On this page
The Star Health Insurance data breach of 2024 is a reminder of the evolving cybersecurity risks facing the insurance industry and the operational complexity CISOs must navigate to protect sensitive customer data. According to IBM's Cost of a Data Breach Report 2024, the average cost of a data breach involving personal data is $4.88 million, and if it's disclosed by attackers, then the average cost is $5.53 million. A breach like Star Health's, which involved the attacker, xenZen, using compromised credentials and disclosing the data leak of 31 million customers' sensitive personal and medical data, is likely to cost Star Health exponentially more than $5.53 million. The attacker's attempt to sell Star Health's data was first brought to light by the United-Kingdom-based cybersecurity researcher, Jason Parker.
Star Health publicly acknowledged the data leak and revealed that the attacker demanded $68,000 to regain access to the stolen data. While this revelation was made by Star Health in October, its CEO had received emails from the attacker on Aug. 13, 2024, claiming that with the help of a privileged insider, they had gained unauthorized access to and stolen confidential customer data. This incident shows that CISOs must equip their teams to perform robust credential management and insider threat detection.
Star Health attack: An overview and timeline
In early August 2024, Star Health and Allied Insurance, one of India's largest health insurers, suffered a major data breach. On Aug. 14, 2024, the company reported the breach to its board of directors and the risk management committee, Tamil Nadu Cybercrime Department, CERT-In, and the Insurance Regulatory and Development Authority of India (IRDAI). Independent cybersecurity experts were immediately brought in to investigate the incident.
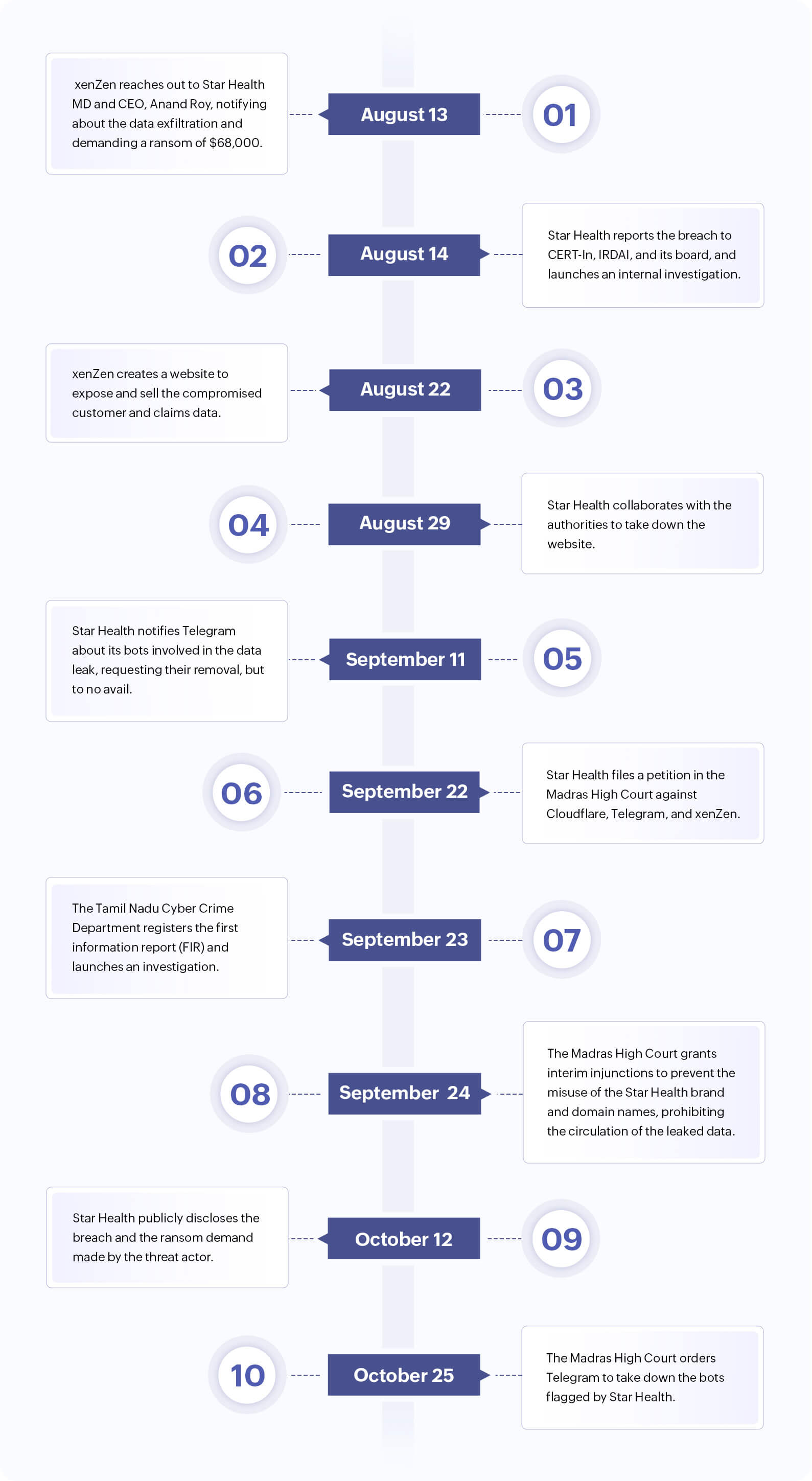
Figure 1: Timeline of events—Star Health Insurance data breach 2024.
The breach was allegedly orchestrated by a Chinese threat actor called xenZen for financial and geopolitical reasons. XenZen claimed to have colluded with Star Health's CISO to gain illegal access to 7.24TB of data, including records of over 31 million customers and 5.7 million insurance claims, as shown in Figure 2.

Image source: HackManac
Figure 2: The Star Health Insurance data leak exposed by xenZen.
While the leaked customer data included sensitive information, such as full name, mobile number, email and residential address, permanent account number, gender, date of birth, height, weight, preexisting medical conditions, policy number, nominee details (i.e., name, age, relationship, and claim %), the claims data leaked included customers' Aadhar and PAN card photo, claims and amount details, detailed health reports, contact details, and more (see Figure 3). Apart from hosting a sample of the leaked data on a website, xenZen also used Telegram bots to distribute and sell the stolen data. Star Health claims to have requested Telegram take down the bots involved in their data leak permanently multiple times, but it had failed to do so.
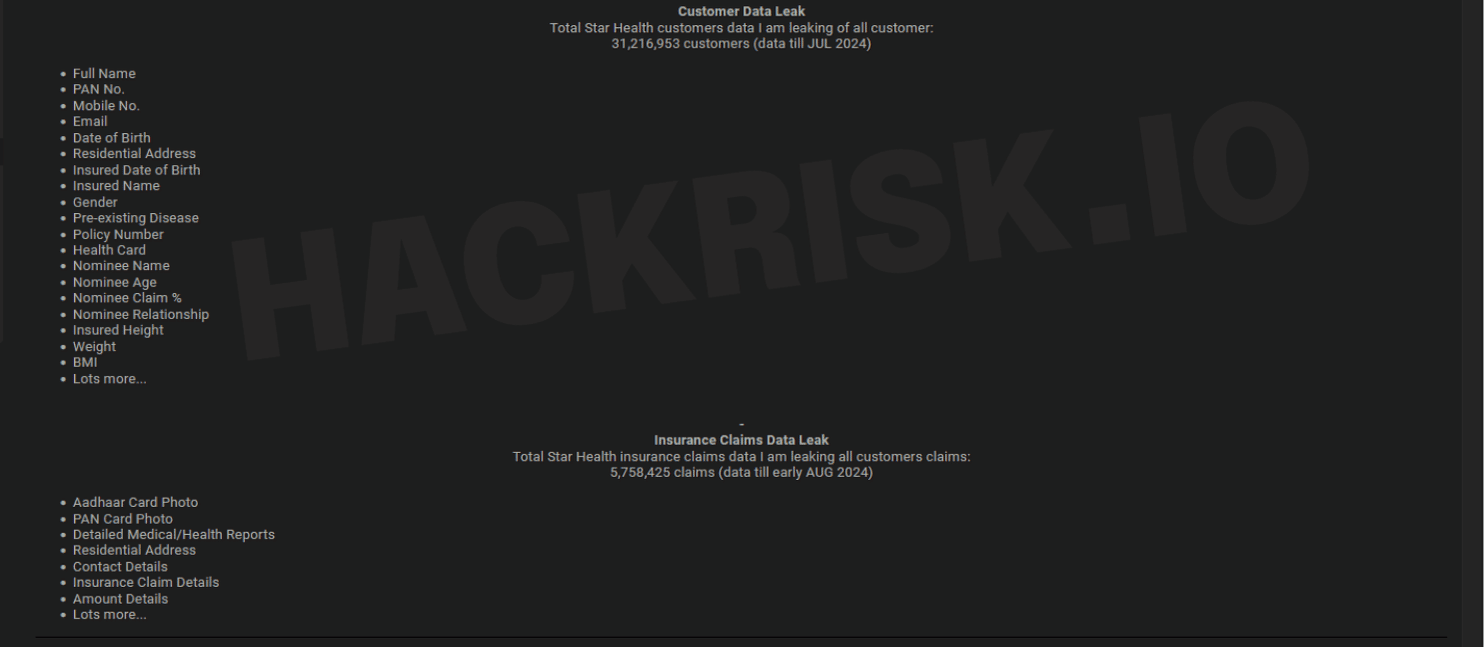
Image source: HackManac
Figure 3: List of sensitive data exposed in the leak.
To add to this nightmare, xenZen, as proof of the CISO's collusion, released a video containing the alleged screenshots of the text messages shared between the CISO (as mc6) and the threat actor along with an email from the CISO sharing the credentials for xenZen to access customer data as shown in Figure 4. Apart from implicating the CISO, xenZen claimed that the CISO demanded more money than they had agreed on because senior management also wanted a share.
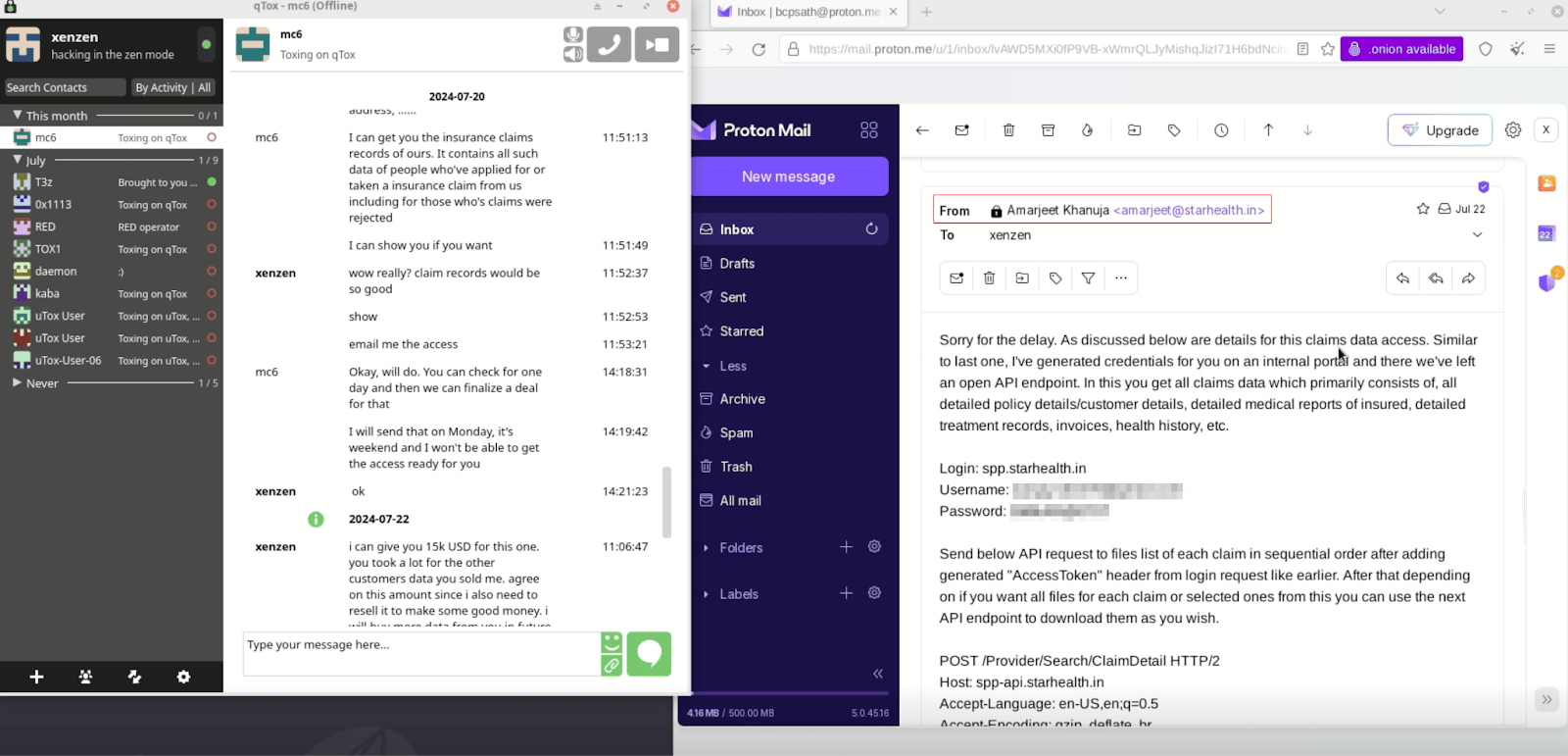
Image source: CloudSEK
Figure 4: Screenshots of alleged communication between the Star Health CISO and xenZen.
When news of the leak broke, Star Health shares plummeted by 11% while the insurance company was investigating internally to verify the claims made by the attacker. Later, it also filed a petition in the Madras High Court against the attacker, Telegram, and Cloudflare for allowing the attacker to use their hosting services to expose the stolen sensitive data. Moreover, CloudSEK, the independent experts hired by Star Health, revealed that its investigations showed that the evidence shared by xenZen against the CISO were falsified and fabricated to distort public opinion and sidetrack the investigation with false information.
The Madras High Court granted a temporary injunction on Sept. 24, 2024, directing all parties to disable the websites and bots to prevent further dissemination of the compromised sensitive data. While the original incriminating sites and bots were taken down, xenZen created mirror sites and self-hosted bots, making it difficult to take them down permanently. Since Telegram stated that it was unable to monitor content independently, the Madras High Court ordered Telegram to take down the posts and block the bots flagged by Star Health on Oct. 25, 2024, with the latter emailing Telegram the username(s) and URL(s) of the bots involved in the data leak.
Star Health data breach attack execution
The attack, according to CloudSEK, unfolded in multiple stages:
- Credential theft: The hacker, xenZen, exploited stolen credentials from the dark web, contradicting claims of insider collusion.
- Exploitation of an API vulnerability: xenZen then used an insecure direct object reference (IDOR) vulnerability in Star Health’s API. IDOR is a vulnerability where an attacker can access or modify data by directly manipulating input parameters—such as changing a URL, API request, or form field—without proper authorization checks. This flaw often occurs due to insufficient access controls and can lead to unauthorized access to sensitive information, account takeovers, or data leaks, which is what happened in the case of Star Health.
- Data exfiltration and ransom demand: After obtaining access, xenZen stole sensitive customer information and attempted to extort Star Health with a ransom demand. xenZen also hosted websites and Telegram bots to sell the stolen data.
- Disinformation campaign: The hacker falsely accused the CISO of involvement and spread misleading narratives to damage the company’s reputation. The emails xenZen shared as proof of the CISO's collusion were the result of the attacker using the Inspect Element feature to manipulate the HTML code to portray a false origin for the email and its sender.
Consequences of the data breach
Financial losses and market impact
- The attacker demanded $68,000 in ransom for the stolen data, though Star Health has not confirmed if the ransom was paid.
- Following the breach disclosure, Star Health's stock price declined by approximately 11%, reflecting investor concerns over security lapses and regulatory scrutiny.
- The breach has led to additional legal costs since Star Health is pursuing lawsuits against the hacker, Cloudflare, and Telegram.
Regulatory scrutiny and potential fines
- The IRDAI has issued a show-cause notice to Star Health over compliance violations, citing breaches of multiple regulatory guidelines, including:
- IRDAI (Health Insurance) Regulations, 2016
- IRDAI (TPA – Health Service) Regulations, 2016
- IRDAI (Protection of Policyholders’ Interest) Regulations, 2017
- It may also face severe financial penalties under India’s Digital Personal Data Protection (DPDP) Act 2023, which (if fully enforced) allows fines of up to ₹500 crore (approximately $60 million) for data protection violations.
Reputational damage and customer distrust
- Large-scale customer data exposure has damaged Star Health’s credibility, making it vulnerable to customer churn and a decline in new policy sales.
- Identity theft and medical fraud risks from leaked health data could lead to prolonged litigation and compensation claims.
- Star Health’s response—initiating legal action against involved parties and improving security controls—may help mitigate some risks, but restoring trust will require long-term efforts.
Key takeaways for CISOs from the Star Health data breach
1. Reduce API risk exposure with proactive security measures
The breach exploited insecure API endpoints, allowing hackers to extract data. CISOs must ensure API resilience to mitigate data exfiltration risks and regulatory penalties. This can be achieved by:
- Regularly conducting API security assessments and penetration testing to identify vulnerabilities like an IDOR.
- Implementing access controls, such as role-based access control and OAuth, to restrict unauthorized API access.
- Encrypting data in transit and at rest.
- Implementing rate limiting and anomaly detection to detect unusual access patterns.
2. Implement stronger encryption standards
The breach exposed unencrypted personal and medical data, making it easily readable by attackers. CISOs should implement:
- End-to-end encryption for sensitive customer data.
- Tokenization to mask identifiable information.
3. Implement a Zero Trust architecture
Adopt a Zero Trust security model, which eliminates implicit trust and continuously verifies access based on identity, device, and context. CISOs should ensure:
- Multi-factor authentication (MFA) for all access points and passwordless authentication where feasible.
- Implementation of the principle of least privilege to ensure just-in-time access and just enough access, and revoke permissions dynamically.
- Adequate network segmentation to isolate critical networks and sensitive environments from lateral movement attempts.
- Real-time security monitoring to enhance visibility, prevent threats, and reduce breach impact.
- Robust endpoint security by deploying antivirus, anti-malware, and endpoint detection and response solutions to protect against malware and unauthorized access.
- Third-party risk management by periodically assessing the security practices of third-party vendors and partners to ensure they meet their organization's security standards.
- A comprehensive patch management strategy, preferably automated, to ensure all systems and software are up to date with the latest security patches.
4. Strengthen insider threat management
There were allegations (later proven false) of an insider data leak by the CISO. While this was misinformation, it highlights the importance of:
- Privileged access management to enforce strict controls over high-level accounts and minimize the risk of unauthorized access and credential-based attacks.
- A SIEM solution with UEBA capabilities to monitor and analyze user activities for unusual or suspicious behavior indicative of insider threats and account compromises.
- Deploying data loss prevention (DLP) solutions or a DLP-integrated SIEM solution to monitor and control the movement of sensitive data within and outside the organization.
5. Enforce continuous dark web monitoring and proactive threat intelligence
The data breach occurred because the attacker obtained compromised credentials from the dark web. To prevent future attacks, CISOs must ensure:
- Proactive monitoring of the dark web to prevent credential-based attacks that increase regulatory risk and cyber insurance costs.
- Automation of alerts for credential reuse attempts across corporate accounts.
6. Strengthen incident response and crisis management
Star Health failed to promptly notify its customers and the public of the breach, and when it eventually did, it led to stock value reducing by 11%. To ensure continued customer trust and minimize financial impact, it's crucial for CISOs to:
- Develop a rapid breach response plan and incident response playbook that includes cyber forensics, containment, and legal compliance.
- Establish a crisis communication strategy to counter misinformation and reputational attacks, and ensure that the concerned stakeholders are notified on time along with the measures taken (or planned) to protect them against identity and financial fraud.
7. Enhance data governance and regulatory compliance
India’s DPDP Act will increase regulatory scrutiny. Enterprises must:
- Conduct periodic audits for compliance.
- Establish transparent breach disclosure protocols.
- Adopt privacy by design principles.
8. Invest in employee training and user education
In the context of cybersecurity, enterprises are only as strong as their weakest link: humans. CISOs must ensure that their security teams:
- Continuously educate employees about cybersecurity best practices and the latest threats.
- Conduct regular training sessions and phishing simulations to help employees recognize and respond to potential attacks.
Related solutions
ManageEngine AD360 is a unified IAM solution that provides SSO, adaptive MFA, UBA-driven analytics, and RBAC. Manage employees' digital identities and implement Zero Trust and the principles of least privilege with AD360.
To learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM solution with UEBA, DLP, CASB, and dark web monitoring capabilities. Detect compromised credentials, reduce breach impact, and lower compliance risk exposure with Log360.
To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
