On this page
Did you know that a Mercedes-Benz employee’s authentication token was accidentally exposed in a public GitHub repository for months? The token granted unrestricted access to the company’s internal source code, leaving it vulnerable from September 2023 until it was discovered and revoked in January 2024.
Prioritizing software development security is critical for every organization because even a single oversight in safeguarding source code can expose the business to massive cyber risks.
Why developer workstations are a high-value target
Here are the top-five reasons why developer workstations are high-value targets for attackers:
- Direct access to source code: Developer machines often hold local copies of proprietary code, intellectual property, and internal documentation, making them a goldmine for attackers.
- Privileged credentials and keys: Developers frequently store API tokens, SSH keys, and admin credentials locally for convenience. Compromising one workstation can unlock access to multiple systems and repositories.
- Integration with critical systems: Developer workstations are connected to CI/CD pipelines, internal Git servers, cloud environments, and testing frameworks, giving attackers a pivot point into the broader infrastructure.
- Weaker endpoint security controls: Unlike hardened production servers, developer endpoints may run less restrictive policies, making them more susceptible to phishing, malware, and supply chain attacks.
- Blend of personal and corporate use: Developers often use their workstations for both work and personal tasks, increasing the attack surface through unsafe downloads, browser extensions, or unsecured networks.
What are the common attack vectors targeting developer machines?
Here are the common attack vectors targeting developer machines today:
1. Credential theft and token leakage
- How it works: Attackers steal stored SSH keys, API tokens, or cloud credentials from local files, browsers, or Git configuration.
- Example: Exposed GitHub or AWS tokens in local config files or the commit history.
2. Malicious code injection via dependencies
- How it works: Compromising third-party libraries or open-source packages that developers pull into projects.
- Example: Typosquatting or dependency confusion attacks where malicious packages replace legitimate ones.
3. Phishing and spear phishing
- How it works: Highly targeted emails or messages trick developers into revealing credentials or executing malicious payloads.
- Example: Fake GitHub security alerts or cloud service login requests.
4. Compromised development tools and plugins
- How it works: Attackers inject malicious code into IDE plugins, build tools, or extensions used in daily development.
- Example: Malicious VS Code extensions or poisoned NPM/PIP build scripts.
5. Supply chain and CI/CD pipeline exploitation
- How it works: Gaining access to developer machines to tamper with build processes, commit history, or signing keys.
- Example: Inserting backdoors into software releases through compromised local build scripts.
6. Malware and ransomware on developer endpoints
- How it works: Exploiting weaker endpoint protection to plant keyloggers, steal local repositories, or encrypt files for ransom.
- Example: Remote access Trojans that exfiltrate source code and credentials.
7. Browser-based attacks
- How it works: Exploiting browser vulnerabilities or malicious extensions to intercept credentials and tokens.
- Example: Malicious Chrome extensions that grant access to internal dashboards.
A real-world incident of source code theft
In March 2025, logistics platform Flexport filed a lawsuit against two former employees for allegedly stealing its proprietary source code to develop a competing platform, Freightmate AI. Flexport contends the duo conspired months before leaving, downloading hundreds to thousands of files daily onto USB drives or cloud storage. Despite their admission to taking internal documents, the former employees have refused to allow inspection of Freightmate’s source code. Flexport is seeking recovery of the stolen assets and a legal injunction to prevent Freightmate from using its trade secrets.
Key takeaways
- Insider risk management is critical: Even trusted employees may have access to large volumes of sensitive source code. Monitoring and access governance are essential to detect unusual data activity.
- Data exfiltration can be gradual and large scale: High-frequency file transfers over time may go unnoticed without proper behavioral analytics and DLP controls.
- Equal monitoring for cloud and removable media: Theft can occur via both USB devices and cloud storage. Security policies should address both vectors with logging and real-time alerts.
- Intellectual property protection extends beyond employment: Risk doesn’t end when an employee resigns; post-exit monitoring and contractual safeguards can help protect intellectual property.
- Transparency and legal safeguards matter: Clear policies on code ownership, legal recourse, and partner and vendor NDAs are essential to safeguard competitive advantage in disputes.
What's the business and security impact of source code theft?
Source code theft impacts business and security in ways that are both immediate and far-reaching. These include:
Business impact
- Loss of competitive advantage: Proprietary algorithms, unique features, and custom integrations are often the secret sauce that can be replicated by competitors or malicious actors, eroding market differentiation.
- IP valuation drop: Investors and partners may devalue the company’s IP portfolio if core code is publicly available or compromised.
- Operational disruption: Stolen code can lead to delays in product launches, forced redesigns, or rushed patch cycles to mitigate exposed vulnerabilities.
- Legal and compliance liabilities: Breaches may violate NDAs, licensing agreements, or industry regulations (e.g., SOX, GDPR, HIPAA), leading to lawsuits or fines.
- Brand and reputation damage: Public disclosure of theft undermines customer trust, especially if security lapses are perceived as preventable.
Security impact
- Vulnerability exposure: Attackers can study the stolen code to identify security flaws, undocumented APIs, or exploitable logic paths.
- Supply chain infiltration: Compromised code can be reintroduced into the organization’s build process (via malicious pull requests or rogue forks), planting backdoors.
- Leaked credentials and secrets: Hardcoded API keys, passwords, or private certificates in code can provide attackers immediate network access.
- Extended attack surface: Source code theft often reveals internal architecture, third-party dependencies, and integrations, making lateral movement easier for adversaries.
- Persistent threat risk: Once source code is exposed, it cannot be fully contained. Threat actors may exploit it repeatedly for months or even years.
What are the security challenges in protecting developer workstations?
When it comes to protecting developer workstations, the security challenges include:
- High privilege access: Developer accounts often have elevated permissions, making them prime targets for attackers.
- Local storage of sensitive data: Unencrypted code, keys, and credentials stored on workstations can be instantly exploited if breached.
- Risk from unverified dependencies: Third-party libraries and tools may contain malicious code that compromises both the machine and source code.
- Phishing and social engineering: Attackers often target developers with convincing technical lures to deliver malware.
- Weak endpoint security: Inconsistent patching and disabled security tools leave developer machines vulnerable to intrusion.
- Remote work and BYOD challenges: Insecure networks and personal device usage expand the attack surface beyond corporate control.
- Lateral movement risk: A compromised workstation can serve as a launchpad to infiltrate broader systems and repositories.
What are the recommended security policies for CISOs?
Here’s a CISO-focused set of recommended security policies to prevent attacks on developer workstations and reduce the risk of source code theft:
- Enforce the principles of least privilege: Limit developer access to only the repositories, systems, and environments required for their role.
- Mandate MFA: Require MFA for all developer accounts, code repository logins, and CI/CD platforms.
- Implement secure code signing and repository controls: Use signed commits, enforce branch protections, and require code reviews before merges.
- Require EDR on developer machines: Deploy EDR tools with continuous monitoring to detect suspicious behavior in real time.
- Encrypt local storage and credentials: Ensure all developer workstations use full-disk encryption and secure vaults for API keys, tokens, and SSH keys.
- Control third-party library and dependency usage: Use dependency scanning and approved package registries to avoid malicious code injection.
- Conduct regular security awareness training for developers: Educate developers on phishing, social engineering, and secure coding practices.
- Enforce secure remote development environments: Leverage VPNs, Zero Trust Network Access, or cloud-based development sandboxes instead of local builds.
- Integrate SIEM for developer activity monitoring: Use solutions like Log360 to correlate workstation activity with code repository logs for early threat detection.
- Apply strong IAM and privileged access management: Use AD360 or similar IAM solutions to manage, audit, and automate the privileged access life cycle.
What are the recommended steps in an incident response playbook for handling source code theft?
When source code theft happens, it's important to act swiftly. Here are the recommended steps:
1. Detect and alert developer activity
- Monitor developer workstation logs, repository access logs, and API usage for unusual activity.
- Set up real-time alerts for:
- Unusual repository clone or pull activity.
- Large file transfers from developer machines.
- Access from unusual geolocations or hours.
2. Contain the access breach
- Immediately revoke or suspend the compromised developer’s accounts.
- Reset passwords and invalidate all active authentication tokens and SSH keys.
- Enforce conditional access rules to block high-risk logins until verified.
3. Investigate scope exposure
- Use log correlation to trace:
- Which files or repositories were accessed.
- Any lateral movement to other accounts or systems.
- Pull access history to identify what other privileged resources were touched.
4. Remediate and recover assets
- Rotate all exposed credentials, API keys, and certificates.
- Reinforce MFA policies for all developers.
- Remove unused accounts and stale privileges to reduce future risk.
5. Report and strengthen compliance
- Use SIEM's forensic audit reports for legal, compliance, and board updates.
- Leverage IAM to audit privileged account hygiene and close gaps.
- Feed investigation findings back into SIEM to tune detection rules for faster response in the future.
How does SIEM and IAM enhance the security posture of developer workstations?
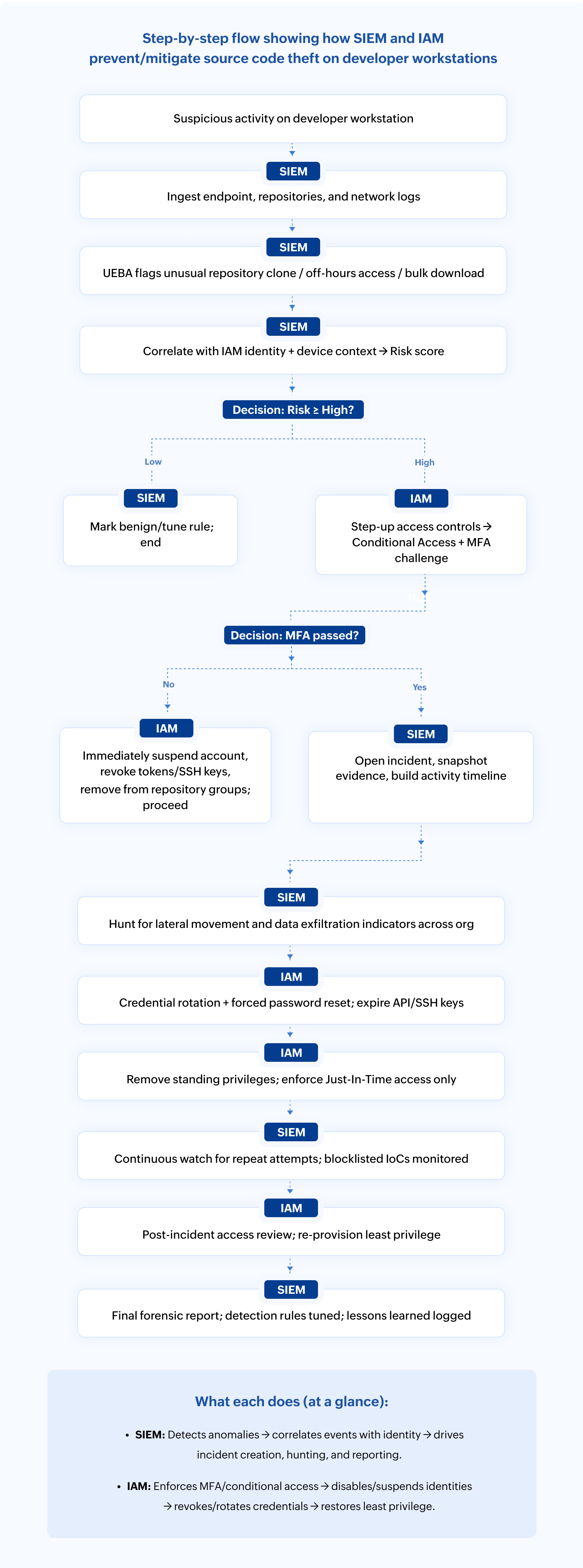
Figure 1: How SIEM and IAM strengthens source code security by preventing and mitigating theft on developer workstations.
How SIEM enhances developer workstation security
| Feature | How does it help? | Financial benefits |
|---|---|---|
| Real-time anomaly detection | Monitors workstation activity, code repository access, and network traffic to flag unusual patterns such as bulk code downloads or off-hours commits. | Prevents costly breaches early, avoiding expenses related to incident response, downtime, and reputational damage. |
| Insider threat identification | Correlates workstation logs with repository events to spot unauthorized code access or suspicious privilege use. | Minimizes financial loss from intellectual property theft and potential regulatory penalties. |
| Advanced threat intelligence integration | Leverages threat feeds to detect malicious IPs, domains, and indicators of compromise targeting developer environments. | Reduces the risk of targeted attacks that could lead to multi-million dollar source code leaks. |
| File integrity monitoring | Tracks changes to critical source code files and alerts security teams to unauthorized modifications. | Avoids rework, production delays, and legal liabilities from compromised or altered code. |
| Comprehensive forensic investigation | Stores and correlates historical logs for deep-dive investigations post-incident, helping identify attack paths and compromised accounts. | Cuts costs of prolonged investigations and helps speed up recovery to normal operations, reducing downtime losses. |
How IAM enhances developer workstation security
| Feature | How does it help? | Financial benefits |
|---|---|---|
| Principle of least privilege enforcement | Restricts developer access to only necessary code repositories and tools. | Reduces breach risk by limiting attack surface, avoiding costly data leaks and compliance fines. |
| Automated RBAC | Grants and revokes repository permissions automatically based on role changes. | Prevents unauthorized access that could lead to source code theft, saving on breach remediation costs. |
| MFA | Adds strong verification for repository and workstation logins to prevent unauthorized access. | Significantly lowers the risk of credential-based breaches, reducing potential multi-million dollar damages. |
| Privileged account management | Protects and audits elevated accounts, ensuring temporary and just-in-time privileges for sensitive tasks. | Prevents abuse of high-privilege accounts, reducing the likelihood of insider threats and related losses. |
| Account life cycle automation | Quickly deactivates accounts and revokes credentials when developers leave or change roles. | Eliminates security gaps that could lead to post-employment breaches, avoiding legal and reputational costs. |
How SIEM and IAM work together
| Feature | How does it help? |
|---|---|
| Unified threat and identity correlation | A SIEM solution like Log360 detects suspicious access attempts, while IAM solutions like AD360 confirms identity legitimacy |
| Automated incident response | When SIEM flags a high-risk event, IAM can automatically disable the account or enforce MFA challenges to contain the threat. |
| End-to-end access visibility | Combines identity access logs with activity logs for a full picture of who accessed what, when, and how. |
| Proactive privilege risk reduction | IAM limits excessive permissions, and SIEM alerts when those permissions are misused or exploited. |
| Compliance and audit readiness | Together, they generate detailed, audit-ready reports showing both identity governance and security event histories for regulations like ISO 27001, SOX, and the GDPR. |
Related solutions
ManageEngine Log360 is a unified SIEM solution with UEBA, DLP, CASB, and dark web monitoring capabilities. Detect compromised credentials, reduce breach impact, and lower compliance risk exposure with Log360.
Sign up for a personalized demoManageEngine AD360 is a unified IAM solution that provides SSO, adaptive MFA, UBA-driven analytics, and RBAC. Manage employees' digital identities and implement Zero Trust and the principles of least privilege with AD360.
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
