In any organization, a single user may use different usernames to access various operating systems, devices, and applications. For enterprises, this administrative challenge can easily translate into a security issue, particularly if the security analytics solution that tracks user behavior is unable to attribute discrete user account actions to the actual individual.
With UIM in Log360, different user accounts are mapped to the single user, subsequently improving anomaly detection across platforms for accurate user risk scoring.
This Whitepaper covers:
- The need for UIM in anomaly detection
- How Log360 maps user identities
- Benefits of comprehensive risk scoring
Introduction
In any organization, a user may access numerous devices and applications, but not always with the same username or credentials. As a result, organizations end up monitoring different user accounts from different sources separately, while they actually belong to a single user. User identity mapping (UIM) is the process of mapping different user accounts in an enterprise to a base account, such as Active Directory (AD), by matching common attributes. Log360, ManageEngine's SIEM solution, uses UIM to determine the anomalous activities of a single user across multiple domains and collates these activities together. Subsequent user risk scoring becomes more accurate as all of the user's identities in the network are synced together.
What is the need for user identity mapping (UIM)?
Consider your username for your Linux, Windows, and SQL accounts. Are they the same? Devices and applications use platform-specific user registries that are distinct from each other.
The table below shows one user, Michael Bay, using different user identities to log on and access various devices and applications.
| Device/Application | Attribute | Value |
|---|---|---|
| Windows | Username | Mike |
| Windows | SAM Account Name | michael |
| Unix | Source | Michael_4182 |
| Cisco Router | Username | michael.b |
| Azure | Username | michael@abc.com |
| SQL Server | Username | michael |
Having such discrete user accounts in an enterprise network is a common problem organizations face, especially during access restriction or single sign-on implementation. Also, this administrative challenge can hinder an organization's security performance if the security analytics solution is not able to map user behavior across platforms and assign risk scores accordingly. Imagine monitoring various user accounts in separate silos, each with a different risk score, even though it's a single employee performing them. This is the issue at hand.
The UIM feature in Log360 enhances the anomaly detection capability by linking all such distinct user accounts to a base account, resulting in a single representation of the user, making it easier to detect abnormal behavior across multiple sources and providing comprehensive risk scoring.
How Log360 maps user identities
Users are mapped across the network with their AD account as the basis, or source account, using mapping configurations. Mapping configurations are rules that admins can create using the UIM feature by specifying which of the user's source account attributes and target account attributes should match. The Source Attribute is a value from the user's AD data (e.g., SAMAccount_Name). The Target Attribute could be any field value in the target account (e.g., the SQL server's User Name field). AD user data is automatically fetched by Log360 when a domain is added to the product.
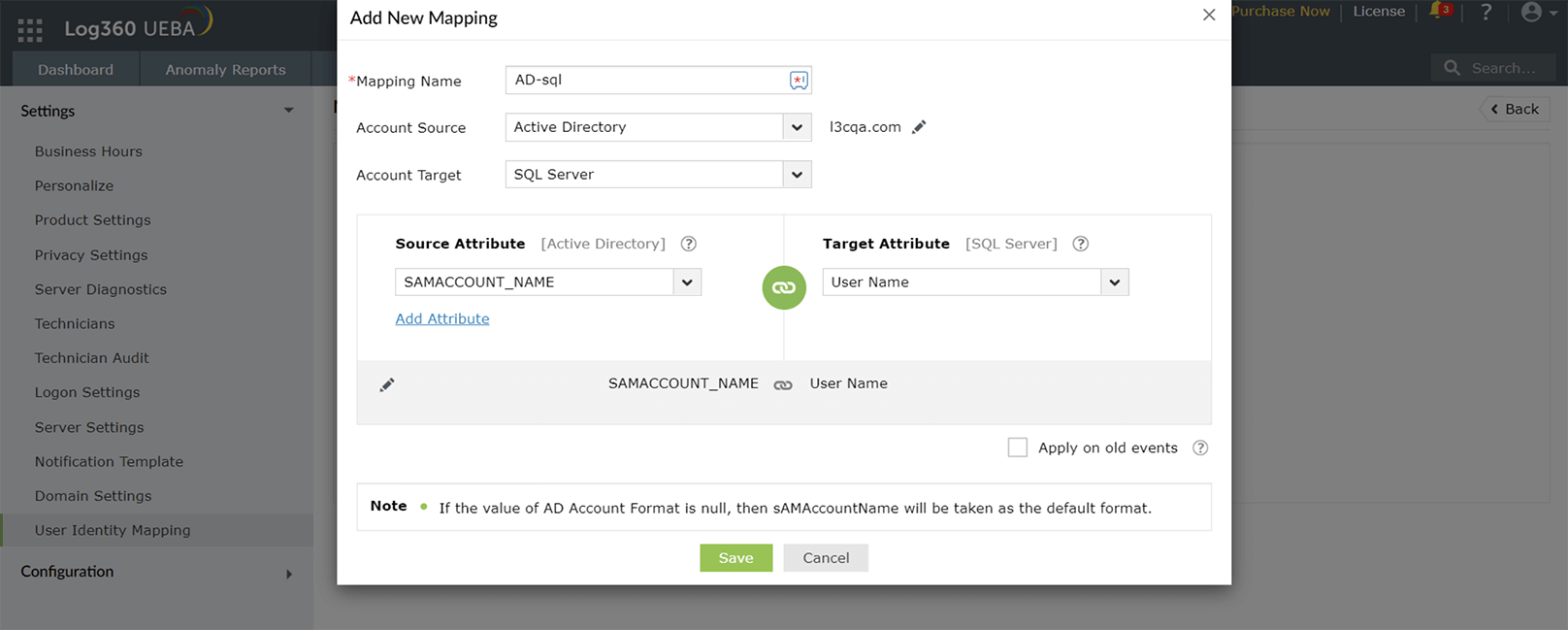
Figure 1: Creating new mapping to link user accounts
Log360 will then look for all SQL user accounts and AD accounts that meet this criteria and map them. Similarly, a mapping can be created with Windows as the target account, specifying the Target Attribute that will be the same as the Source Attribute (the SAM Account Name of the AD account).
Admins can also create individual identifier rules for each specific AD user to map relevant user accounts with that particular AD user.
Admins can review these mappings identified by UIM and verify them. The individual user accounts (Windows and SQL) are thus mapped with AD, and all anomalies associated with the user across sources can be viewed in the dashboard.
Comprehensive user risk scoring
Log360 collects logs from across the network, identifies suspicious activities from users and entities, and generates a risk score. This helps admins track and prevent occurrences of insider threats, account compromise, logon anomalies, and data exfiltration. The dashboard for the user displays the user's overall risk score, the risk score trend, the peak risk score, as well as the anomalies that contribute to the risk score.
With UIM, the user accounts that were earlier considered separate and had individual risk scores will now have only one representation and one risk score. The consolidated risk score is calculated from the individual's anomalies across platforms (Windows, SQL, or Linux). Figure 2 shows user Michael and his associated anomalies across different platforms in the network.
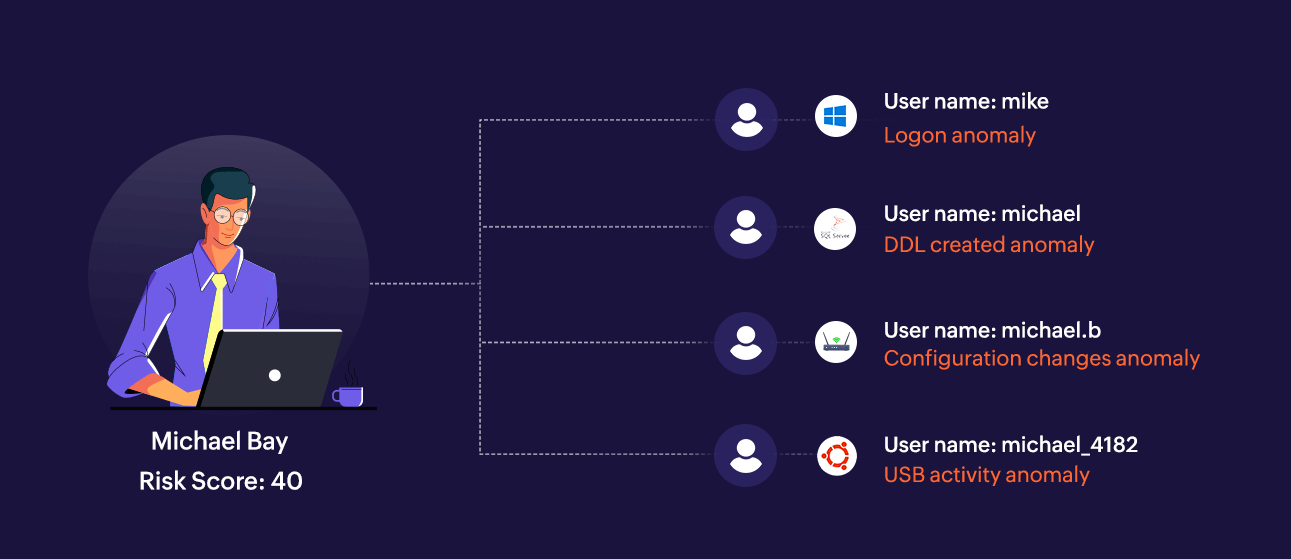
Figure 2: The various user identities of user Michael and corresponding anomalies performed
Michael from our example will have just one representation on the User Risk Score dashboard once all of his accounts—including those of Windows, SQL Server, and other platforms—are mapped to his AD account and verified by the admin. The dashboard compiles all anomalies from various platforms and calculates his risk level accordingly.
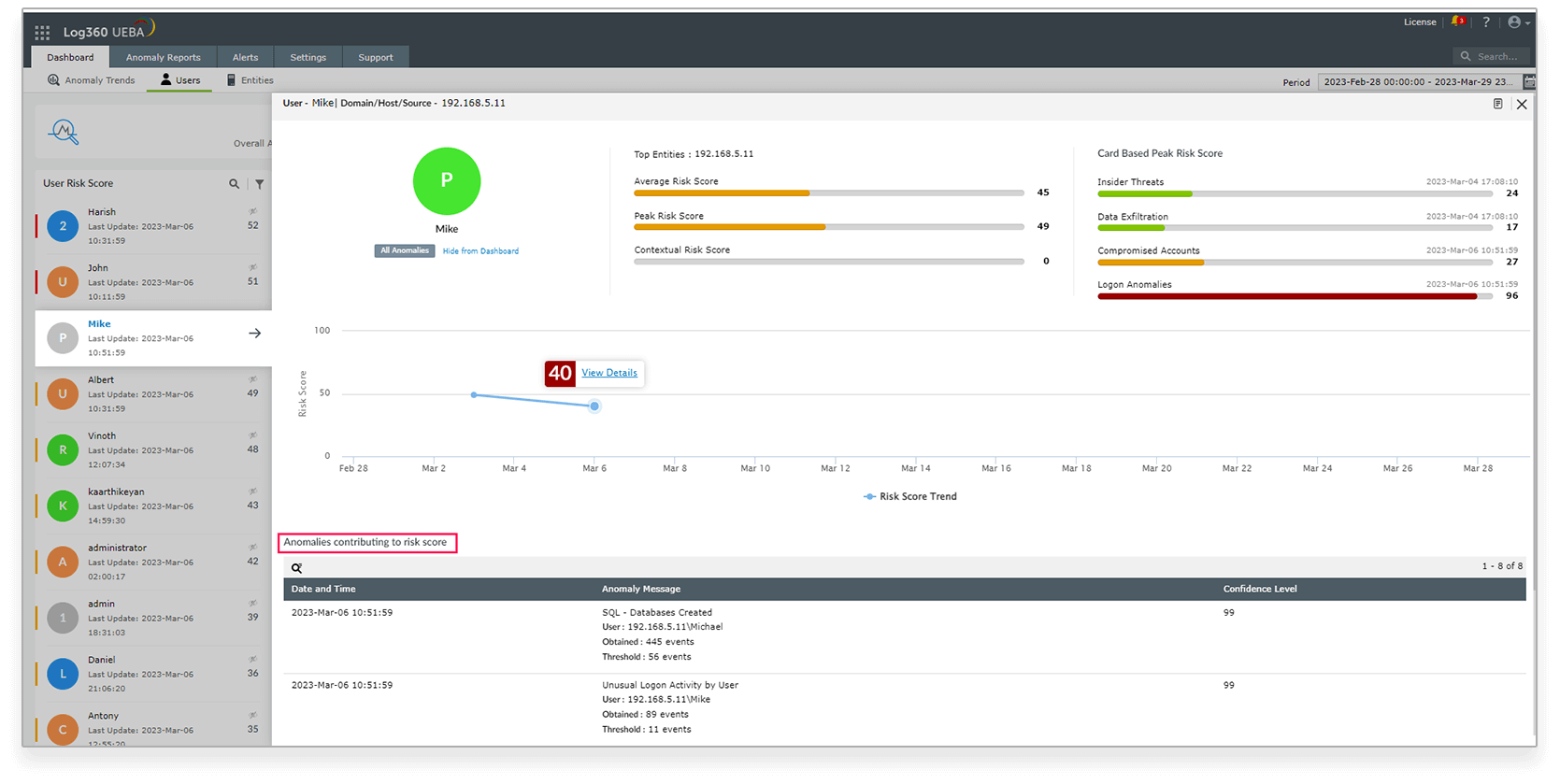
Figure 3: User risk dashboard in Log360
About Log360
Log360 is a unified SIEM solution with integrated UEBA, DLP, and CASB capabilities to detect, investigate, and respond to security threats. It offers threat intelligence, machine-learning-based anomaly detection, rule-based attack detection, event correlation, log forensics, cloud security monitoring, and incident management to address complex security use cases of organizations. Log360 ensures the security of different on-premises, hybrid, and cloud network components, such as AD, perimeter devices, workstations, databases, business-critical applications, and cloud services, through continuous monitoring.
The user interface is simple to understand and use. With its intuitive dashboards and advanced security analytics capabilities, a security analyst will immediately know if a threat is lurking anywhere in the network. With alerts and contextual responses, they can also resolve a problem before it turns into a major security incident.
With UEBA, which analyzes user behavior using ML algorithms, a security analyst can track anomalous activities by suspicious users and entities, assign risk scores, and get alerted about anomalous activities in real-time.
For more information about Log360 UEBA, visit manageengine.com/log-management/user-and-entity-behavior-analytics