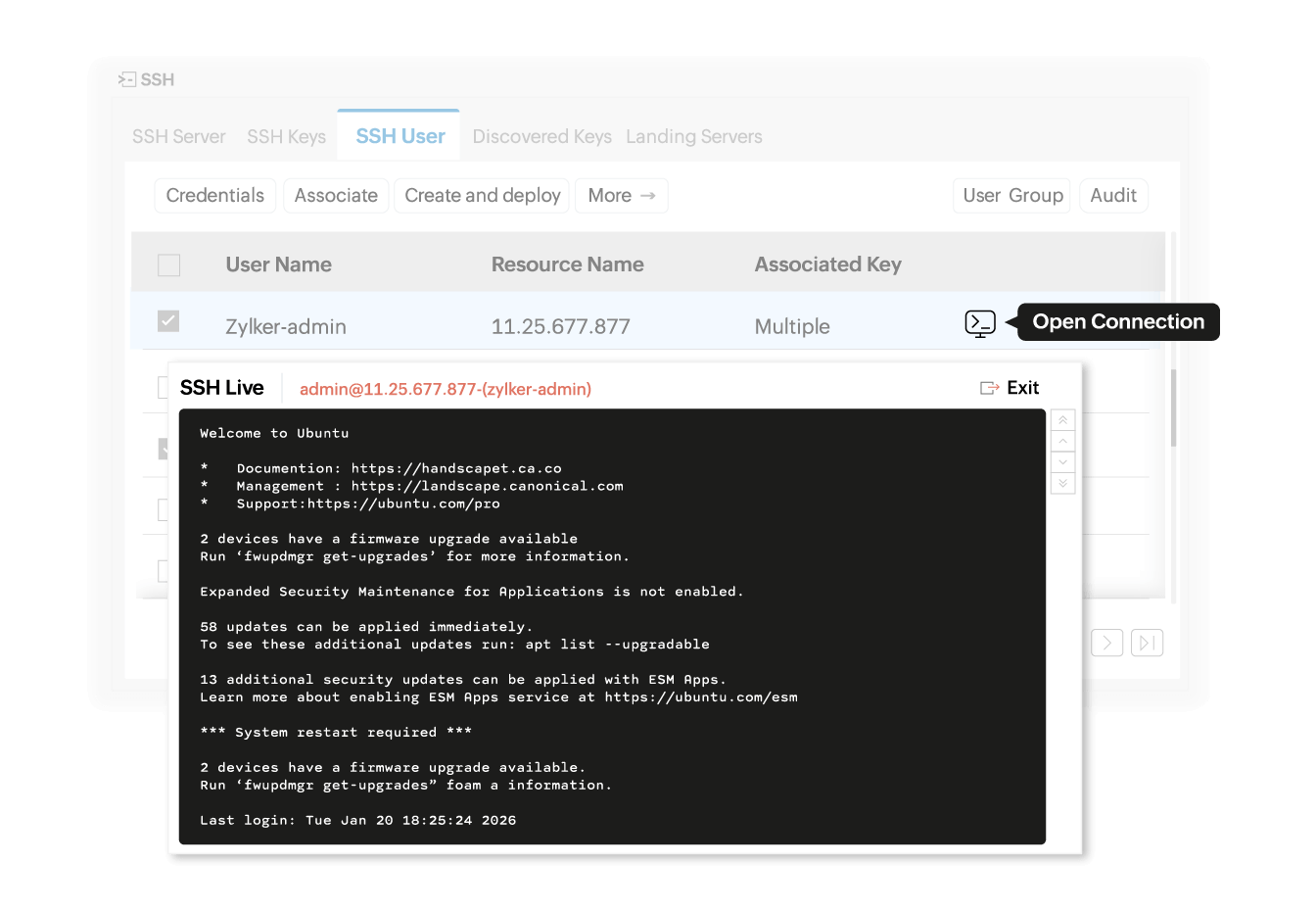
Connect directly with remote servers
Eliminate the hassle of manually entering keys each time you connect to remote systems. Key Manager Plus automates the entire remote access process, delivering credentials and launching secure shell sessions in a single click.
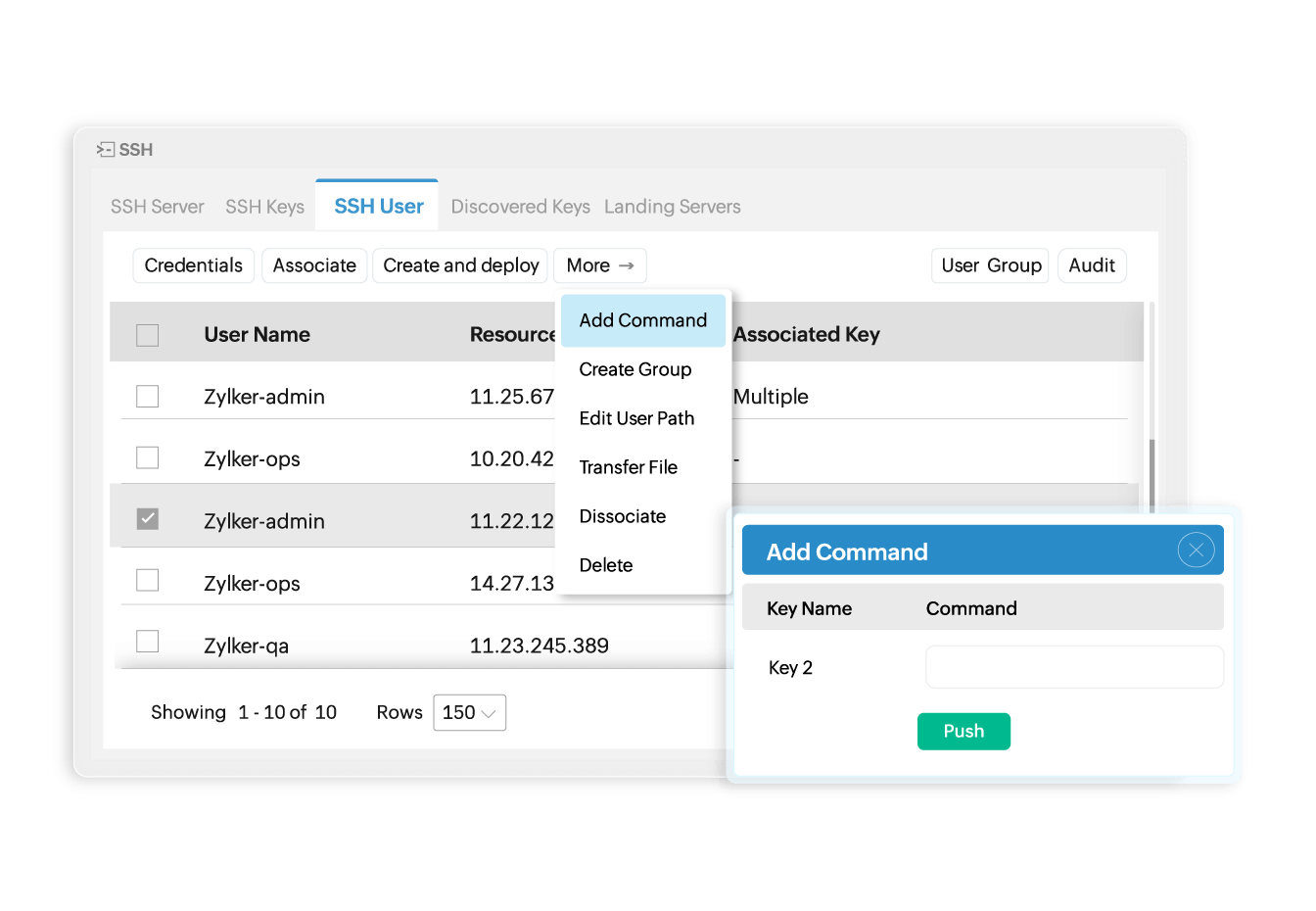
Fortify connections by defining pre-approved commands
Prevent unauthorized command execution and data extraction during remote sessions. Key Manager Plus enables you to define approved commands when launching a connection using an SSH key, ensuring only those pre-approved commands can be performed during remote connection.
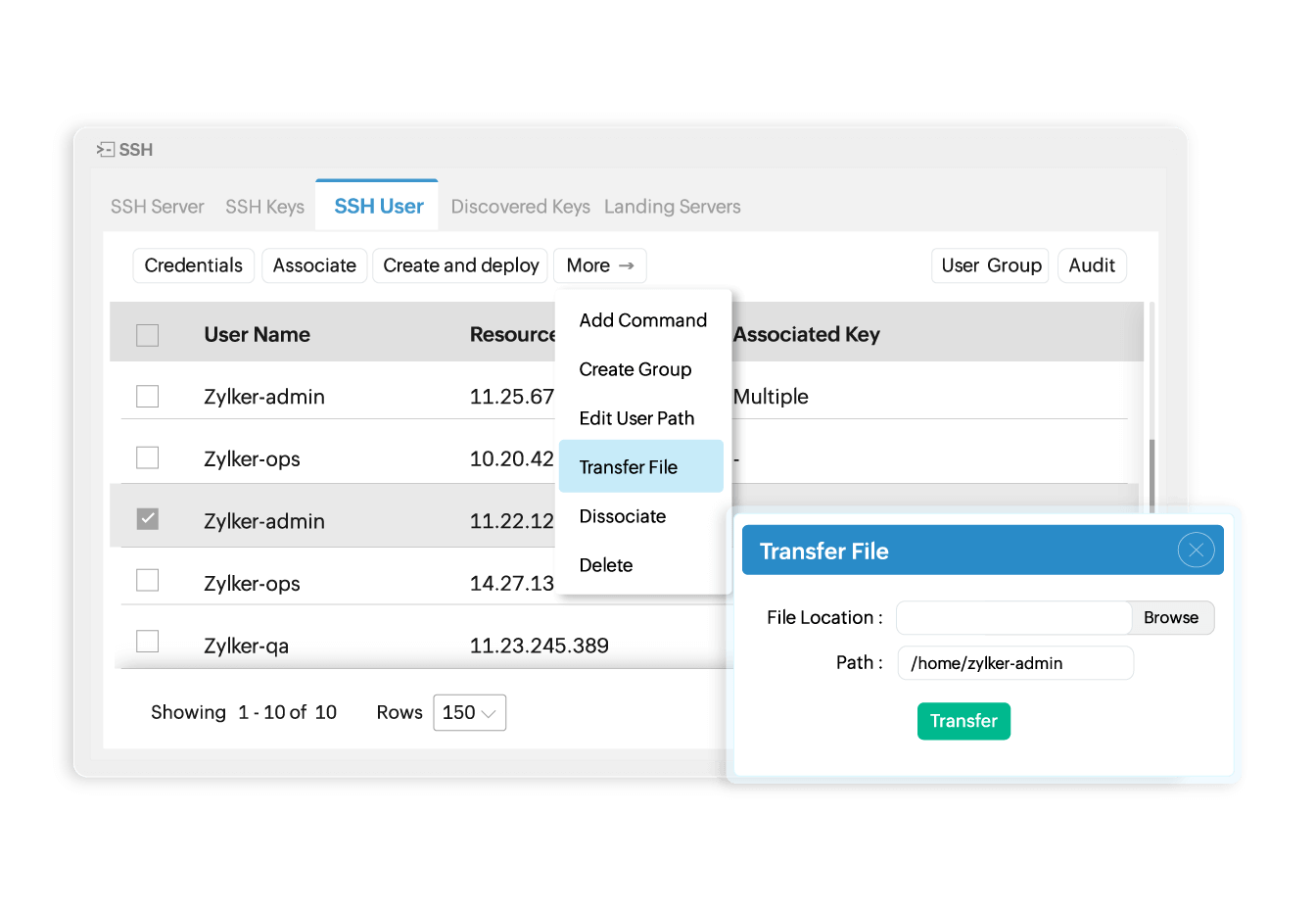
Securely transfer files
Securely transfer files across your infrastructure through the Secure Copy Protocol. Key Manager Plus enables you to safely transmit files to target servers through encrypted SSH tunnels.
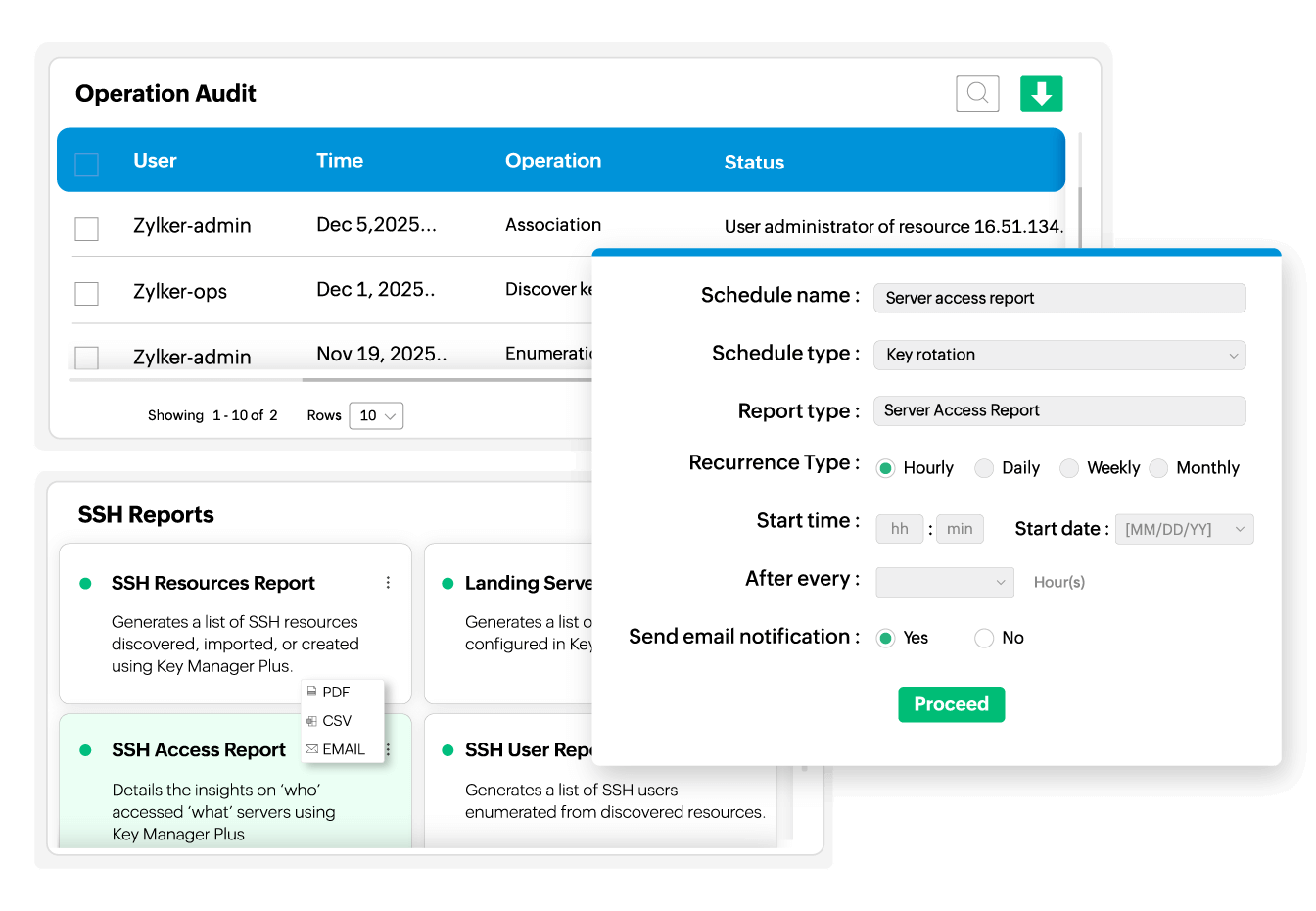
Get comprehensive audits and reports
Get full visibility of all SSH-key-based remote connections with Key Manager Plus' comprehensive audit trails, including details on the accessing user, target server, SSH key used, time of access, and more. Further, generate on-demand or scheduled reports for all server access activity and export them as a PDF or CSV file, or get them via email.