These steps will guide you through setting up SAML SSO for Microsoft 365/Entra ID (formerly known as Azure AD) users, using ADSelfService Plus as the identity provider (IdP) and Microsoft 365/Entra ID as the service provider (SP).
Install-Module Microsoft.Graph -Scope CurrentUser
Connect-MgGraph -Scopes "Directory.AccessAsUser.All"
Note: Sign in with a Microsoft 365/Entra ID account that has Global Admin privileges.
Update-MgUserByUserPrincipalName -UserPrincipalName "<user_mailID>" -OnPremisesImmutableId "<immutable_id>"
New-MgUser -AccountEnabled:$true -UserPrincipalName "user01@selfservice.com" -MailNickname "user01" -OnPremisesImmutableId "
Get-MgUserByUserPrincipalName -UserPrincipalName "<user_mailID>" -Property UserPrincipalName, OnPremisesImmutableId | select UserPrincipalName, OnPremisesImmutableId
Login to ADSelfService Plus as an administrator.
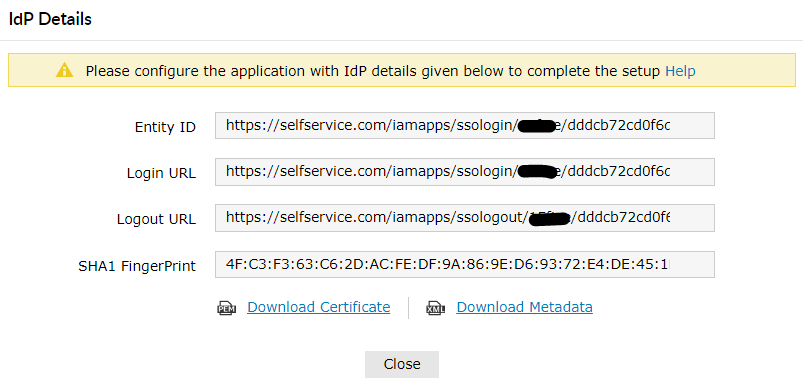
In the pop-up that appears, copy the Entity ID, Login URL and Logout URL and download the SSO certificate by clicking on the Download Certificate.
Install-Module Microsoft.Graph -Scope CurrentUser
Connect-MgGraph -Scopes "Directory.AccessAsUser.All"
Get-MgDomain
$dom = "selfservice.com"
$url = "<login URL value>"
$uri = "<entity ID value>"
$logouturl = "<logout URL value>"
Example values:
$url = "https://selfservice.com:9251/iamapps/ssologin/office365/1352163ea82348a5152487b2eb05c5adeb4aaf73"
$uri = "https://selfservice.com:9251/iamapps/ssologin/office365/1352163ea82348a5152487b2eb05c5adeb4aaf73"
$logouturl = "https://selfservice.com:9251/iamapps/ssologout/office365/1352163ea82348a5152487b2eb05c5adeb4aaf73"
$cert = "MIICqjCCAhOgAwIBAgIJAN..........dTOjFfqqA="

New-MgDomainFederationConfiguration -DomainId $dom -IssuerUri $uri -PassiveSignInUri $url -SignOutUri $logouturl -SigningCertificate $cert -PreferredAuthenticationProtocol saml -federatedIdpMfaBehavior rejectMfaByFederatedIdp
Get-MgDomainFederationConfiguration -DomainId $dom | Format-List

If you have already enabled Microsoft 365/Entra ID SSO using another IdP or want to update ADSelfService Plus' SSO settings, then you must first disable SSO in Microsoft 365/Entra ID, and then follow the steps given in this guide. To disable SSO in Microsoft 365/Entra ID, use the command given below:
$dom = "selfservice.com"
$federations = Get-MgDomainFederationConfiguration -DomainId $dom
Remove-MgDomainFederationConfiguration -DomainId $dom -InternalDomainFederationId $federations.Id

Please note that the above change may take some time to get implemented in Microsoft 365/Entra ID.
Note: Use Unspecified as the default option if you are unsure about the format of the login attribute value used by the application
Note: ADSelfService Plus supports SP- and IdP-initiated SAML SSO flows for Microsoft 365/Entra ID.
Your request has been submitted to the ADSelfService Plus technical support team. Our technical support people will assist you at the earliest.
Copyright © 2025, ZOHO Corp. All Rights Reserved.