Authentication of knowledge-based credentials (think passwords and PINs) can be vulnerable to attacks such as credential stuffing, brute force attacks, and over-the-shoulder attacks. To defend authentication from credential abuse, solutions have started accommodating personalized factors, thereby giving rise to multi-factor authentication (MFA). MFA requests an additional layer of verification factor that cannot be replicated.
However, to authenticate users that operate in a composite, hybrid environment—one that includes on-premises and cloud infrastructures—it is important for MFA to be instance-aware. As hybrid environments tend to accommodate devices that are not monitored by company-defined policies and solutions, organizations run the risk of adding a potential threat vector, or a weak link, to their supply chain. These gaps are addressed by adaptive authentication.
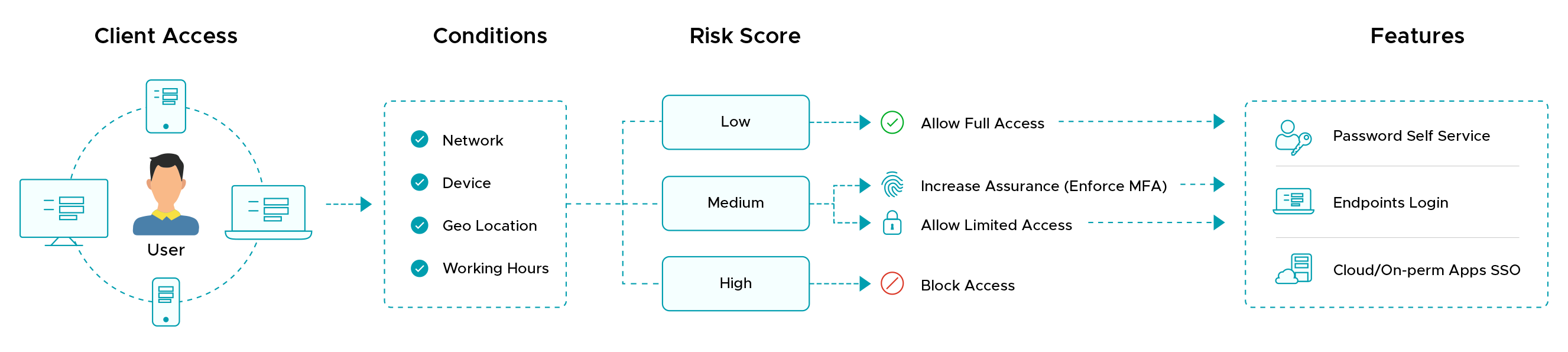
Upon verifying an endpoint, solutions must gauge contextual factors to change the stringency of their authentication measures. Adaptive authentication, also known as contextual or risk-based authentication (RBA), achieves this layered mechanism.
Adaptive authentication either steps-up or steps-down the intensity of verification after evaluating major indicators for deviant user behavior during the device posture scan. These indicators form a basis for the company's contextual access policies.
While standard password-based verification expects the user to provide a predictable set of credentials for verification, adaptive authentication goes a step beyond by gauging external factors to increase or decrease the stringency of authentication measures. It also expands the capabilities of MFA by rendering a context-aware approach to its operations. After determining a standard login procedure, implementing adaptive authentication strategy involves leveraging the risk profile.
A key metric to measuring an endpoint's potential vulnerability to threats, a risk profile helps implement adaptive authentication by taking contextual changes into account.
Adhering to the organization's PDP/PEP (Policy Decision Point/Policy Enforcement Point), a risk profile can be created by evaluating the following factors:
Based on their score (characterized as high, medium, or low), the intensity of authentication and further access can be determined by the authenticator. Access is granted for devices with a lower risk score and denied for those with a higher score.
If medium risk, the authenticator takes either of the following decisions:
To deliver urgent messages and send requests seeking additional stages of verification, authentication systems deliver push notifications to the users' devices via email, SMS, etc.
Triggering an MFA request is one of the most common actions undertaken by adaptive authentication. Some of the authentication factors requested include biometric data (such as fingerprints or facial recognition), security questions, and PIN requests.
Such as the FIDO U2F token, which can be used to access any online service that permits the FIDO U2F authentication protocol.
Adaptive authentication workflow
Some of the factors used to determine anomalous instances include:
Adaptive authentication solutions also leverage entity-based information to evaluate a client's identity. Device factors are of two types: device recognition and device context. While a device's recognition is based on its identity, such as manufacturer and model, context represents external factors, such as geolocation, network used, operating system configuration, browser type, etc. With the widespread adoption of BYOD, organizations are faced with the challenge of accommodating managed and unmanaged devices without compromising their security posture and policy enforcement.
This corresponds to the user's location and the associated risks. If a user tries to authenticate their identity from a remote area, adaptive authentication verifies the user's attempt by detecting their location using GPS coordinates or an IP address. Their environmental factor is weighed to detect suspicious travel activity and also block users that try to access an organizational network from a location that is forbidden by the organization.
User behavior can be a major indicator of anomalous digital activity. Some of the common pointers include log information, search history, keystroke dynamics, etc. To determine key behavioral attributes, adaptive authentication must derive insights from user-related information obtained from user and entity behavior analytics (UEBA) and security information and event management (SIEM) tools.
Role-based credentials, such as designation and date of joining, can be used to categorize users. The stringency of authentication can be meted out on the basis of their level of access to sensitive assets in the organization.
Adaptive authentication accommodates a wide range of instances, including:
| Factor | Use case | How can adaptive authentication solve this? |
|---|---|---|
| Device | When a user exhibits a drastic change in their device history. For example, an employee tries to log in to the organizational network via a new device, or when a contract device tries to log in. | Analyzes their digital footprint, such as user agent and browser cookies, and adds another layer of authentication based on the contextual factors (such as the operating system used) before allowing access. |
| Environmental | When networks are vulnerable to geo-targeted cyberattacks. Location-based targeting has emerged as a convenient technique for nation-state attackers to inflict cyberattacks on target countries. | Leverages the lookup table of geo-location coordinates formed by organizations and their respective IP addresses, based on which administrators can decide whether to allow or deny access. |
| Behavioral | A user enters incorrect credentials repeatedly during authentication. | Flags it as a suspicious action after a definite number of attempts and steps-up verification by requesting the user to provide personalized credentials. |
| Attribute | When a user requests access to a sensitive file. For example, when a non-administrative user requests access to a CSV file to onboard new users. | Designated users will have access to the asset after clearing one-step authentication. However, for a non-designated user to gain access, they have to complete multi-factor authentication, provided that the designated user has delegated access permissions to the resource. |
With adaptive access control, contextual awareness can be extended throughout a user's digital activity. According to NIST, adaptive access control authorizes user accounts by assessing their "identity, mission need, and the level of security risk that exists between the system being accessed and a user." Adaptive access control aims to optimize the findings obtained from adaptive authentication's risk profile to delegate access.