Various information security guidelines, including those from the NIST (National Institute of Standards and Technology), recommend that organizations manage their SSH keys and track all access and activities. However, that may be easier said than done.
To manage keys effectively, you need a comprehensive auditing and tracking mechanism. You must track all active and inactive SSH keys in the network. Active keys should be changed periodically and inactive keys should be deleted. To track user actions, organizations must control and regulate access to the keys, identify who has access to what, log all access by users, and record their operations during privileged SSH sessions. When users leave the organization, their keys must be deleted, and their access terminated. Organizations need trails to make sure all these crucial activities are being properly executed.
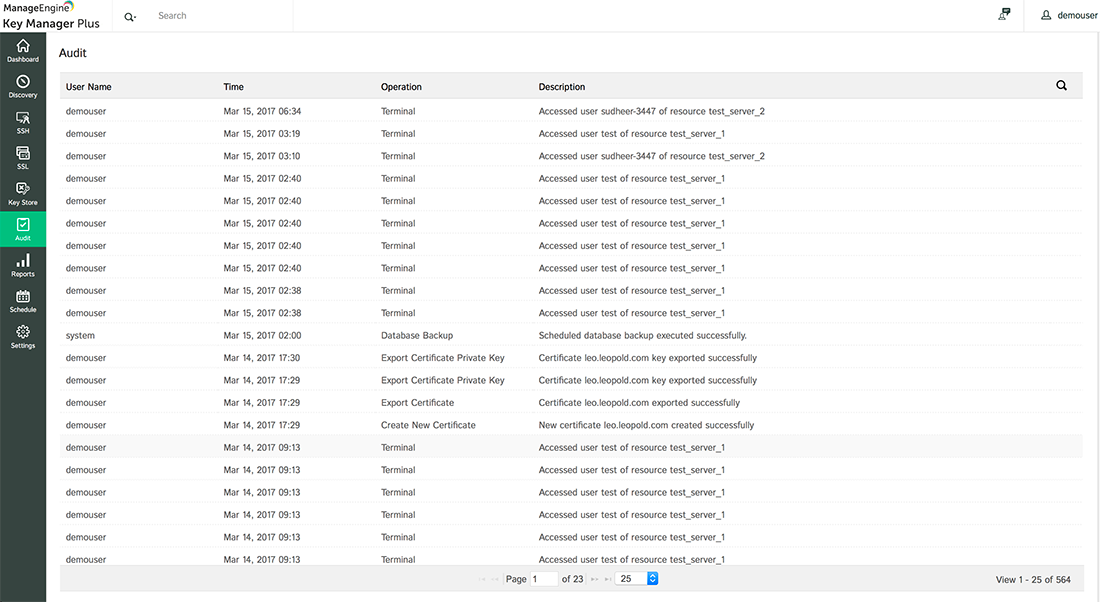
Key Manager Plus helps establish a sound auditing mechanism around the use of SSH keys. It captures all activities executed in the application as audit trails, including the time and result of the execution, the IP address from which the action was performed, and other details. In addition, Key Manager Plus's first-in-class session recording mechanism video records the operations performed by the users during any privileged sessions launched from the application. The recorded sessions serve as records for forensic examination and can be played back at any time.
Administrators can instantly generate reports to review or demonstrate the effectiveness of SSH key management in the organization. The entire life cycle of the keys—from the moment they are created, deployed, accessed, and updated, to the moment they are deleted—is captured in real time by Key Manager Plus.