Integrate Entra ID(formerly Azure Active Directory) with MDM On-Premise
Azure has been fast rising as the preferred AD services for organizations, especially as more organization go cloud. With that in consideration, you can integrate the Entra ID(formerly Azure AD) of your organization with MDM, to configure policies based on Directory users and/or groups.
Integration Procedure
You need to follow the steps below to integrate your Entra ID with MDM On-Premise:
- On the MDM console, navigate to Enrollment > Directory Services.
- Click on Add Domain and select Entra ID.
- Click on Integrate.
- In case of MDM On-Premises, If OAuth is not configured, you will get an error message saying "OAuth App details are not yet configured".
- Click here to configure OAuth. You will be prompted to enter the Client ID and Client Secret. How to obtain client id and client secret?
Note: For MDM Cloud, OAuth app configuration is not required. - Once you have entered the Client ID and Client Secret, click on Integrate.You will be redirected to Azure login page.
Note : Once you are redirected to Microsoft's login page , complete the integration within 1 minute or else the session will timeout.
- After logging into the Azure portal, a consent screen will be displayed. Click on Accept to complete Azure integration.
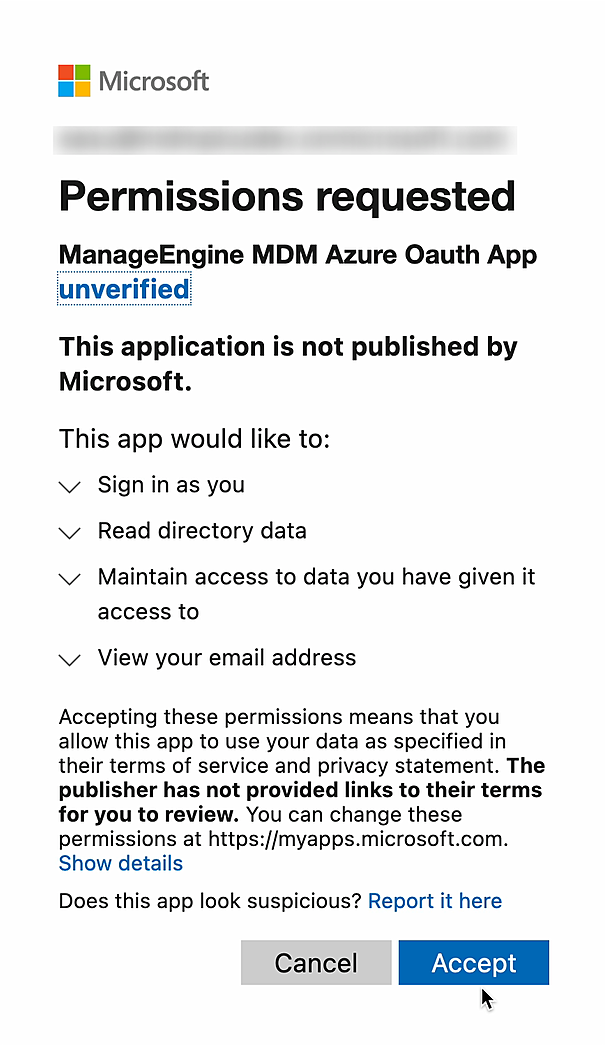
- Once the integration is successful, you will be redirected back to the MDM server. You can utilize the Entra ID credentials for User Authentication during enrollment and creating Directory user groups.
How to obtain Client ID and Client Secret
- Log in to the Azure portal, navigate to App registrations and click on New registration.
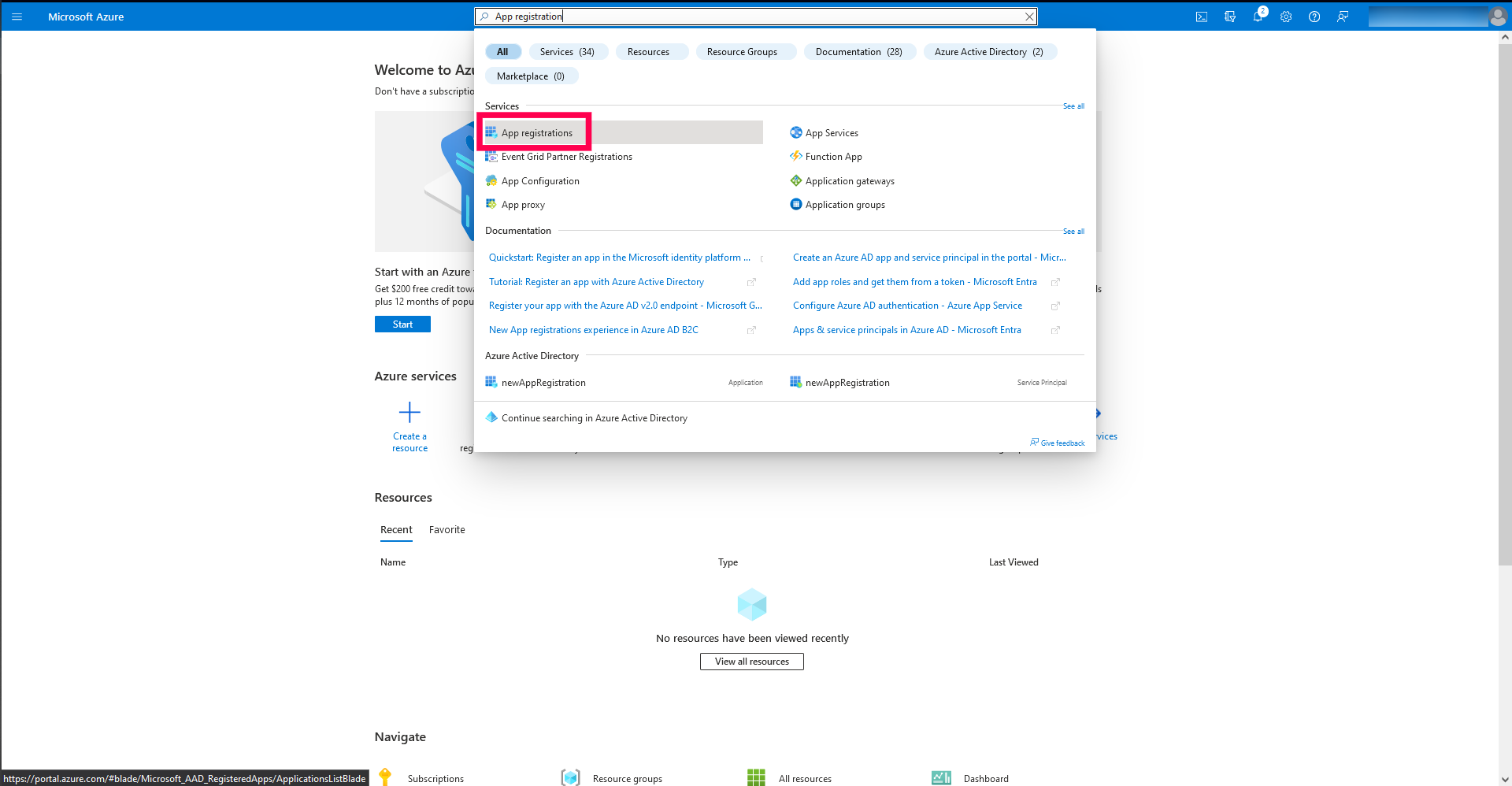
- Provide the name for Azure OAuth app.
- Select Multitenant under supported Account types.
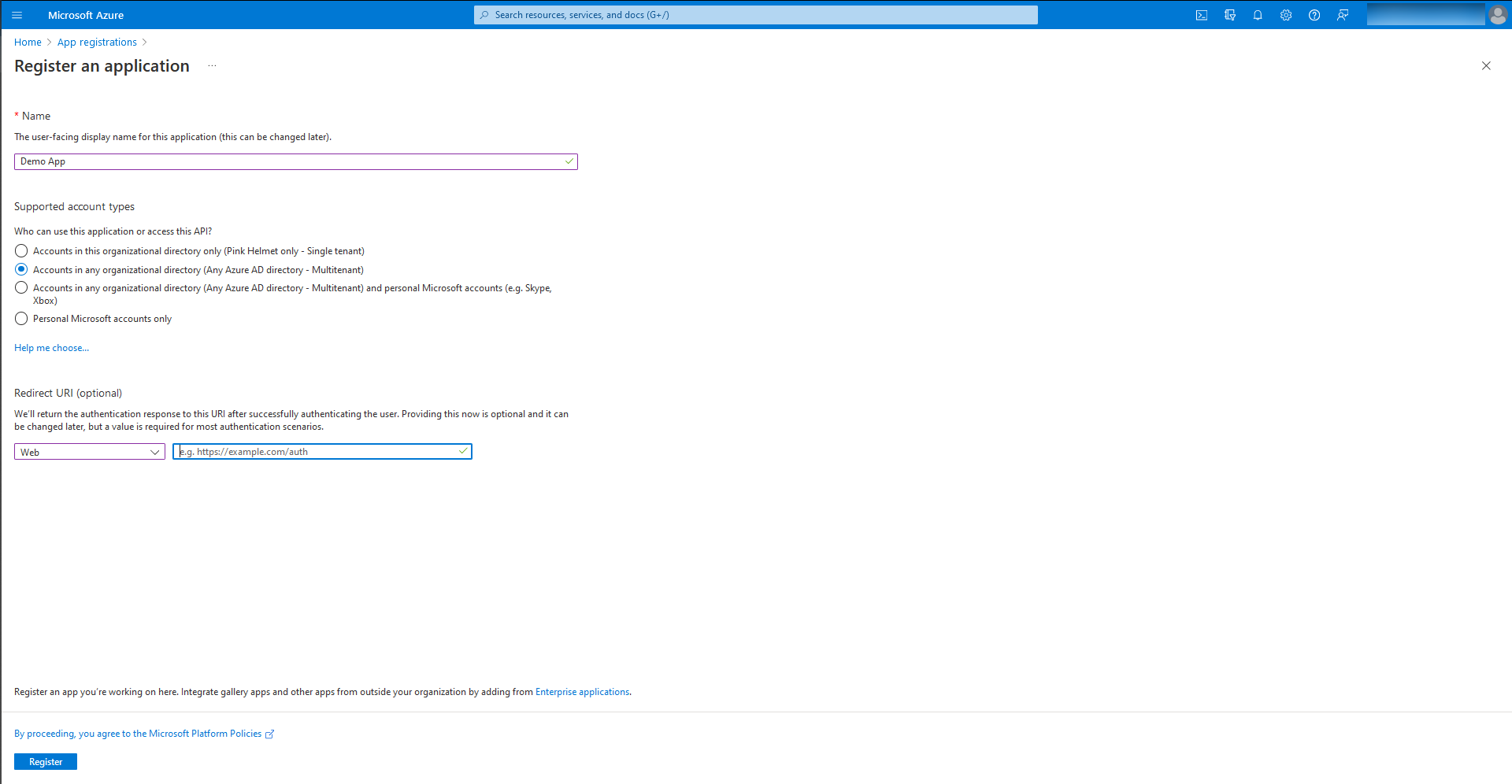
- Select Web as Redirect URI and copy the Redirect URI from the MDM console and enter here.
- Click on Register.
- Once you have registered Azure OAuth app, copy the Client ID and paste it on the MDM server.
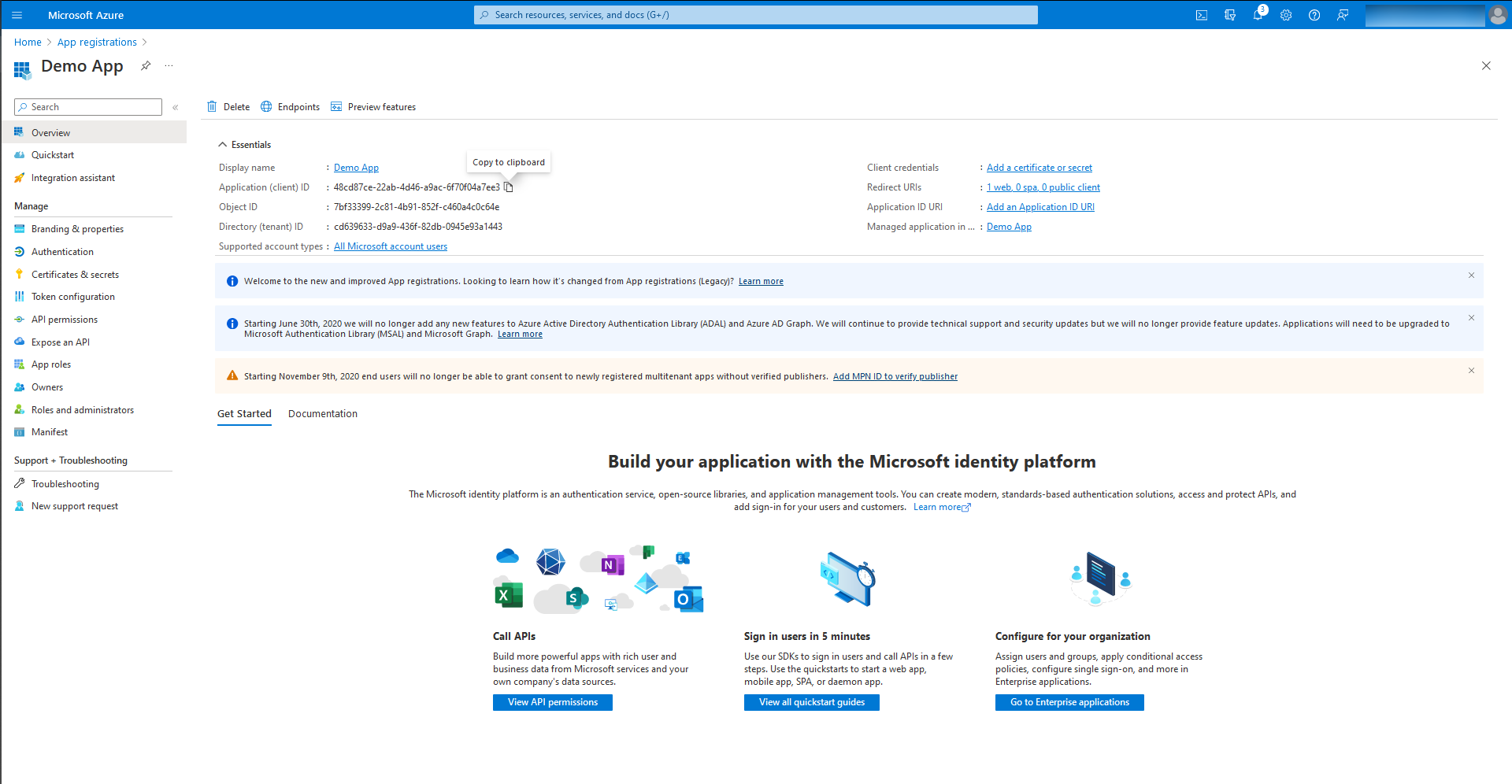
- Click on Add a certificate or secret and click New Client Secret.
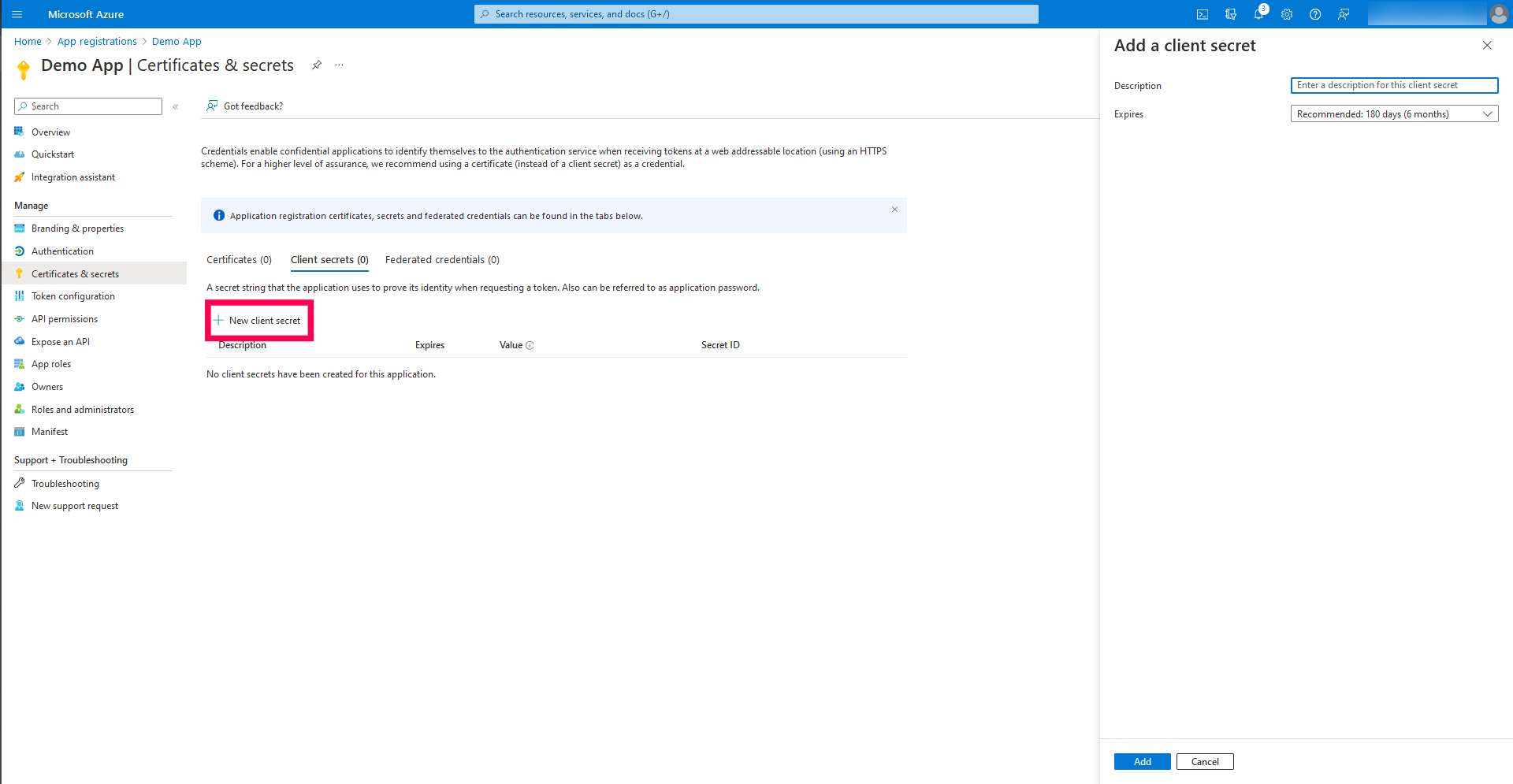
- Enter a description and set the client secret expiry duration.
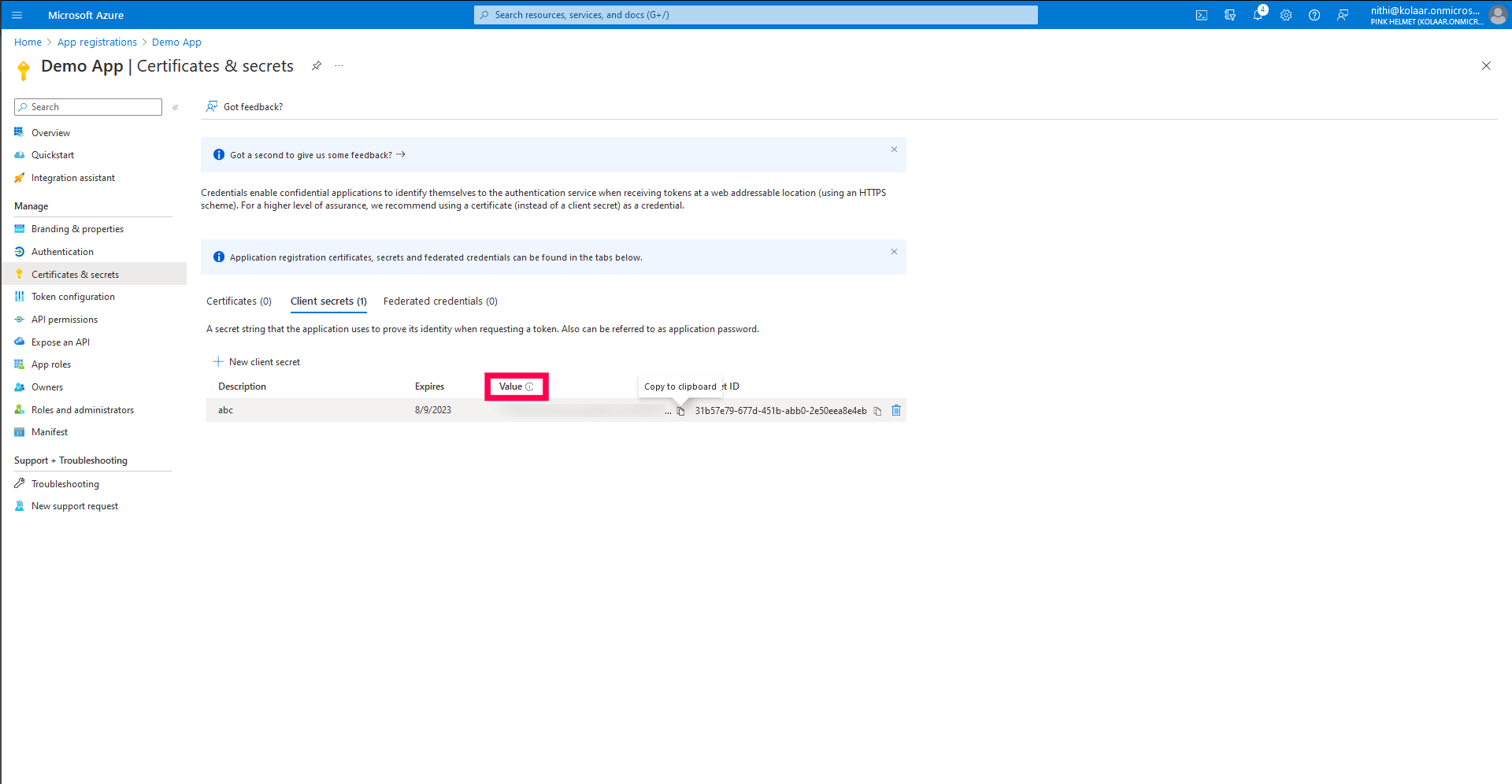
- Copy the value of the Client Secret and paste it back on the MDM server.
- Now the OAuth will be successfully configured on the MDM server.
How to configure 'login_hint'
The login_hint optional claim will be used to offer seamless single sign out experience for users logging in via OAuth. It is a best practice from security and user experience perspective. If you are allowing users to login to the MDM console using Azure credentials, it is recommended to configure 'login_hint'. To configure 'login_hint' follow the below mentioned steps:
- Log in to the Azure portal, navigate to App registrations and choose the Azure OAuth app created for MDM integration.
- Click on Token Configuration.
- Click on Add Optional Claim and select ID.
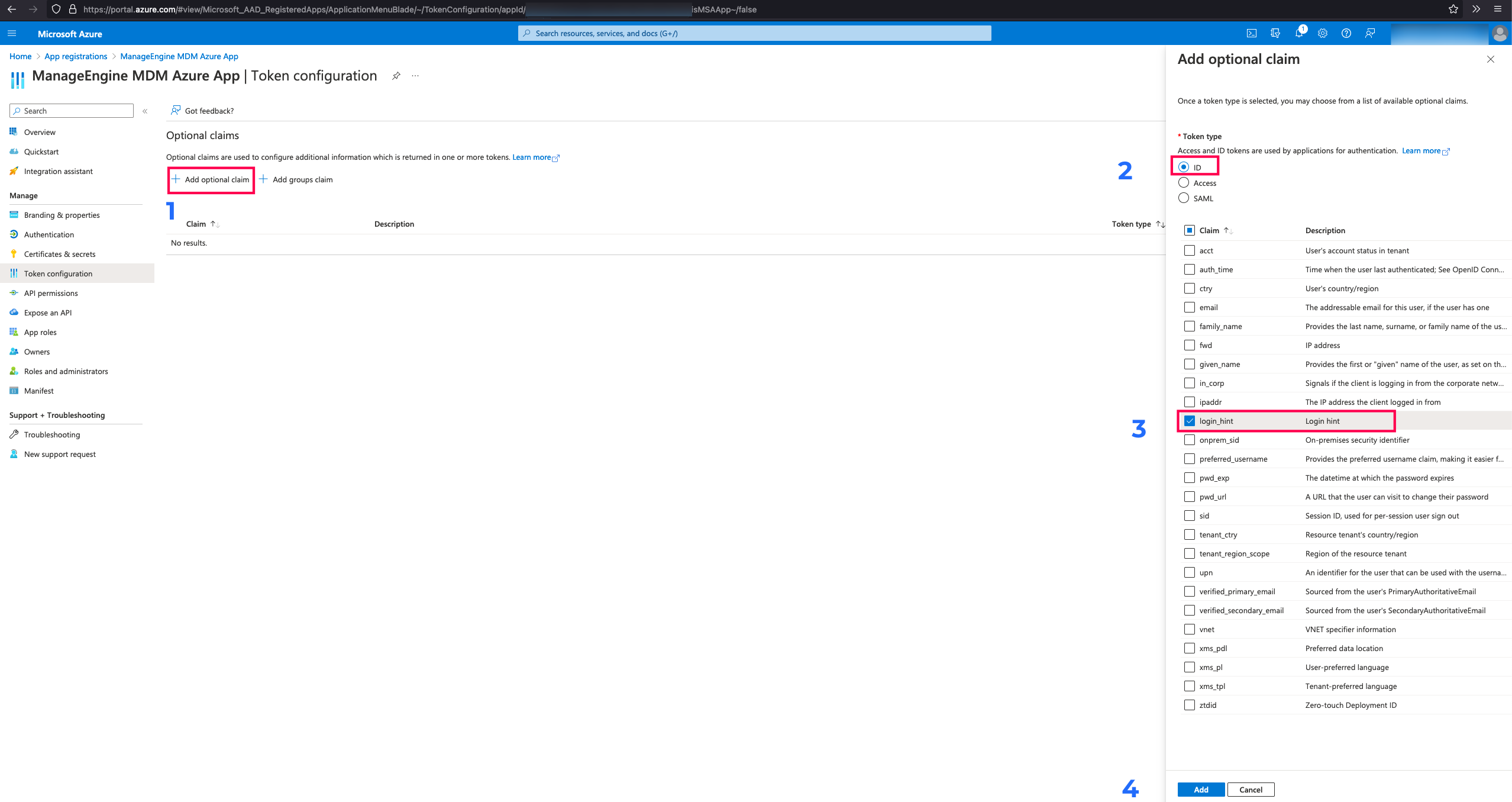
- Select login_hint and click on Add.
