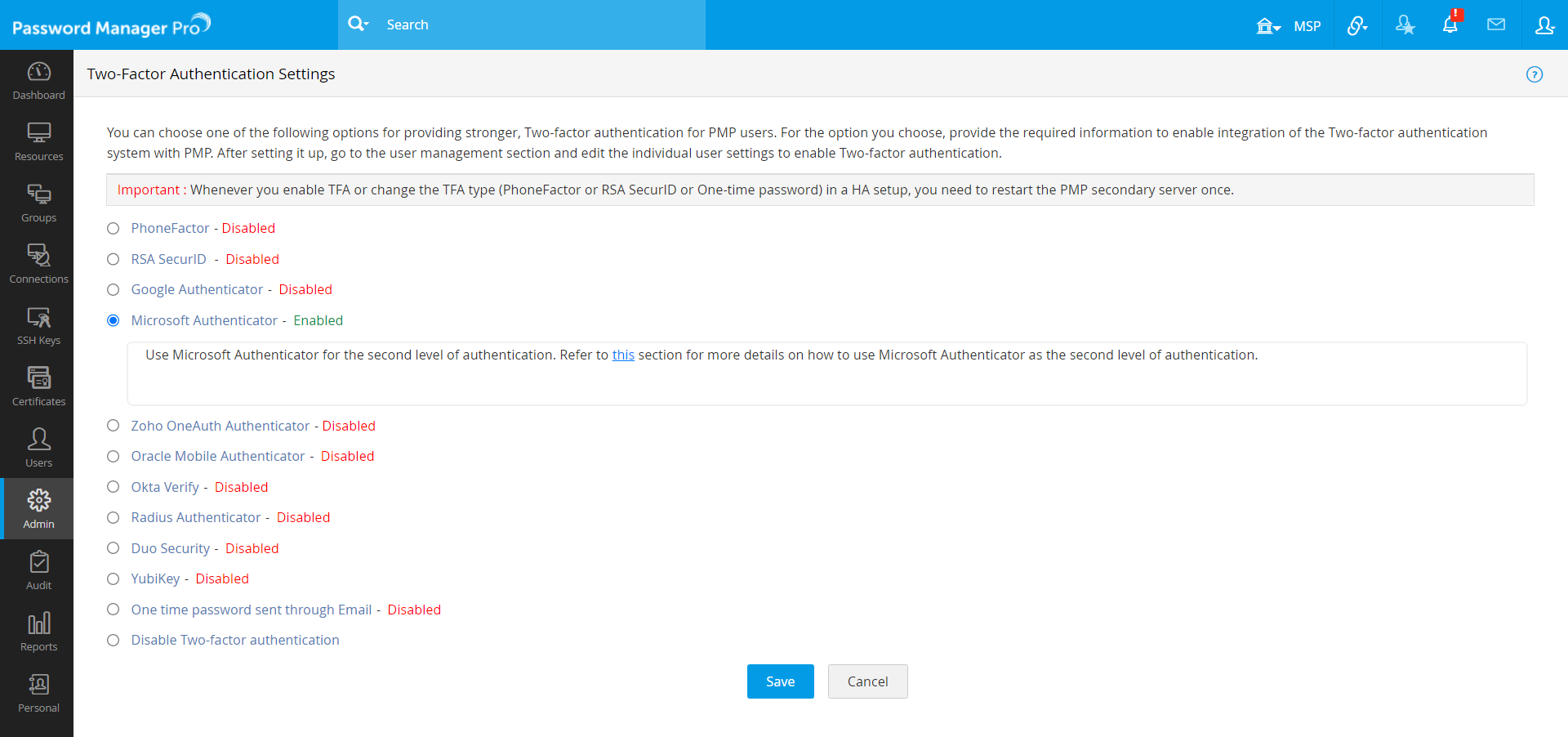
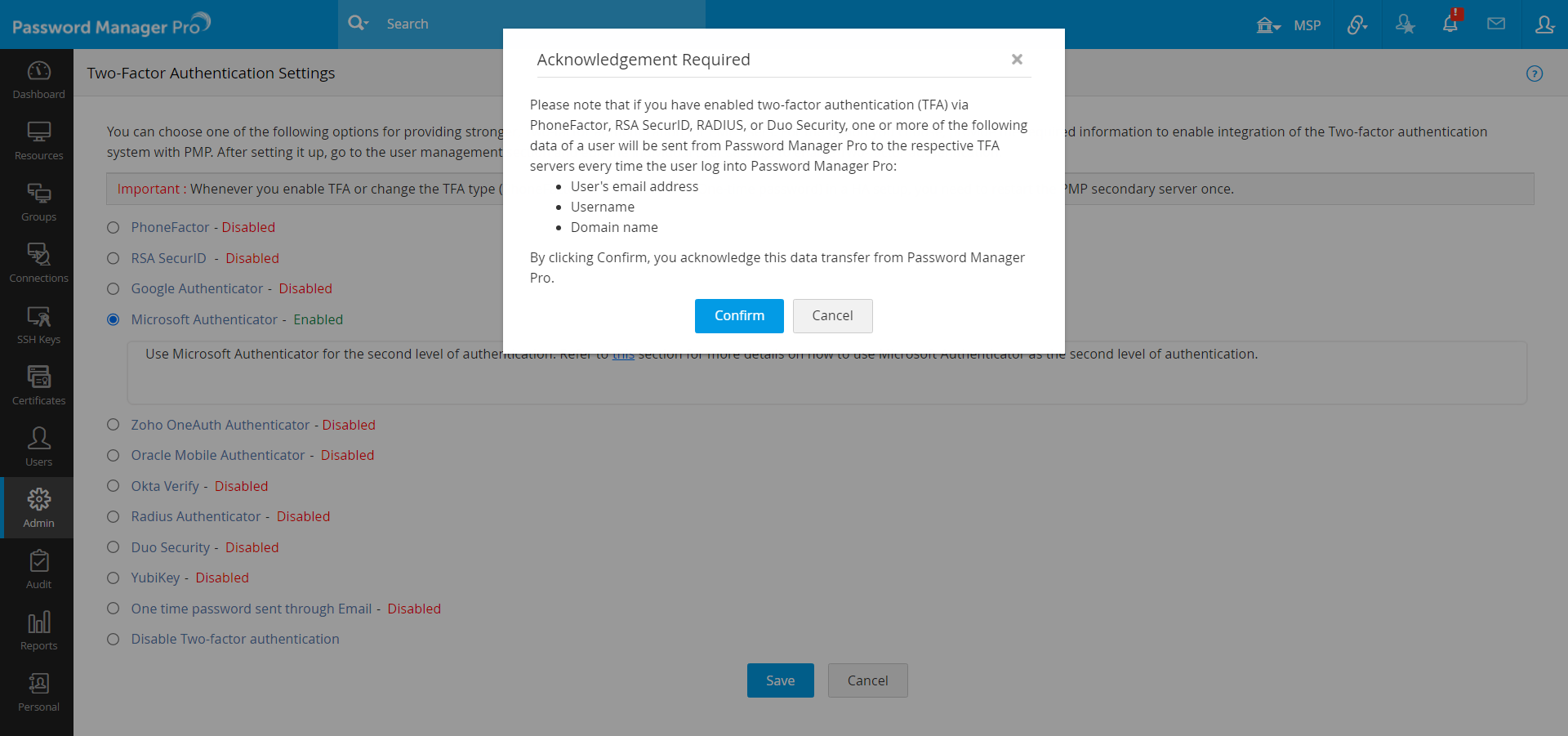
- Click Confirm to enforce Microsoft Authenticator as the second factor of authentication.
2. Enforcing Two-factor authentication for the required users
- Once you confirm Microsoft Authenticator as the second factor of authentication in the previous step, a new window will prompt you to select the users for whom two-factor authentication should be enforced.
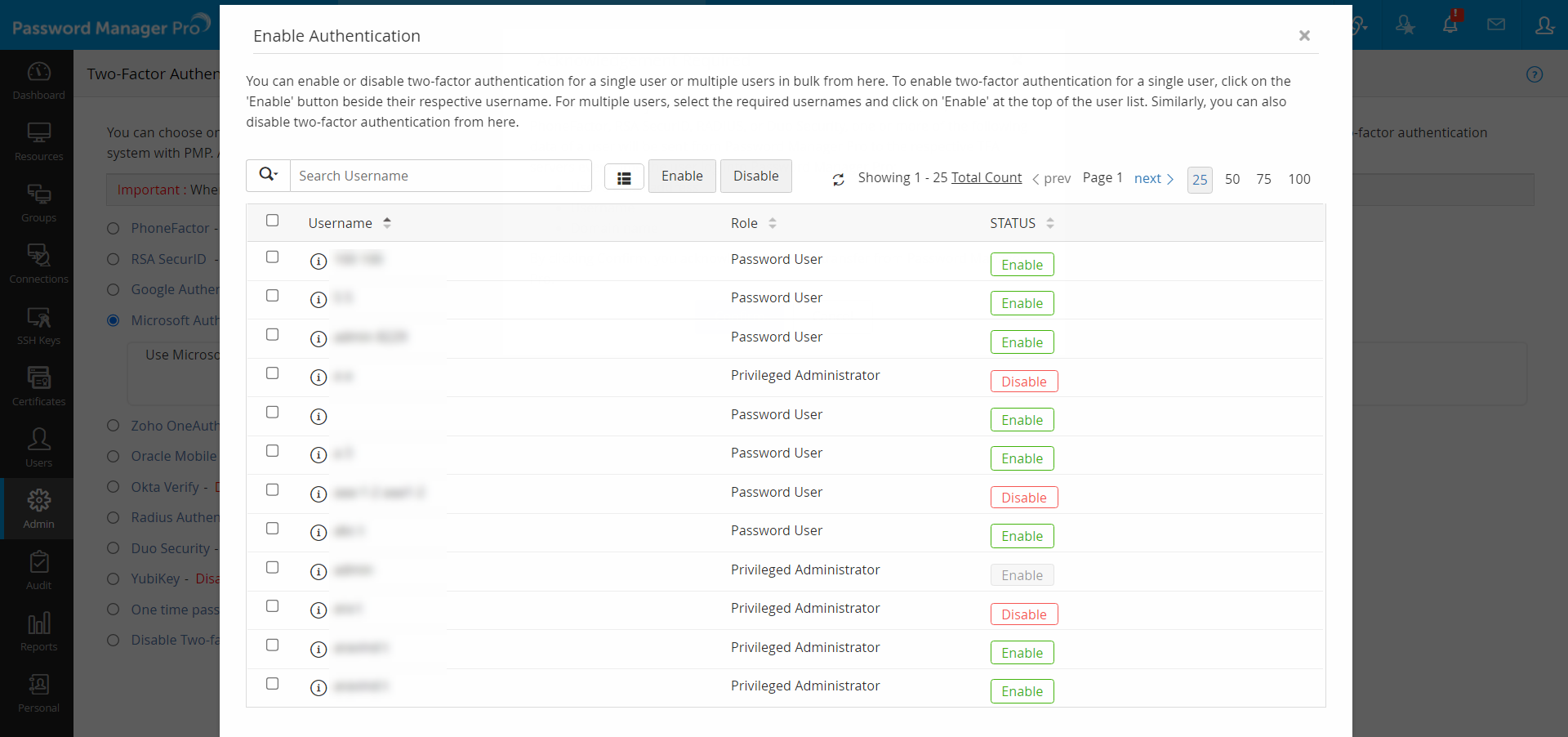
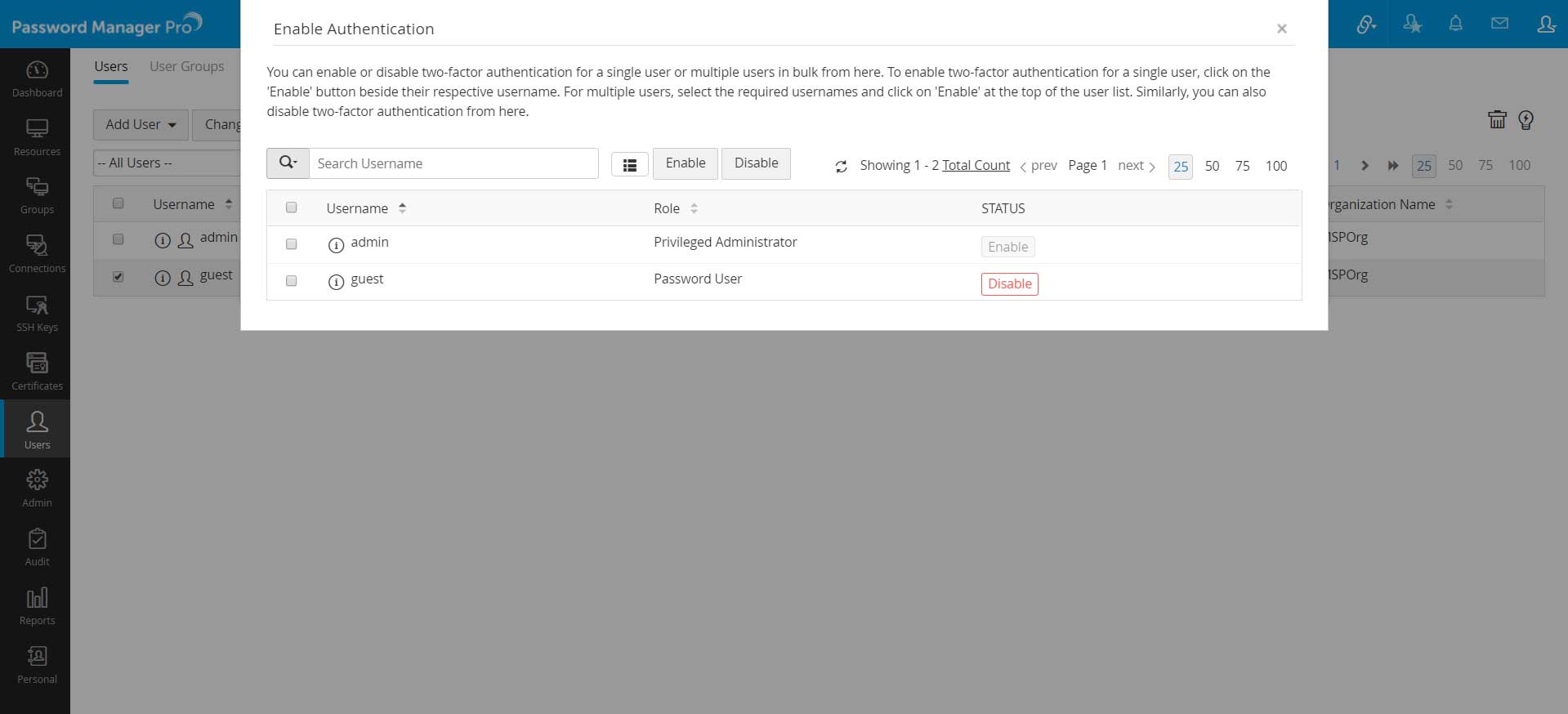
- You can enable or disable two-factor authentication for a single user or multiple users in bulk from here. To enable two-factor authentication for a single user, click on the 'Enable' button beside their respective username. For multiple users, select the required usernames and click on 'Enable' at the top of the user list. Similarly, you can also 'Disable' two-factor authentication from here.
- Close the window.
- You can also select the users later by navigating to Users >> More Actions >> Two-factor Authentication.
- In the window that opens, select the users for whom you want to enforce YubiKey two-factor authentication.
3. How to connect to Password Manager Pro web interface when TFA via Microsoft Authenticator is enabled?
3.1 Pre-requisite
To use Microsoft Authenticator as the second factor of authentication, you should first install the app in your smart phone or tablet.
3.2 Connecting to Password Manager Pro web interface
The users for whom two-factor authentication is enabled will have to authenticate twice successively. The first level of authentication will be through the usual authentication, i.e., the users have to authenticate through Password Manager Pro's local authentication or AD/LDAP authentication, whichever is enabled.
- Launch Password Manager Pro web interface, enter the Username and Password (local authentication or AD/LDAP), and click Login.
- Associating Microsoft Authenticator with your Password Manager Pro account:
- When you are logging in for the first time after enabling TFA through Microsoft Authenticator, you will be prompted to associate it with your account in Password Manager Pro. After launching the Microsoft Authenticator app in your mobile device or tablet, click on "Add Account" or the "+" button. Choose "Other (Google, Facebook, etc.)" for the kind of account you're adding, since Password Manager Pro is not a Microsoft extension.
- Here, you can either scan the QR code displayed in your Password Manager pro website by scanning the barcode shown in the GUI, or Enter Code Manually.
- If you choose to enter the code manually, the GUI will prompt you to enter an account name and a security key.
- Supply an Account name for your Password Manager Pro account in the format– PMP:account name (for example. PMP:john@abc.com).
- Provide an alphanumeric string as your Secret key, and then click Finish.
- Microsoft Authenticator will now start generating codes periodically, that changes every 30 seconds.
- You can enter this code in the text box provided in the Password Manager Pro login page for the second level of authentication.
Troubleshooting Tip
As mentioned earlier, the Microsoft Authenticator is associated with your Password Manager Pro account. If you ever lose your mobile device/tablet OR if you accidentally delete the Microsoft Authenticator app on your device, you will still be able to get tokens to log in to Password Manager Pro. In such scenarios, just click the link "Have trouble using Microsoft Authenticator?" in the Password Manager Pro login screen. You will be prompted to enter your Password Manager Pro username and the email address associated with Password Manager Pro. Once done, you will receive instructions to get Microsoft Authenticator again.
If you have configured High Availability
Whenever you enable TFA or when you change the TFA type (PhoneFactor, RSA SecurID, One-time password, RADIUS, or Duo) and if you have configured high availability, you need to restart the Password Manager Pro secondary server once.