-
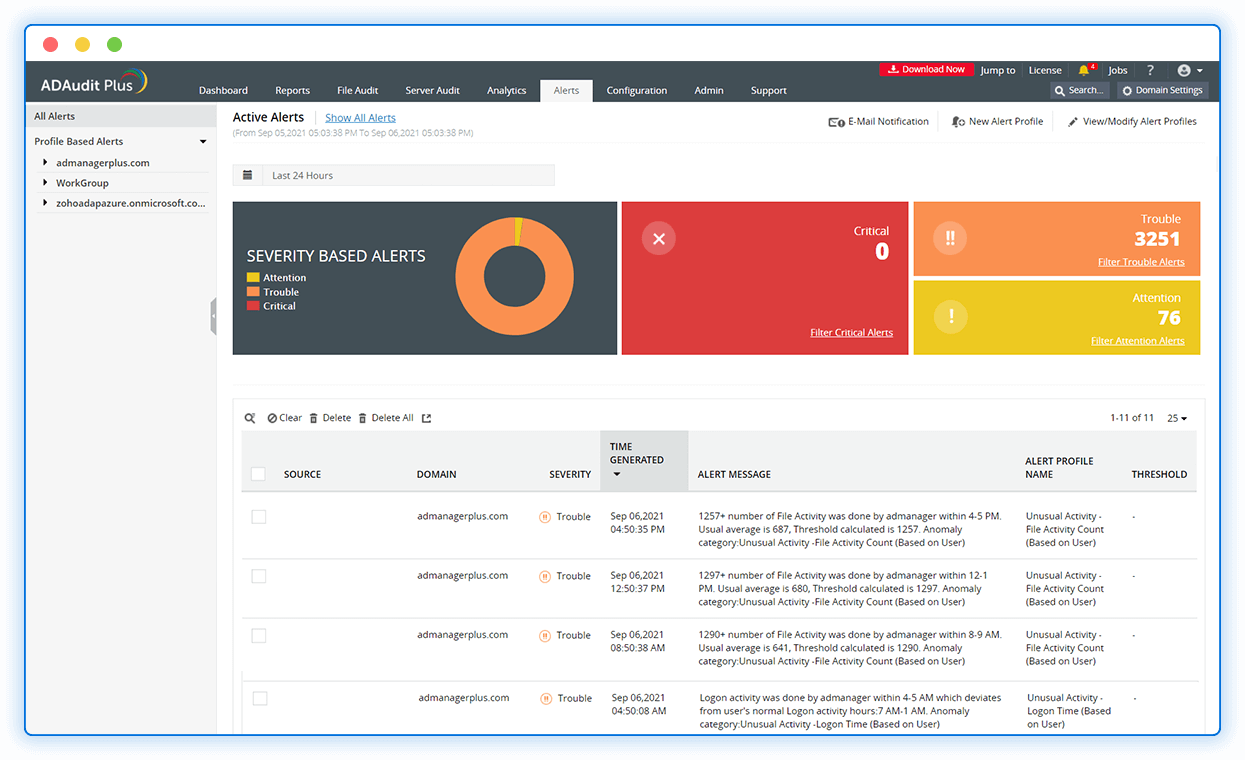
Spot abnormal logon activity
Leverage UBA to detect suspicious logon activities, like unusual spikes in logon failures, excessive account lockouts, and logons occurring outside business hours.
-
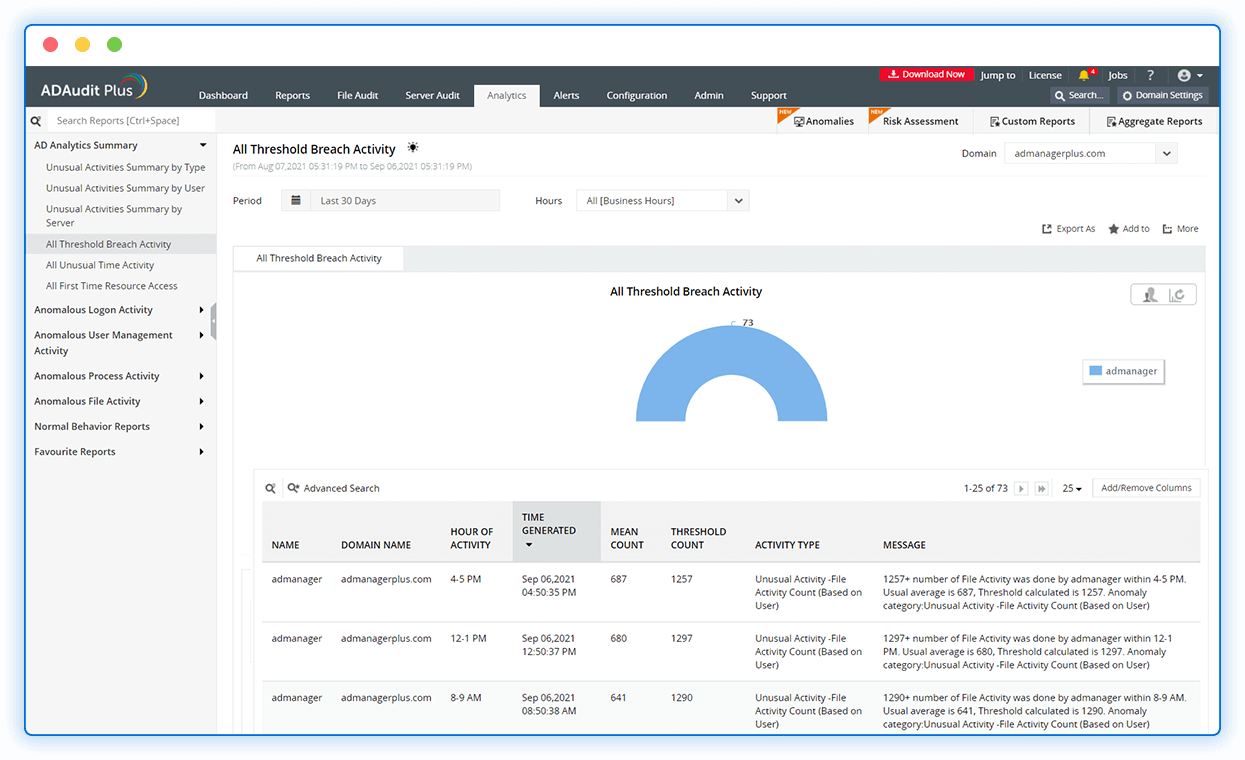
Track suspicious file activity
Investigate anomalous file activities, like file accesses at odd times, sudden surges in failed file accesses, and unauthorized modification or deletion of critical files.
-
Detect privilege abuse
Track the actions of high-privileged users and identify user management activity occurring at irregular times, including unusual volumes of user creation, deletion, and modification.
-
Automate threat response
Remediate security threats by automatically executing custom scripts to disable user accounts, disconnect user sessions, and shut down computers.
Combat insider threats in your Active Directory using our insider threat monitoring tool.