Log360 SIEM
for enterprise security
Get a 360-degree view into your enterprise network, detect sophisticated threats, and decrease
your risk exposure.
Thank you for downloading!
Your download should begin automatically in 15 seconds. If not, click here to download manually.
Start your 30-day free trial
- Benefits
- Capabilities
- Awards
- Customer Testimonials
- Why choose Log360
- Resources
What can enterprises achieve with Log360?
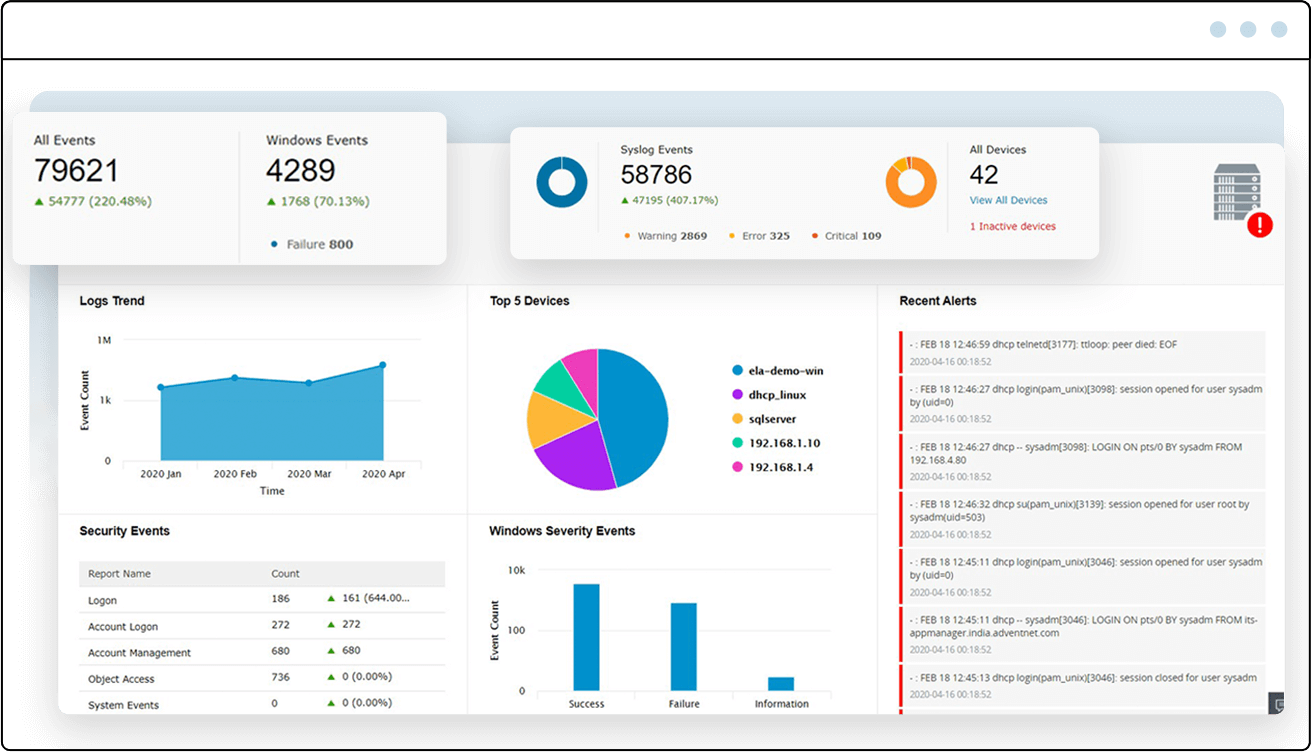
Get complete visibility into your enterprise network
Is it hard to keep track of all the activities within your cloud and on-premises environments? Are you afraid a potential threat might slip through your defenses?
Gain comprehensive visibility from a single console, no matter the number of users and devices on your network. Log360 collects, analyzes, correlates, and archives logs from more than 700 log sources, including endpoints, databases, security tools, applications, and cloud sources like AWS and Azure.
Detect and mitigate sophisticated threats in your enterprise network
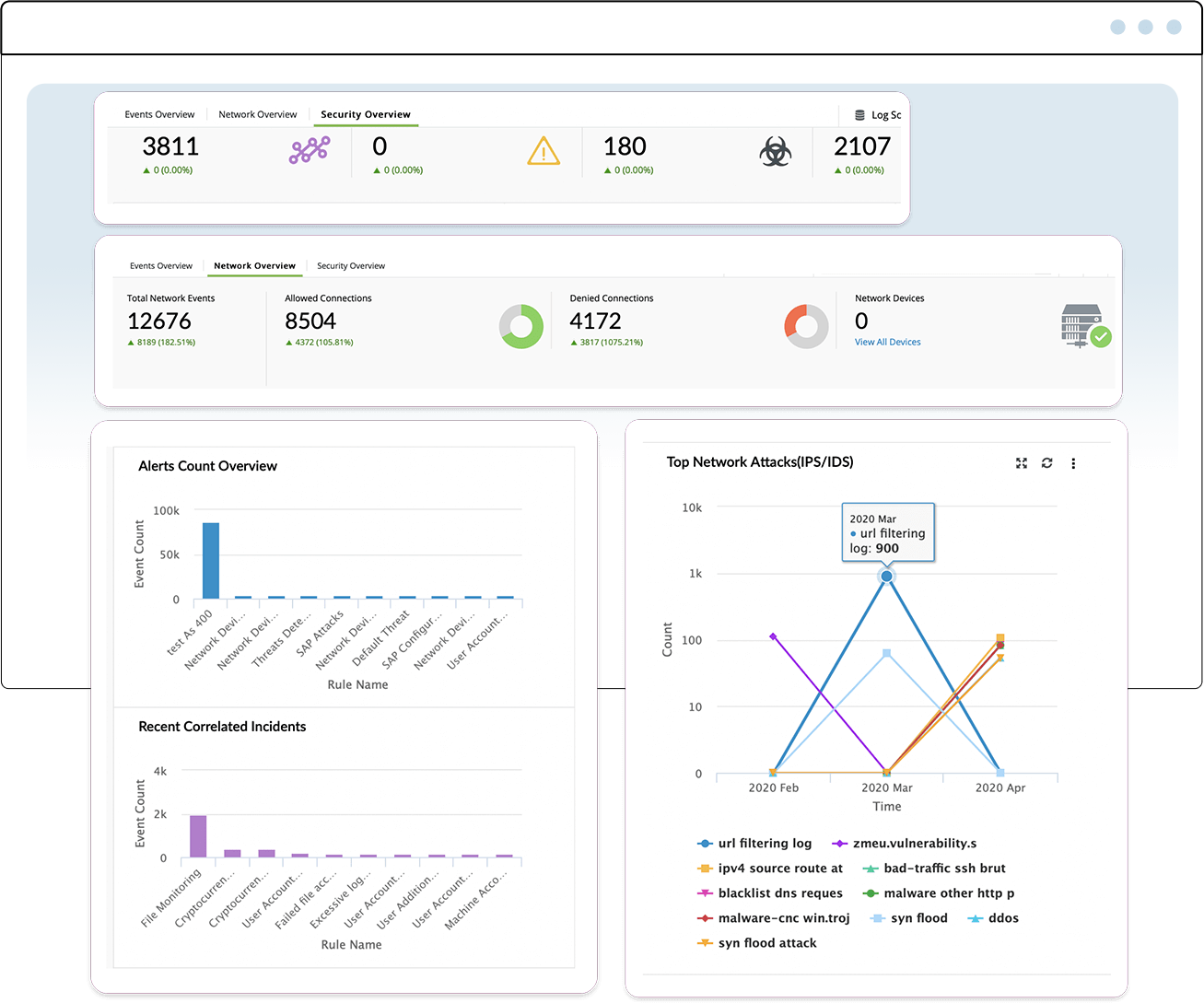
Security analysts at enterprises need to reduce the mean time to detect (MTTD), and the mean time to respond (MTTR) to threats.
Log360 comes with numerous built-in correlation rules to protect against threats. New correlation rules are added every month to protect against an expanding attack surface. By integrating with popular threat intelligence feeds, Log360 can also block malicious domains, IPs, and URLs, while enabling threat hunting.
Security analysts and detection engineers can also use the ML-powered Smart Threshold feature to improve threat detection further. Here, Log360 will automatically recommend the thresholds you need to program into detection rules. This will make threat detection more accurate and decrease false positives.
Minimize risk exposure and maximize security
The CISO of any enterprise is tasked with reducing risk. This is also becoming a key success metric of security managers.
Log360 can offer your enterprise frontline defense to reduce risk exposure and improve security maturity. For example, you can leverage Log360's risk posture analysis to see the level of risk your Active Directory is exposed to. Additionally, with insights into compliance with regulations like the PCI DSS, HIPAA, FISMA, and the GDPR, Log360 helps your enterprise adhere to various industry mandates.
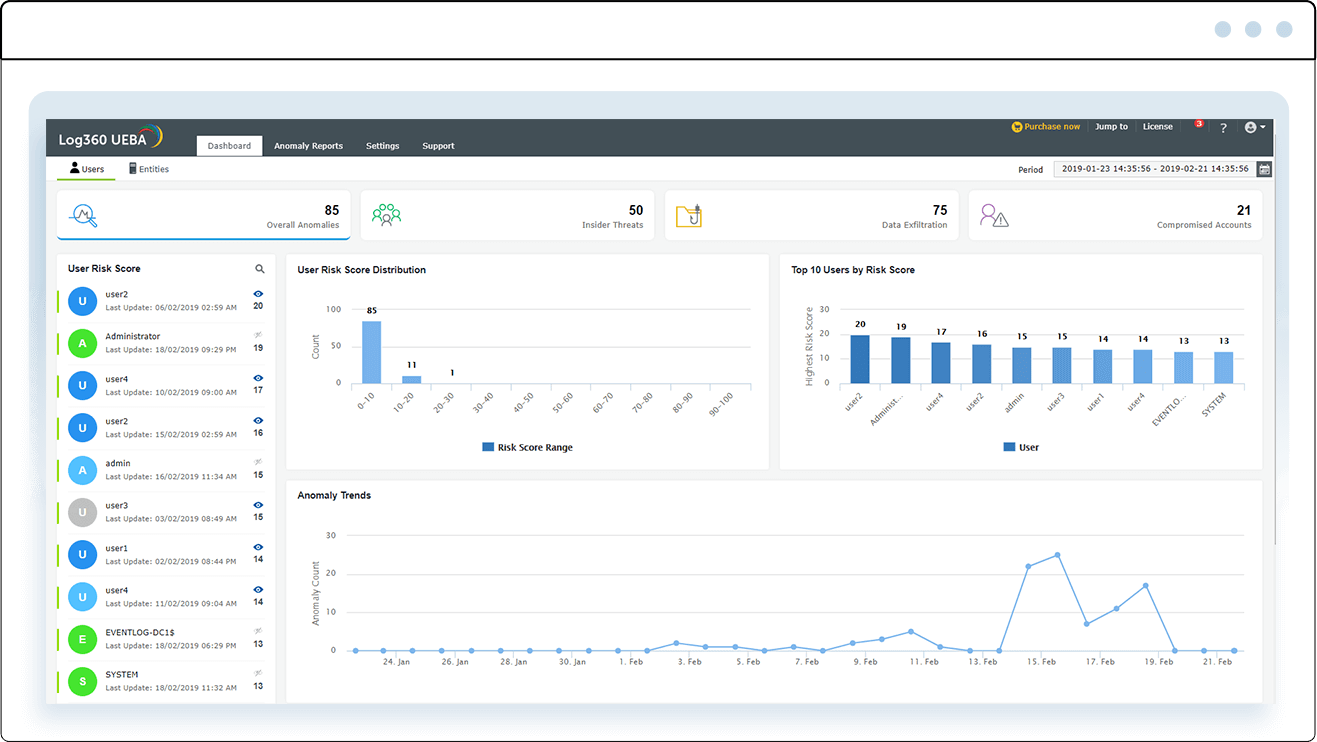
A standout feature of this enterprise SIEM solution is its strong risk identification techniques that keep you ahead of potential threats. Log360 also has a user and entity behavior analytics (UEBA) module that allows you to monitor anomalous activities by suspicious users and entities, assign risk scores, and receive real-time alerts about unusual activities, thereby reducing the dwell time of hidden attackers in your environment.
How Log360 caters to your enterprise security needs?
Businesses of any size require a robust security solution that can protect against attacks. Log360 is a comprehensive enterprise security incident and event management (SIEM) solution that monitors, detects, investigates, and responds to threats. The table below provides a holistic view of all the powerful features offered by Log360 to fulfill these capabilities.
| Capability | Supporting features of Log360 |
|---|---|
| Monitoring |
|
| Threat detection |
|
| Investigation |
|
| Threat response |
|
| Incident resolution and management |
|
Detect, investigate, and respond to threats
while meeting compliance requirements with Log360.
DownloadAwards and recognitions
We strive for excellence to provide your organization with the best security. Our commitment to innovate constantly and ensure customer satisfaction has earned us some awards and recognitions. Here are a few of the accolades from 2023-2024.
| Firm | ||||
|---|---|---|---|---|
| Recognitions |
Niche Player in the 2024 Gartner Magic Quadrant for Security Information and Event Management Custerms' Choice in the Peer Insights 'Voice of the Customer': Security Information and Event Management, 2023 |
Contender in Extended Detection and Response (XDR) in the ISG Provider Lens Cybersecurity - Solutions and Services, 2023 |
Challenger in KuppingerCole's Leadership Compass: Data Leakage Prevention, 2023 |
Challenger and Outperformer in the GigaOm Radar for Autonomous SOC, 2023 Challenger and Fast Mover in the GigaOm Radar for Security Management and Event Management, 2023 |
“The manageability of [Log360] and what was built in as opposed to the behemoth that is Splunk—I think that was probably the number one selling point.”
Cybersecurity operations senior technical lead
Concurrent Technologies Corporation
Pennsylvania, USA
"Using [Log360] freed up time we used to spend manually doing the work that is now automated in the reports."
IT operations manager
Eureka Casinos
Nevada, USA
“There's not a huge learning curve, it's searchable, and the way that it's built its framework is very simple to understand. Like, anytime that I run into technical problems, I'm able to parse through it and typically attempt to fix it myself before I need to get customer support involved.”
IT Security
Electroimpact
United States
5 reasons to choose Log360 for your enterprise
Here are five reasons why Log360 is the perfect security solution for your enterprise:
Leave no log unturned
You can collect, analyze, correlate, search, and archive log data from over 750 types of log sources with Log360. Even a simple password change will not go unmonitored. Do you have enterprise-specific IoT devices or homegrown applications? You can parse those logs with the custom log format feature.
Identify and mitigate threats automatically
Using advanced threat detection mechanisms, such as event correlation, threat feed analysis, and UEBA, Log360 provides in-depth insights, detects threats, and mitigates them before it affects your entire enterprise network.
Manage compliance
Regardless of your industry, Log360's preconfigured compliance reports help you meet various compliance mandates, including the PCI DSS, FISMA, GLBA, SOX, HIPAA, and ISO 27001. Log360 also makes it easier to prove compliance to IT auditors, ensuring your enterprise meets regulatory requirements efficiently.
Boost SOC team productivity with automation
Mean time to respond is a major KPI for any security operations center (SOC) because a shorter response time directly correlates with quicker containment and mitigation of security incidents. Enhancing team productivity is essential for reducing MTTR, and automation plays a pivotal role in achieving this.
Using Log360, you can automate threat detection and execute response workflows when alerts are raised so that the first-level response to an incident is taken before an administrator enters the scene. This offers around-the-clock protection for enterprises of all sizes to manage security operations efficiently.
Enhance Active Directory security
Log360 offers reports crucial for understanding potential risks in your Active Directory (AD) environment, such as group memberships and file permissions. This proactive approach ensures robust security across your enterprise network, while automated reporting saves valuable time and resources.
Our vision of the future
In the future, ManageEngine plans to evolve Log360 into a completely automated security solution that seamlessly integrates with machine learning algorithms and generative AI to enable unsupervised detection, response, and mitigation of threats.


