Network traffic (or data traffic) refers to the flow of data packets across a digital network as devices communicate with each other. This includes web requests, file transfers, email exchanges, and application communications.
On this page
Advanced persistent threats (APTs) pose a serious risk to enterprises, leveraging stealth, persistence, and multi-stage attack chains to exfiltrate data or maintain long-term access and often remaining undetected for months. Traditional defenses often fall short against such threats. To counter this, enterprises require real-time visibility into network activity. Network traffic analysis (NTA) provides that visibility by monitoring and analyzing internal and external traffic patterns to detect suspicious behavior, command and control (C2) communications, and lateral movement. For CISOs and security leaders, NTA is a critical layer of defense, enabling early detection of APTs and reducing dwell time.
An overview of APT and NTA
APTs are stealthy and prolonged cyberattacks, typically orchestrated by well-funded threat actors or nation states, often targeting sensitive data or critical infrastructure. Unlike opportunistic attacks, APTs infiltrate a network silently, maintain long-term access, and move laterally to expand control, all the while avoiding detection. The objectives of APT actors usually include espionage, intellectual property theft, or sabotage.
NTA is a security monitoring technique that involves monitoring and analyzing the flow of data across the network to detect and prevent APTs. NTA solutions use various techniques, including packet capture, flow analysis, and machine learning, in real time to identify anomalies, suspicious patterns, and indicators of compromise (IoCs) that traditional perimeter defenses might miss.
By monitoring both north-south traffic (data moving between internal systems and external networks) and east-west traffic (lateral movement within the network), NTA helps detect key APT tactics like data exfiltration, C2 communication, or unauthorized access.
How do APTs operate?
1. Reconnaissance: APTs begin with extensive open-source intelligence gathering. Threat actors collect information about the target’s network, employees, suppliers, and systems to identify vulnerabilities and entry points.
2. Initial compromise: Attackers often use spear phishing, watering hole attacks, or zero-day exploits to gain initial access. The payload is typically a remote access Trojan or malware customized to evade detection.
3. Establishing foothold: Once inside the network, APTs establish persistence using backdoors, scheduled tasks, or registry changes. They often use legitimate credentials or abuse trusted tools and services to evade detection.
4. Lateral movement: Threat actors move through the network, escalating privileges and accessing sensitive systems and data, using tools like Mimikatz, PsExec, or WMI to traverse the network while masking their activities.
5. Data collection and exfiltration: After identifying the object of their desire, usually PII or business-critical data, attackers may compress it, often encrypting the files before exfiltrating them to external servers, sometimes using common protocols like HTTPS or DNS.
6. Maintaining access and covering their tracks: APTs usually accomplish this during the third stage of their modus operandi (MO), where they install multiple backdoors to establish foothold. Additionally, they may clear event logs to evade detection and maintain long-term access. Some APTs return months later using dormant credentials or malware.
For CISOs, understanding the MO of APTs is essential to develop threat hunting programs, incident response playbooks, and implement technologies like NTA, SIEM, and EDR.
How does NTA work?
Here's how NTA works to protect enterprises against APTs:
- Data collection: NTA tools gather traffic metadata and, in some cases, full packet data from across the enterprise network. Key data sources include:
- NetFlow, IPFIX, and sFlow: Provide flow-level metadata such as source and destination IPs, ports, protocols, byte and packet counts, and session duration.
- Full packet capture: Offers granular insights into traffic content, which is especially useful for forensic analysis.
- Switched port analyzer (port mirroring) and test access points: Allow NTA solutions to passively monitor live traffic from switches and routers.
- Encrypted traffic metadata: NTA tools analyze TLS handshake characteristics and certificate data without decrypting payloads.
This step ensures broad visibility across both north-south (external) and east-west (internal) network traffic.
- Data filtering and preprocessing: Once the data is collected, it’s filtered and normalized to reduce noise and focus on the traffic of interest. Key processes include:
- Protocol dissection: Identifies and decodes various network protocols to understand context and payload structure.
- Session reconstruction: Rebuilds sessions or flows to track communication over time.
- Noise reduction: Filters out known benign traffic, such as software updates and scheduled backups, using allowlists or behavioral baselining.
- Threat intelligence enrichment: Tags IPs, domains, or URLs using threat intelligence feeds to flag known IoCs.
This stage ensures the system focuses resources on analyzing high-risk or anomalous activity rather than routine traffic.
- Analysis and threat detection: NTA solutions use behavioral analytics and ML models to analyze the pre-processed data. They look for deviations from established norms and identify threat indicators. Threat analysis involves:
- Statistical anomaly detection: Flags traffic patterns that diverge from historical baselines, for instance, a device suddenly sending large volumes of outbound traffic.
- Behavioral modeling: Learns the typical communication patterns of users and devices to detect lateral movement or privilege escalation.
- Signature-less detection: Detects zero-day threats and previously unseen attack vectors based on traffic behavior rather than predefined rules.
- Correlation with external feeds: Matches activity against threat feeds to identify traffic associated with malicious IPs, domains, or malware families.
- Integration with SIEM, IDS, and IPS solutions: Leverages these integrations to correlate events across platforms, assign risk scores to anomalies—based on severity, impact, and confidence—for threat prioritization, and helps incident response by alerting SOCs with enriched context.
How does NTA help detect APTs?
NTA can detect each stage of the APT's MO; here's how it does that:
| APT stage | How NTA helps | Example |
|---|---|---|
| Reconnaissance | While identifying the initial reconnaissance (executed outside the network) is beyond its scope, once attackers are inside, NTA can flag unusual scanning behavior, such as internal port scans, abnormal DNS queries, or devices probing for exposed services. | Detection of lateral scanning attempts or high volumes of ARP requests from a single host |
| Initial compromise | NTA tools analyze traffic metadata and payload patterns to detect anomalies in communication, such as uncommon ports, sudden beaconing to C2 servers, or traffic to known malicious IPs. | Identification of irregular outbound traffic after a phishing email delivers a payload |
| Establishing foothold | NTA monitors for persistent or scheduled connections to external hosts, unusual authentication behavior, or newly established encrypted tunnels that signal ongoing access. | Detection of repeated outbound traffic to unusual destinations during off-hours |
| Lateral movement | NTA identifies unauthorized or abnormal peer-to-peer traffic, SMB protocol misuse, or remote admin tools being used between endpoints, which indicates attempts to move laterally. | Alerts triggered when a low-privileged user initiates RDP sessions across multiple servers |
| Data collection and exfiltration | NTA detects large, abnormal data transfers, especially to unapproved external domains or over unusual protocols, for example, DNS tunneling or FTP. It can also flag encrypted data exfiltration. | Identification of a large outbound upload to a third-party file sharing service not sanctioned by the enterprise |
| Maintaining access and covering their tracks | NTA detects beaconing patterns and signals to C2 infrastructure or stealthy re-entry attempts. It also identifies unusual VPN connections or usage of anonymizing services like Tor. | Flagging recurring connections to an IP address that rarely appears in the organization’s network history |
Table 1: How NTA helps detect and protect against each stage of the APT life cycle.
NTA best practices for CISOs
Clearly, NTA is essential for enterprise cybersecurity, especially in detecting APTs and protecting sensitive data across cloud and on-premises environments. The following are some best practices that CISOs can adopt to strengthen threat detection and response.
1. Gain complete network visibility
Deploy network sensors at key ingress, egress, and internal network points to monitor east-west and north-south traffic. Ensure visibility across cloud, on-premises, and hybrid infrastructures to detect hidden threats and insider activity.
2. Use encrypted traffic analysis
With network traffic now predominantly encrypted, traditional inspection techniques are insufficient. Adopt NTA tools that can analyze encrypted traffic without decryption. This helps identify malware and C2 communication hiding in TLS/SSL traffic.
3. Establish baselines for normal behavior
Use ML to profile typical user, device, and application traffic patterns. Flag deviations like unusual data transfer volumes, protocol misuse, or off-hours access as potential APT signals.
4. Integrate NTA with SIEM and SOAR
Feed NTA telemetry into your SIEM solution to correlate alerts with identity, endpoint, and threat intelligence data. Use SOAR playbooks to automate response actions and reduce mean time to detect and respond.
5. Apply threat intelligence to NTA
Combine network behavior data with real-time threat intelligence feeds to uncover known IoCs, suspicious IPs, or malicious domains targeting your industry.
6. Retain logs for historical threat hunting
Store NTA data for extended periods. This helps with compliance and forensic analysis of threats discovered after initial compromise.
7. Segment networks and enforce least privilege
Limit lateral attack paths by applying network segmentation and least-privilege policies. Use NTA alerts to enforce access rules and stop privilege escalation in real time.
How can enterprises benefit from SIEM and NTA integration?
It's crucial for CISOs to integrate SIEM and NTA because these tools are synergistic and can work in tandem to detect and mitigate APTs. While SIEM centralizes and correlates diverse log data, NTA adds behavioral and flow-based detection as shown in Figure 1. This can help enterprises improve the speed and accuracy of threat detection and response significantly.
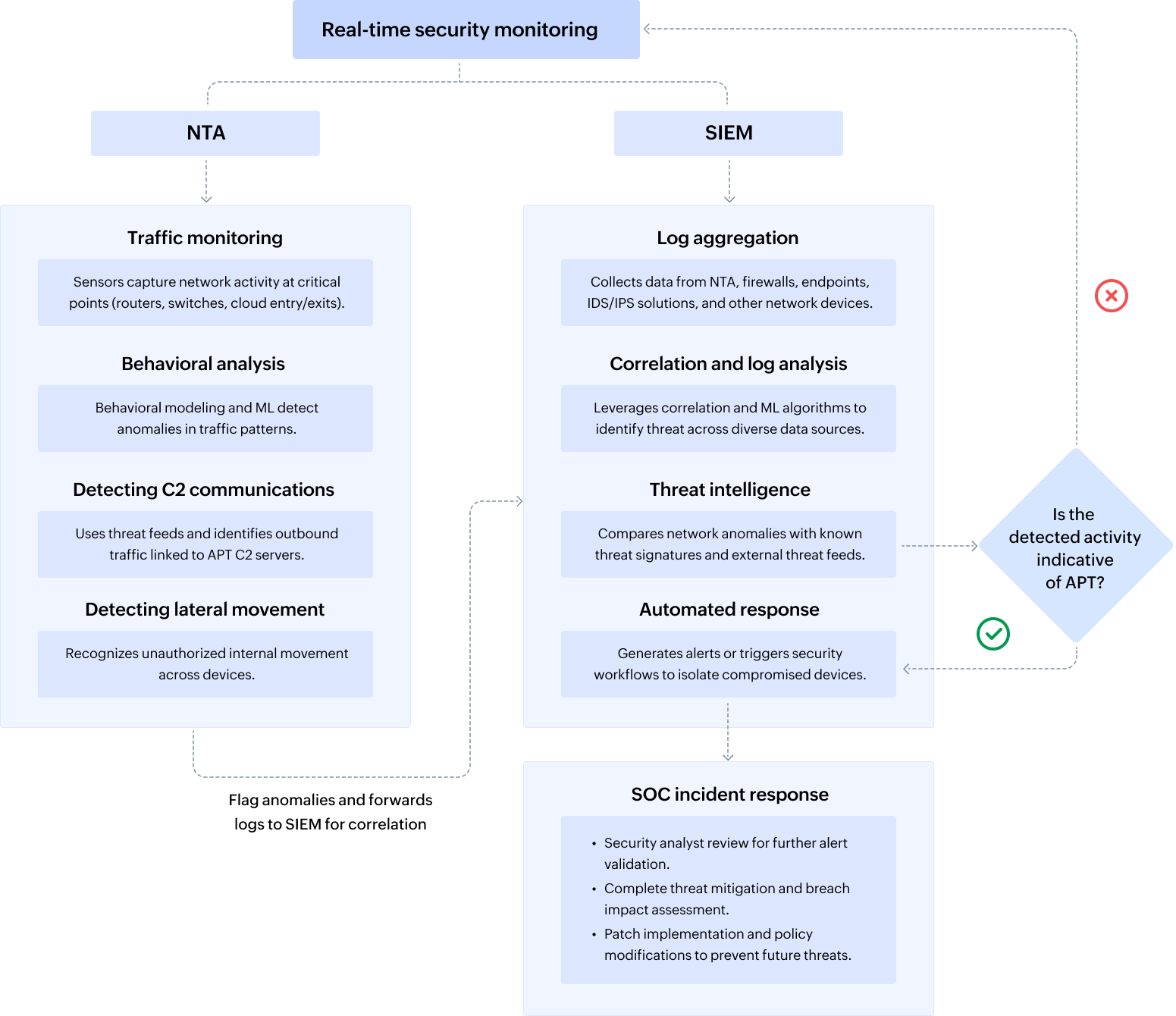
Figure 1: Benefits of integrating SIEM and NTA in APT prevention and detection.
1. Strengthen enterprise-wide visibility across digital assets
By integrating SIEM’s centralized log analysis and ML-driven threat detection with NTA’s packet and flow-level telemetry, CISOs gain comprehensive oversight across endpoints, cloud workloads, and lateral network traffic. This integrated visibility is critical for identifying stealthy APT activities that evade traditional defenses.
2. Correlate threat intelligence across layers for faster detection
SIEM identifying behavioral anomalies and NTA identifying traffic anomalies can together provide high-fidelity alerts on APT behavior such as beaconing or privilege escalation. This reduces detection time and aligns with risk-based prioritization strategies.
3. Detect lateral movement and data exfiltration with greater precision
NTA is particularly effective in detecting unauthorized internal communication paths and data exfiltration attempts, while SIEM provides the contextual identity and access data needed for attribution. The combined approach enables early intervention before data loss or business disruption occurs.
4. Improve incident response time and compliance readiness
SIEM offers log-based forensic evidence and compliance-aligned reporting, while NTA accelerates root cause analysis through traffic-level visibility. SIEM also provides SOAR capabilities, which enables automated incident response. This improves mean time to respond and contain APTs, and audit-ready reports helps ace compliance for frameworks like the NIST's Cybersecurity Framework (CSF), HIPAA, and the GDPR.
5. Cover the entire APT kill chain with layered detection
Advanced threats often unfold over weeks or months. SIEM and NTA together enable detection at each APT stage—from initial compromise to data exfiltration—allowing CISOs to enforce layered, proactive defense strategies.
6. Reduce noise, maximize analyst productivity, and focus on real threats
SIEM and NTA together can help filter out false positives by providing context-rich alerts. This empowers your SOC team to focus on validated threats, streamlining workflows, reducing alert fatigue, and preserving resources in a high-alert environment.
Frequently asked questions
Network traffic analysis is the process of continuously monitoring and analyzing network data flows to detect abnormal behavior, security threats, performance issues, and policy violations.
NTA is crucial for detecting advanced threats like lateral movement, data exfiltration, and C2 communications that often bypass traditional defenses. By continuously analyzing traffic patterns across cloud, hybrid, and on-premises environments, NTA provides deep visibility into malicious behavior, insider threats, and policy violations, thus enabling faster threat detection and response.
An APT is a prolonged and targeted cyberattack where threat actors obtain unauthorized access and manage to stay undetected for weeks or months.
APTs often use phishing or other social engineering attacks, zero-day exploits, and custom malware to infiltrate and maintain persistence in the victim's network.
Common indicators include:
- Repeated failed login attempts or credential misuse
- Communication with known malicious IPs or domains
- Data exfiltration via unusual ports or protocols
- Internal traffic patterns inconsistent with normal operations
APTs typically involve stealthy, long-term intrusions. NTA identifies anomalies like unusual data transfers, beaconing behavior, or C2 traffic, which are indicative of APT activity.
SIEM solutions aggregate and correlate data from various sources, including NTA tools. This integration provides full-context visibility, automates alert triage, and supports rapid response to threats, including APTs.
NTA helps organizations meet compliance requirements such as HIPAA, the GDPR, and the NIST's CSF by providing real-time visibility into network activity, monitoring sensitive data flows, and generating audit trails to maintain data integrity and meet reporting requirements.
Yes. While NTA tools can't always decrypt traffic, they can analyze metadata such as packet size, frequency, destination, and timing patterns to detect anomalies. This helps flag encrypted tunnels or obfuscated C2 channels commonly used in APTs.
Related solutions
ManageEngine AD360 is a unified IAM solution that provides SSO, adaptive MFA, UBA-driven analytics, and RBAC. Manage employees' digital identities and implement Zero Trust and the principles of least privilege with AD360.
To learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM solution with UEBA, DLP, CASB, and dark web monitoring capabilities. Detect abnormal network traffic, compromised credentials, and reduce breach impact with Log360.
To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
