-
Track user management actions
Keep track of privileged users and report on unchecked user creation, deletion, modification, and password changes and resets to identify privilege abuse.
-
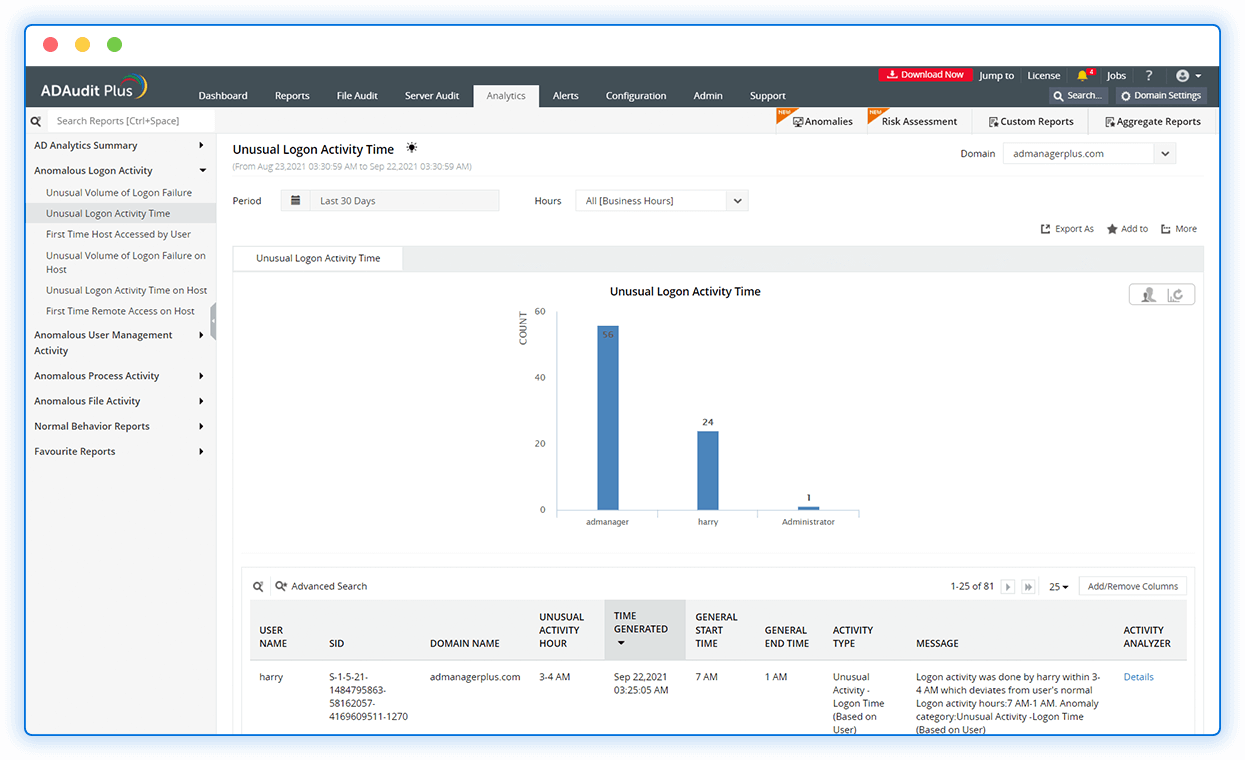
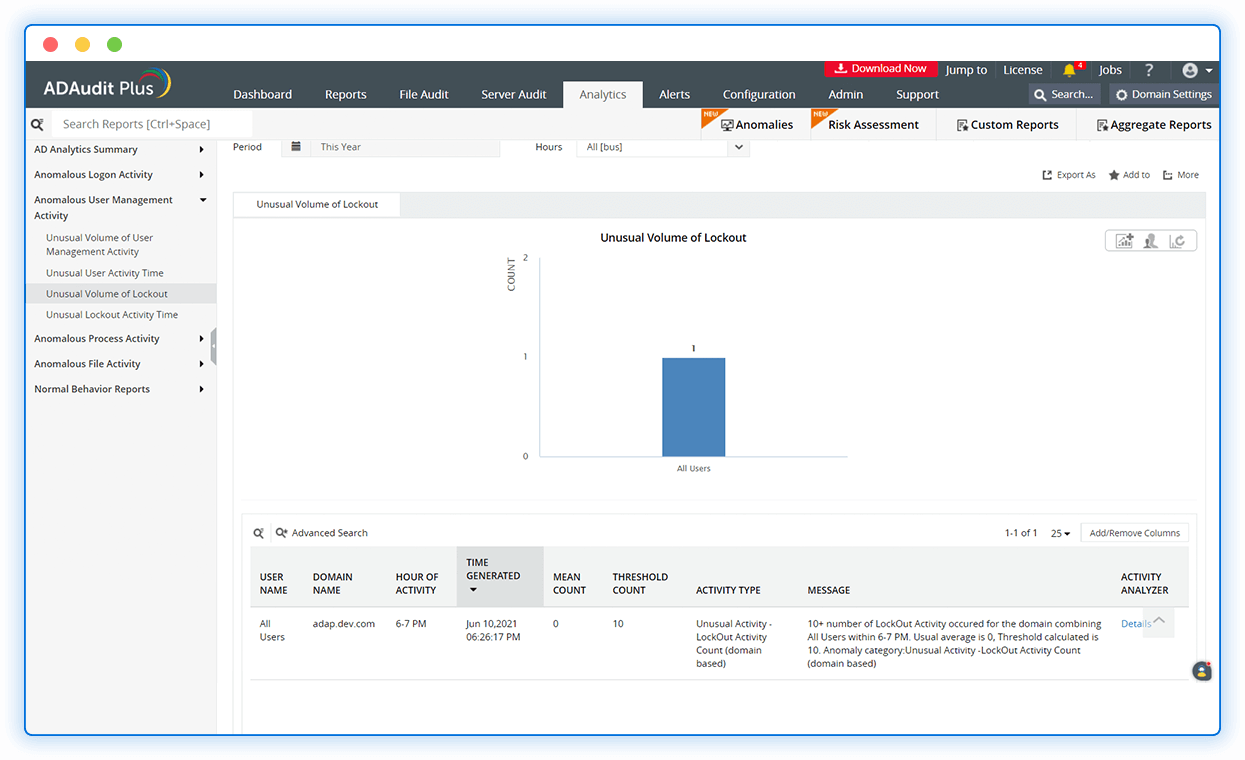
Investigate anomalous logons
Detect abnormal logon activities, like logons occurring at unusual times, excessive logon failures, and surges in account lockouts with detailed reports.
-
Identify suspicious file activity
Track every file access attempt and spot anomalous activities, including unusual spikes in failed file accesses, unwarranted file modifications, and multiple file deletions.
-
Be notified in real time
Get instant SMS and email notifications when thresholds are breached, and execute automated threat responses to security incidents.
Manage insider threats in your AD using our insider threat management software.