-
Gain critical logon insights
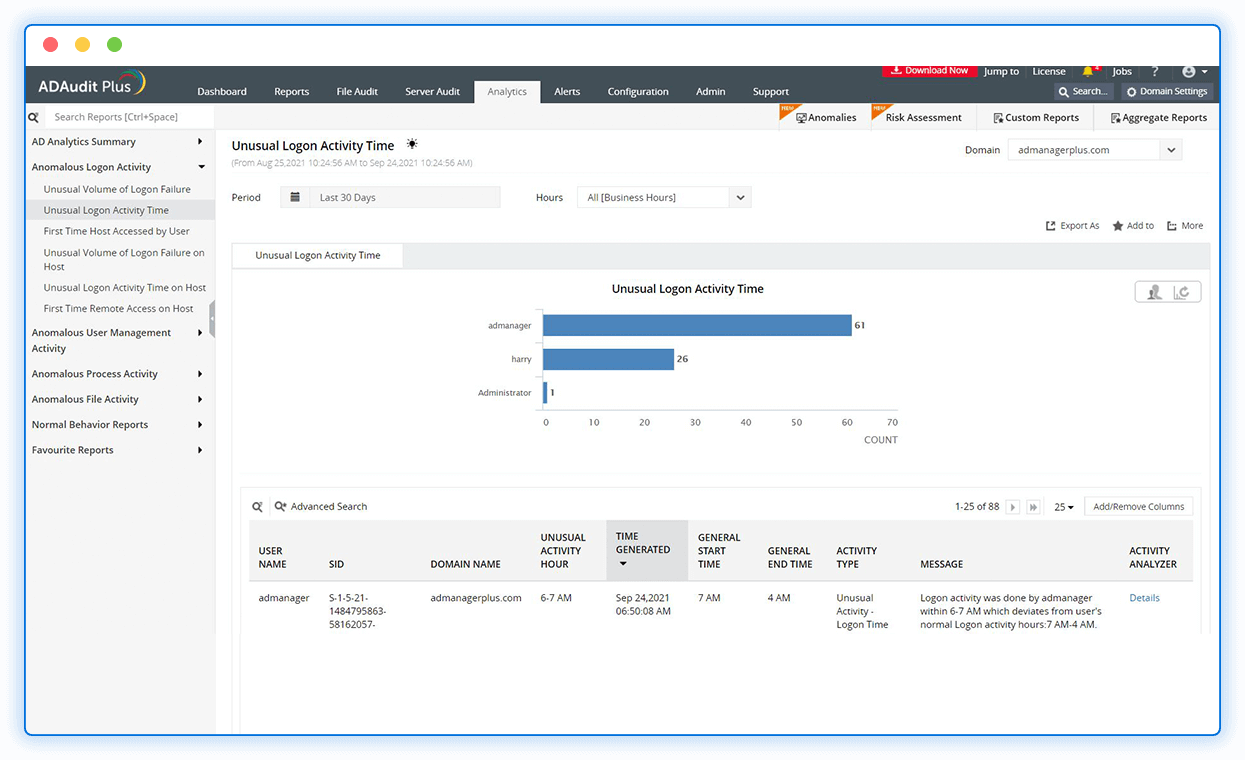
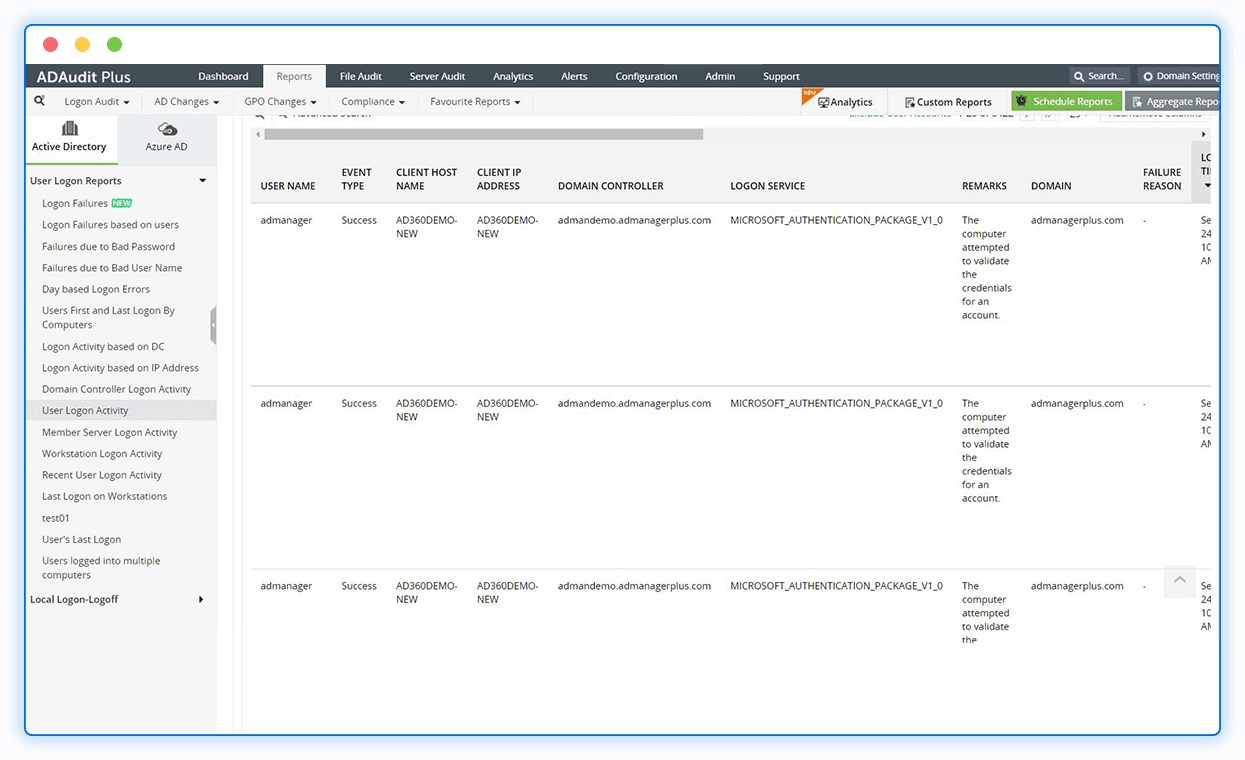
Track user-specific information for each logon activity, including details on who logged in, when, and from where.
-
Monitor employee work hours
Observe the actual time spent working by analyzing various metrics, such as first logon, last logout, and idle and active periods.
-
Scrutinize failed login attempts
Monitor repeated failed login attempts for signs of malicious insider activity, notify admins, and use scripts to initiate threat responses that will disconnect the rogue user's session.
-
Generate actionable reports
Gain security insights by monitoring employees logged on to multiple computers, terminated user sessions, RADIUS logon activities, and much more.
Track employees' logon and logoff activity in detail using our AD auditing software.