Securing the digital foundation: A CXO's guide to SDLC security

Summary
This article explains why SDLC security is critical in today’s threat landscape and how organizations can embed security into every phase of the software development life cycle. It covers the benefits of a Secure SDLC (SSDLC), best practices for secure coding, testing, and vulnerability management, and the role of compliance in shaping security processes.
The piece also explores how DevSecOps extends SSDLC by automating and integrating security into CI/CD pipelines. Finally, it provides actionable strategies for CXOs, including fostering a security-first culture, automating controls, managing third-party risks, gamifying security awareness, and adopting a risk-based approach to remediation.
For today's IT leaders, checking for vulnerabilities right before deployment is a relic of the past. It's like building a skyscraper and only calling in the safety inspector on the day it opens. The cost of fixing flaws at this stage is astronomical, and the risk of a breach is dangerously high. According to IBM's Cost of a Data Breach Report 2025, the global average cost of a data breach is USD 4.4 million.
This is why a secure software development life cycle (SSDLC) is no longer a luxury but a strategic necessity. It's a fundamental shift, embedding security into every phase of the software development life cycle (SDLC), from the first line of code to the final release. This proactive, shift-left approach identifies and mitigates risks early, when they're easiest and cheapest to address, building security directly into your digital foundation.
The high stakes of software vulnerabilities
The consequences of a security breach can be catastrophic for any business. Beyond the immediate financial losses, a breach erodes customer trust, damages the brand's reputation, and can lead to significant legal and regulatory penalties. Examples are abundant and serve as cautionary tales.
The Equifax data breach in 2017, for instance, exposed the personal data of over 163 million people, a direct result of a known, unpatched vulnerability in a third-party software component. The incident underscored the critical importance of a robust process for managing and updating open-source libraries within the SDLC. Incidents like this are a stark reminder that software is a primary attack vector, and an SSDLC is your best defense.
DevSecOps: Extending SDLC security into operations
The next logical step beyond an SSDLC is DevSecOps. It's the practical, cultural evolution that fully integrates security across the entire DevOps pipeline. While an SSDLC establishes the framework, DevSecOps provides the how-to, embedding security into a continuous, automated process.
These are three key pillars of a DevSecOps model:
- Continuous security integration: Security tools are embedded into continuous integration and continuous deployment (CI/CD) workflows, providing developers with immediate feedback on vulnerabilities.
- Shared accountability: Developer, operations, and security teams collaborate seamlessly, ensuring faster remediation.
- Agility with assurance: DevSecOps enables organizations to maintain rapid release cycles without compromising their security posture.
For CXOs, DevSecOps represents the alignment of speed, scalability, and security. This turns potential bottlenecks into competitive advantages.
The benefits of SDLC security
Adopting an SSDLC model yields significant advantages for enterprises:
- Reduced costs: Catching vulnerabilities early prevents the exponential costs of late-stage fixes.
- A stronger compliance posture: Regulations such as the GDPR, HIPAA, and the PCI DSS become easier to meet with security woven into processes.
- A faster time to market: Automated testing and integrated controls reduce delays caused by last-minute security fixes.
- Improved customer trust: Demonstrating that security is prioritized strengthens the brand's credibility.
- Long-term resilience: A security-first culture ensures ongoing adaptability against evolving cyberthreats.
How to build SDLC security into the DNA of your development
Building an SSDLC requires a multifaceted approach that integrates a mix of automated tools and best practices across the development life cycle.
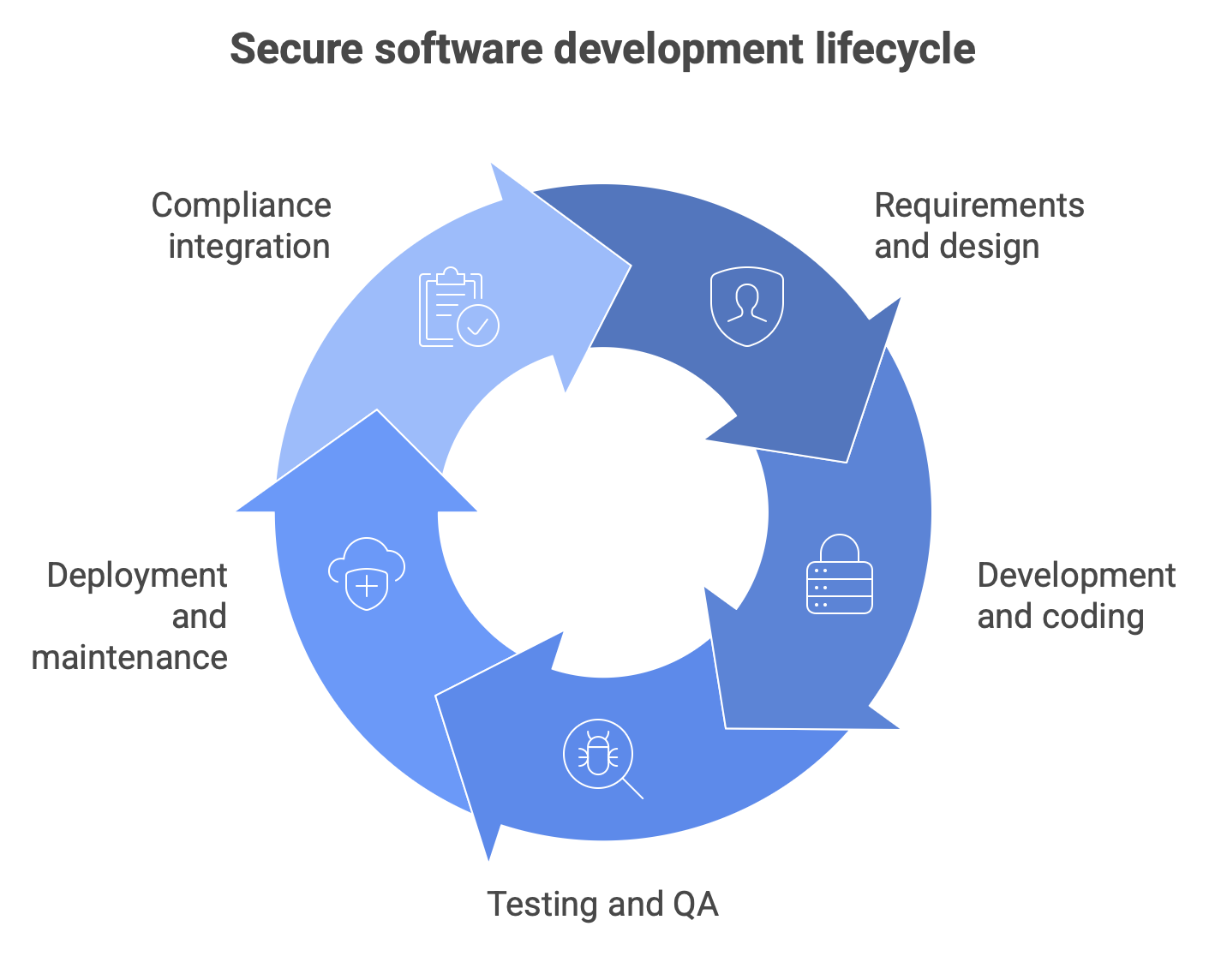
- Requirements and design: Security begins long before a single line of code is written. At this stage, teams conduct threat modeling to proactively identify potential threats and vulnerabilities. They also define clear security requirements, ensuring they are treated with the same importance as functionality requirements.
- Development and coding: Developers are the first line of defense. By providing training on secure coding practices and implementing automated security testing, you can catch vulnerabilities as they are created. This is where tools like static application security testing (SAST) solutions come in, scanning the source code to identify flaws without running the application. It's like having a real-time spellchecker for security vulnerabilities.
- Testing and quality assurance (QA): Security is a shared responsibility. During this phase, security and QA teams collaborate to validate the software's security. A dynamic application security testing (DAST) tool simulates an attacker's perspective on a running application, probing it for weaknesses. For a more comprehensive review, penetration testing by ethical hackers can uncover vulnerabilities that automated tools might miss.
- Deployment and maintenance: Security doesn't end when the software is released. The CI/CD pipeline should include automated security checks to prevent vulnerable code from reaching production. Post-deployment, continuous vulnerability management and monitoring are essential to detecting and responding to new threats.
- Compliance integration: An SSDLC also helps align development practices with regulatory frameworks such as the GDPR, HIPAA, and the PCI DSS. By embedding compliance checks into each phase of the life cycle (requirement gathering, design reviews, code scans, and release approvals), organizations can demonstrate due diligence, avoid penalties, and streamline audits.
Implementing SDLC security: Actionable strategies for CXOs
For CXOs, the mandate is clear: constantly advocating to adopt and enable a pervasive culture of security across the organization. The following strategies are essential to driving this transformation:
- Requirements and design: Security begins long before a single line of code is written. At this stage, teams conduct threat modeling to proactively identify potential threats and vulnerabilities. They also define clear security requirements, ensuring they are treated with the same importance as functionality requirements.
- Development and coding: Developers are the first line of defense. By providing training on secure coding practices and implementing automated security testing, you can catch vulnerabilities as they are created. This is where tools like static application security testing (SAST) solutions come in, scanning the source code to identify flaws without running the application. It's like having a real-time spellchecker for security vulnerabilities.
- Testing and quality assurance (QA): Security is a shared responsibility. During this phase, security and QA teams collaborate to validate the software's security. A dynamic application security testing (DAST) tool simulates an attacker's perspective on a running application, probing it for weaknesses. For a more comprehensive review, penetration testing by ethical hackers can uncover vulnerabilities that automated tools might miss.
- Deployment and maintenance: Security doesn't end when the software is released. The CI/CD pipeline should include automated security checks to prevent vulnerable code from reaching production. Post-deployment, continuous vulnerability management and monitoring are essential to detecting and responding to new threats.
- Compliance integration: An SSDLC also helps align development practices with regulatory frameworks such as the GDPR, HIPAA, and the PCI DSS. By embedding compliance checks into each phase of the life cycle (requirement gathering, design reviews, code scans, and release approvals), organizations can demonstrate due diligence, avoid penalties, and streamline audits.
Building trust through security
In an era of increasing cyberthreats, an SSDLC is a strategic investment in your company's future. By embedding security in every step of the development process, you not only protect your digital assets but also build trust with your customers and a reputation for reliability. An SSDLC goes beyond technology; it is a commitment to making security a core part of your business strategy.