External threat detection
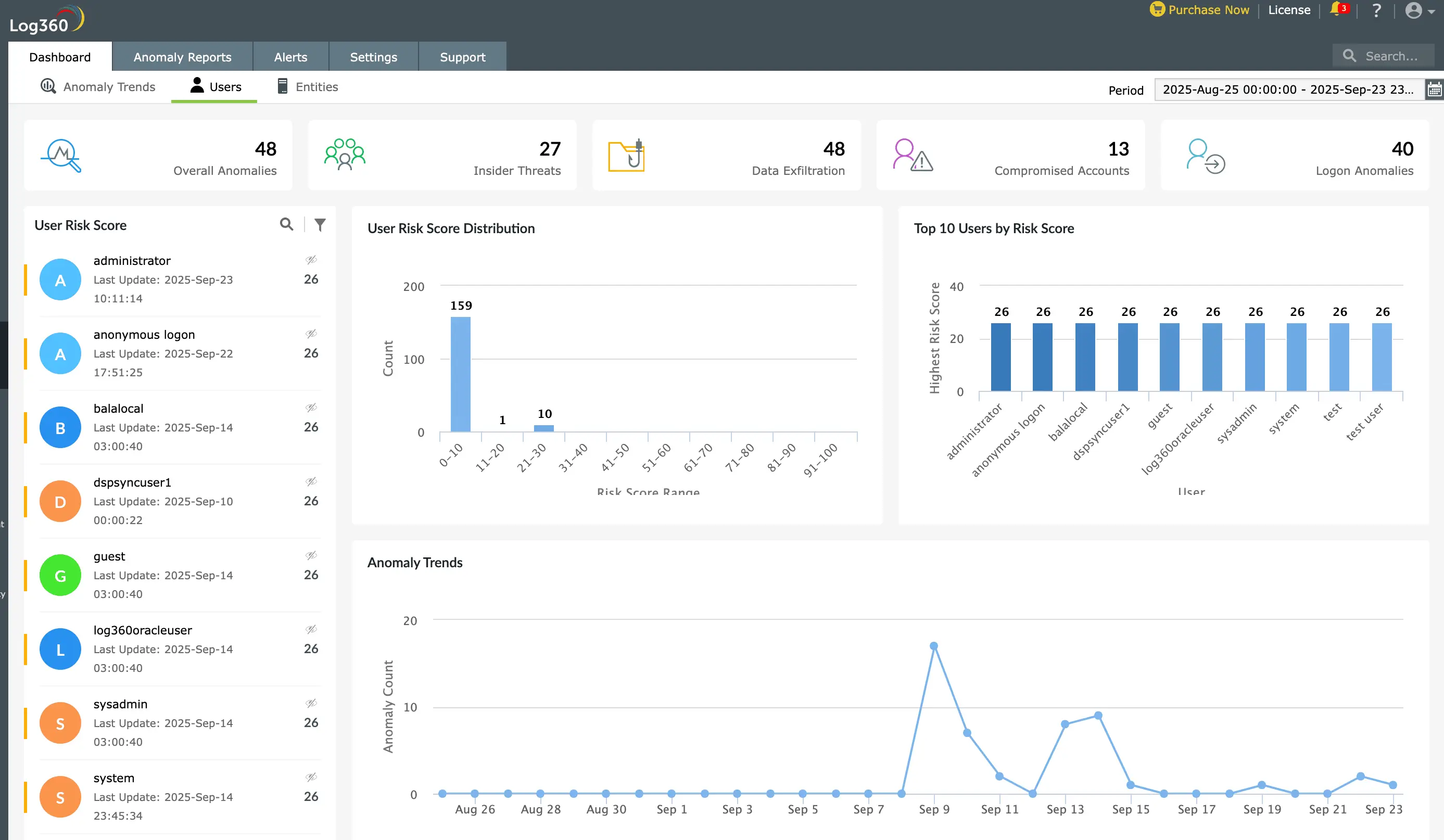
Identify and block external threats such as brute force attacks, phishing attempts, port scans, and reconnaissance activities targeting your network with Log360's real-time monitoring of authentication and network traffic.
Learn more
Real-time threat intelligence
Enhance threat detection by correlating your security data with real-time threat intelligence feeds such as Webroot and STIX/TAXII. This enrichment adds valuable context around malicious IP addresses, domains, and URLs, improving alert accuracy and investigation efficiency.
Learn more
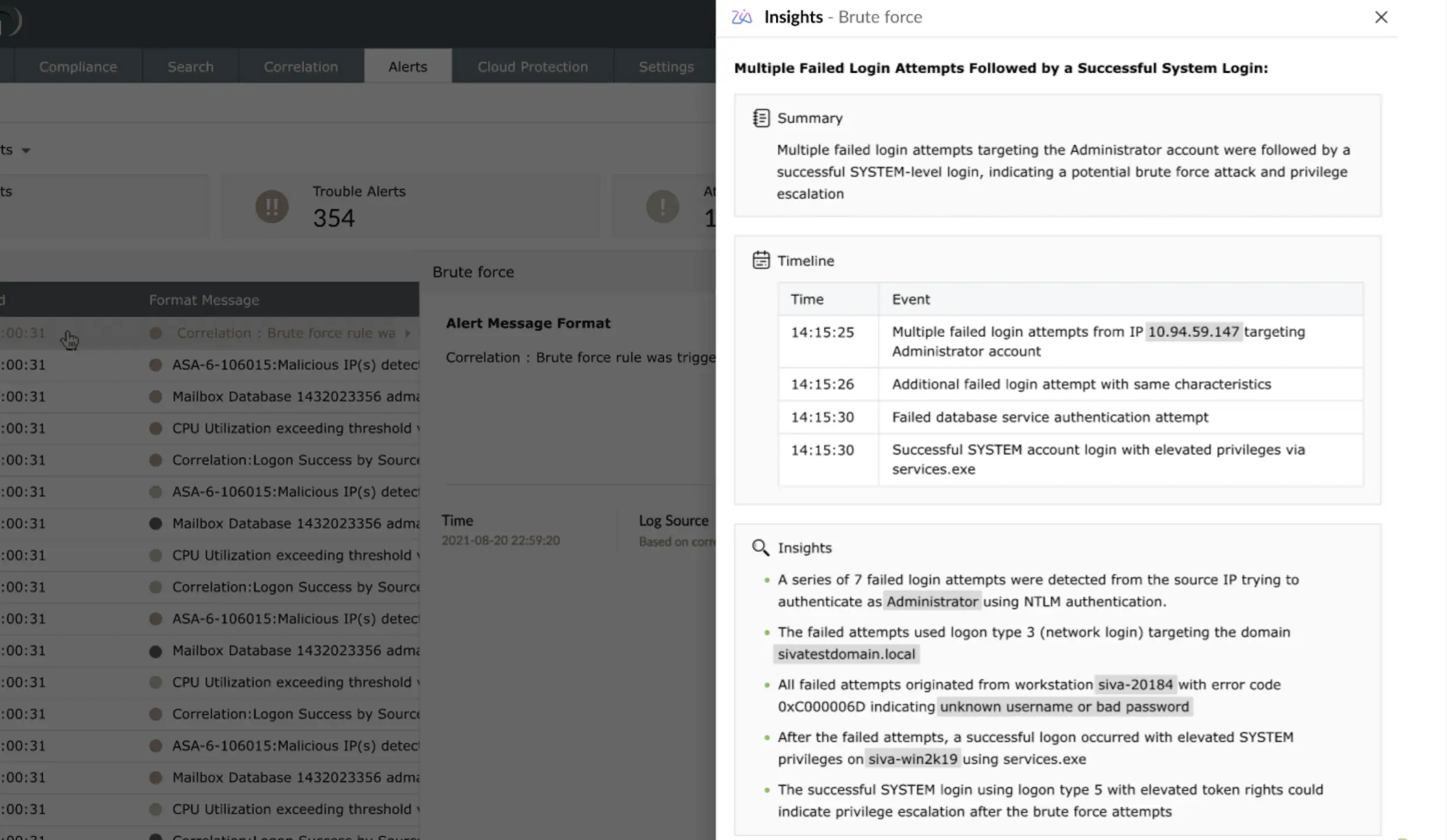
Automated incident response
Log360 automates response actions through predefined correlation rules that identify attack patterns. It can trigger automatic alerts, notifications, and remediation steps to help you respond quickly and minimize potential damage from security incidents.
Learn more
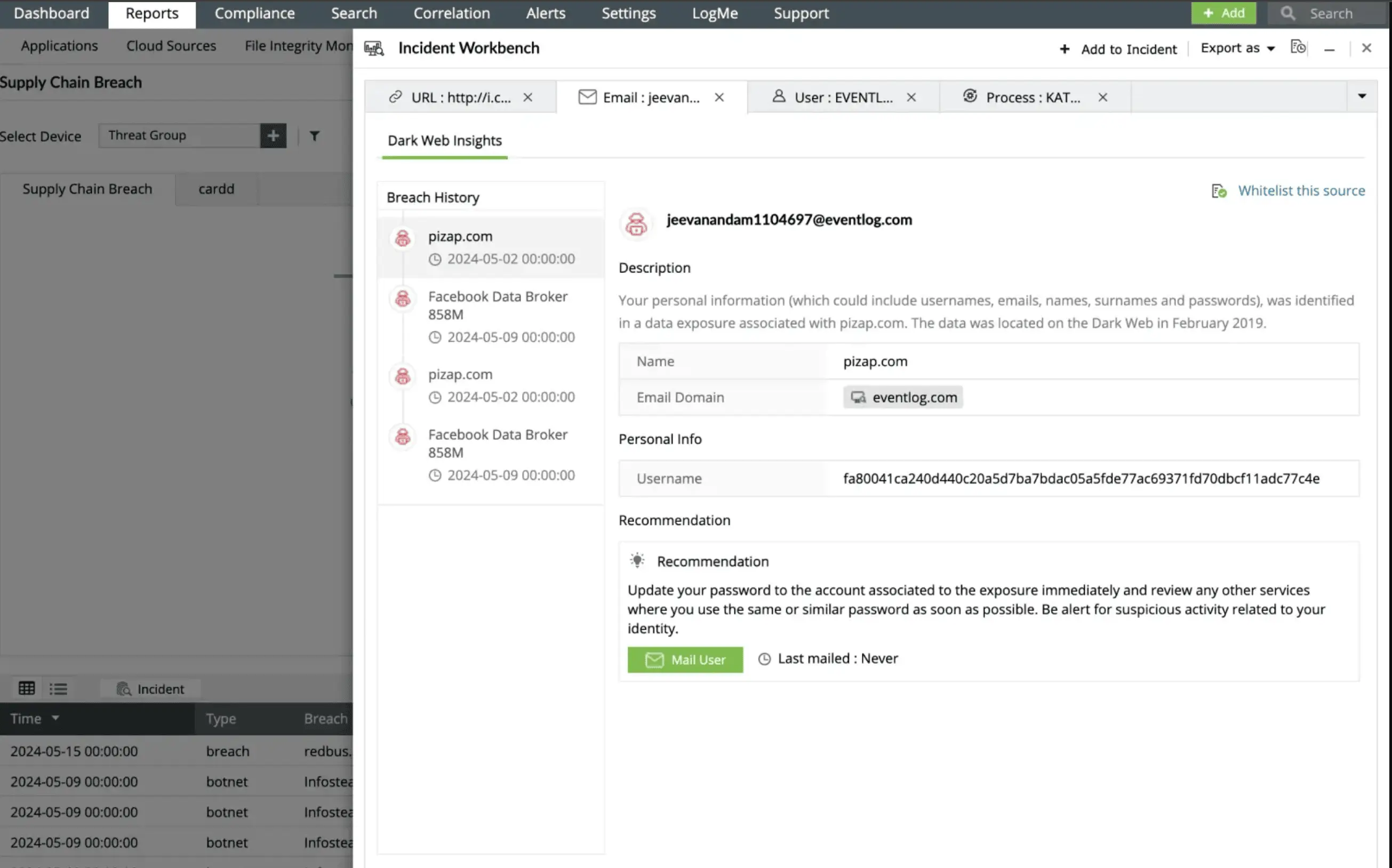
Dark web monitoring
Proactively monitor the dark web for compromised credentials, leaked data, or other threats related to your organization. Log360's dark web monitoring helps identify risks before they escalate, enabling timely risk mitigation and a stronger security posture.
Learn more
Compliance management
Simplify compliance with Log360's extensive library of predefined compliance reports aligned with major regulations including PCI DSS, HIPAA, GDPR, and more. Real-time event correlation and secure, tamper-proof log archiving streamline audit readiness and regulatory adherence effortlessly.
Learn more