On this page
Every day, your Active Directory generates thousands of events. Account logins. Password changes. Group memberships modified. Permissions adjusted. The logs pile up relentlessly, a torrent of data that should tell you exactly what's happening in your identity infrastructure.
But here's the uncomfortable truth: most IT teams are drowning in AD events while starving for actual insights.
The problem isn't that AD doesn't log enough. It's that it logs too much of the wrong things and not enough of the right things, all in a format that turns critical security investigations into archeological expeditions through cryptic event IDs and XML fragments.
Meanwhile, the threats you need to catch—insider access abuse, privilege escalation, policy drift—are buried somewhere in that avalanche of noise, invisible until it's too late.
The smartest enterprise IT teams have stopped accepting this trade-off. They're demanding something different: AD auditing that cuts through the noise, surfaces real threats, and delivers actionable intelligence when it matters most.
The native AD logging trap
Native Active Directory auditing isn't exactly broken. It's more like a smoke detector that goes off every time you make toast. It is technically functioning, but so noisy that everyone learns to ignore it.
Microsoft built AD logging for basic forensic reconstruction, not for real-time threat detection or operational intelligence. The result is a system that generates massive volumes of low-value events while missing critical context that would make those events meaningful.
Event ID cryptography and context gaps
When AD logs an event, you get an event ID number, a timestamp, and a collection of attributes that might include the information you need, if you know where to look and how to interpret it.
For example, event ID 4728 tells you someone was added to a security-enabled global group. Sounds useful, right? Except it doesn't tell you what group memberships that person already had, what new access this membership actually grants them, or whether this represents a dangerous privilege escalation or routine access provisioning.
Was this user added to Domain Admins? That's critical. Added to the Marketing department group? Probably routine. Native logs treat both events identically. You're left connecting dots manually across multiple event entries and directory queries, and dependent on institutional knowledge about which groups take precedence and which are mission-critical to safeguard.
The old value problem compounds this challenge. When permissions change, group memberships are modified, or security policies are updated, native logs capture the new state but rarely preserve what existed before. Seeing that a GPO changed is marginally useful. Seeing that it changed from requiring fifteen-character passwords to eight-character passwords? That's a security regression that demands immediate investigation.
Without before-and-after context, you're analyzing changes in isolation, unable to assess whether each modification strengthens or weakens your security posture.
Volume without value
Native AD auditing operates on the premise that more logging equals better visibility. Enable the right audit policies and you'll capture thousands of events per hour—authentication successes, Kerberos ticket requests, directory service access, and countless other activities.
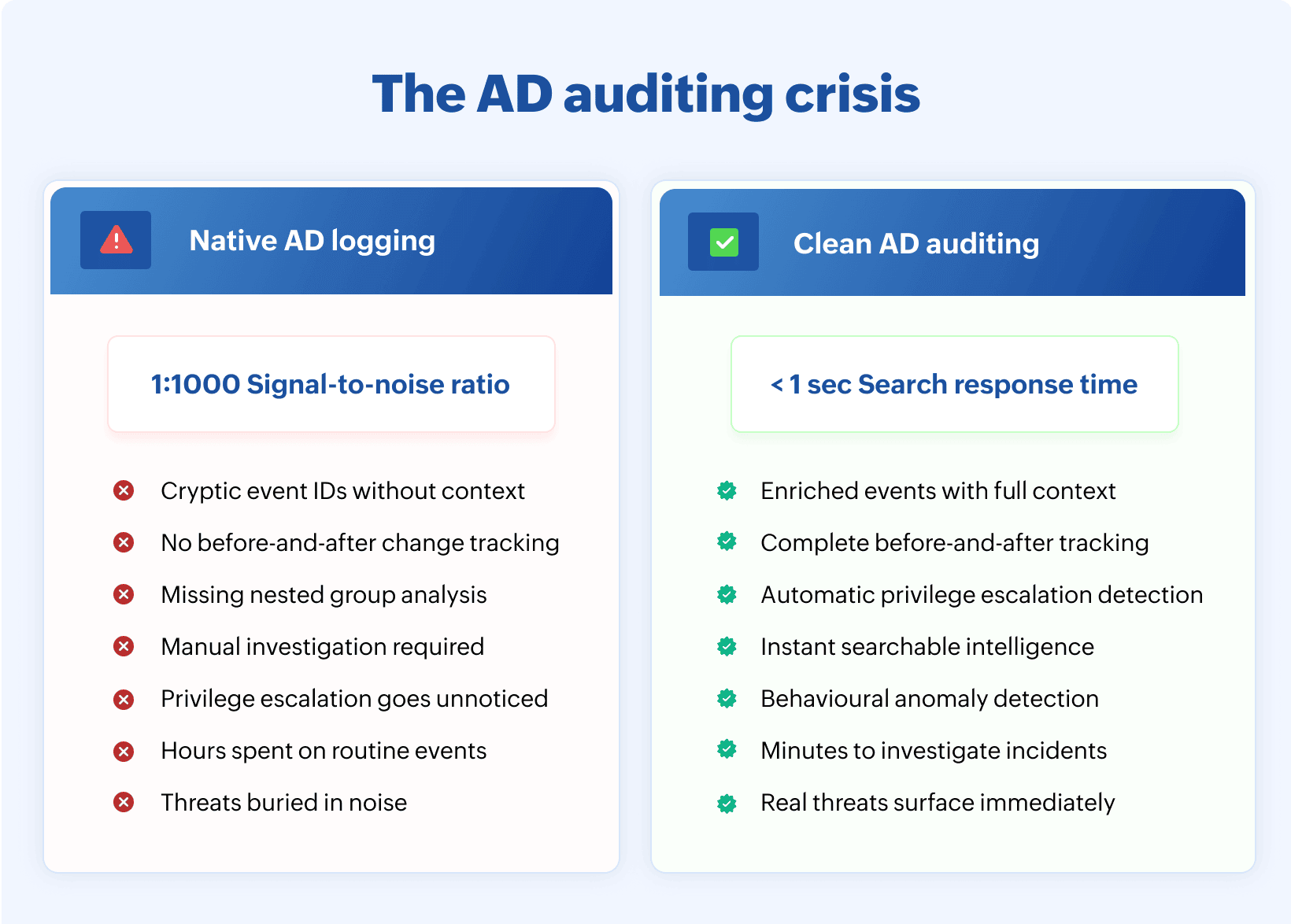
Most of these events represent normal operations. Users logging in. Applications authenticating. Scheduled tasks running. The signal-to-noise ratio hovers somewhere around 1:1000, meaning IT teams must sift through a thousand routine events to find one that actually matters.
This volume problem doesn't just create storage challenges. It creates an investigation bottleneck that turns every security incident into a time-consuming manual analysis project. When auditors request evidence of who had privileged access during a specific timeframe, you're left reconstructing that information from raw event logs, cross-referencing multiple event types, and hoping you haven't missed anything critical.
The filtering problem gets worse as environments grow. Small organizations with a few hundred users might manage with native logging and manual investigation. Enterprise environments with tens of thousands of users, complex OU structures, and nested group hierarchies? Native logs alone become effectively unusable for anything beyond basic forensic reconstruction.
Retention and correlation challenges
Native AD logs live in the Windows Event Log system, which has practical retention limits based on log file sizes. Configure aggressive retention and you'll consume massive storage. Accept shorter retention periods and you lose the historical data needed for compliance requirements and trend analysis.
Organizations typically compromise with 30-60 day retention, enough to meet basic security needs but insufficient for comprehensive compliance frameworks that require access to audit data for years. When auditors request documentation of who had access to what six months ago, you're often explaining gaps in the audit trail rather than providing evidence.
Correlation presents another fundamental limitation. AD events exist in isolation from other security telemetry. When suspicious AD activity occurs—say, a service account suddenly granted administrative rights—you need to understand what else was happening simultaneously. Were there unusual login attempts? Unexpected network connections? Suspicious file access patterns?
Native logs can't answer these questions. They document what happened within AD, full stop. Correlating AD events with firewall logs, endpoint detection data, email security events, or application access records requires exporting AD logs to a centralized security information and event management (SIEM) platform—a process that many organizations never fully implement or maintain.
Signal versus noise: The incident response crisis
The real cost of noisy AD auditing becomes painfully clear during security incidents, when time matters most and clarity is essential.
The three-hour privilege escalation you missed
Consider a scenario that plays out regularly in enterprise environments, usually discovered weeks or months after the fact.
A contractor joins your organization for a three-month project. Standard onboarding creates their user account, assigns basic group memberships, and grants access to project-specific resources. Everything appears routine in the AD logs—account creation, group memberships assigned, authentication events generated.
Two weeks later, a help desk technician modifies the contractor's group memberships to resolve an access issue. The technician adds the contractor to a group that seems appropriate based on its name: "Engineering Resources Access." What neither the technician nor the contractor initially realizes is that this group is nested within another group called "Infrastructure Management," which is itself nested within a group that has administrative rights over production servers.
Through this chain of nested groups, the contractor now possesses production server administrative access. Native AD logs recorded each event: the initial group membership change, the nested group relationships, the resulting permissions. But none of those events triggered alerts because they individually appeared routine.
The contractor eventually discovers their elevated access (accidentally or deliberately) and begins accessing systems far beyond their project scope. Maybe they're curious. Maybe they're gathering information for a competitor. Maybe they're preparing for ransomware deployment. The motivation varies, but the outcome is consistent: unauthorized privileged access continues undetected because your audit data contained the evidence but lacked the intelligence to surface the threat.
This isn't a hypothetical scenario. It's a pattern that security teams recognize from post-incident investigations, where reconstruction reveals that every critical step was logged but no alarm was raised because the signal was invisible beneath the noise.
When seconds count and you're searching for needles
Security incidents compress time brutally. An alert fires to indicate potential privilege abuse. Your security operations team has minutes, not hours, to determine if this represents a real threat requiring immediate response or if it is a false positive that can be deprioritized.
With clean, actionable AD auditing, this investigation follows a clear path: Who accessed or owns this account? What changes occurred to their permissions recently? What is their normal access pattern compared to current activity? What resources have they accessed in the past hour?
With native logs alone, the investigation becomes an expedition. Query event logs for specific event IDs. Export results. Parse XML data. Cross-reference user SIDs with account names. Check group memberships across nested groups. Query GPO settings to understand what policies should be enforcing controls. Correlate timestamps across multiple log sources. Reconstruct effective permissions from scattered data points.
Fifteen minutes into this investigation, your team still hasn't definitively answered whether the alert represents a genuine threat. Meanwhile, if the alert is real, the attacker has had a quarter-hour to exploit their access, exfiltrate data, or establish persistence mechanisms.
This investigation time differential isn't minor. It's the difference between containing a breach at initial compromise versus discovering a security incident days after significant damage has occurred.
The compliance investigation that exposed operational reality
Audit season arrives and your compliance team receives the standard request: demonstrate that administrative access is properly controlled, that segregation of duties is enforced, and that privileged account activity is monitored and reviewed.
In theory, your policies document exactly how administrative access works. Domain Admin membership is tightly controlled. Privileged access is granted temporarily through a formal request process. Changes to critical security groups are approved by security leadership.
In practice? The compliance investigation reveals an uncomfortable truth.
Your AD might contain 47 accounts with Domain Admin privileges. Policy says there should be 12. Investigation reveals that some of these accounts belong to former employees whose accounts were disabled but never removed from privileged groups. Others represent "temporary" access grants from three years ago that nobody remembered to revoke. Several are service accounts that someone added to Domain Admins as a troubleshooting shortcut that became permanent.
Let's say that the security group called "Backup Operators" has 89 members. Policy specifies that this group should contain only designated backup administrators, i.e. approximately six people. Investigation shows that membership grew organically over years as various teams requested access for legitimate business needs, but nobody ever removed members when those needs expired.
None of this would have been discovered without the compliance pressure forcing a deep investigation. Native AD logs documented every addition to privileged groups, but nobody was monitoring those additions in aggregate to detect the drift between policy and practice. The audit data existed. The intelligence to transform that data into actionable insights did not.
Specialized AD audit tools versus sprawling security platforms
When organizations recognize that native AD logging falls short, they face a decision: invest in a specialized Active Directory audit solution or absorb AD monitoring into their broader security information and event management platform.
This decision carries implications for visibility quality, operational efficiency, and actual security outcomes.
The SIEM promise and the integration reality
Modern SIEM platforms promise unified visibility across your entire security infrastructure. Firewall logs, endpoint detection telemetry, application security events, cloud service audit trails, and Active Directory events, all flowing into a centralized analytics platform that correlates across data sources to detect threats.
It's a compelling vision. In practice, most organizations discover that getting rich AD intelligence into their SIEM requires significant integration effort, ongoing maintenance, and often still delivers lower-quality AD visibility than specialized tools provide.
The challenge starts with data ingestion. Native AD logs need to be exported from domain controllers, parsed from Windows Event Log format, normalized for SIEM consumption, and correlated with directory data to provide meaningful context. That's not a one-time configuration—it's an ongoing operational requirement as your AD structure evolves, new domain controllers are added, and audit policy changes.
Even when ingestion works flawlessly, you're still feeding the SIEM with the same noisy native logs that lack critical context. The SIEM becomes better at storing and searching this data, but it doesn't inherently solve the signal-to-noise problem or the missing context gaps.
Specialized AD audit solutions approach the problem differently. Instead of treating AD as just another log source to ingest, they understand the directory structure deeply. They track nested group relationships. They calculate effective permissions across inheritance chains. They maintain historical baseline data that enables meaningful anomaly detection.
When a group membership changes, a specialized tool knows what access that modification actually grants, whether it represents a privilege escalation, and how it deviates from normal patterns for that account. A SIEM sees an event and correlates it with other events, but lacks the AD-specific intelligence to assess what the event means in directory context.
When specialization outperforms integration
There's a legitimate place for comprehensive SIEM platforms in enterprise security architectures. But there are specific scenarios where specialized AD audit tools deliver superior outcomes.
AD-specific threat patterns require directory-aware detection logic. Identifying Kerberoasting attacks, Golden Ticket usage, DCSync attempts, or AdminSDHolder manipulation demands understanding how these techniques exploit specific AD mechanisms. Specialized tools encode this knowledge into detection rules that would require extensive custom configuration in a general-purpose SIEM.
Compliance reporting for AD-specific requirements benefits from tools designed around those requirements. When auditors request evidence of privileged access controls, GPO security settings across the environment, or delegated administration patterns, specialized tools generate those reports natively. Building equivalent reporting in a SIEM requires custom queries, scheduled reports, and ongoing maintenance as reporting requirements evolve.
Operational AD management involves tasks that security teams shouldn't own but still require audit visibility. When help desk staff reset passwords, when department managers approve access requests, or when IT administrators modify GPO settings, these activities need monitoring even though they're not primarily security functions. Specialized tools provide this operational visibility without forcing IT operations through security team workflows.
Performance and storage efficiency matter at scale. A large enterprise might generate millions of AD events daily. Storing every single event in a SIEM for long-term retention becomes expensive quickly. Specialized tools can apply intelligent filtering and aggregation at collection time, preserving high-fidelity data for security-critical events while summarizing routine operations—reducing storage costs without sacrificing visibility where it matters.
The hybrid approach that actually works
The most effective enterprise architectures don't force a choice between specialized AD tools and comprehensive SIEMs. They recognize that both serve distinct purposes and integrate them intelligently.
Specialized AD audit tools handle the depth: granular change tracking, comprehensive GPO visibility, permission analysis, and AD-specific threat detection. They provide the clean, contextualized intelligence that IT administrators, security analysts, and compliance officers need for day-to-day operations.
SIEM platforms handle the breadth: correlating AD events with other security telemetry to detect multi-stage attacks, maintaining unified security event search capabilities, and serving as the system of record for compliance evidence across all security controls.
Integration between these systems is selective rather than comprehensive. High-confidence AD security alerts flow from the specialized tool into the SIEM for correlation and incident workflow. Critical AD changes like Domain Admin group modifications, security policy updates, privileged account activity, are forwarded as enriched, contextualized events rather than raw logs.
This approach delivers the best of both worlds: AD-specific intelligence where it's needed, cross-domain correlation where it matters, without the integration complexity or cost of forcing all AD auditing through the SIEM.
The real cost of invisible threats
Abstract discussions of audit data quality become concrete when you examine the security incidents that clean AD auditing would have prevented.
The departing administrator who kept the keys
An IT administrator gives two weeks' notice. Standard offboarding processes kick in: return company equipment, disable network access, remove system accounts. HR signs off. IT marks the exit checklist complete.
What nobody notices: four days before the termination date, this administrator created a new domain user account with an innocuous name that blends into your directory. They added this account to the Domain Admins group. They documented the credentials securely in their personal notes.
Native AD logs captured both actions: account creation and group membership assignment. Both appeared as routine events among thousands of other changes happening that week—new contractor accounts, project team reorganizations, standard access provisioning.
Six months later, your security team detects unusual activity: weekend authentication from an unknown account, suspicious PowerShell execution on domain controllers, evidence of credential dumping. Investigation reveals the sleeper account and traces it back to the departed administrator.
The breach window was six months. The evidence existed from day one. What was missing? Audit intelligence that could have flagged the combination of new account creation and immediate privileged group assignment by an administrator about to leave the company.
Clean AD auditing would have surfaced this pattern immediately. User behavior analytics would have noted the deviation from normal patterns. Automated alerting would have escalated for security review. The threat would have been neutralized before the administrator's last day, not discovered half a year later after months of unauthorized access.
The service account that became an attack vector
Application teams create service accounts constantly. Database services need domain authentication. Monitoring tools require access to query system health. Backup solutions need read access across file shares.
One particular service account was created for a legitimate business need: an inventory management application required access to query AD for asset tracking purposes. The account was granted the minimum permissions necessary, or so everyone believed.
Three months into production, the application started failing with permission errors. Under deadline pressure, the application team contacted a senior administrator who quickly resolved the issue: added the service account to a high-privilege group that definitely had the necessary permissions. Application worked. Ticket closed. Everyone moved on.
What nobody realized is that the high-privilege group included administrative rights far exceeding what the application needed. What was intended as a targeted permission grant became a standing credential with administrative access to significant portions of the infrastructure.
This elevated service account ran for two years before an external penetration test discovered it. The testers compromised a low-privilege system, found the service account credentials stored in a configuration file (a separate security failure), and used those credentials to gain administrative access to production environments.
Native AD logs showed the service account's privileged group membership. They documented every authentication event using those credentials. But amid millions of service account authentication events across the enterprise, there was no way to identify that this particular account had more access than it should.
Specialized AD auditing could have detected this privilege creep immediately. Anomaly detection would have flagged that a service account, which typically authenticates from a handful of systems, was being granted permissions normally associated with administrator accounts. Automated permission analysis would have highlighted the excessive access. The vulnerability would have been identified and corrected long before it became an attack vector.
What clean AD auditing actually delivers
The gap between noisy native logs and clean, actionable AD auditing isn't just about having better dashboards or prettier reports. It's about fundamentally different capabilities that transform how organizations understand and secure their identity infrastructure.
Enriched context that tells the complete story
Clean AD auditing enriches every event with the context needed to understand what actually happened and why it matters.
When a user is added to a security group, enriched auditing captures not just the event itself but the complete membership context: what groups did this user already belong to, what new access does this grant them, how does this compare to similar users in their department, and what is the total privilege level this user now possesses?
When a GPO changes, enriched auditing preserves the complete before-and-after comparison: which specific settings were modified, what the previous values were, what security implications the changes create, and which users or computers are affected by the updated policy.
When permissions are modified on an AD object, enriched auditing resolves the complete permission chain: inherited permissions from parent objects, explicit permission assignments, effective permissions after resolving group memberships, and comparative analysis showing whether this change increases or decreases access.
This enrichment happens at collection time, not as an afterthought during investigation. The moment an event occurs, the context is captured and stored alongside it, ready for instant analysis when needed.
Consolidated visibility across distributed teams
AD auditing shouldn't be exclusively a security team responsibility, yet most organizations struggle to provide appropriate visibility to different stakeholders without exposing sensitive data or overwhelming non-technical users.
IT operations teams need visibility into administrative actions, configuration changes, and operational issues without necessarily seeing every security-sensitive event or having access to raw security logs. Clean auditing provides scoped access that shows what's relevant for operations: GPO deployment status, delegation changes, OU structure modifications, and troubleshooting data.
Security teams require deep visibility into privilege modifications, authentication patterns, suspicious activities, and potential policy violations. They need access to raw event data when investigating incidents, but benefit from intelligent filtering and prioritization that surfaces high-confidence threats rather than forcing manual triage of thousands of events.
Compliance teams need evidence of control effectiveness, attestation of privileged access management, and documentation of separation of duties enforcement. They don't need real-time alerting or deep technical details. They need clean, auditable reports that demonstrate compliance with specific frameworks.
Consolidated auditing serves all these needs through a single data collection and enrichment layer, with appropriate views and access controls that deliver relevant intelligence to each stakeholder without data duplication or access complexity.
Searchable intelligence when it matters most
The true test of audit data quality arrives during investigations, when security teams need specific answers to urgent questions and every minute counts.
Clean AD auditing delivers search capabilities that match how security teams actually think during investigations: "Show me everyone who was granted Domain Admin access in the past 90 days." "Which GPO settings changed last week?" "What are the complete permission modifications for this user account over the past month?" "Who has administrative access to this specific OU?"
These aren't simple log queries. They are intelligence questions that require understanding the directory structure, permission inheritance, nested group relationships, and historical change patterns. Native logs contain the raw data. Clean auditing provides the intelligence layer that makes that data searchable in meaningful ways.
Search performance matters as much as search capability. When investigating a potential security incident, waiting several minutes for search results isn't just frustrating, it extends the window during which an attacker can operate undetected. Sub-second search response times across months or years of audit data enable iterative investigation patterns where security teams can follow leads quickly, test hypotheses, and reach conclusions before threats escalate.
Automated alerting that respects your time
Alert fatigue isn't just an annoyance, it's a security vulnerability. When every AD event triggers notifications, security teams learn to ignore alerts entirely, missing the genuine threats buried among false positives.
Clean AD auditing enables intelligent alerting that reduces noise while increasing threat detection accuracy. Alerts fire based on actual security implications, not just event occurrence. A group membership change to a low-privilege departmental group doesn't generate an alert. The same change to Domain Admins triggers immediate notification. A GPO modification that strengthens security controls might log the event without alerting. A modification that weakens password requirements demands immediate investigation.
Behavioral baselines enable anomaly detection that catches threats even when individual events appear legitimate. A user account that typically authenticates Monday through Friday 9am-5pm suddenly shows weekend access at 3am. That deviation triggers investigation even though the authentication itself wasn't technically unauthorized.
Alert context matters as much as alert generation. When an alert fires, security teams need to understand not just what happened, but why it matters and what to do next. Clean auditing delivers alerts that include the enriched context, risk assessment, affected resources, and recommended investigation steps, transforming alerts from "something happened" notifications into actionable intelligence.
The bottom line
Enterprise IT teams aren't demanding clean AD auditing because they want prettier dashboards or because compliance requires it (though those are excellent benefits). They're demanding it because the current state of AD visibility is fundamentally broken in ways that create real security risks, operational inefficiencies, and compliance gaps.
Native AD logs generate vast quantities of data without delivering proportional insight. Security teams spend hours investigating events that turn out to be routine operations while genuine threats remain invisible in the noise. Compliance teams manually reconstruct evidence from scattered log fragments because coherent audit trails don't exist. IT operations teams react to problems after they occur because they lack the visibility to identify risks before they materialize.
The technology to fix this exists. It's not theoretical or cutting-edge. Specialized AD audit solutions that provide clean, enriched, contextual intelligence are deployed across thousands of enterprises. They're capturing old and new values for every change, resolving nested group permissions, tracking GPO modifications at granular levels, and delivering searchable audit data that serves multiple teams from a single collection layer.
What's missing isn't technical capability, it is organizational recognition that AD auditing deserves more than the bare minimum of native logging. Your identity infrastructure is the authentication foundation for your entire enterprise. The visibility into that infrastructure should match its importance.
The question facing enterprise IT leadership isn't whether clean AD auditing delivers value—the ROI is clear in reduced investigation time, faster incident response, improved compliance posture, and prevented security breaches. The question is: how much longer will you accept the gap between the AD visibility you have and the AD intelligence you need?
Your next security incident won't wait for you to implement better auditing. The compliance audit won't postpone itself while you build reporting capabilities. The insider threat isn't pausing until you can detect privilege escalation patterns.
The time to demand clean, actionable AD auditing isn't after the next breach. It's now.
Related solutions
ManageEngine AD360 provides unified Active Directory, Azure AD, and Exchange management with advanced audit capabilities that track granular permission changes, GPO modifications, and privileged account activity. Combine operational AD management with security-grade audit intelligence in a single integrated platform designed for enterprise scale.
Schedule a personalized demoManageEngine Log360 delivers enterprise-grade Active Directory auditing with enriched event capture, complete before-and-after change tracking, and intelligent alerting that cuts through the noise. Transform overwhelming AD event volumes into clean, searchable intelligence with automated threat detection, comprehensive compliance reporting, and consolidated visibility that serves IT, security, and compliance teams from a single platform.
Request a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
