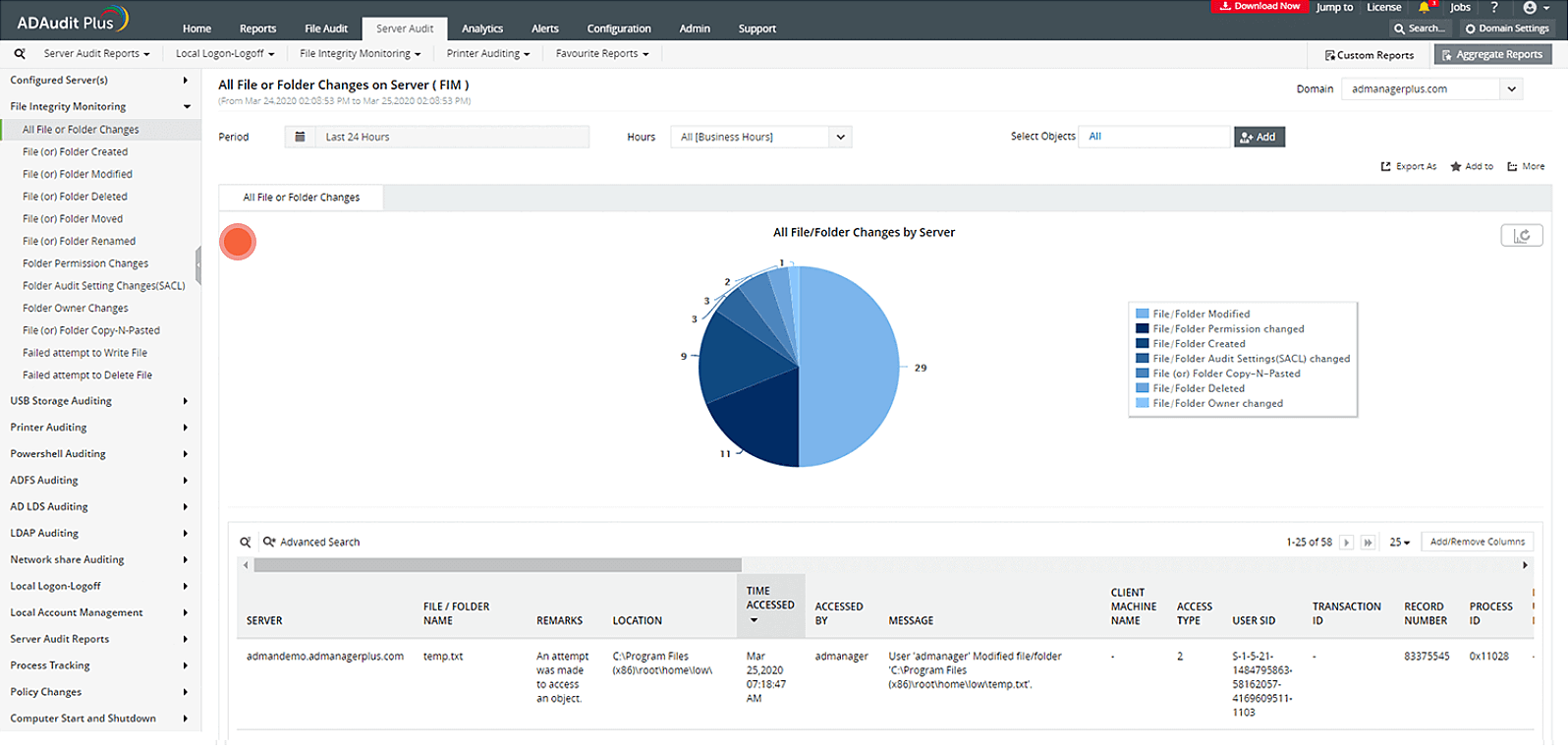
As organizations expand, so does the complexity of their operations; i.e., the volume of information handled by the company increases in size. The information stored within the company may belong to a diverse group of sectors with varying degrees of sensitivity attached to them. As a result, organizational activities often fall under the purview of several different regulatory and compliance bodies.
Not to mention, as an organization experiences rapid changes across its infrastructure, it'll need to ensure that its operational activities are in line with business targets. To tackle these logistical challenges, it is important for organizations to adopt an organized approach; the unified concept that ties enterprise integrity, adherence of regulations, and resilience to risks is governance, risk, and compliance (GRC).
With overlapping features shared among the three disciplines, an integrated GRC solution reduces duplicated efforts, which can help organizations streamline operations, cut costs, and encourage cross-domain analytics to deliver expansive results.
Describes the executive decisions made by an organization to ensure that its operations are working towards a collective business goal. Organizational governance combines management information and the control structures and stakeholders that influence, enforce, and monitor key policy decisions.
The key components that determine effective governance include internal assessments, risk management, and compliance monitoring reports. Some of the most prominent frameworks that can help with implementing IT governance are:
The existing or perceived challenges an organization must overcome to ensure smooth functioning. The types of risks faced by a company include:
Refers to the need for organizations to conform to a set of regulatory laws and guidelines. Compliance ensures that companies do not infringe any ethical boundary at the cost of fulfilling their objectives.
According to OCEG, an ideal GRC practice should incorporate the following components:
A foolproof GRC solution can ease the workload of network administrators by automating mundane tasks such as policy enforcement and monitoring. GRC tools unify diverse tasks and save the workforce from focusing their efforts on redundant, repetitive tasks that overlap between different teams. GRC solutions should also provide the necessity functions that are in line with the requirements of compliance laws and also aid in auditing entities, systems, and vendors that are associated with the organization.
Some of important components of a GRC solution include:
Deals with the conception and enforcement of company-defined regulations that shape up user and device activity within the organizational network. Apart from administering the end-to-end life cycle of company policies, the component also establishes communication channels to escalate policy violations via alerts and notifications along with dashboards that track, report on, and manage incidents of policy violations.
A continuous evaluation to ensure that an organization obeys security standards along with legal and regulatory frameworks while also mapping new compliance and licensing requirements as per the organization's evolving infrastructure.
The first step to delivering compliance management is regulatory mapping, which involves understanding and addressing the obligatory requirements expected from an organization by the regulation. This can be carried out by conducting risk surveys to gain inferences on the organization's security posture and the issues faced by the employees throughout different areas of the organization that amount to non-compliance.
Besides dashboards and auditing systems that administer and report anomalous activities, users must be educated on regulations so that they can incorporate the best practices in their day-to-day operations.
The process of identifying the possible and existing threats that endanger an organization and the subsequent mitigation measures taken by the organization constitute risk management. The five steps that amount to risk management include:
Parent organizations must intervene in improving the security posture of vendor companies and solutions, as they are seen as a lucrative threat vector by attackers to unleash prolonged supply chain attacks. This includes gaining visibility into the security metrics of third-party organizations, such as non-compliance and patch management; aggregating risk scores for partner companies; and placing tools that bridge the communication gap between parent and third- or fourth-party companies, such as unified dashboards to track, assess, and monitor shared security and business goals.
For companies, the ability to foresee, withstand, and react to adversaries requires a thorough knowledge of understanding the pain points and success factors that affect their supply chain. Being a critical component of GRC, operational resilience can be inherently achieved with better effect by automating key processes that identify vulnerabilities in workflows. Some of the main benefits of GRC that complement a resilient organization include:
Integrated GRC solutions allow better visibility to the risk indicators and appetite due to the breakdown of siloed mechanisms and interoperable knowledge sharing across domains. This means employees, process owners, and stakeholders can get a better overview of the strengths and weaknesses of an organization and make informed decisions and policies accordingly. With better transparency, it becomes easier for organizations to create risk profiles and action plans for exceptional cases and the subsequent risk and compliance factors for such situations.
Non-compliance with regulatory and license obligations can result in companies paying hefty sums as fines. This, in turn, affects the financial well-being of organizations. A 2017 survey by Ponemon and Globalscape shows that organizations guilty of non-compliance must pay up to 2.71 times the cost required to achieve effective compliance.
The EU's General Data Protection Regulation (GDPR), considered one of the most stringent regulations in the IT landscape, can levy fines of up to 20 million euros or 4% of an organization's total global turnover of the preceding fiscal year in cases of non-compliance.
Additionally, GRC saves organizations from financial and workforce burden by eliminating repetitive tasks. Compliance, in addition to other GRC features, help companies navigate the perils of avoidable overheads that can eat up a major chunk of their profits.
An intrinsic ability of GRC solutions to gauge adversaries that affect a company in the short, medium, and long term can guarantee a longer shelf life to the critical processes happening within. GRC gives leeway for organizations to prioritize critical functions and assets and aids in fortifying them (totally or partially) in the face of an inevitable operational risk, such as an external calamity like a pandemic, for instance. In such cases, when all other operations are compromised, these essential operations are up and running.
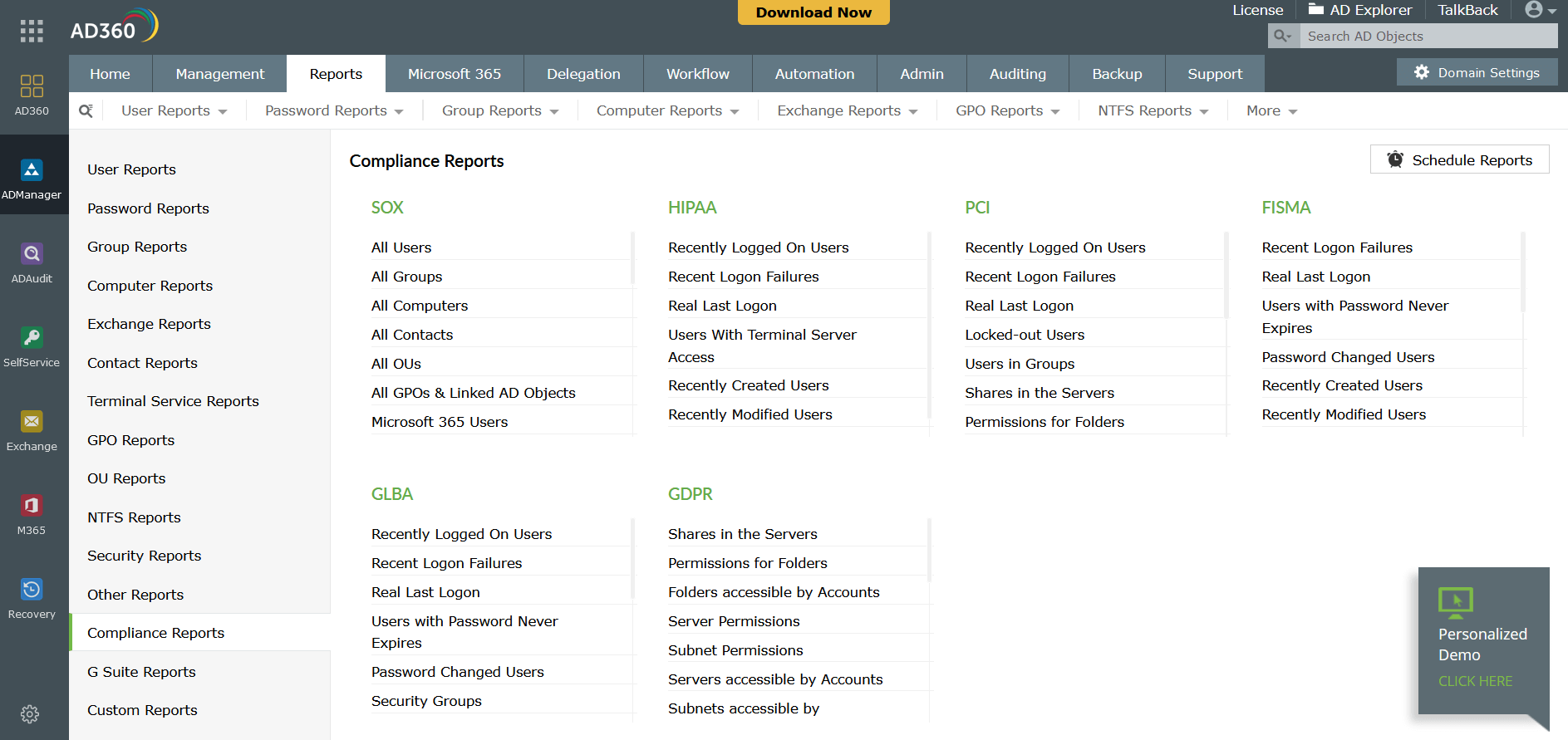
The AD360 suite has built-in features that can be mapped with the obligations of various regulatory frameworks such as:
A regulatory standard for organizations that store, process, transmit, and maintain protected health information. For an AD environment to be secure and protected from unauthorized access, it is essential to comply with HIPAA. AD360 fills the gap left by native tools when it comes to HIPAA compliance by providing an end-to-end audit trail providing insights on:
Additionally, AD360 guides organizations on compliance to the provisions of section 164.308 of the HIPAA framework.
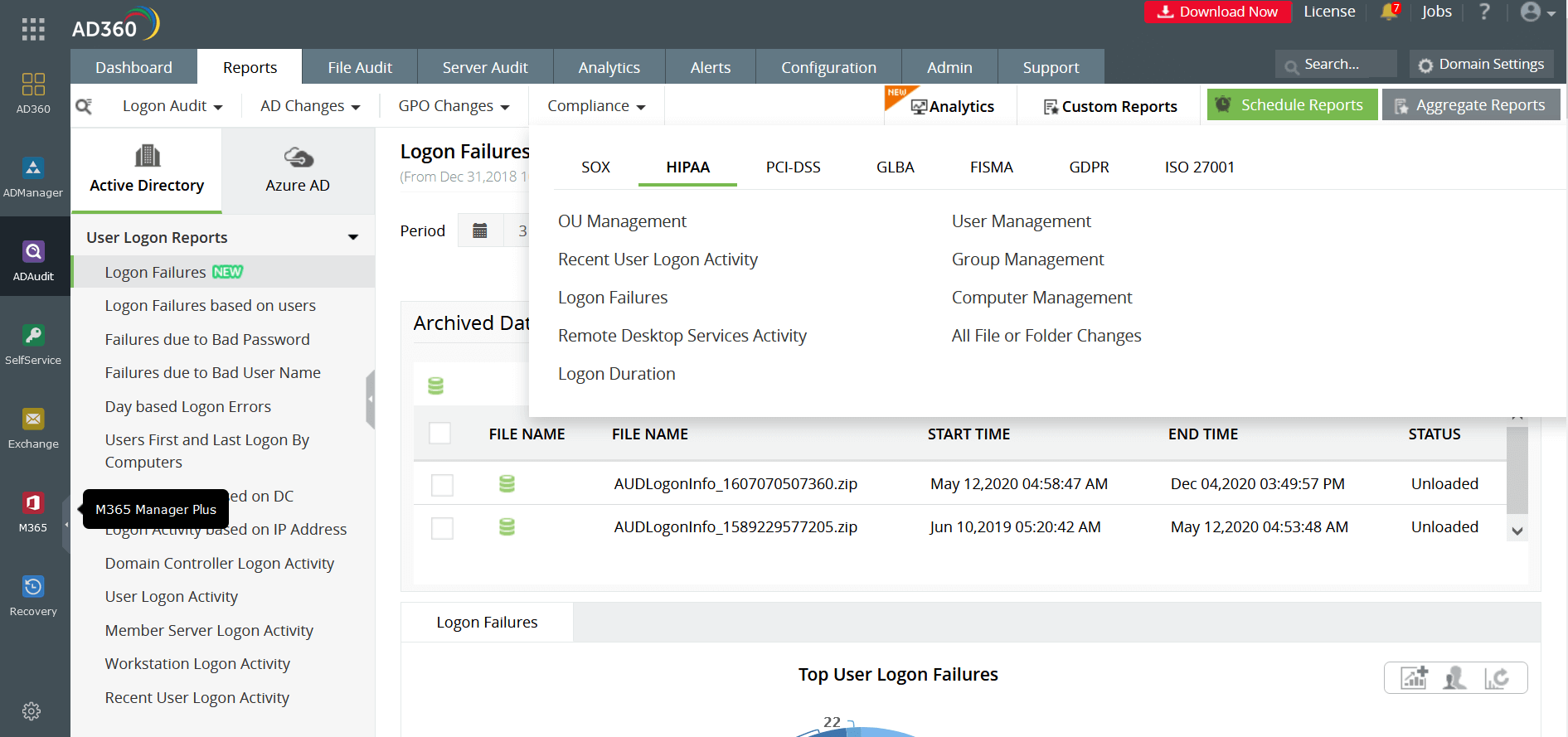
Introduced in 2002 by the US Congress, SOX aims to curb fraudulent financial practices by companies and its effect on investors. The key objectives of this legislation is to establish trusted internal controls, transparent financial disclosures, efficient auditing infrastructures, and policy making among companies. SOX compliance in an IT infrastructure can be achieved by putting the right identity and access management system in place, which aids in administering the internal controls of a company. AD360 performs Active Directory reports that can be categorized under sections of SOX compliance such as:
AD360 also helps organizations satisfy clauses that come under section 302 of SOX, which mandates a set of internal procedures created to ensure financial compliance.
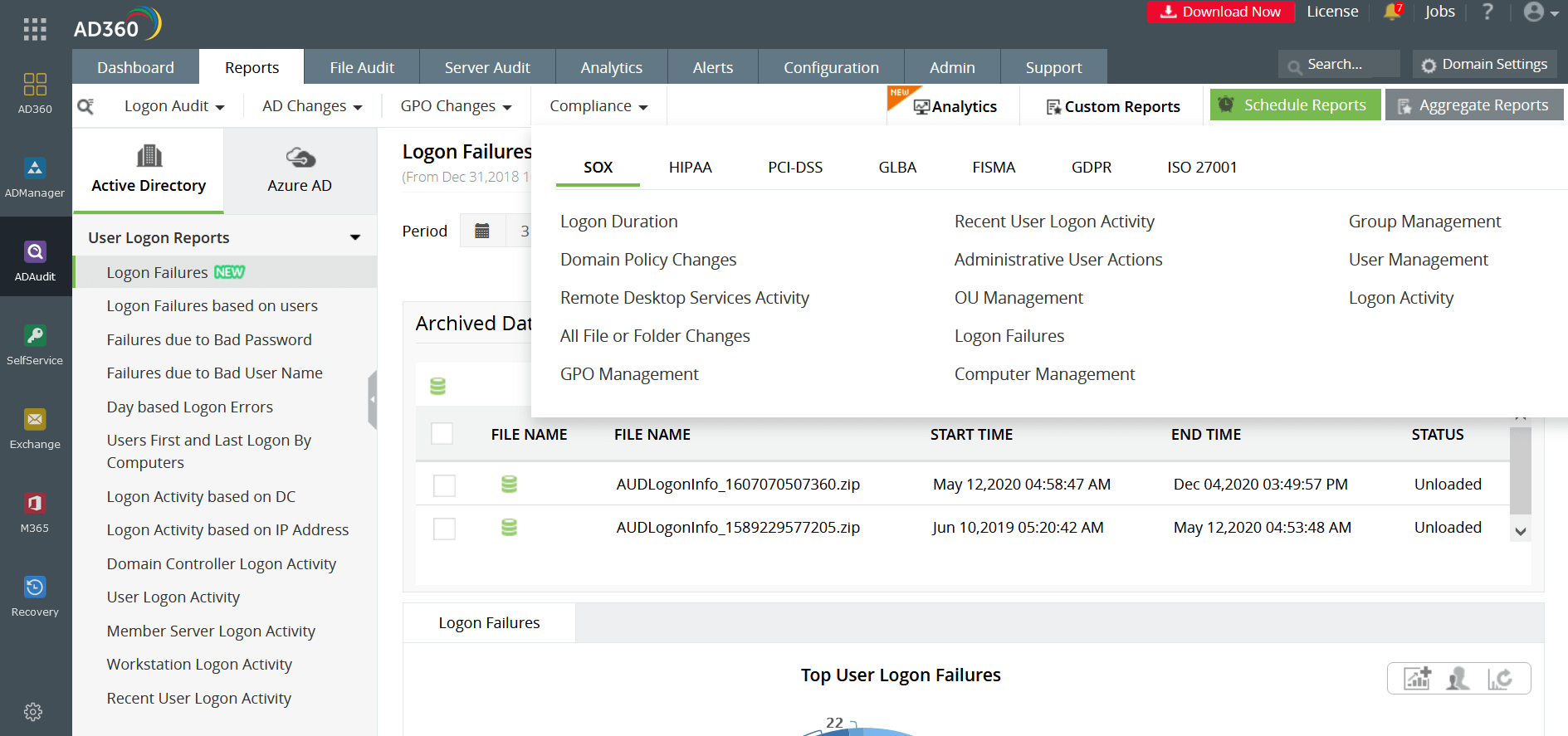
One of the most significant regulatory policies of the industrial climate at present, the central objective of the PCI DSS framework is to standardize and secure the operational and technical practices related to payment card information. Any business that accepts or processes payment card details must comply with PCI DSS.
Since the law directly addresses the transactional side of a business, being PCI DSS compliant can provide added assurance to customers regarding the security of their card-related information. PCI DSS compliance makes organizations trustworthy and reliable. With AD360 at the helm, restricted access to cardholder data can be enforced by implementing two-factor authentication and performing reports on logon attempts, audit policy changes, and permission changes among other operations.
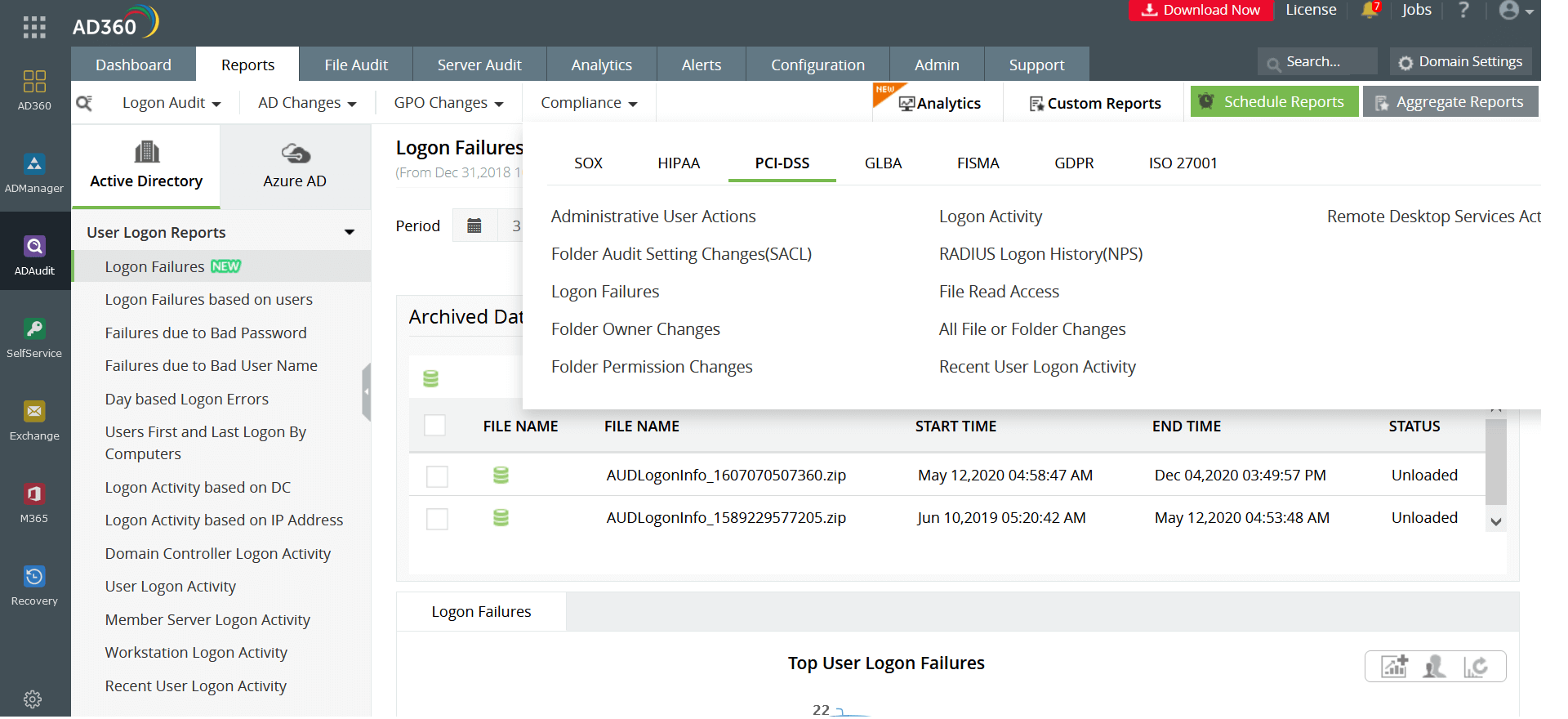
Passed in 2002, this US federal law requires federal agencies to secure their critical infrastructures and data assets. AD360 secures federal assets by monitoring the organization's Windows server environment and by notifying about changes with email notifications along with periodic reports. AD360 features a FISMA compliance kit to ease the adherence process.
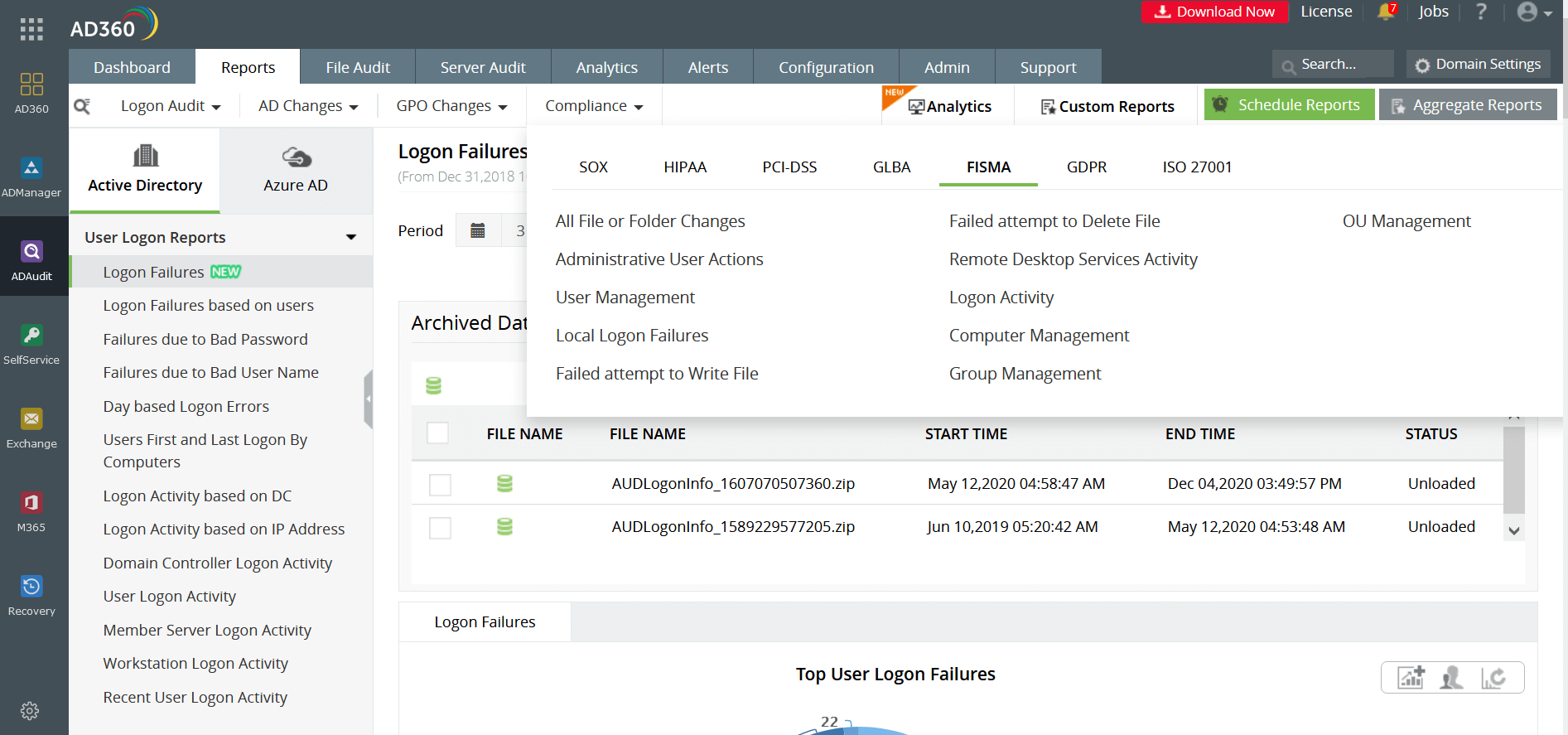
A regulatory framework that must be complied with by organizations that operate from or serve customers that belong to the European Union. The GDPR deals with securing the personal data of customers, employees, and prospects held by a company. AD360 ensures organizations are equipped with the appropriate measures that ensures GDPR compliance. With AD360, organizations can:
Furthermore, AD360 can fortify the personal data of organizations by checking logon attempts to detect unauthorized access. By providing visibility on login information, privilege escalations and other modifications in the user's life cycle, AD360 increases the ability of organizations to detect information breaches while ensuring GDPR compliance.
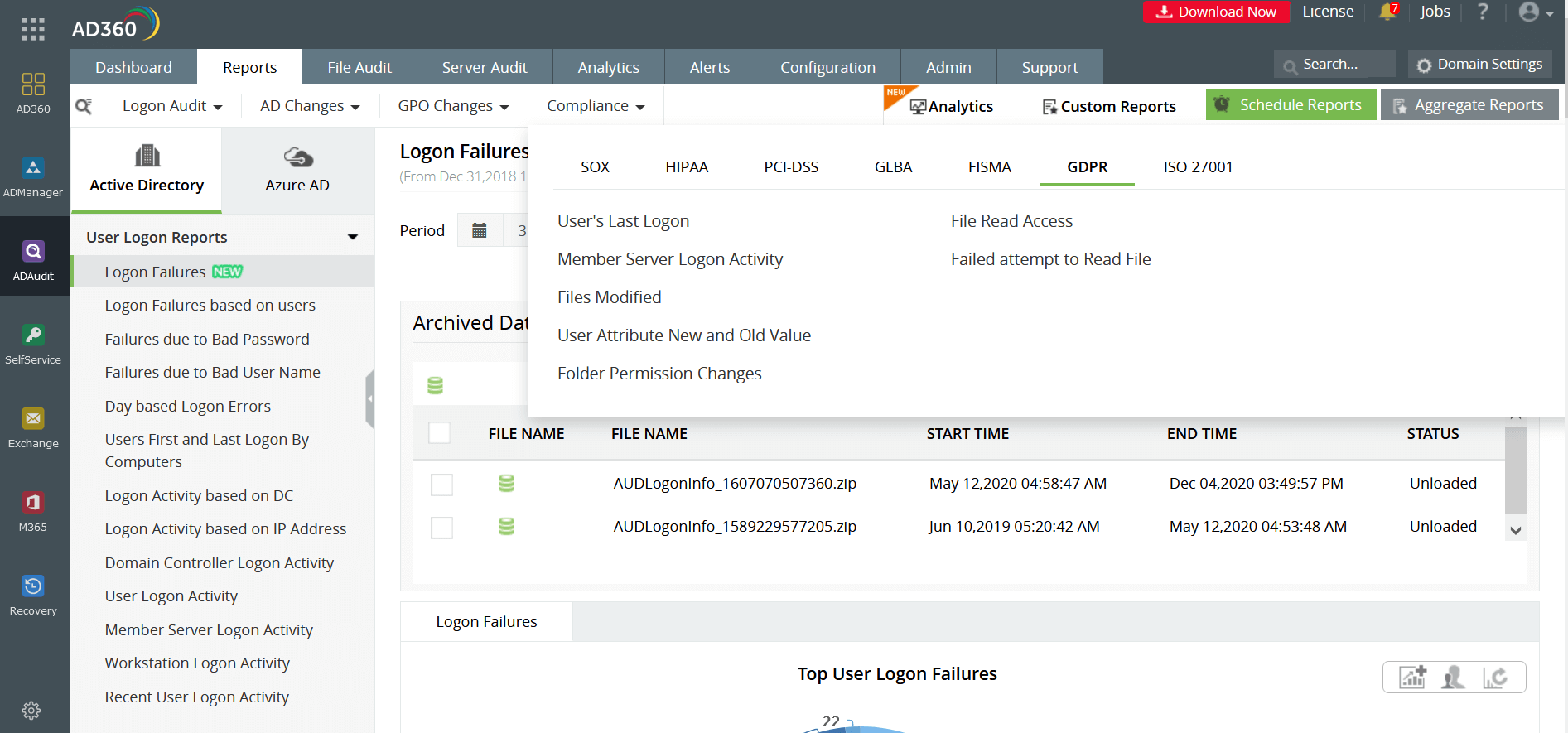
Also known as the Financial Services Modernization Act, the policy requires financial institutions—companies that offer consumers financial products or services like loans, financial or investment advice, or insurance—to be transparent about their information-sharing practices to their customers and to safeguard sensitive data. A mandatory compliance requirement for every financial organization, the GLBA also states that companies must secure their assets from foreseeable threats to security and data integrity. AD360 delivers preventive measures with 24/7 monitoring and easy-to-view preconfigured reports and alerts.
Emphasizes the need for companies to establish, implement, administer, and continually improve an information security management system within the context of an organization. ISO 27001 features 11 clauses, of which, four to 10 define the mandatory requirements to be met. AD360's ADAudit Plus repurposes event log data from across your Active Directory (AD) domain controllers, file servers, Windows servers, and workstations into real-time reports and alerts.
The LGPD governs the collection, usage, and processing of PII in Brazil. The LGPD directs organizations to implement an incident response plan that entails prompt reporting of security incidents. With customizable reports that can be generated in different file formats, ManageEngine AD360 can elevate an organization's incident reporting and response to help with LGPD compliance.
For instance, one of AD360's salient features is file integrity monitoring, which enables IT admins to detect any unauthorized attempts by users to tamper with or change the contents of critical documents.