
- Overview
- Configuration
Aha!
Simplify user access to Aha! and ADSelfService Plus integration
Aha! is a comprehensive product development platform that helps teams align on a strategic roadmap and manage each phase of the development process, from the first idea to product delivery. Integrating ADSelfService Plus with Aha! provides users with single-click SSO access, simplifying login and enhancing security.
Enable one-click access to Aha! through SSO
Streamline access to Aha! with secure, single-click login, allowing teams to focus on product development without login delays.
Enhanced security with advanced authentication
Strengthen access to Aha! by implementing MFA options like FIDO2 and biometrics, ensuring only authorized users can log in.
Passwordless authentication for a simplified experience
Reduce user dependency on passwords, making it easier and more secure for users to access Aha! without password-related issues.
Configuring SAML SSO for AHA!
These steps will guide you through setting up the single sign-on functionality between ADSelfService Plus and AHA!.
Prerequisite
- Login to ADSelfService Plus as an administrator.
- Navigate to Configuration → Self-Service → Password Sync/Single Sign On → Add Application, and select AHA! from the applications displayed. Note: You can also find AHA! application that you need from the search bar located in the left pane or the alphabet wise navigation option in the right pane.
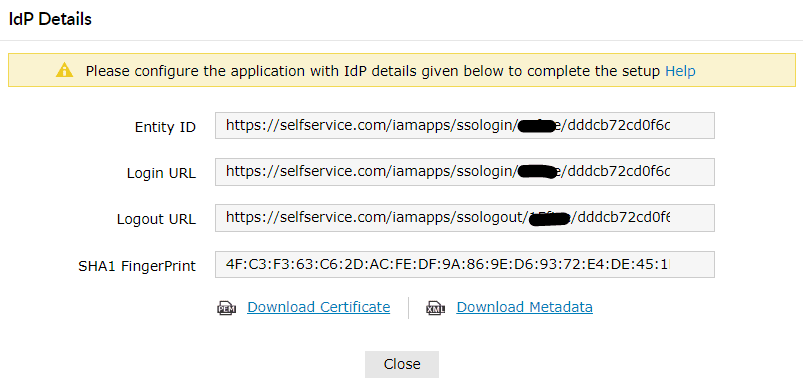
- Click IdP details in the top-right corner of the screen.
- In the pop-up that appears, copy the Login URL, SHA1 Fingerprint and download the SSO certificate by clicking on the Download Certificate link.
AHA (Service Provider) configuration steps
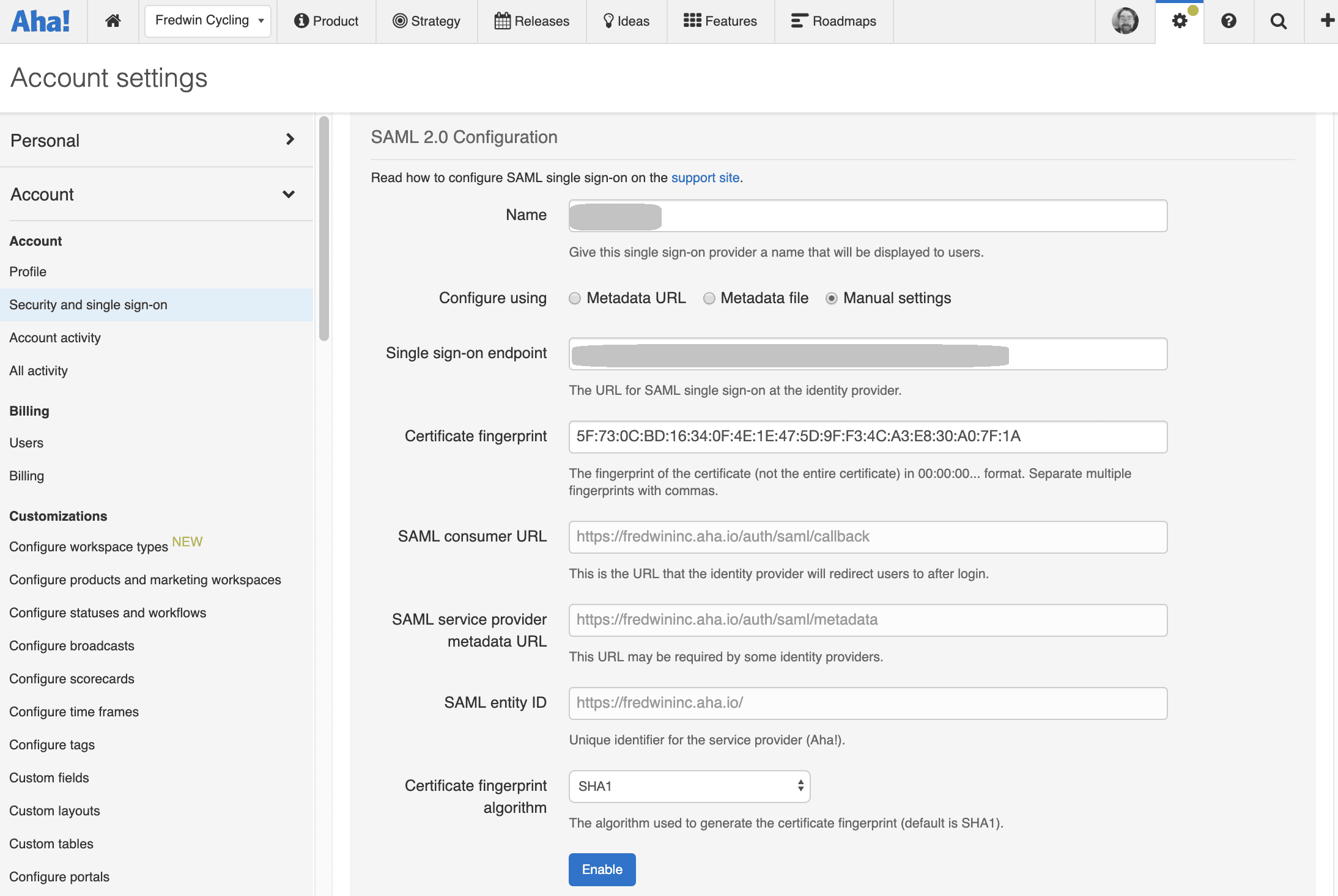
- Login to AHA! with an administrator’s credentials.
- Navigate to Settings Icon → Account → Security and single sign-on.
- Choose SAML 2.0 Provider from the Identity provider dropdown.
- Name your configuration.
- Choose Manual settings.
- Paste the copied URL, from Step 4 of Prerequisite, in the respective URL fields.
- Select certificate fingerprint as SHA1.
- Click Enable to save the configuration.
ADSelfService Plus (Identity Provider) configuration steps
- Now, switch to ADSelfService Plus’ AHA! configuration page.
- Enter the Application Name and Description.
- In the Assign Policies field, select the policies for which SSO need to be enabled. Note: ADSelfService Plus allows you to create OU and group-based policies for your AD domains. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy.
- Select Enable Single Sign-On.
- Enter the Domain Name of your AHA account. For example, if you use johndoe@aha.com to log in to aha, then aha.com is the domain name.
- Enter the sub-domain name of your AHA! portal in the SP Identifier field. Example format: https://
.aha.io - In the Name ID Format field, choose the format for the user login attribute value specific to the application. Note: Use Unspecified as the default option if you are unsure about the format of the login attribute value used by the application.
- Click Add Application. Note: For AHA!, both IdP-initiated and SP-initiated flows are supported.