Configuring Single Sign-on (SSO) using SAML 2.0 for ADFS
Single Sign-On (SSO) is an authentication method that allows users to sign in with a single ID and Password. ManageEngine Password Manager Pro offers support for SSO using SAML 2.0, which facilitates integration with Federated Identity Management Solutions for Single Sign-on (SSO). Password Manager Pro acts as the Service Provider (SP) and it integrates with Identity Providers (IdP) using SAML 2.0. The integration basically involves supplying details about SP to IdP and vice-versa. Once you integrate Password Manager Pro with an IdP, the users have to just login to IdP and then, they can automatically login to Password Manager Pro from the respective identity provider's GUI without having to provide credentials again.
Note: Password Manager Pro allows users to configure SAML SSO for Secondary server as a service provider, which allows users to log in to Password Manager Pro using the Secondary server when Primary is down.
Configuring SSO using SAML is a two step process involving the following topics:
1. Steps to Configure ADFS 10.0
Active Directory Federation Services (ADFS) created by Microsoft runs on Windows and supports SAML integration to provide SSO services to systems and applications throughout the organization. A similar configuration can be achieved in Password Manager Pro as well. For this, you need to first integrate ADFS with Password Manager Pro followed by enabling SSO services. Read further to know about the complete process of configuring SAML using ADFS for Password Manager Pro.
Video Representation of Complete ADFS Configuration:
Steps in Detail:
- Log in to Password Manager Pro and navigate to Admin >> SAML Single Sign On. In the SAML SSO configuration page, download the service provider metadata.xml file available under step 1.
- Navigate to Start >> All Programs >> Administrative Tools, and open ADFS 10.0 Management.
- The first step is to add Trust Relationships in ADFS 10.0 to add Password Manager Pro details. Under Trust Relationships, right-click on Relying Party Trusts and select Add Relying Party Trust from the drop down menu. A Add Relying Party Trust Wizard appears on the screen.
- Click Start and click Select Data Source from left pane.
- Choose the second option, Import data about the relying party from a file.
- Click Browse to import the metadata.xml file downloaded earlier from Password Manager Pro, and click Next.
- Set a Display name for the relying party, i.e. Password Manager Pro and click Next.
- Choose Access Control Policy: Select Permit everyone and click Next.
- Skip the Ready to Add Trust step by clicking Next and then click Close.
- Password Manager Pro will now be displayed in the Relying Party Trusts list. Right-click on the same and select Properties from the drop down menu as shown below.
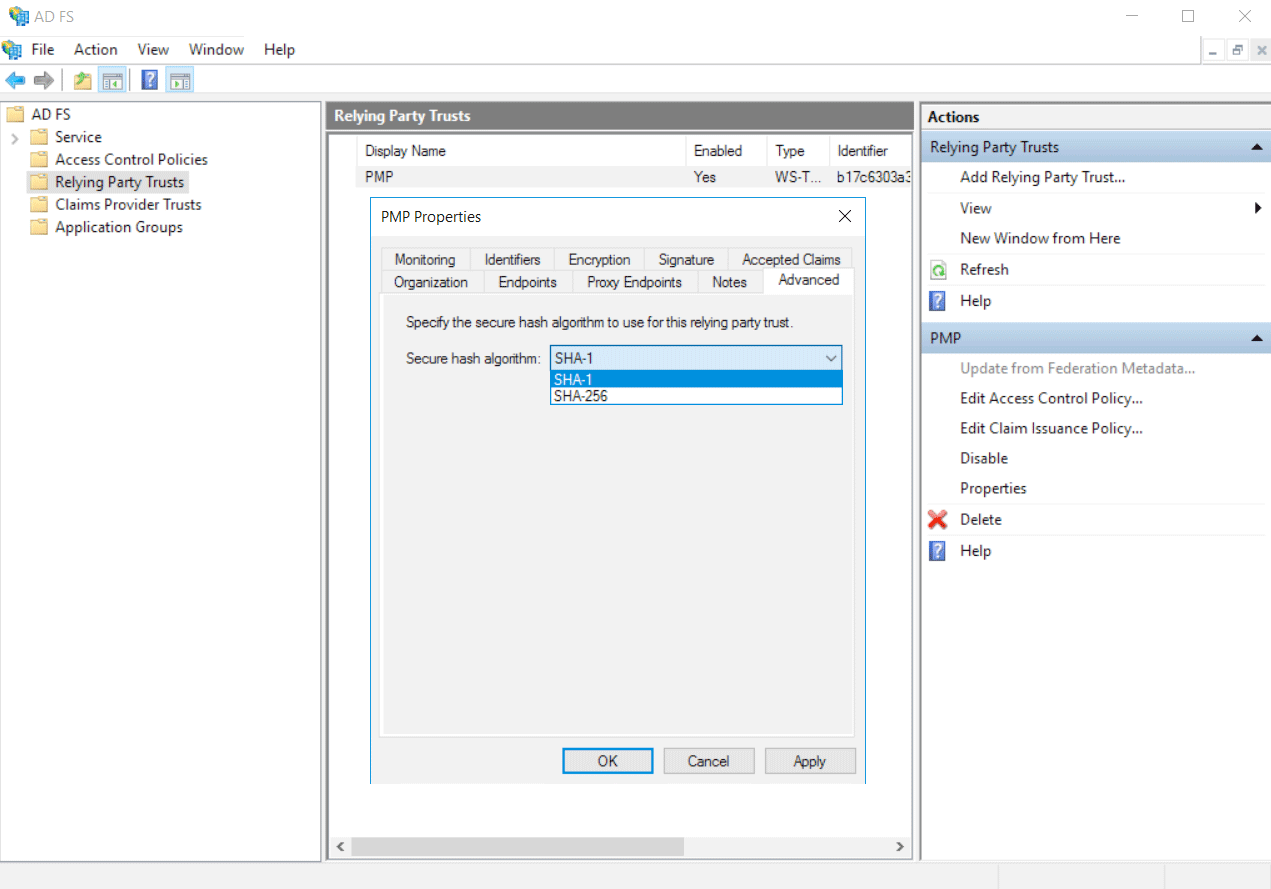
- In the dialog box that opens, switch to the Advanced tab and select SHA 1 as the secure hash algorithm. Apply changes and click OK.
- Right-click on Password Manager Pro again and now select Edit Claim Insurance Policy.
- In the dialog box that opens,
- Click Add Rule under Issuance Transform Rules.
- Select Transform an Incoming Claim as the Claim rule template and click Next.
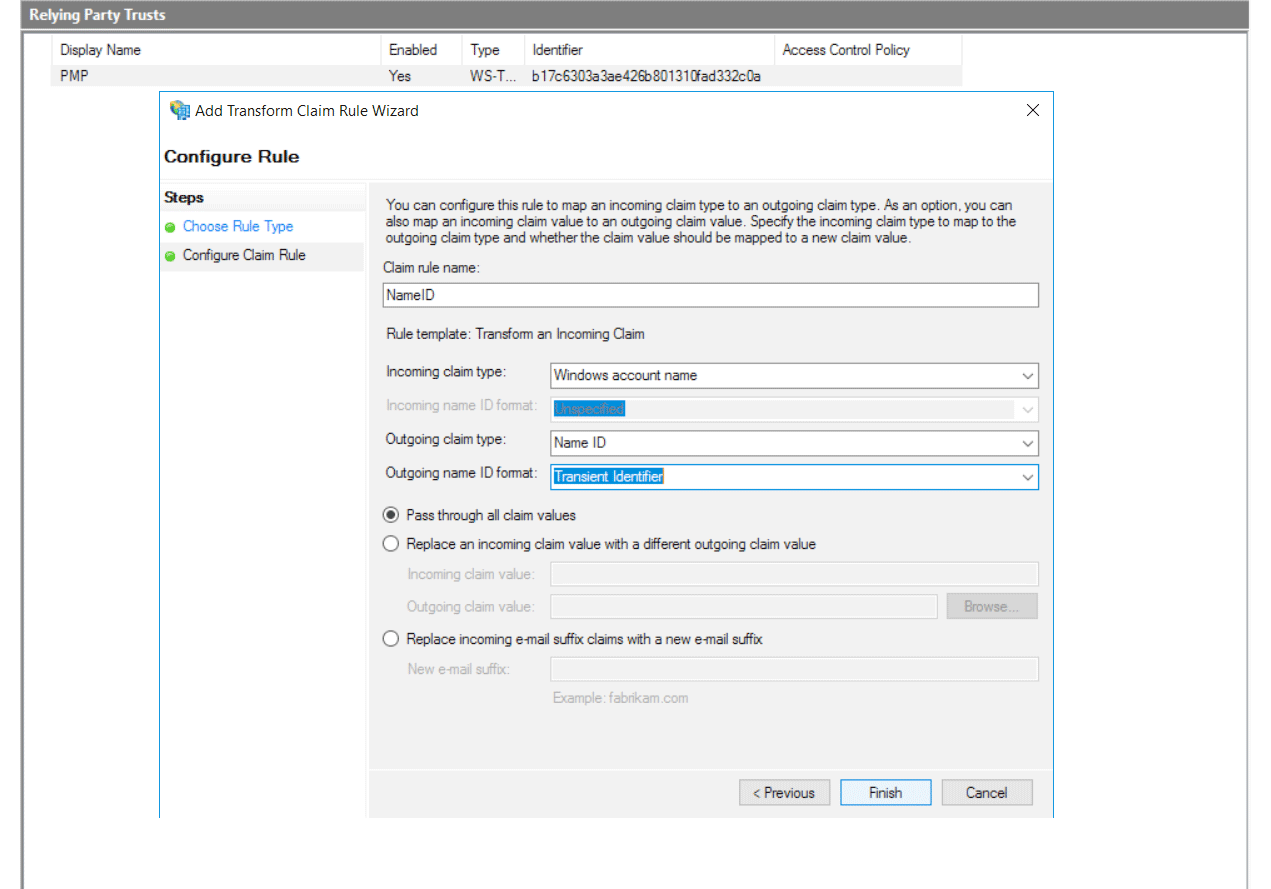
- Under Configure Claim Rule,
- Enter NameID as the Claim rule name.
- Select Windows account name as the Incoming claim type.
- Select Name ID as the Outgoing claim type.
- Select Transient Identifier for Outgoing name ID format.
- Click Finish.
- Click Apply to save changes and close the Edit Claim Rules window by clicking OK.
Now, you have successfully configured ADFS in Password Manager Pro. Proceed to step 2 below to know how to enable SSO services in Password Manager Pro.
Note: If you have already imported users to Password Manager Pro from AD, then their login names will be stored in the format, DOMAIN\Loginname. By default, setting Windows account name as the incoming claim type will match this format. However, if you have created Password Manager Pro local accounts for your AD users by importing them via a CSV file, you need to instead select a different claim type that matches the login name format stored in Password Manager Pro.
2. Steps to Configure Password Manager Pro to Enable SSO Services
- Open Password Manager Pro and navigate to Admin >> Authentication >> SAML Single Sign-On.
- Under Step 2 in the page, choose the first option Upload IdP metadata file to browse and open ADFS's Federation.xml file.
- The XML file can be downloaded from ADFS 10.0 console. In the console's left navigation pane, click on Endpoints and scroll down to the Metadata list. Now, locate the URL Path provided for the Federation Metadata type in this list and open the URL in a new browser tab to download the metadata .XML file.
- For SAML SSO authentication, the Assertion Consumer URL is the hostname of the server, by default. To update the Assertion URL, follow the below steps:
- Go to Admin >> Settings >> Mail Server Settings.
- Under Access URL, update the required URL and click Save. Now, the Assertion Consumer URL under Service Provider Details will be updated.
- The uploaded XML file will also populate the certificate details required for Step 3. In case the details aren't auto-filled in upon providing the metadata file, try configuring the Identity Provider details manually in Step 2 & 3. Then, click Save.
- To configure SAML Single Logout, navigate to <PMP_Installation_Directory\PMP\conf\system_properties.conf> and append the following system property under the existing properties.
- saml.logout.redirect.slo=true
- SAML Single Logout is applicable from build 12100 and above only.
- If you have already configured SAML for Password Manager Pro, re-upload the metadata.xml file to configure Single Logout.
- ADFS SSO service is now successfully configured for Password Manager Pro. Click on Enable SAML SSO to activate the service.
- Log out and log back in to Password Manager Pro to test the configuration.
Notes:
Notes: