Configuring Single Sign-On (SSO) using SAML 2.0 for Okta
(Feature available only in Enterprise Edition)
ManageEngine Password Manager Pro offers support for SAML 2.0, which facilitates integration with Federated Identity Management Solutions for Single Sign-On. Password Manager Pro acts as the Service Provider (SP) and it integrates with Identity Providers (IdP) using SAML 2.0. The integration basically involves supplying details about SP to IdP and vice-versa. Once you integrate Password Manager Pro with an IdP, the users have to just log in to IdP and then, they can automatically log in to Password Manager Pro from the respective identity provider's GUI without having to provide credentials again. Password Manager Pro supports out-of-the-box integration with Okta.
Note: Password Manager Pro allows users to configure SAML SSO for Secondary server as a service provider, which allows users to log in to Password Manager Pro using the Secondary server when Primary is down.
Steps Required
Integrating Password Manager Pro with Okta involves the following four steps:
1. Adding Password Manager Pro as an application on the Okta dashboard
- Log in to your Okta Admin account and click the Applications tab on the left-side panel.
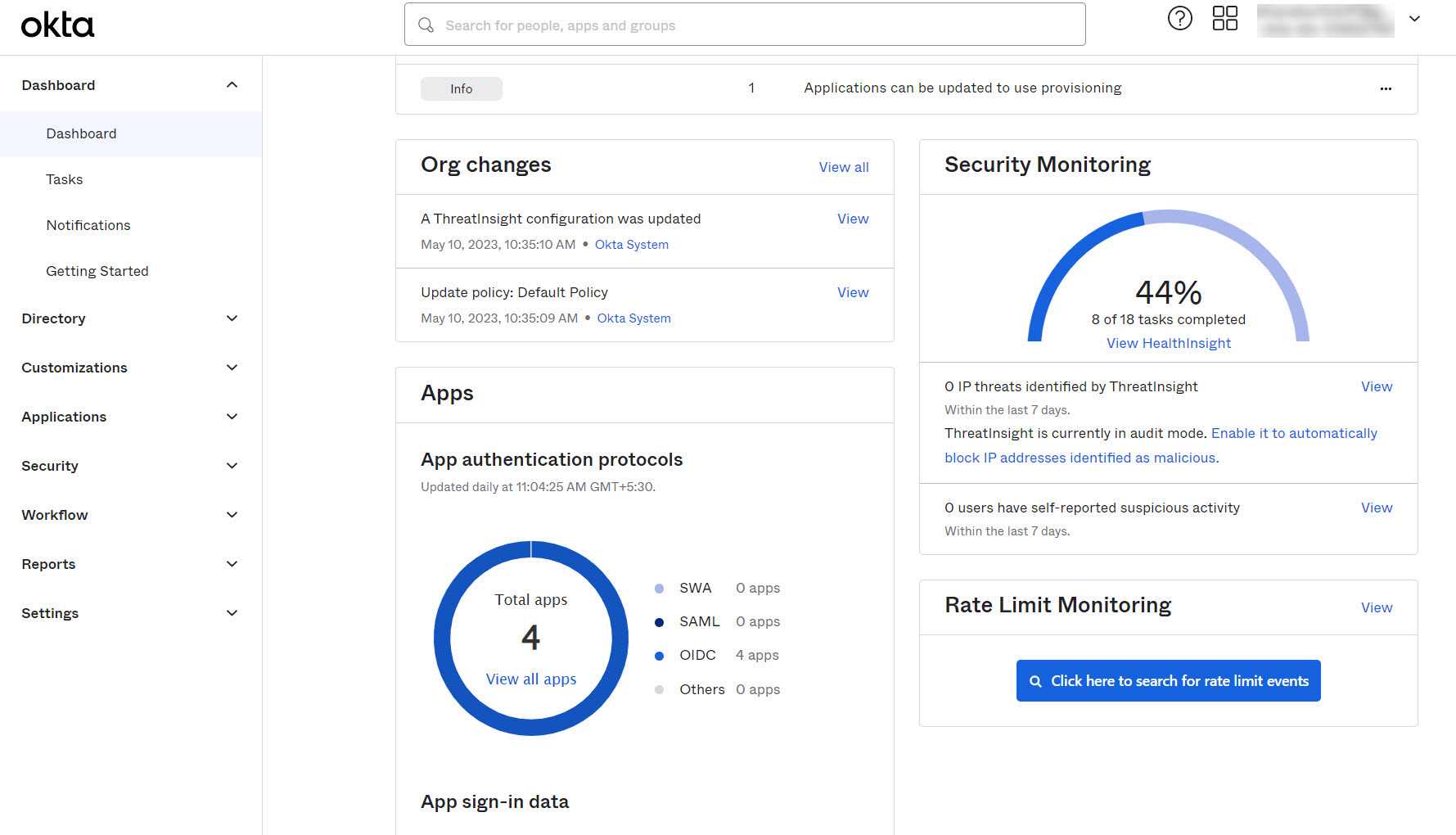
- As shown in the image below, click the Create App Integration button.
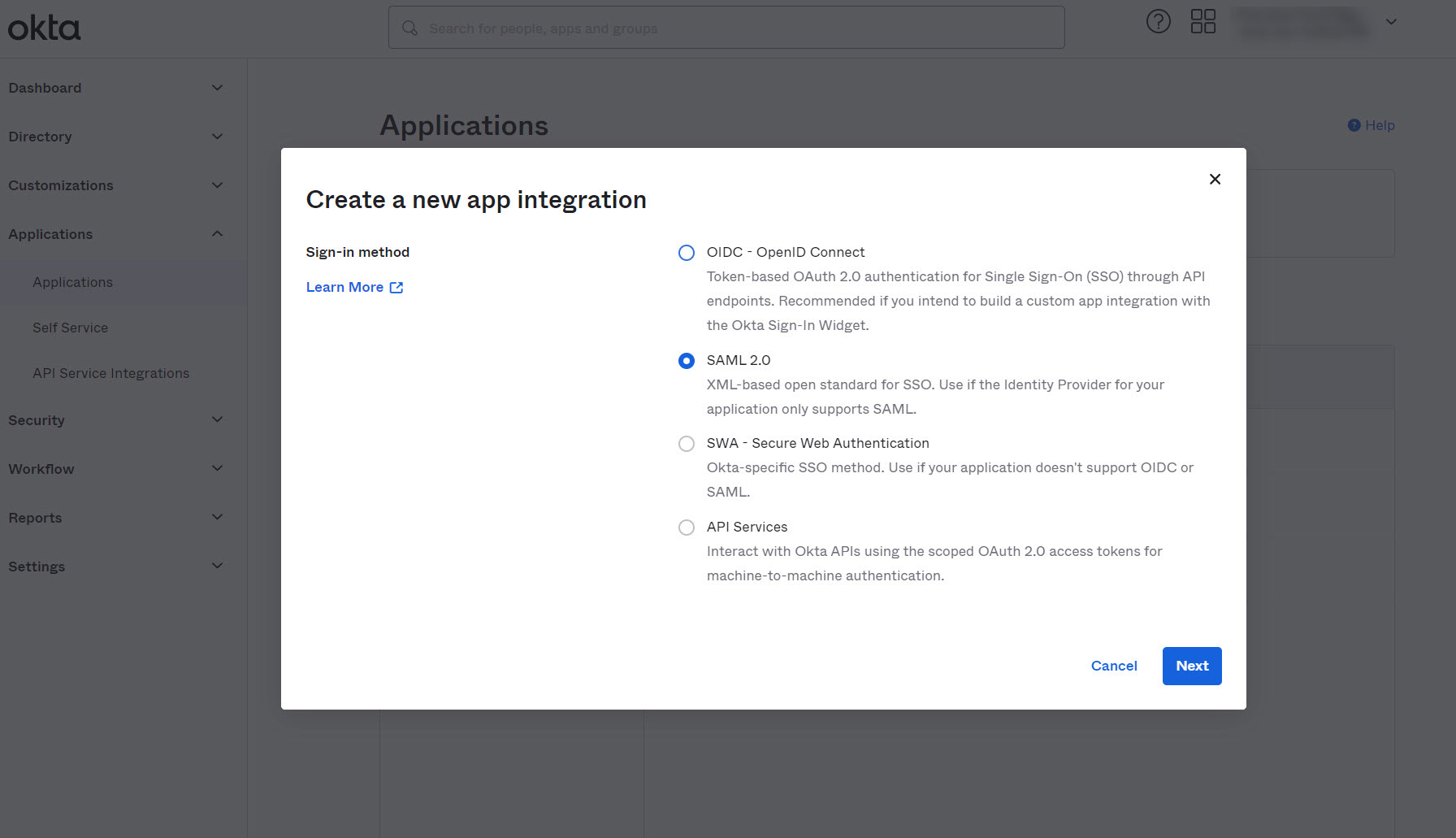
- Immediately, a window will pop-up asking information about the type of application integration. Select SAML 2.0 and click Next.
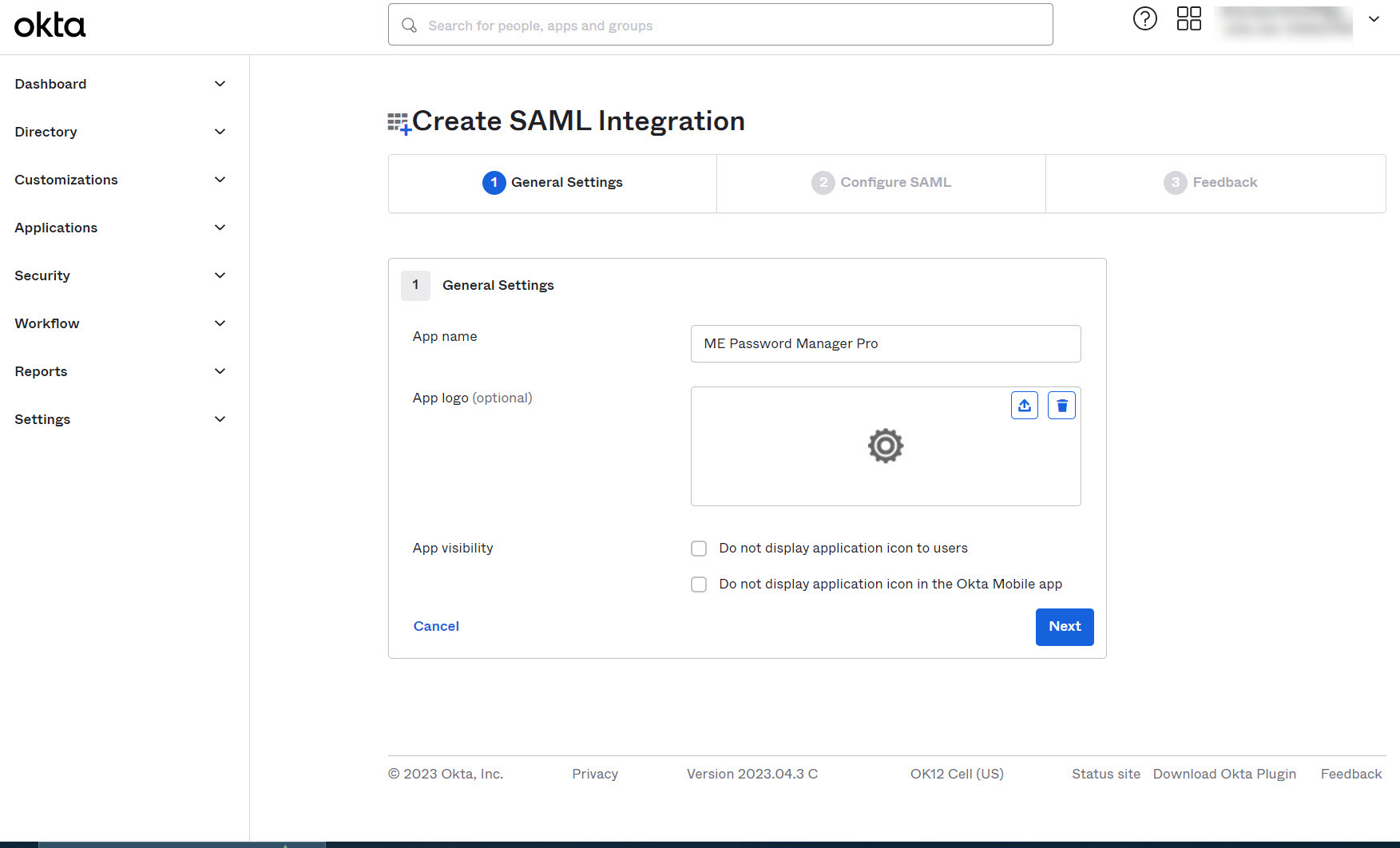
- Enter the name of the app being added (ME Password Manager Pro) in the General Settings section. You can also upload a logo for the app (optional). When you are done, click
Next.
- Configuring SAML integration consists of providing details about the Service Provider (ME Password Manager Pro) to Okta. To access these details, do the following:
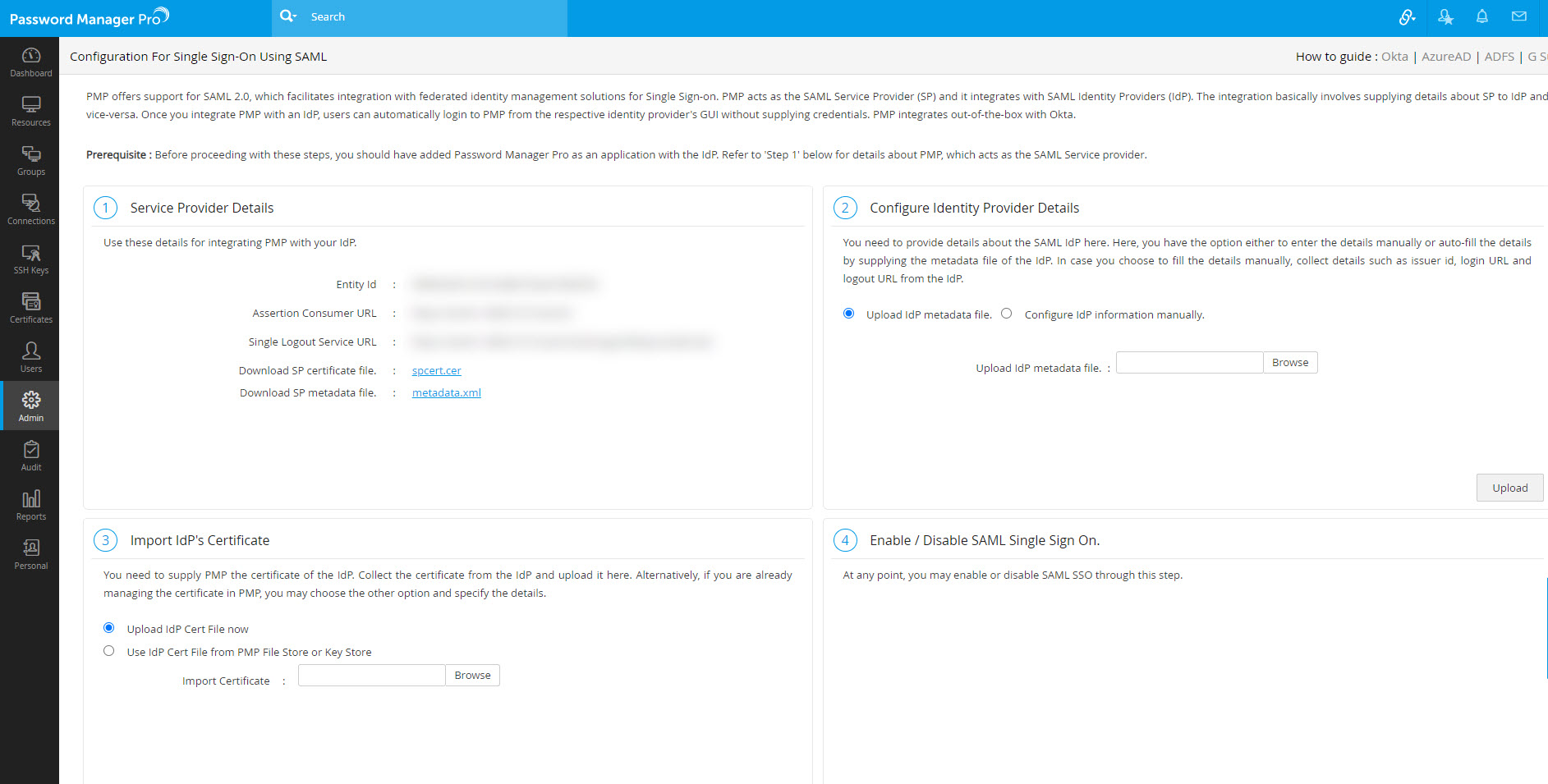
- Navigate to the Password Manager Pro homepage and select Admin >> Authentication >> SAML Single Sign-On.
- Under 1. Service Provider Details, you will find Entity Id, Assertion Consumer URL and Single Sign On URL; copy the values.
- Go to Admin >> Settings >> Mail Server Settings.
- Under Access URL, update the required URL and click Save.
- Return to Okta's SAML Settings page.
- For MSP, enter Assertion Consumer URL from Password Manager Pro under Single sign-on URL and select the Use this for Recipient URL and Destination URL checkbox.
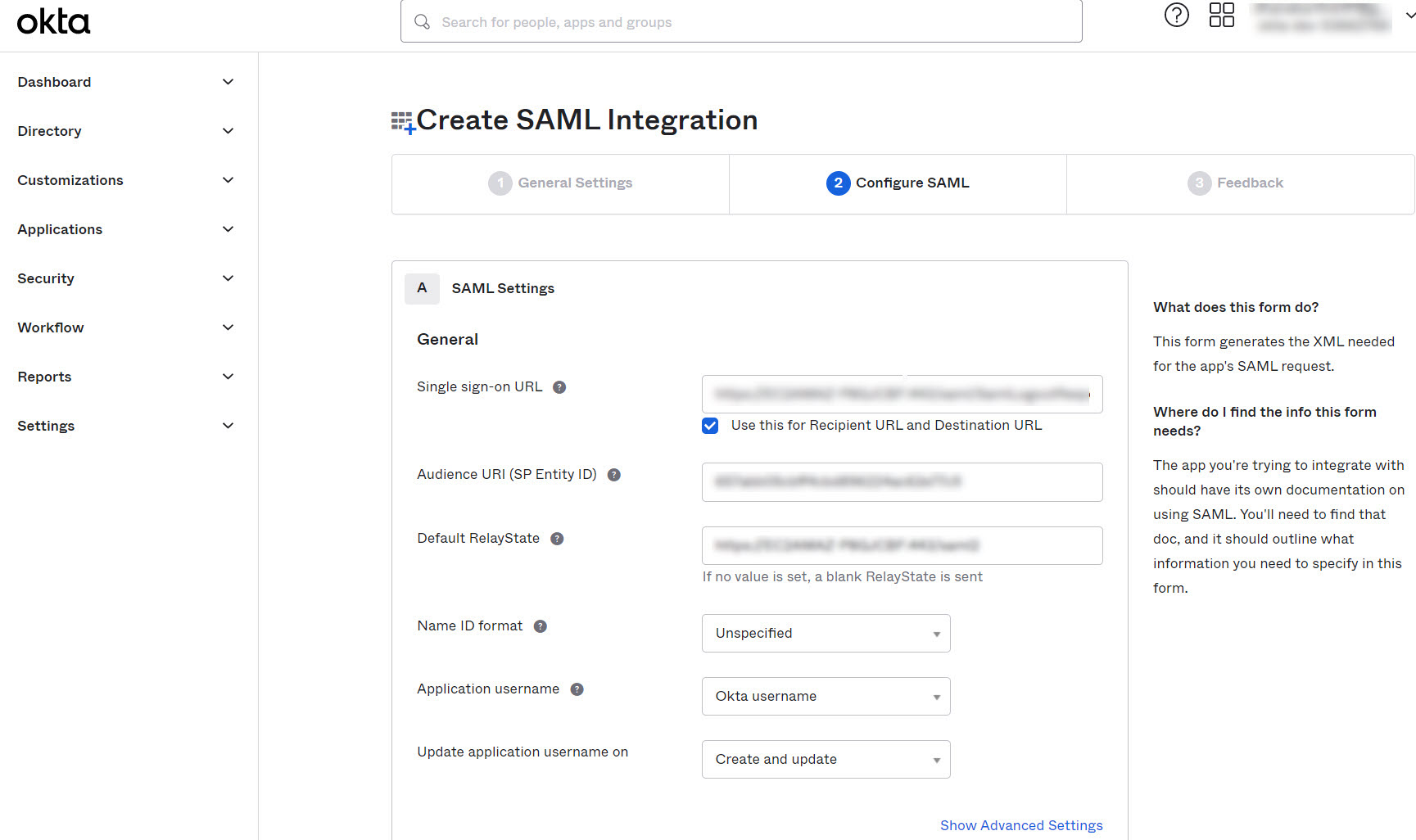
- For Client Organizations, enter Single Sign On URL from Password Manager Pro in the field next to Single sign on URL.
- Deselect the checkbox Use this for Recipient URL and Destination URL and mention the Assertion Consumer URL from Password Manager Pro in the fields next to Recipient URL and Destination URL.
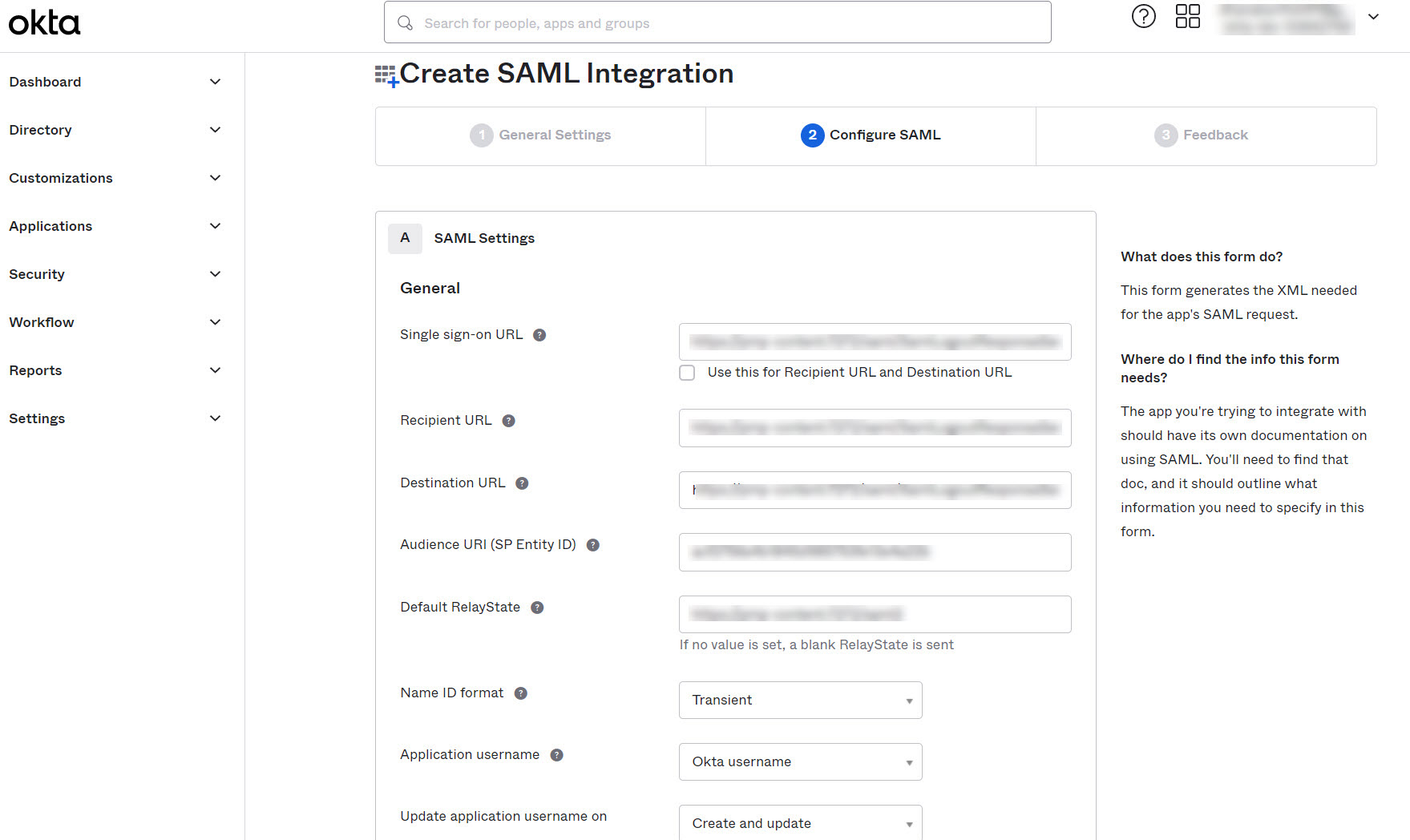
- Mention the Entity Id from Password Manager Pro in the field next to Audience URI (SP Entity ID).
- After filling-in the Single Sign On URL and Audience URI (SP Entity ID) fields, you need to specify how you want Okta to recognize the names of your users in Password Manager Pro. Since the way in which the usernames are displayed in Okta is different from how they are depicted in Password Manager Pro, you have to specify the format. There are two scenarios here:
- Scenario 1: If you have imported users from AD into Password Manager Pro, they would have been imported in the format Domain\Username. For more help on integrating Okta with your on-premise AD, please check the help documentation of Okta available here. In Okta GUI, you need to choose the option Custom from the dropdown Name ID format. Then, you should specify the custom format as given below:
- Scenario 2: If you have not used AD integration in Password Manager Pro, you should select the option Okta Username Prefix. This is because in Okta, user profiling is done in the format username@domain.com. But, in Password Manager Pro, user names are depicted only as usernames.
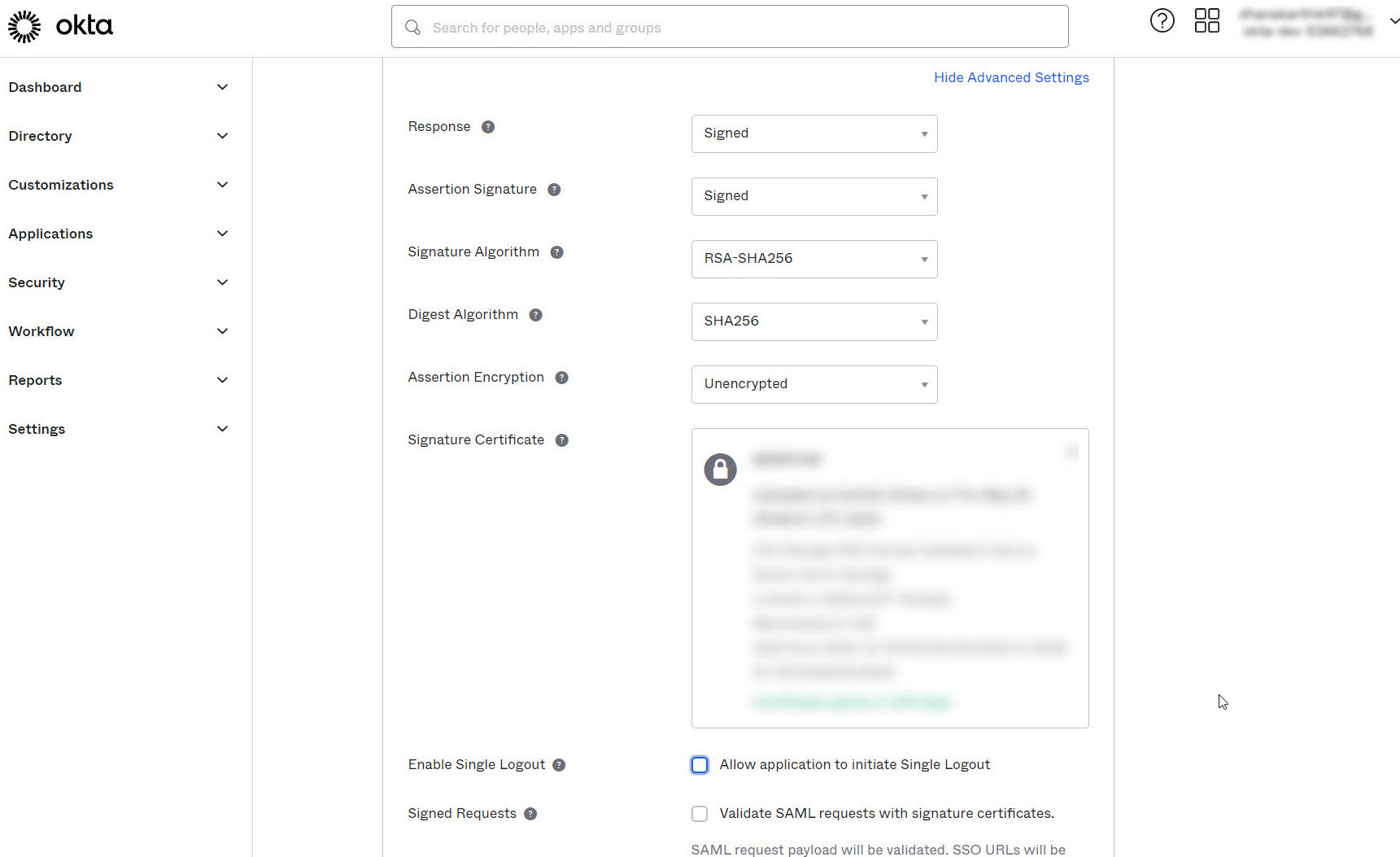
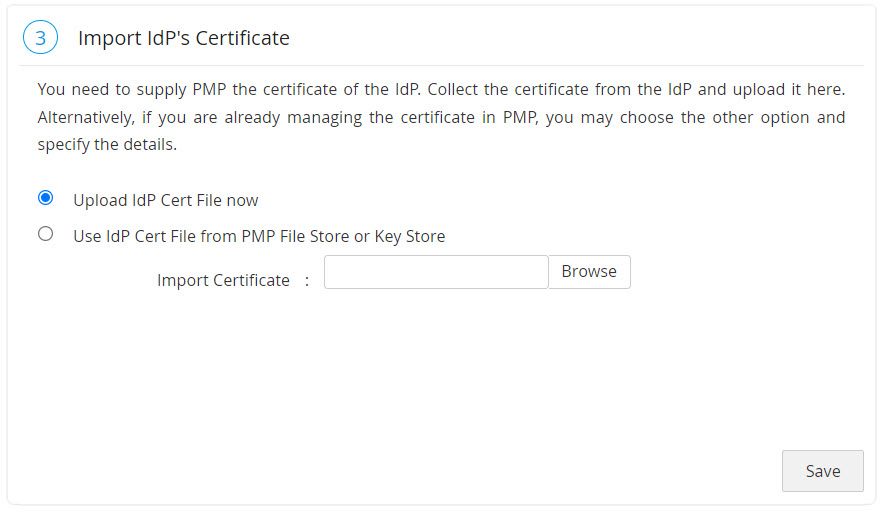
- To configure SAML Single Logout, click on Show Advanced Settings.
- Click the Browse files button next to Signature Certificate to upload the Password Manager Pro certificate.
- Select the checkbox Allow application to initiate Single Logout next to Enable Single Logout.
- Mention the Single Logout Service URL (copied from Password Manager Pro) in the field next to Single Logout URL.
- Enter the Entity Id (copied from Password Manager Pro) in the box next to SP issuer. Click Next.
- SAML Single Logout is applicable from build 12100 and above only.
- To download Password Manager Pro certificate, navigate to Admin >> Authentication >> SAML Single Sign-On (Step 1) and Download SP Certificate File.
Notes:
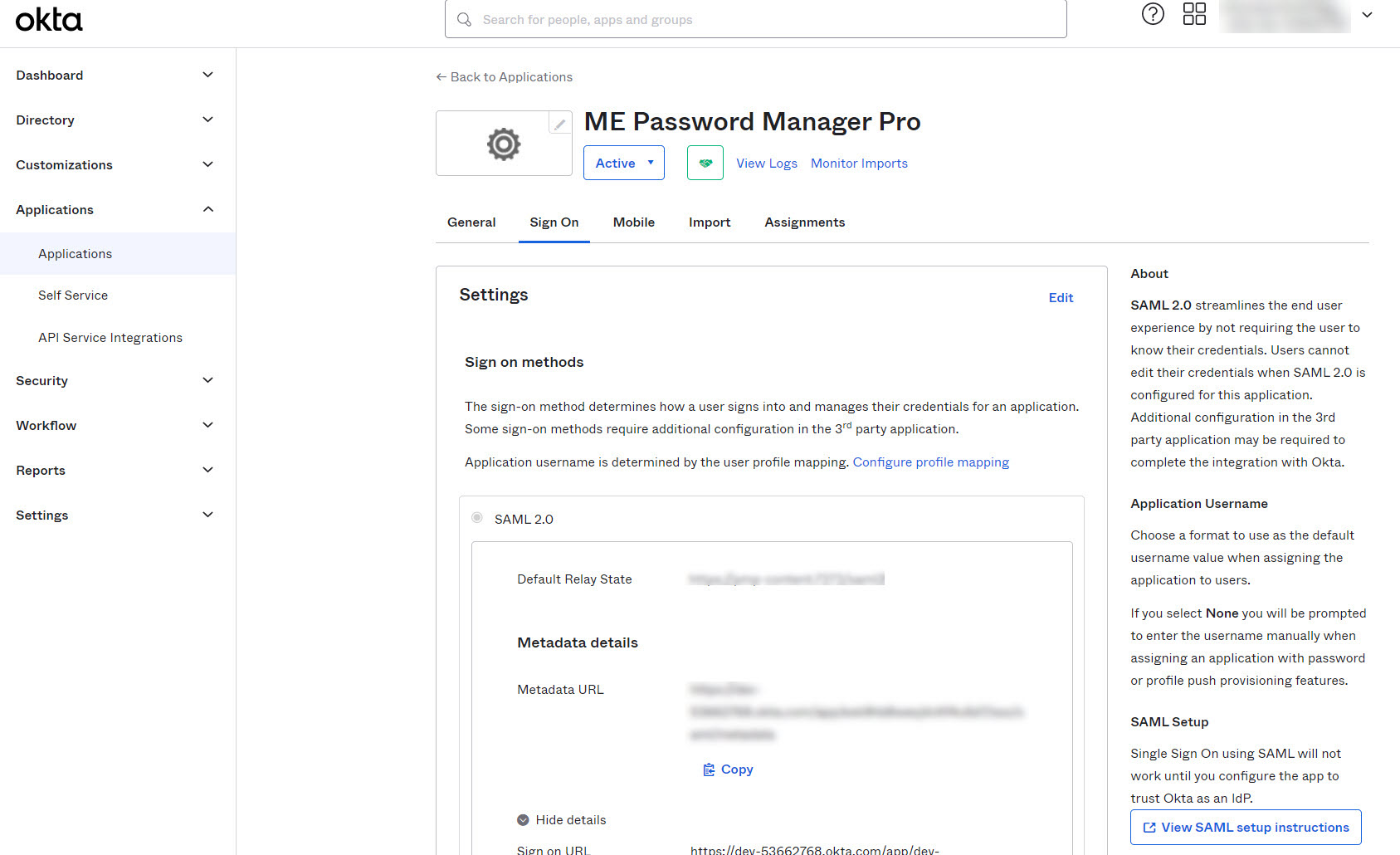
- In the Feedback tab, select an option to confirm how you have configured the application and click Finish. Now, the application details will be displayed as shown in the image below. In the right-side pane, click View SAML setup instructions. A new tab will open containing the details required to configure SAML 2.0 in Password Manager Pro, which is discussed in the next step.
Note:
For SAML SSO authentication, the Assertion Consumer URL is the hostname of the server, by default. To update the Assertion URL, follow the below steps:
Now, the Assertion Consumer URL under Service Provider Details will be updated.
toUpperCase(substringBefore( substringAfter(user.email, "@"), ".")) + "\" + substringBefore( user.email, "@")
This step is crucial because, only if you specify the correct Name ID format in Okta, you will be able to assign the application (Password Manager Pro) to other users in Okta.
2. Configuring Okta details in Password Manager Pro
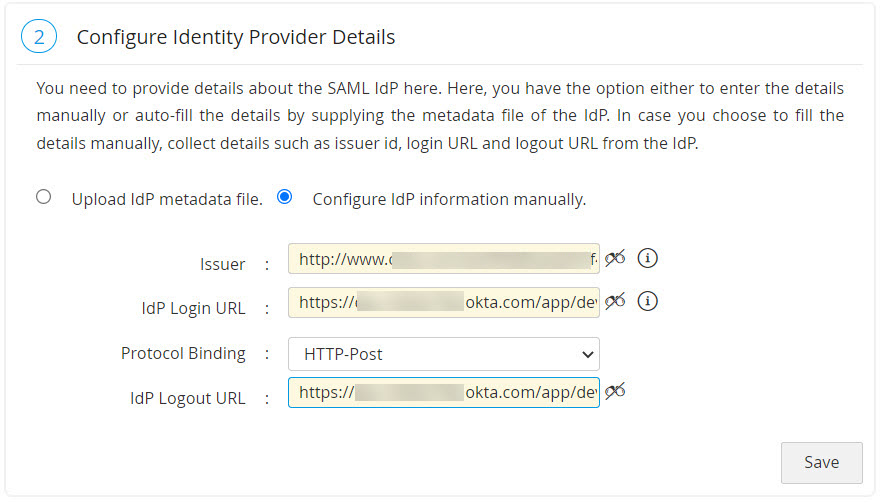
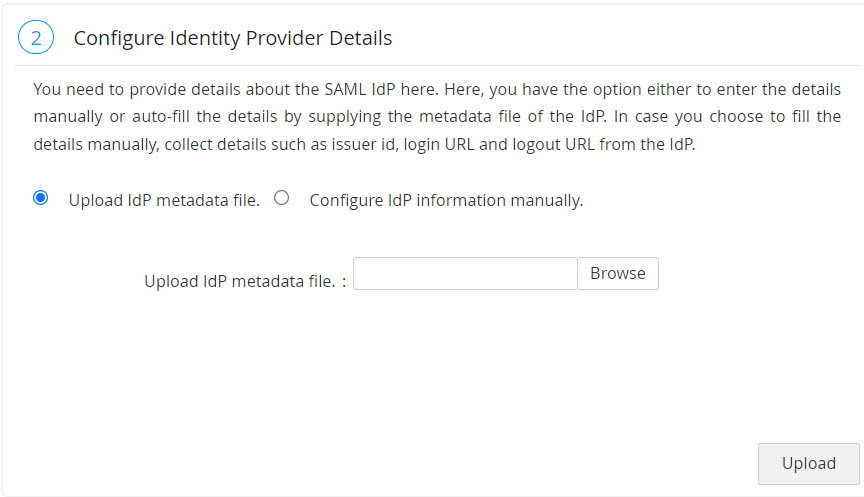
You need to configure IdP details in Password Manager Pro. This is done as part of the second step, Configure Identity Provider Details in Password Manager Pro's SAML Single Sign-On page. Here, you have the option either to enter the details manually or auto-fill the same by supplying the metadata file from the IdP.
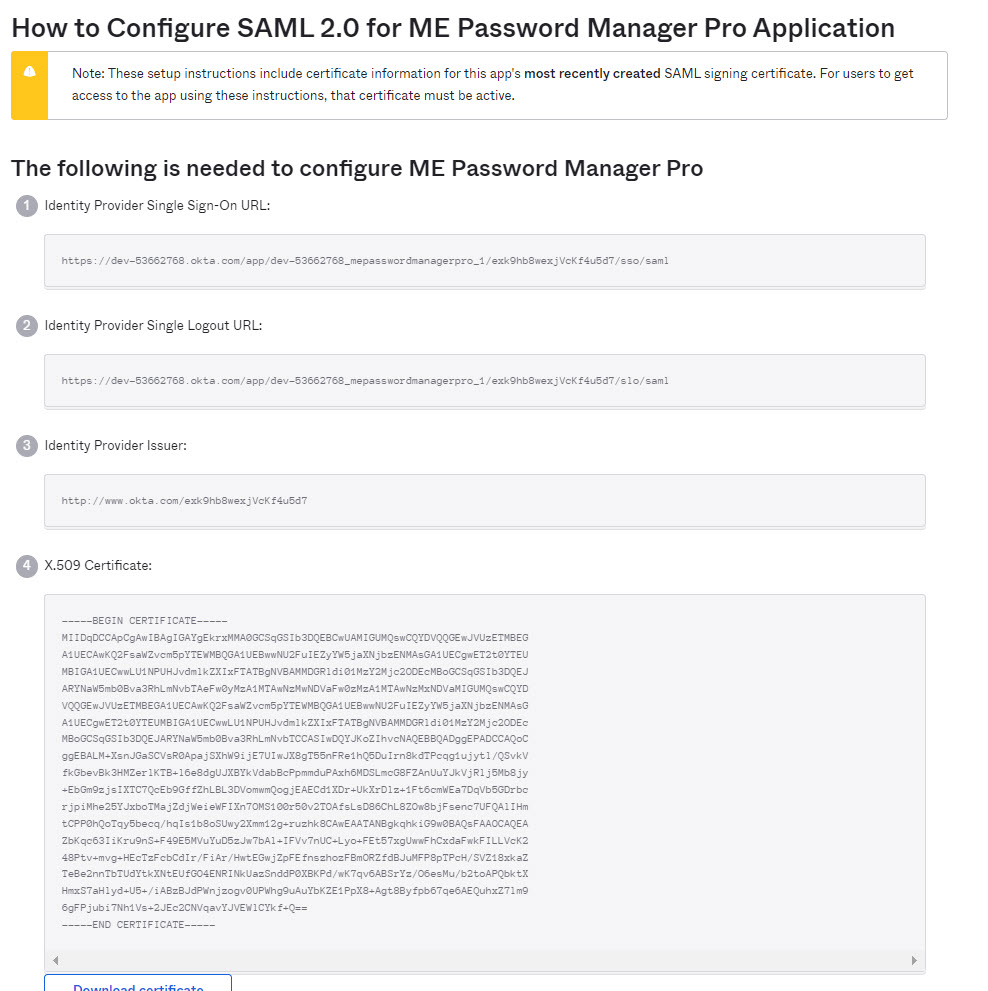
- Manual Set-up: If you choose to fill the details manually, get the IdP details such as Issuer ID, Login URL, and Logout URL from the Setup Instructions page of Okta. Configure the same in the step 2 given in Password Manager Pro SAML Sign On configuration page. Enter the details in the corresponding fields and also download the Okta certificate and upload onto the Password Manager Pro client (Listed as the 3rd step in the Password Manager Pro GUI). Alternatively, you can save the certificate file in the Password Manager Pro File Store or Key Store and then use it here.
- Auto-Filling with IdP Metadata File: Scroll down a little bit on the SAML 2.0 setup instructions page of Okta to find the IdP metadata from the section Optional. Copy the text and save it in a file with .xml extension. Now, upload the same .xml file onto the Password Manager Pro client. In this case, you needn't import IdP certificate in Password Manager Pro. It will be updated automatically.
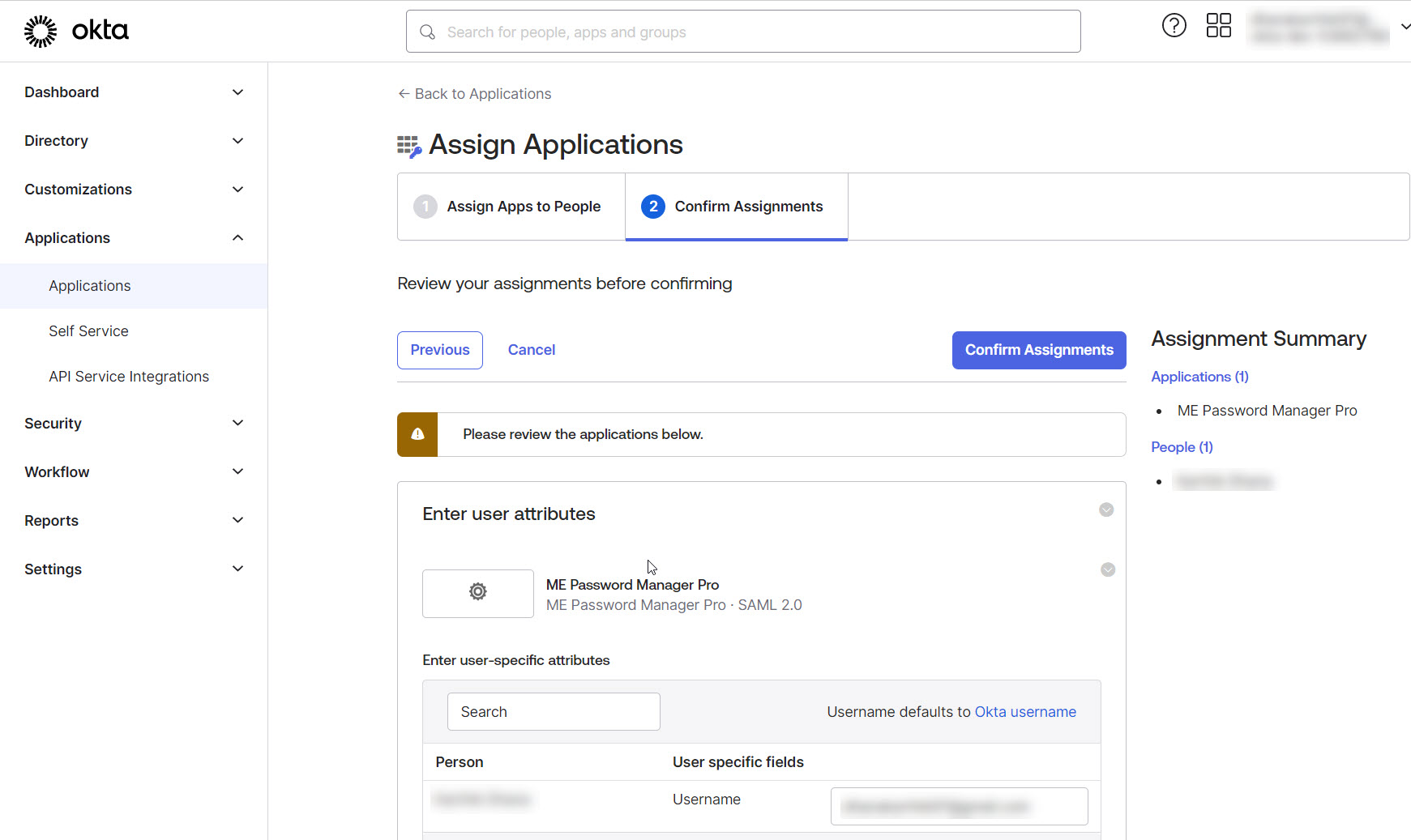
3. Assigning Application to Users in Okta
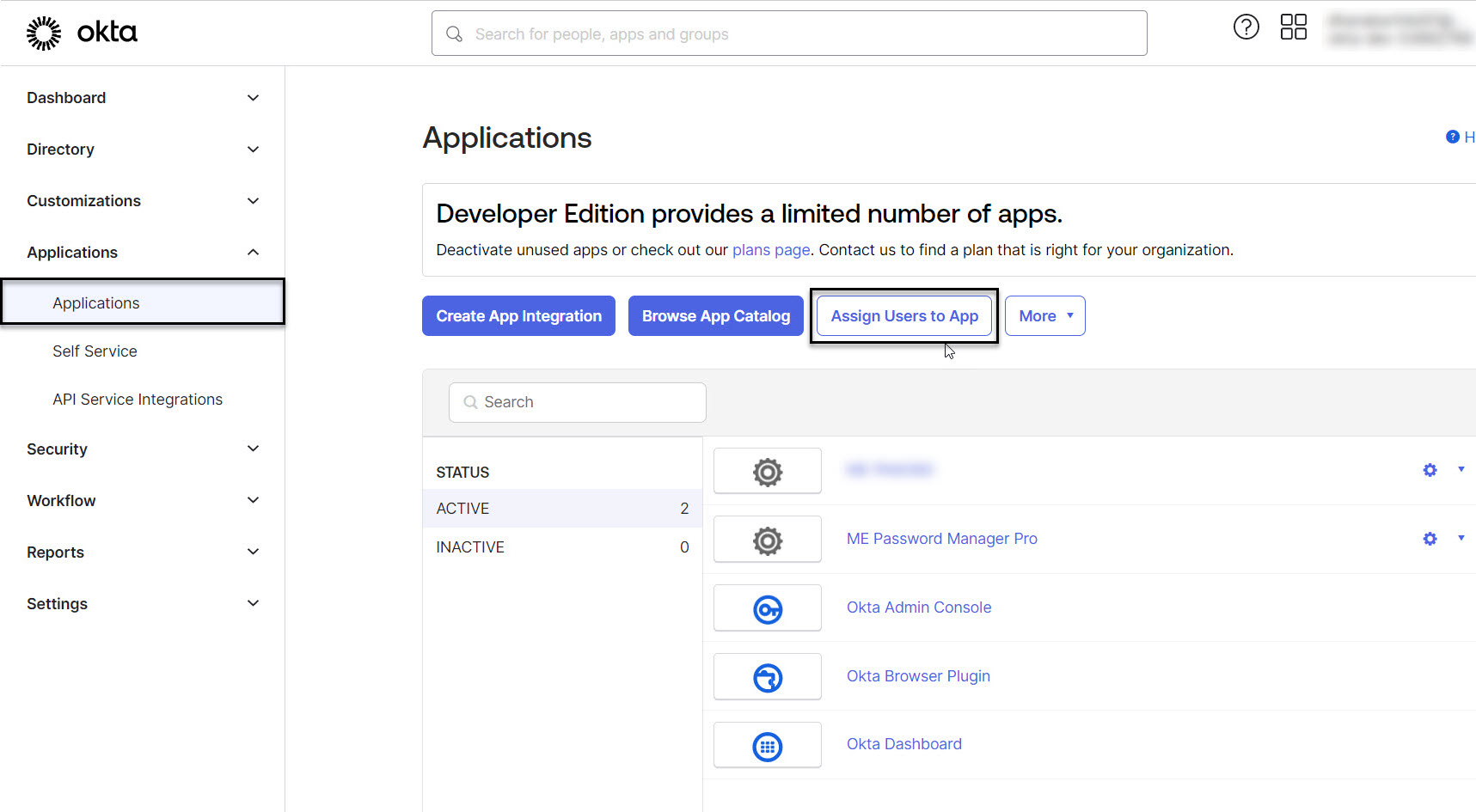
After completing the configurations in Password Manager Pro, return to the Okta portal to assign the newly added application to your users. To do so:
- Click the Applications tab from the left-side panel and select Assign Users to App.
- In the Assign Apps to People tab, select ME Password Manager Pro from the Applications section and pick the desired user name from the People section.
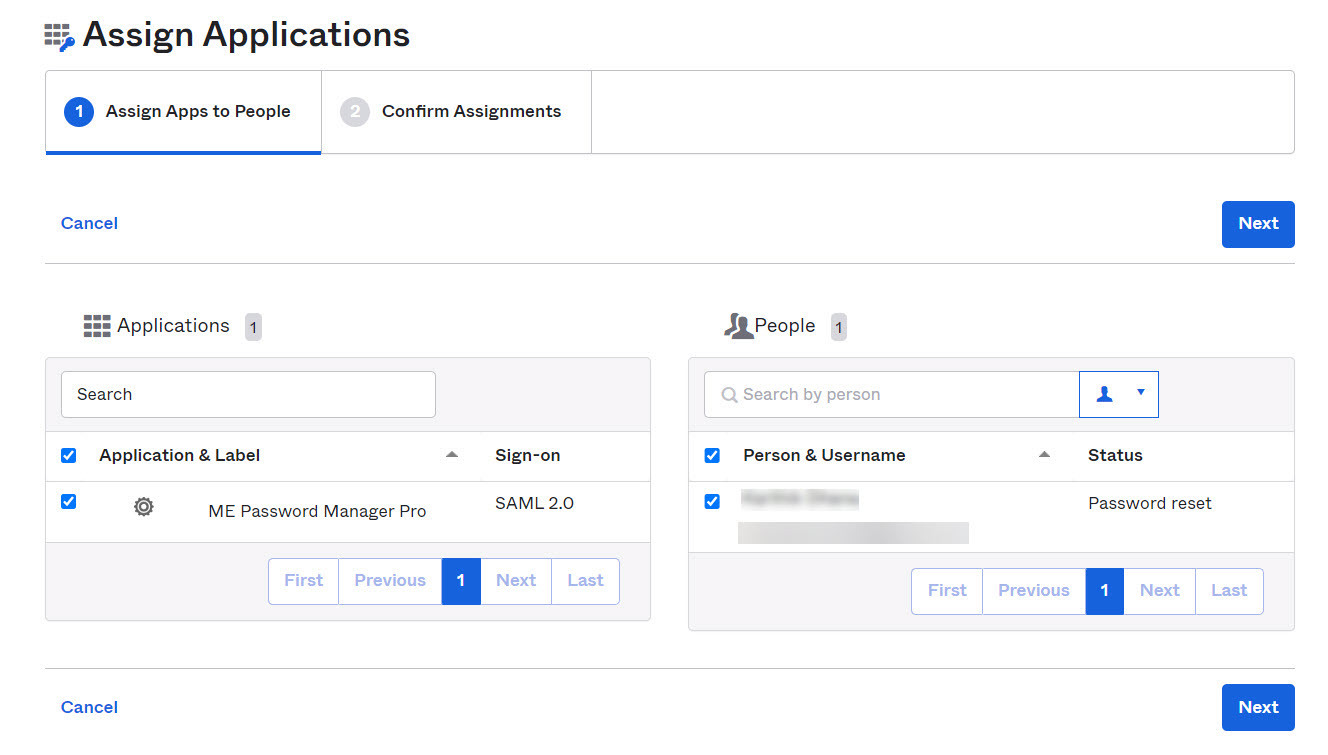
- Click Next. Review the applications and click the Confirm Assignments button.
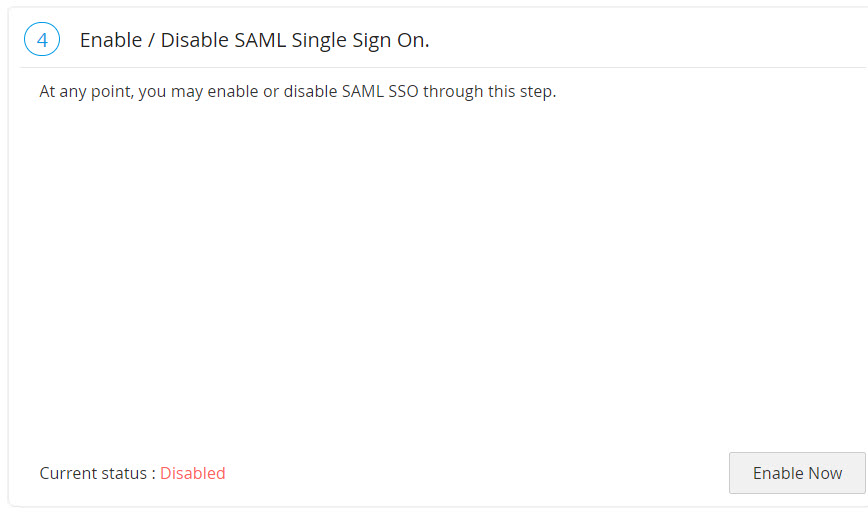
4. Enabling SAML Sign On in Password Manager Pro
The final step of this configuration is enabling SAML Single Sign On in Password Manager Pro. This would be shown as the 4th step in the SAML page in Password Manager Pro GUI. Click Enable Now shown at the bottom right to begin using this feature.
Note: It is not possible to configure SAML SSO in Password Manager Pro logins enabled with AD authentication. To disable AD authentication, go to Admin >> Active Directory.