Vigil IQ is the advanced TDIR engine within Log360 that helps enterprises identify, navigate, and investigate potential threats, this solution enables proactive and effective responses to mitigate security risks.
With the high coverage to key security threats, intuitive analytics, and automated playbooks, Vigil IQ helps enterprises overcome their complex cybersecurity challenges—by enhancing mean time to detect (MTTD) and respond (MTTR), extended investigation of false positives, detecting low priority or non-real threats, and managing manual mitigation.
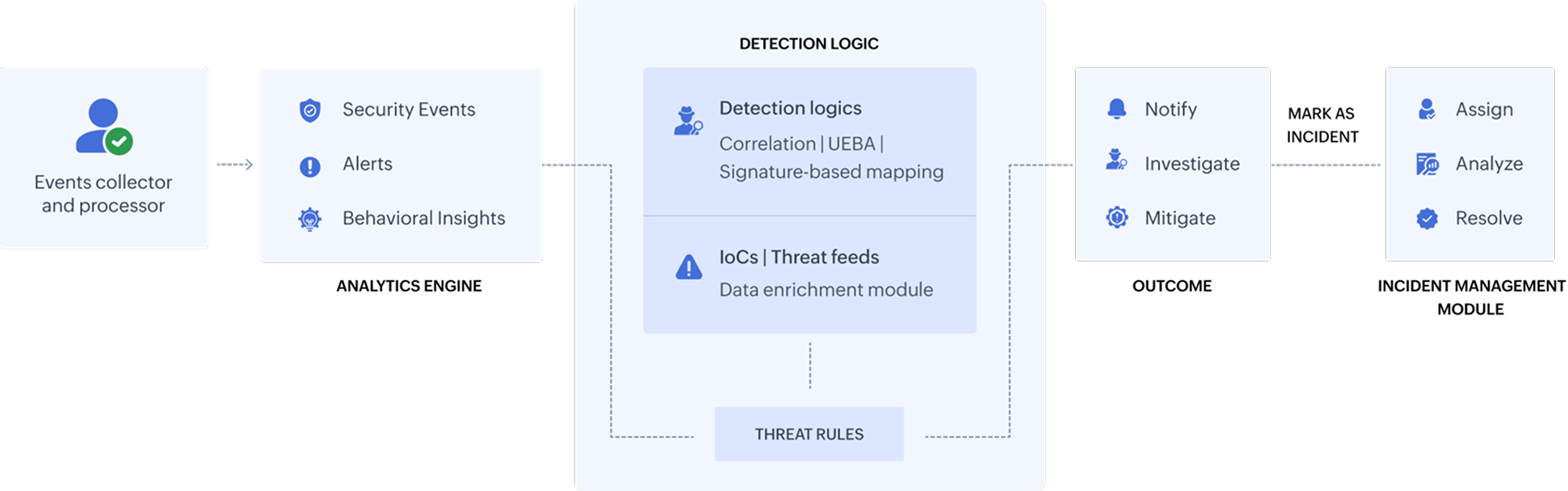
Log360's collects, processes, and analyzes log and event data utilizing its Analytics Engine (AE) which then classifies the information as notable security events, alerts, and behavioral insights for enhanced visibility and auditing. The data from the analytics engine is then passed on to Vigil IQ.
Vigil IQ uses different detection logic, and data enrichments such as threat feeds and IoCs to form threat rules that are applied in the correlation engine, UEBA module, and MITRE ATT&CK framework adoption system to identify potential risks and threats.
Vigil IQ's security analytics component then provides the ability to triage and investigate the detected security threats. Automated and pre-packaged playbooks can then be executed over the detected threat or incident to remediate the attack.
What makes Vigil IQ an impactful TDIR engine?
-
Contextual
Log360 scans the deep and dark web continuously for leaked credentials associated with organizations, their employees, and third-party vendors. This ensures that you are alerted about potential security risks before potential damage.
-
Guided investigation with the Incident Workbench
Vigil IQ's investigation module has an exclusive inspection console that facilitates contextual assessment and unification of the exploit triad: users, devices, and processes. Along with this, external threat sources can also be analyzed for reputation scores.
-
Balance
Vigil IQ brings a right balance in adoption of proactive and reactive security approaches. It ensures equilibrium by blending the methodologies and techniques required to detect threats and risks. The investigation and remediation platform comes with prepackaged actionable insights for threat neutralization, risk mitigation, and impact analysis.
-
Prepackaged cases
Vigil IQ comes with prepackaged correlation rules and anomaly cards that helps detect known security threats. The solution's incident management system granularly associates automated workflows for the threat rules to neutralize threats instantly.
-
Accuracy and precision
Vigil IQ encompasses in itself a dual-layered threat detection system that includes smart threshold setting, dynamic learning, high coverage to spot threats accurately, and precise threat detection for improved reliability.
-
High coverage
Constantly updated indicators of compromises (IoCs) in the Advanced Threat Analytics platform, behavioral analytics, granular rule-based correlation system, Vigil IQ can spot external threats with common attack vectors, insider attacks, identity-based attacks, ransomware, and more.
-
Performance tracking
Vigil IQ delivers the right balance of proactive and reactive security approaches.