Genomics is the branch of molecular biology that focuses on the structure, function, evolution, and mapping of genomes, which are the complete sets of DNA within an organism, including all of its genes. Unlike genetics, which typically studies individual genes and their roles in inheritance, genomics examines all genes and their interrelationships to understand their combined influence on the organism’s biology, development, and health. It uses advanced tools like DNA sequencing, computational analysis, and systems biology to decode and interpret complex biological data.
On this page
Genomics and personalized medicine platforms are at the cutting edge of healthcare innovation. By analyzing a patient’s DNA and other biological data, these platforms enable precise, tailored treatments for conditions ranging from cancer to rare genetic disorders. Genomic data is complex and voluminous. So, researchers turned to cloud services, databases, and bioinformatics software applications to develop drugs and sequence, decode, and share the analyzed data.
Meanwhile, individuals are leveraging direct-to-consumer genetic testing services like 23andMe and Mapmygenome to explore their ancestry and genetic predispositions. This introduces cybersecurity risks, particularly around genomic data confidentiality and integrity. A prime example of this is the 23andMe data breach that occurred in July 2023, which resulted in the company being fined £2.31 million in June 2025. Genomic data security has become a critical priority for healthcare providers, researchers, and related industries.
Genomics and personalized medicine: An overview
Genomics is the study of an individual’s entire DNA sequence, including all of their genes, and how these genes interact with one another and with the environment. Advances in genomics have enabled researchers and healthcare providers to analyze genetic information and pave the way for personalized healthcare.
Genomics and personalized medicine are closely interlinked in the following ways:
- Genomics enables precision medicine: Personalized medicine, also known as precision medicine, relies on genomic data to tailor medical treatments to individual patients based on their genetic profiles, lifestyle, and environmental factors. Healthcare providers can predict disease risks, optimize drug therapies, develop targeted interventions, and improve patient outcomes by analyzing a person’s genetic makeup.
- Disease prediction and prevention: Genomic studies help identify genetic predispositions to diseases such as cancer, cardiovascular disorders, and neurological conditions. It also helps discover biomarkers that indicate disease progression or treatment response. This allows for early intervention and preventive strategies. For example, in cancer care, genomic profiling of tumors enables oncologists to identify driver mutations and choose targeted therapies, such as the HER2-targeted treatment in breast cancer.
- Pharmacogenomics and drug response: Genomics plays a crucial role in pharmacogenomics, which studies how genetic variations affect an individual's response to drugs. For instance, genomic insights can reveal how a patient’s body might metabolize specific drugs such as Warfarin (an anticoagulant), if they have variations in the CYP2C9 gene. This can help clinicians personalize the dosage to reduce the risk of bleeding and improve treatment efficacy.
Personalized medicine platforms integrate bioinformatics tools, ML algorithms, and cloud infrastructure to analyze massive genomic datasets, including whole-genome sequencing, RNA sequencing, and genotyping arrays efficiently. However, this expands the attack surface and presents complex challenges that demand a strategic, risk-based security approach.
Security challenges in genomics and personalized medicine platforms
The digital infrastructure supporting genomics and personalized medicine presents critical cybersecurity concerns, as mentioned below:
- Data privacy: Genomic data is immutable, personally identifiable, and unlike a stolen password or credit card, it can never be reset or changed once exposed. A breach doesn’t just compromise patient privacy; it can expose hereditary information that affects entire families. It also increases the risk of identity theft and genetic discrimination.
- Data integrity: Research organizations and testing companies often store terabytes of raw and processed genetic data on cloud services or third-party bioinformatics platforms. Cyberattacks targeting genomic databases can manipulate genetic information, leading to incorrect diagnoses or treatment recommendations. Moreover, misconfigured cloud environments, lack of encryption, and insecure APIs can result in unauthorized access, data leakage, and cloud supply chain risks.
- Lack of standardized security measures: The rapid growth of genomic research has outpaced the development of standardized cybersecurity protocols, leaving gaps in data protection. According to a 2023 NIST report, the gaps identified by stakeholders include:
- Practices across the life cycle concerning genomic data generation
- Safe and responsible sharing of genomic data
- Monitoring the systems processing genomic data
- Lack of clear guidelines addressing specific needs of genomic data processors
- Regulatory/policy gaps with respect to national security and privacy threats in the collection, storage, sharing, and aggregation of human genomic data.
- Third-party and research collaboration risks: Genomic research often involves data sharing with external collaborators, such as academic institutions and biotech companies. From bioinformatics partners to cloud storage providers, every third-party integration increases potential entry points. Insider threats and insecure research collaborations further complicate governance. Figure 1 shows the genomic data sequencing workflow as documented in NIST's Cybersecurity and Privacy of Genomic Data Fact Sheet. As depicted in Figure 1, the researcher submits a DNA sample to the genome sequencer, which generates digital sequencing results for further analysis. However, the use of untrusted open-source software in this process expands the potential attack surface.
- Regulatory complexity: The use of genomic data is governed by strict compliance requirements such as HIPAA, GDPR, and the Genetic Information Nondiscrimination Act (GINA). These compliances are difficult to adhere to, and a breach can lead to significant fines and legal consequences for the organizations handling genomic data.
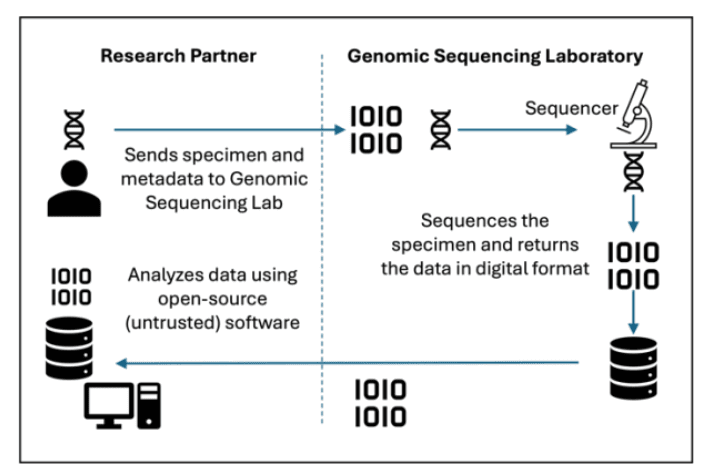
Image source: NIST Data Fact Sheet
Figure 1: Genomic data sequencing workflow
Common vulnerabilities and possible attacks on bioinformatics tools
According to the Journal of Biomedical Informatics, the common vulnerabilities in bioinformatic tools are as follows:
- Poor code sanitization and insufficient input validation: Many bioinformatics applications lack robust mechanisms to validate and sanitize user inputs, making them susceptible to injection attacks and data corruption.
- Use of deprecated or unsafe functions: Reliance on outdated or insecure programming functions—such as gets(), scanf(), strlen(), and strcpy()—can lead to vulnerabilities like buffer overflows, which can be exploited by attackers to execute arbitrary code.
- Weak authentication and access controls: Some genomic databases implement minimal authentication protocols and inadequate access controls, especially while downloading genomic data. Such databases often lack MFA or secure password policies, increasing the risk of unauthorized data access.
- Transmission over insecure channels: Transmitting sensitive genomic data over insecure protocols like HTTP instead of HTTPS makes it vulnerable to manipulator-in-the-middle attacks.
- Public availability of sensitive data: The open sharing of genomic datasets, while beneficial for research, can inadvertently expose PII and impact the privacy and integrity of genomic data.
The same article lists the possible cyberattacks on bioinformatic tools processing genomic data as shown in Figure 2.
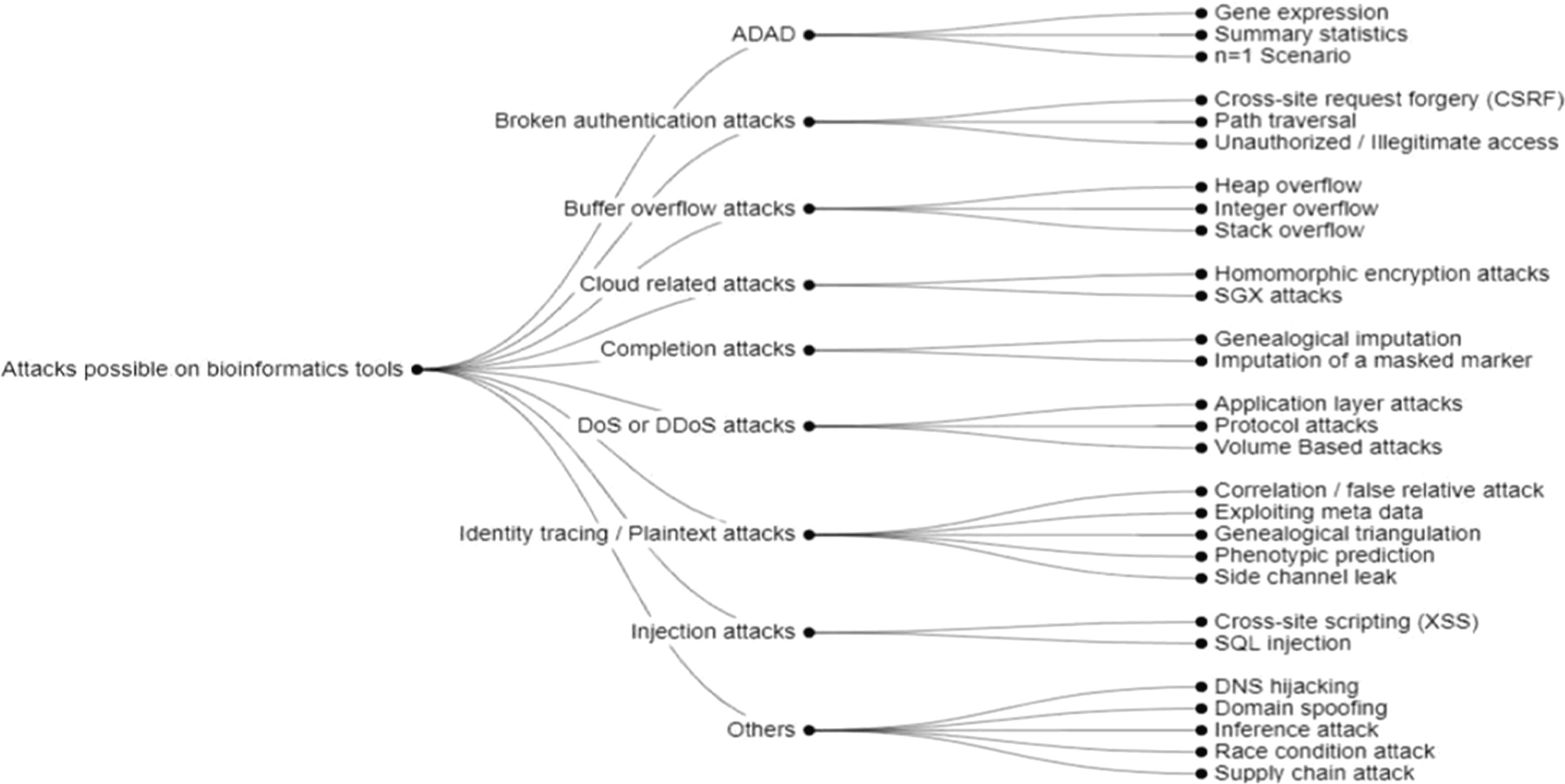
Image source: Journal of Biomedical Informatics
Figure 2: Possible attacks on bioinformatic tools
Some of these attacks are:
- Attribute disclosure attacks using DNA (ADAD): ADAD attacks use techniques like analyzing gene expression profiles or summary statistics to identify individuals from anonymized datasets, compromising privacy.
- Authentication bypass attacks: Common web-based authentication attacks on bioinformatics software are as follows:
- Cross-site request forgery: Tricks authenticated users into executing unwanted actions.
- Path traversal: Allows unauthorized access to files outside the intended directories and is carried out by leveraging URLs, system calls, or shell commands.
- Credential theft: Exploiting weak authentication to compromise user credentials (e.g. keys, passwords, and tokens) and impersonate legitimate users.
- Buffer overflow attacks: Threat actors exploit software vulnerabilities to overwrite memory and execute malicious code.
- Cloud-related attacks: Attackers often target misconfigured storage buckets, weak API security, and inadequate access controls, leading to unauthorized access of sensitive genetic information. Also, they may exploit vulnerabilities in cloud-based bioinformatics pipelines or leverage insecure third-party integrations to execute data exfiltration.
- Data completion attacks: To reconstruct complete genetic profiles from partial data, attackers may leverage linkage disequilibrium between genetic markers and reference panels containing comprehensive genetic information.
- Denial-of-service attacks: Threat actors can overwhelm bioinformatics servers with excessive requests, rendering services unavailable to legitimate users.
- Identity tracing attacks: Cyberattackers pinpoint the identity of an anonymous DNA sample by leveraging quasi-identifiers within the dataset to establish a unique match. These attacks can be carried out by correlating with public databases, genetic triangulation, exploiting metadata, phenotype prediction, or side channel leaks.
- Injection attacks: Attackers may execute SQL injection or cross-site scripting attacks on bioinformatic web applications.
- Software supply chain attacks: Attackers may insert malicious code into third-party software components used in bioinformatics pipelines, leading to widespread vulnerabilities.
- DNS hijacking: Attackers redirect traffic from legitimate genomic databases to malicious sites.
- Race condition attacks: Threat actors may take advantage of timing issues in software processes to execute unauthorized actions.
How to prevent genomic data breaches
Preventing genomic data breaches requires a multi-layered approach that combines cybersecurity best practices, regulatory compliance, and advanced technologies.
1. Use robust encryption techniques
- Encrypt genomic data both at rest and in transit to prevent unauthorized access.
- Implement quantum-resistant encryption to safeguard against future threats.
2. Enforce strict access controls
- Use MFA to ensure only authorized personnel can access genomic databases.
- Implement role-based access control to limit data exposure.
3. Leverage AI-driven threat detection
- Deploy AI-powered security systems to identify anomalies and potential breaches in real time.
- Use ML models to detect unusual access patterns.
4. Use blockchain for data integrity
- Utilize blockchain technology to create immutable records of genomic data transactions.
- Ensure transparency and security in data sharing while preventing unauthorized modifications.
5. Ensure regulatory compliance and ethical standards
- Implement controls to adhere to data protection laws such as GDPR, HIPAA, GINA, and NIST CSF.
- Establish clear consent policies for individuals sharing their genetic information.
6. Ensure continuous monitoring and automated incident response
- Implement SIEM solutions for real-time monitoring.
- Develop a rapid incident response plan to mitigate breaches effectively.
7. Leverage privacy-preserving technologies
- Use federated learning to analyze genomic data without exposing raw genetic information.
- Employ strong homomorphic encryption to allow computations on encrypted data without decryption.
How can SIEM solutions ensure cybersecurity in genomics?
SIEM solutions can improve cybersecurity in genomics and personalized medicine platforms by providing:
- Centralized visibility and real-time security monitoring: SIEM solutions consolidate logs and telemetry from cloud providers, bioinformatics tools, endpoints, and user sessions. This allows security teams to detect anomalous behavior, such as large downloads of DNA sequences or API misuse; correlate threats across environments; and automate alerts and orchestrate incident response. SIEM solutions also integrate with DLP and CASB tools to monitor data flows and block unauthorized transfers or uploads of genomic data.
- Insider threat detection: SIEM solutions come with user and entity behavior analytics capabilities which leverages ML algorithms to learn normal user behavior and identify anomalies, such as researchers accessing out-of-scope datasets, sudden spikes in data exfiltration activity, or misuse of privileged access. This is critical in research settings where employee roles and data access needs are highly dynamic.
- Regulatory compliance support: With prebuilt compliance dashboards for HIPAA, GDPR, and NIST CSF, SIEM solutions can generate audit-ready reports, provide immutable logs for forensic investigations, and demonstrate security controls during regulatory inspections.
- Dark web monitoring and threat intelligence: SIEM solutions can integrate with dark web monitoring tools and threat intel feeds to detect leaked genome datasets, credential theft of researchers or admins, and IoCs from known advanced persistent threats targeting biotech and healthcare.
- Automated response and playbooks: Security orchestration, automation, and response is a core feature of modern SIEM solutions that can help security teams automate blocking of malicious IPs or users, and execute workflow actions for containing threats like ransomware, data exfiltration, and account compromise.
As genomic sequencing and personalized medicine continue to evolve, safeguarding these platforms from cyberattacks is critical. By implementing SIEM, AI-driven monitoring, and encryption, healthcare CISOs can secure genetic databases, ensure regulatory compliance, and build trust in data-driven healthcare systems.
Frequently asked questions
Genomics data is highly sensitive, uniquely identifiable, and immutable—it cannot be changed like a password. It contains information not just about an individual, but also about their relatives and hereditary traits. This makes it extremely valuable for black-market trade, identity theft, insurance fraud, and even bioweapon research. Attackers may also target genetic testing companies and research institutions for intellectual property theft, such as proprietary sequencing algorithms or therapeutic models.
Genomics is foundational to personalized medicine because it enables tailored healthcare based on an individual’s genetic profile. By analyzing a patient’s genome, clinicians can:
- Predict susceptibility to certain diseases (e.g., cancer, diabetes, rare genetic disorders).
- Determine how a person might respond to specific medications (pharmacogenomics).
- Customize prevention, diagnosis, and treatment strategies based on their genetic profile.
Genomic insights make it possible to move from a one-size-fits-all model to a precision-based approach that improves outcomes and minimizes side effects.
Bioinformatics is essential in personalized medicine as it helps process, analyze, and interpret vast amounts of biological and genomic data. Key roles include:
- Aligning and annotating DNA or RNA sequences from patients.
- Identifying genetic variants linked to disease or drug response.
- Integrating data from genomics, proteomics, and clinical records.
- Enabling the development of predictive models for diagnostics and treatment decisions.
Bioinformatics software and applications enable researchers and clinicians to translate raw genetic data into actionable insights, such as pinpointing mutations that influence therapy selection for cancer or rare disease management.
Genomics has several applications in medicine, including predicting disease risk, guiding cancer treatment through tumor profiling, and tailoring drug therapies based on genetic makeup. It also supports early diagnosis of rare genetic disorders, prenatal screening, and tracking infectious diseases by analyzing pathogen genomes.
Personalized medicine involves integrating genomic, behavioral, and clinical data, often across multiple jurisdictions. This creates difficulties in:
- Ensuring informed consent for each use case
- Maintaining data minimization and purpose limitation
- Managing cross-border data transfers
- Handling genetic information as personally identifiable data under evolving laws like GINA and the GDPR
Ensuring ongoing compliance requires dynamic data governance and audit-ready traceability.
Related solutions
ManageEngine AD360 is a unified IAM solution that provides SSO, adaptive MFA, UBA-driven analytics, and RBAC. Manage employees' digital identities and implement Zero Trust and the principles of least privilege with AD360.
To learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM solution with UEBA, DLP, CASB, and dark web monitoring capabilities. Secure multi-cloud infrastructure and get audit-ready reports for HIPAA, GDPR, and NIST CSF with Log360.
To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
