Log360 is a unified SIEM solution with integrated DLP and CASB capabilities that detects, prioritizes, investigates, and responds to security threats. It combines threat intelligence, machine learning-based anomaly detection, and rule-based attack detection techniques to detect sophisticated attacks, and offers an incident management console for effectively remediating detected threats. Log360 provides holistic security visibility across on-premises, cloud, and hybrid networks with its intuitive and advanced security analytics and monitoring capabilities.
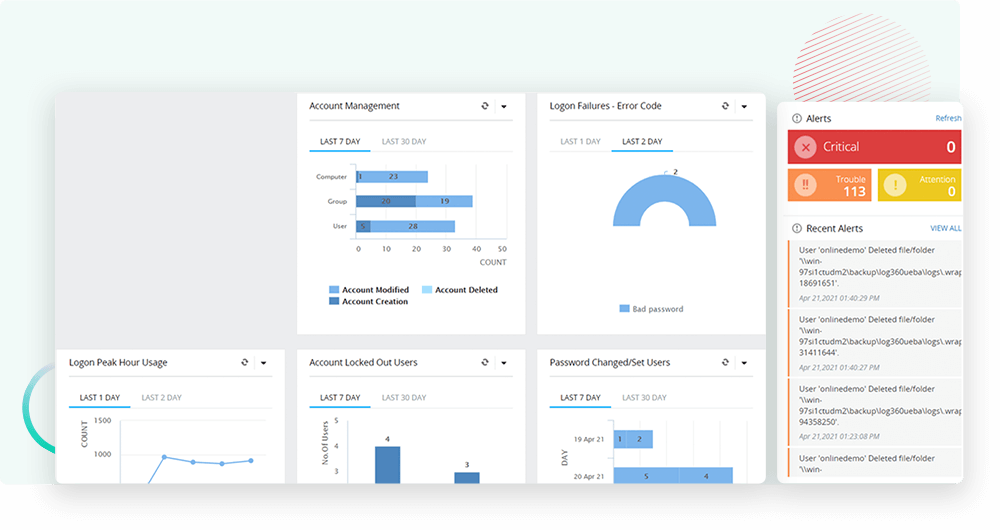
Monitor and audit critical Active Directory changes in real time. Utilize detailed information on AD objects, track suspicious user behavior, monitor critical changes in groups and OUs, and more to proactively mitigate security threats.
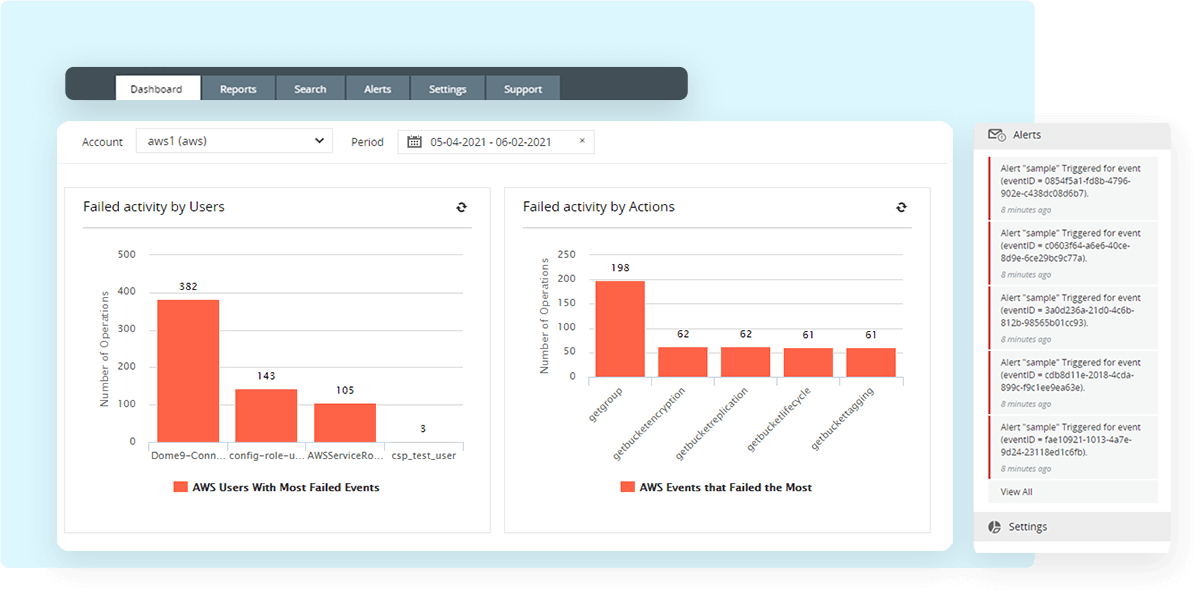
Gain visibility into your AWS, Azure, Salesforce, and Google Cloud Platform cloud infrastructures. Ensure cloud data security by monitoring changes to your users, network security groups, virtual private cloud (VPC), permission changes, and more that occur in your cloud environment in real time.
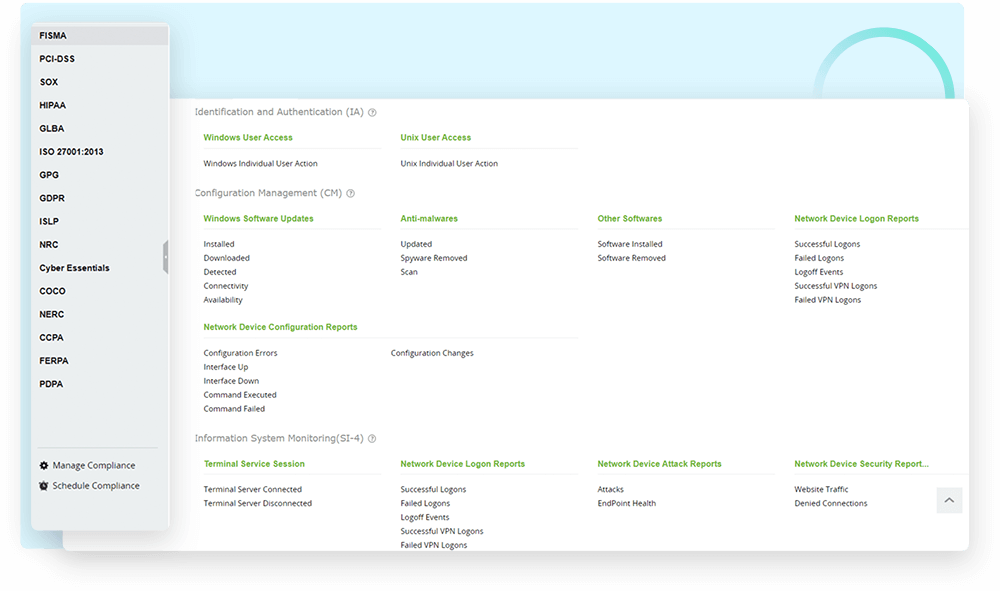
Comply with various regulatory mandates such as HIPAA for healthcare, PCI DSS, and GLBA for finance, FISMA for US federal agencies, ISO 27001, SOX, and many more by using audit-ready report templates and compliance violation alerts.
Leverage Log360's TDIR engine, Vigil IQ, for powerful threat detection using real-time correlation, ML-driven UEBA, and MITRE ATT&CK threat modelling framework implementation, intuitive analytics, and SOAR capabilities.
Detect security incidents or data breaches that pose a challenge for your organization using:
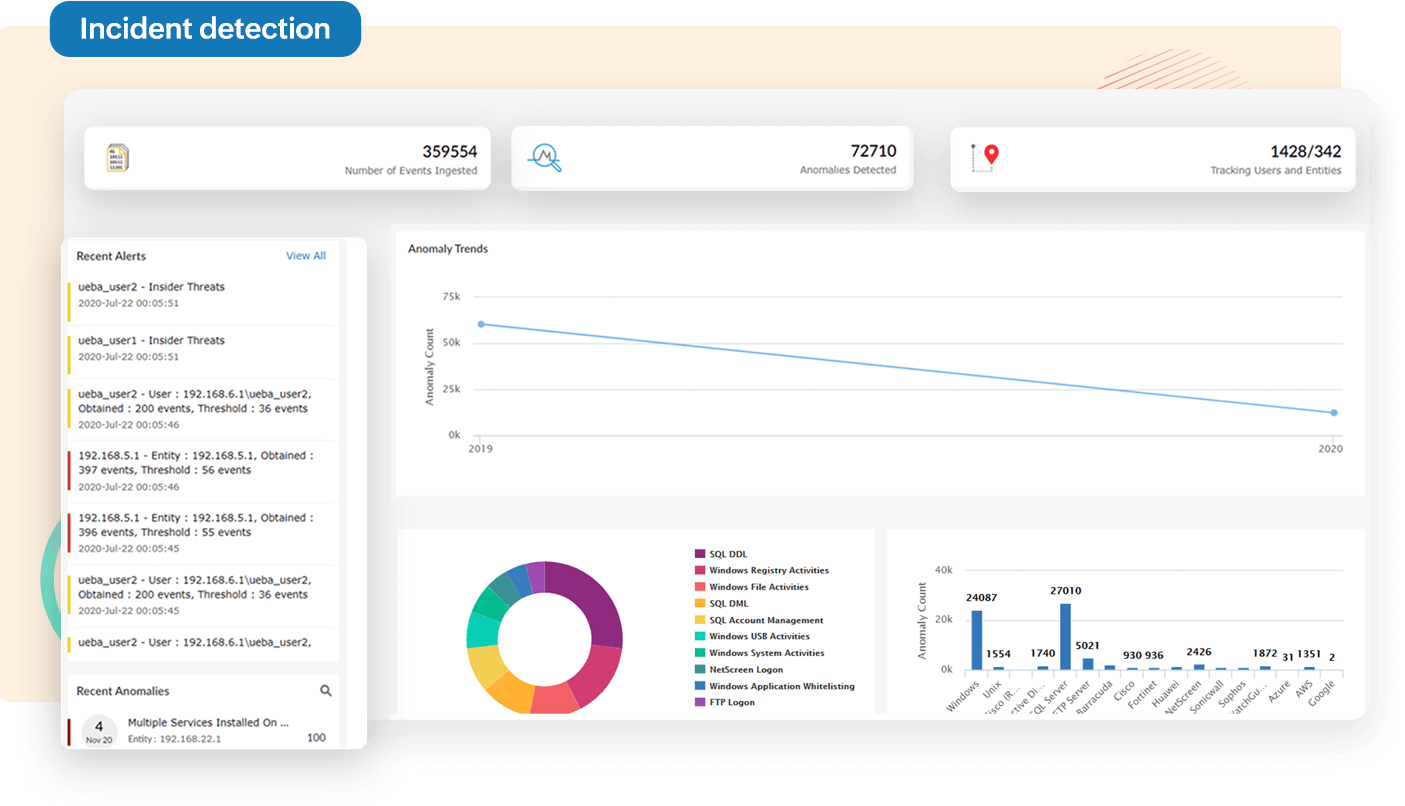
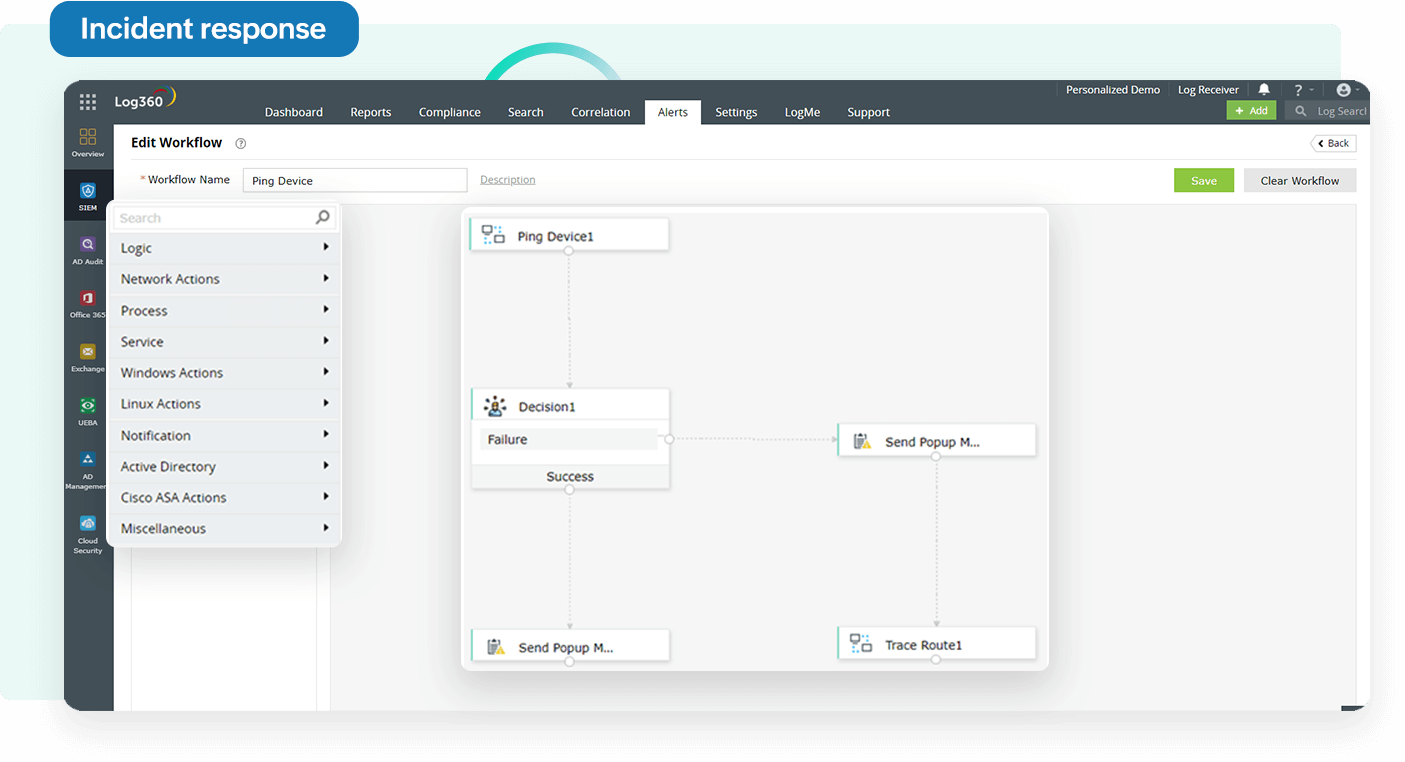
Respond to security threats quickly and effectively.
Cut the complexity of manual threat investigation; proactively hunt for threats with Log360's Incident Workbench, an exclusive console that unifies analytics of the exploit triad: users, processes, and external threat sources.
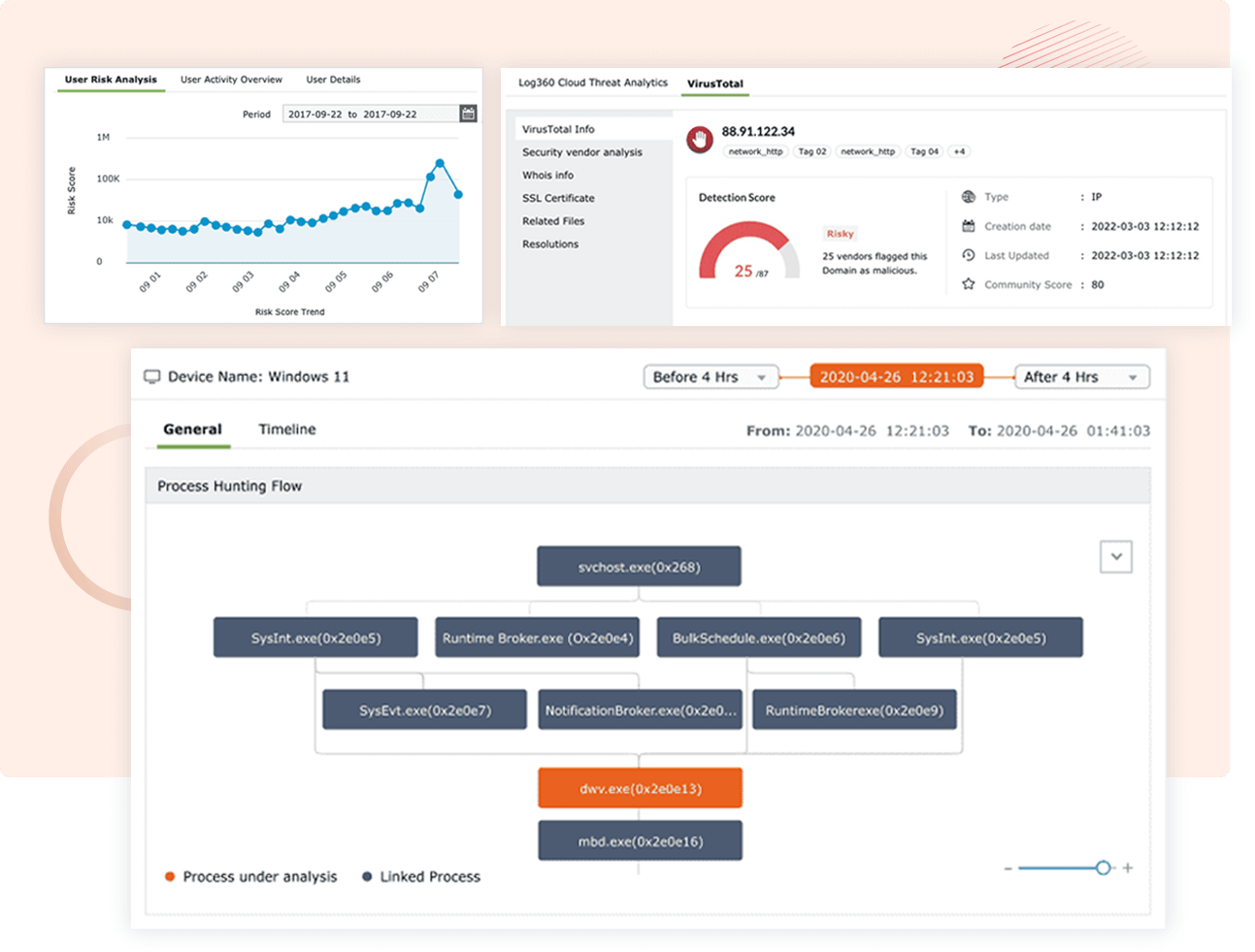
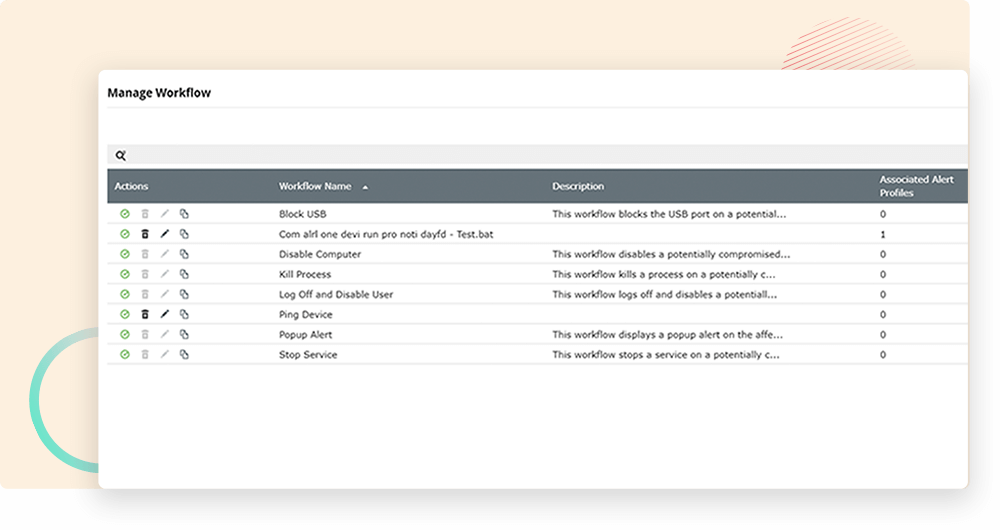
Compile all security data from different platforms such as Exchange Server, Microsoft 365, IaaS, PaaS, SaaS, on-premises network devices, servers, applications, and more in a single console. Expedite threat resolution by automating your response to detected incidents using workflow options.
Uncover security threats accurately with Log360's various techniques such as event log correlation, threat feed analysis to identify malicious IPs and URLs, and machine learning combined with user behavior analysis to identify insider threats.
Mitigate security threats effectively by automating your incident response and creating incident workflows that sync with alerts. Speed up threat mitigation by integrating the process with ITIL solutions to ensure accountability for incident resolution.
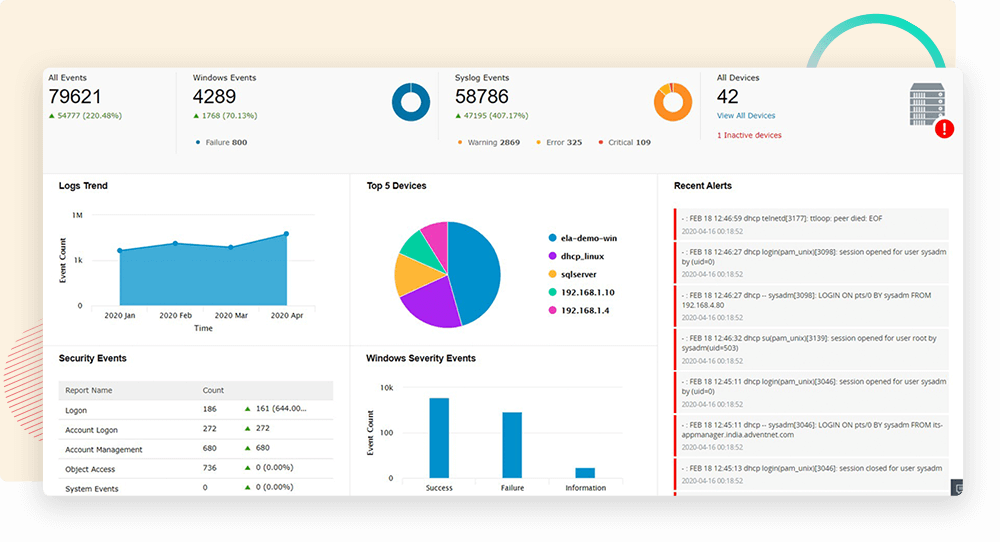
Monitor all security events compiled from your Windows and Linux/Unix machines; IIS and Apache web servers; SQL and Oracle databases; and perimeter security devices such as routers, switches, firewalls, intrusion detection systems, and intrusion prevention systems in real time through interactive dashboards, out-of-the-box reports, and graphs.
Monitor and analyze your log data for security breaches, and meet regulatory compliance requirements with compliance reports for PCI DSS, FISMA, GLBA, SOX, HIPAA, ISO 27001, and more.
Find malicious actors and potential hidden attacks that have slipped through your initial security defenses by leveraging insights into attackers’ tactics, techniques, and procedures (TTP) and advanced threat analytics.
Log360 has made my job a cinch. The real-time reports and alerts make sure I don't have to spend a lot of time worrying about threats
Log360 helps us integrate the components and store logs in one location. We needed a solution to stay compliant and also get to know the threats to our environment and Log360 seems to be the right fit. Since the evaluation of purchase we always find new features that we have found more likeness to it.
Log360 is a complete solution for all of the needs in events auditing! Subcomponents like EventLog Analyzer and ADAuditPlus are really helpful during reviews and audits.
Log360 provides basic login and login failed attempts data in a centralized platform. The solution is good for auditing purposes & for compliance reasons. Works across multiple systems & platforms.