File shadowing with Device Control Plus
Device Control Plus offers file shadowing as a proactive approach to protecting your valuable data. Also known as data mirroring, this feature prevents the loss of sensitive files by storing a copy of the original file in a secured location whenever they are transferred from a computer to USB devices. Following are the five simple steps to configure this feature using Device Control Plus:
- Selecting devices on which to enable file shadowing.
- Choosing file size limits and excluding file extensions.
- Configuring Remote Share Path.
- Mapping policy to custom groups.
- File shadowing reports.
Selecting devices on which to enable file shadowing.
With Device Control Plus, file shadowing or data backup can be easily implemented for all types of USB devices. On top of this, to optimize bandwidth, the policy can be applied to a handpicked selection of devices, so that only the file activities of those devices gets shadowed.
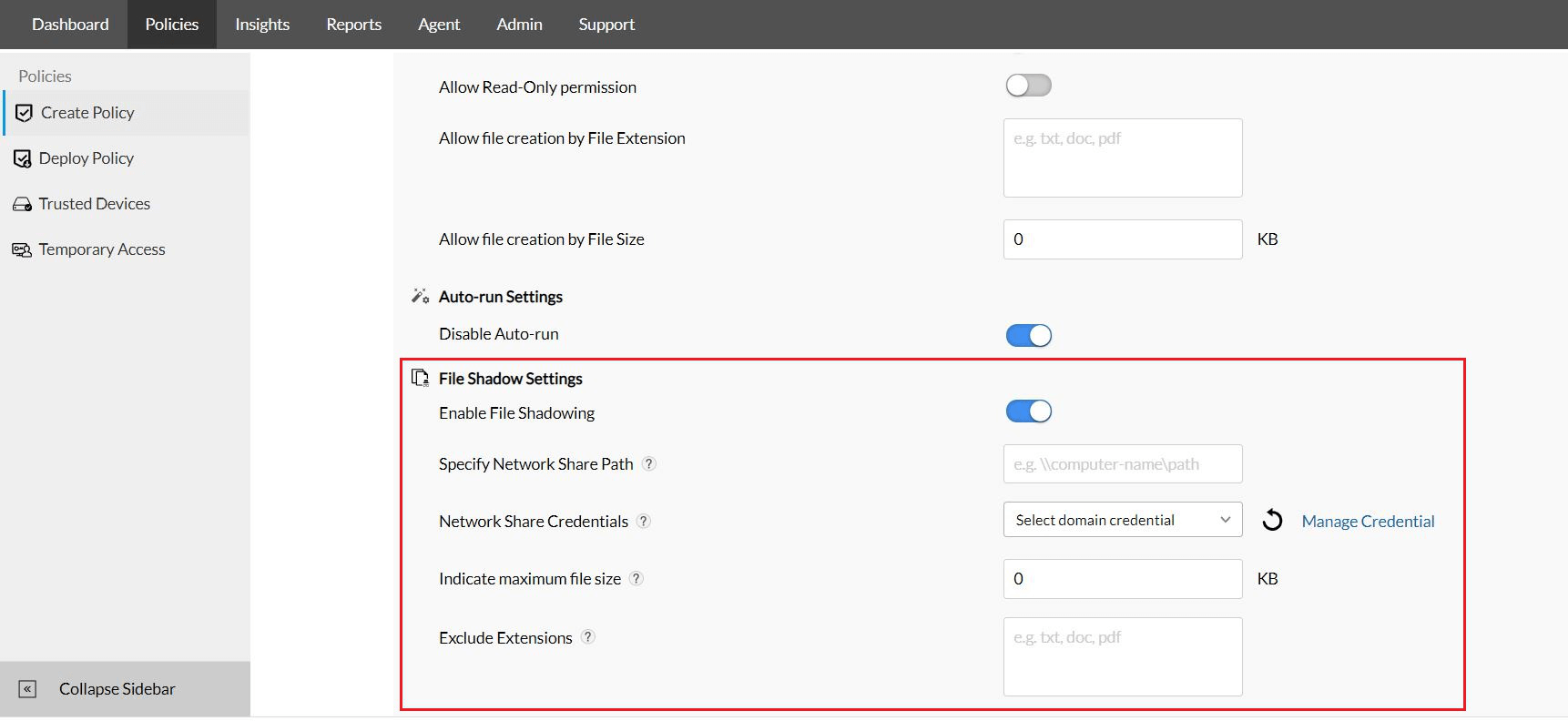
Choosing file size limits and excluding file extensions.
Since file shadowing is a data-intensive operation, in addition to being able to select the specific devices, Device Control Plus also offers provisions to determine the type of data that gets shadowed. A file size limit can be set so that files exceeding a certain size are excluded from file shadowing. Furthermore, files can also be filtered based on their extensions so that certain file types like video or audio files can be excluded from file shadowing.
Note: Device Control Plus' file tracing feature can still track files that exceed the size limit or were excluded based on extension.
Configuring Remote Share Path.
The share folder containing the shadowed copies can occupy a significant portion of disk space, which is why it's important to have a dedicated location for storing these copies. For the most effective file shadowing, this location should be remote.
With Device Control Plus, once a location has been determined, the path can be selected so that as soon as file operations are conducted by the shadowed devices, the copied data is promptly moved to the remote destination indicated by that path. The domain credentials used to access the remote share where the mirrored data is stored can also be configured for added security.
Mapping policy to custom groups.
Once a file shadow policy is created, it can then be mapped to custom groups comprised of specific endpoints. Being able to select the particular devices, file types, and endpoints that are involved with handling and transferring classified information ensures that while critical data is consistently copied and maintained in the file shadow database, disk space is also optimized accordingly.
File shadowing reports.
As soon as the file shadowing policies are applied, extensive audits will be generated in real-time. The logs will include details such as the devices, endpoints, and users involved in the operation as well as the file name and the time it was shadowed. The logs are readily available always and are excellent for analysis of file shadow actions performed across the enterprise.
For rapid recovery, download a 30 day, free trial of Device Control Plus and leverage this file shadowing solution!