Canned Reports in PAM360
The comprehensive password management process within your enterprise is presented through detailed reports in PAM360. These reports provide IT administrators with critical insights into various activities, including password inventory, policy compliance, password expiry, and user activity. The data is displayed in tables and graphs, enabling informed decision-making regarding password management.
PAM360 offers over 50 predefined reports grouped into six main categories:
To access these reports, navigate to the Reports section, where you will find various report types under each category. Upon generating the desired report, you can export it from PAM360 using any one of the following method: Export as Excel / Export to PDF / E-Mail this Report / Print.
The following sections provide a detailed overview of each report category and its available predefined report types.
1. Password Reports
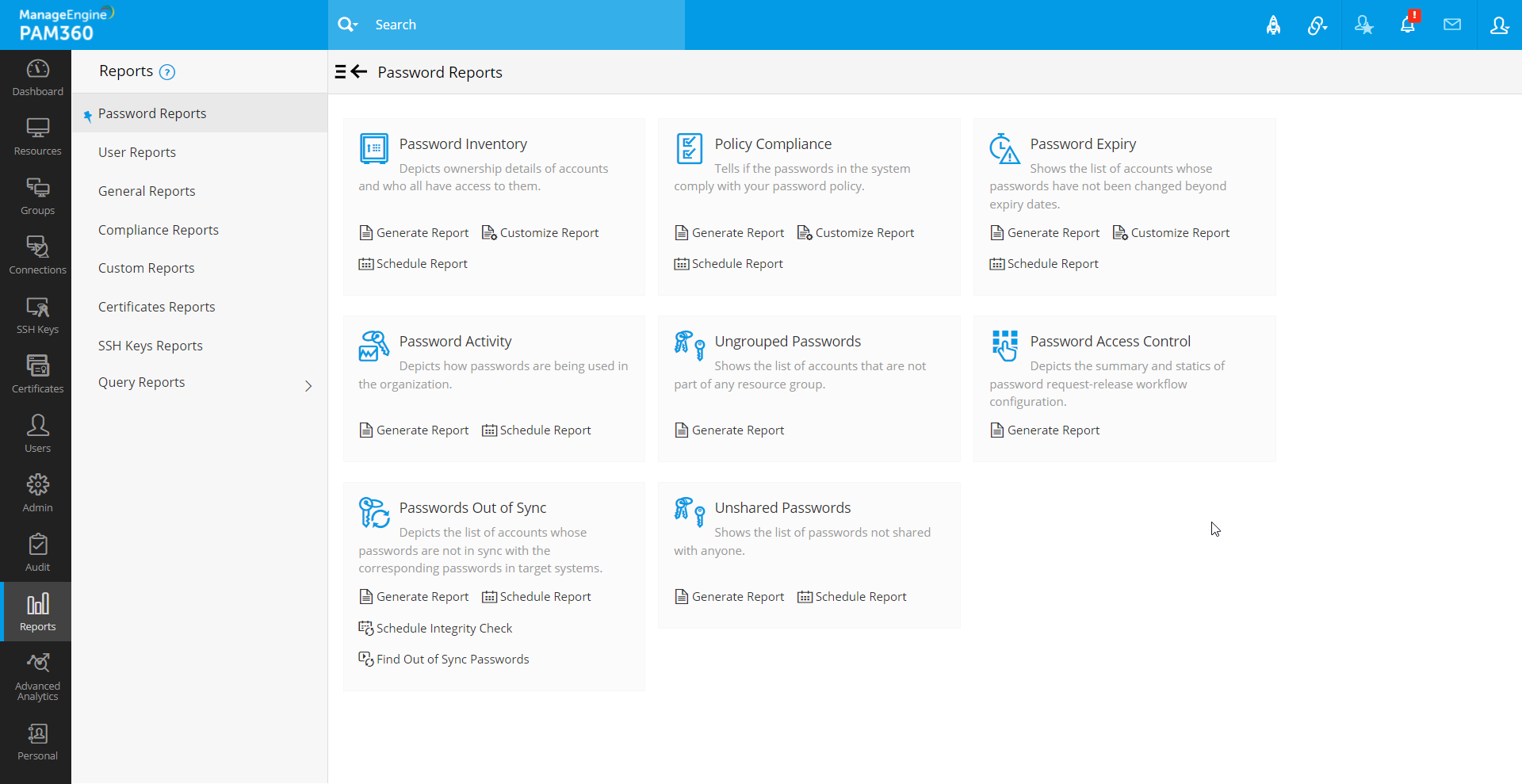
1.1 Password Inventory Report
The Password Inventory Report offers a comprehensive snapshot of key details, including the total number of resources, passwords, resource types, and users in PAM360. Additionally, it provides information on password/resource ownership and access timestamps.
This report is divided into three sections:
- Password Inventory - Summary Report - This section provides a summarized view of the total number of resources, passwords, users, and resource types in PAM360.
- Password Distribution by Resource Type - A pie chart illustrates the distribution of resources by their types, offering a clear visual representation.
- Password Inventory - Detailed Report - This section lists detailed information about all resources, passwords, resource types, and users in PAM360. It also includes ownership details and timestamps of when each password was accessed.
1.2 Policy Compliance Report
The Policy Compliance Report provides a comprehensive overview of passwords that either comply with or violate the password policies set by the administrator. It also includes password ownership details. For non-compliant passwords, the report outlines specific policy violations, helping administrators take immediate corrective actions to ensure compliance.
This report is divided into four sections:
- Password Policy Compliance Summary - This section provides a summary of the total number of passwords, along with counts of compliant and non-compliant passwords.
- Policy Violation by Resource Type - A pie chart illustrates the distribution of non-compliant passwords by resource type, making it easier to identify where violations occur.
- List of Password Policies - All existing password policies are listed here. You can view details of each policy by clicking on its name.
- Policy Compliance Status - This section provides a detailed view of each resource’s compliance status. It shows the number of violations, resource and password ownership, and compliance details in a table format. A search function is also available at the top-right corner of the table for quick access to specific information.
1.3 Password Expiry Report
The Password Expiry Report offers insights into the validity status of passwords. It identifies expired and valid passwords, helping administrators track which passwords require renewal or updates.
This report is divided into three sections:
- Password Expiry - Summary - This section provides a summary of the total number of passwords, along with the number of expired and valid passwords.
- Resource Types and Expiry Status - A pie chart presents the distribution of expired passwords by resource type, offering a quick overview of where action is required.
- Expiry Status of Passwords - This section lists the expiration status of all resources. It includes ownership details and the number of expired/valid passwords for each resource, displayed in a tabular format. A search function at the top-right corner of the table allows quick navigation.
1.4 Password Activity Report
The Password Activity Report provides a detailed analysis of password usage in PAM360. It tracks the most and least accessed passwords, those that were reset frequently, and offers statistics on average password access per day or week.
This report is divided into six sections:
- Activity Statistics - Summary Report - This section summarizes key metrics, including total passwords, average access per day/week, average password age, the number of passwords supporting reset (with or without agents), and any failed password reset attempts.
- Most Accessed Passwords - A graph showing the top 10 most accessed passwords.
- Frequently Reset Passwords - A graph showing the top 10 most frequently rotated passwords.
- Least Accessed Passwords - A graph displaying the 10 least accessed passwords.
- Rarely Changed Passwords - A graph highlighting the 10 least rotated passwords.
- Password Activity Details - This section provides comprehensive details about passwords in sync with target systems, including creation date, access frequency, number of changes, last access/change time, and the frequency of daily/weekly changes.
- Resources with Access Control Workflow Activated - A list of resources configured with password access control workflow.
- Resources with Access Control Workflow Deactivated - A list of resources deactivated with password access control workflow.
- Resources without Access Control Workflow Configuration - This section lists resources for which no access control workflow has been configured.
1.5 Password Access Control - Resource
This report offers a comprehensive overview of the password request-release workflow configuration and usage at the resource level. It details the resources where resource-level access control is enabled, listing password access requests made, approved, and denied over a specified period (between 5 and 30 days). Additionally, it includes information on passwords checked in and out during this time frame.
The report is organized into the following sections:
- Access Control Activated - Lists all resources where resource-level access control is currently active.
- Automatic Approvals - Lists resources configured with an automatic approval time frame for password access.
- Access Control Not Configured - Lists all resources where access control has not been set up.
- Access Control Deactivated - Lists resources where access control has been deactivated.
- Excluded Accounts from Resource Access Control - Lists accounts excluded from resource-level access control.
- Password Access Requests Raised in the Last X Days - Provides a list of all password access requests made within the specified period.
- Password Access Requests Approved in the Last X Days - Details all password access requests that were approved in the specified period.
- Password Access Requests Denied in the Last X Days - Lists all password access requests that were denied within the specified timeframe.
- Passwords Checked Out in the Last X Days - Provides a list of all passwords that were checked out during the specified period.
- Passwords Checked In During the Last X Days - Displays all passwords that were checked in during the specified period.
1.6 Password Access Control - Account
This report provides a detailed summary of how the password request-release workflow is configured and used at the account level. It includes the details of accounts where account-level access control is enabled, along with a list of password access requests made, approved, and denied over a specified period (between 5 and 30 days). It also tracks passwords that were checked in and out during the specified time frame.
The report contains the following sections:
- Access Control Activated - Lists all accounts where account-level access control is currently active.
- Automatic Approvals - Lists accounts with configured automatic approval time frames.
- Access Control Deactivated -Displays accounts where access control is deactivated.
- Password Access Requests Raised in the Last X Days - Lists all password access requests made during the specified period.
- Password Access Requests Approved in the Last X Days - Shows all password access requests approved within the specified timeframe.
- Password Access Requests Denied in the Last X Days - Displays all password access requests denied within the specified period.
- Passwords Checked Out in the Last X Days - Lists all passwords that were checked out during the specified period.
- Passwords Checked In During the Last X Days - Shows all passwords that were checked in within the specified timeframe.
1.7 Passwords Out of Sync Report
This report tracks the integrity of passwords stored in PAM360 compared to their corresponding credentials in target systems like servers, databases, and network devices. Since administrators may directly change passwords on these systems, the passwords stored in PAM360 can become outdated. This report ensures password integrity by conducting checks, both on-demand and automatically, and provides details on whether passwords are synchronized or out of sync.
You can schedule periodic integrity checks by selecting Schedule Report or manually generate this report by selecting Generate Report. Automatic checks are performed daily at 1 AM for accounts with remote synchronization enabled. For on-demand checks, select Schedule Integrity Check, and PAM360 will attempt to establish a connection with the target systems and validate the credentials. Once the connection is successfully established, PAM360 attempts to log in using the stored credentials. If the login attempt fails, PAM360 determines that the password is out of sync. However, if PAM360 is unable to establish a connection with the system due to network issues, it will not classify the password as out of sync. In such cases, a consolidated notification will be sent to all administrators and auditors, keeping them informed of the status.
The report includes the following sections:
- Password Integrity Statistics - Provides a summary of passwords that support remote reset, passwords reset with or without agents, and passwords that are either in sync or out of sync with their corresponding target system credentials.
- Passwords Out of Sync Distribution - A pie chart visualizes the distribution of out-of-sync passwords across different resource types.
- Passwords Out of Sync Details - Lists all out-of-sync passwords, including the owner and resource type.
1.8 Ungrouped Passwords Report
This report provides an overview of the accounts/passwords that are not a part of any resource groups managed in PAM360.
1.9 Unshared Passwords Report
This report highlights passwords stored in PAM360 that are not shared with other users. It lists all unshared passwords, ensuring administrators are aware of restricted access credentials within the system.
2. User Reports

2.1 User Access Report
This report provides comprehensive details on all users within the system, focusing on their access to passwords and resources.
It is organized into the following sections:
- User Statistics - Summary Report - This section summarizes user-related activities, including the number of new users added, users deleted, role changes, invalid login attempts, users who reset passwords, and users who have not logged in during the last five days. It also includes the total number of users and user groups in the system, along with their respective roles. The report can be exported as a PDF or emailed to recipients by selecting the Export to PDF and Email this Report options.
- User Activity Summary Report - Captures and summarizes user actions related to passwords, such as retrievals and resets. It shows the number of such actions performed by each user and user group, offering insights into individual and group-level password activities.
- User Access Details - This section provides a detailed view of the resources and resource groups owned by or shared with each user, along with the privileges granted to them.
- User Group Access Details - Lists all users within each user group and details the resource groups owned by or shared with those groups.
2.2 User Activity Report
This report provides a detailed breakdown of password-related activities performed by all users in the system. It is divided into the following sections:
- Activity Statistics - Summary Report - Graphically represents the total number of passwords accessed by users and user groups over a specified time period.
- Most Active Users - Login/Access/Reset - Highlights the top 10 users based on the highest number of login attempts, password accesses, and password resets.
- Least Active Users - Login/Access/Reset - Lists the 10 users with the fewest login attempts, password accesses, and password resets.
- User Activity Details - Provides comprehensive information about user activities, including total login attempts, invalid attempts, passwords accessed, and passwords reset.
2.3 Ungrouped Users Report
This report lists users in PAM360 who are not part of any user group. It also includes the passwords owned by these users, giving a clear picture of ungrouped individuals and their password access.
3. General Reports

3.1 Executive Report
The Executive Report offers a high-level overview of both password access and user activities within the system. It combines key metrics from password and user reports, summarizing the following:
- Password Statistics
- Password Activity
- Password Policy
- Password Expiry
- Password Out of Sync
- User Statistics
- User Activity
This report provides a holistic snapshot, making it an essential tool for administrators to monitor overall system performance and security.
4. Compliance Reports
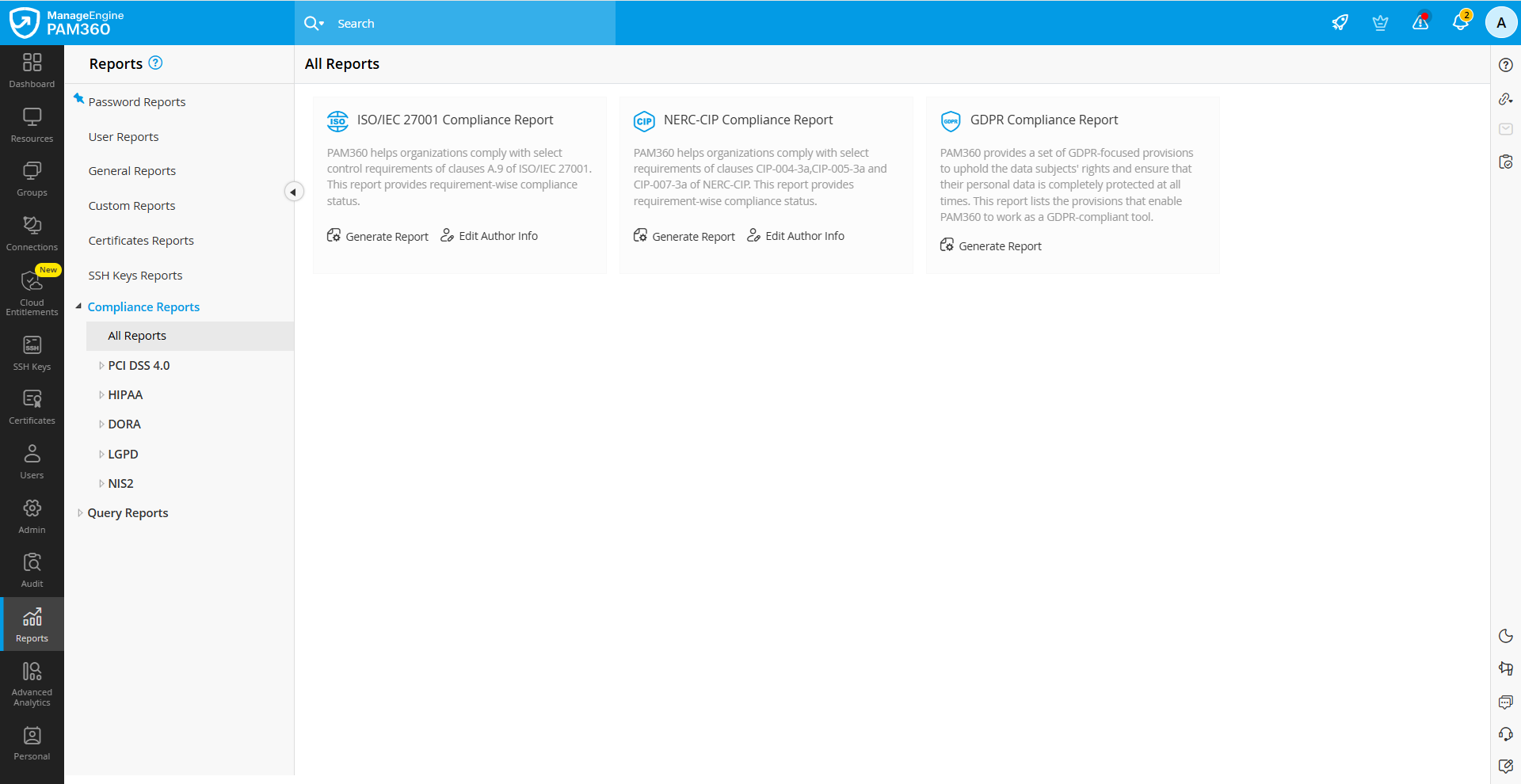
4.1 PCI DSS Compliance Report
PCI DSS identifies network violations related to the Payment Card Industry (PCI) Data Security Standard (DSS), particularly concerning shared administrative, software, and service account passwords across various systems. This multifaceted security standard encompasses requirements for security management, policies, procedures, network architecture, software design, and other critical protective measures. It comprises 12 general requirements aimed at the following six goals:
- Build and maintain a secure network
- Protect cardholder data
- Ensure the maintenance of vulnerability management programs
- Implement strong access control measures
- Regularly monitor and test networks
- Ensure the maintenance of information security policies
This standard is governed by PCI Security Standards Council.
What does it Convey?
This report highlights any violations within your network related to the use and management of shared administrative, software, and service account passwords, as per PCI DSS requirements.
Caution
Full compliance with all 12 PCI DSS requirements necessitates implementing various tools and security procedures within your organization.
You can generate separate compliance reports for each of the PCI DSS requirements, or create a consolidated report covering all requirements. This report can be exported as a PDF or emailed by clicking Export to PDF or Email this Report.
4.2 ISO/IEC 27001 Compliance Report
ISO/IEC 27001 is an internationally recognized standard for establishing, operating, monitoring, reviewing, maintaining, and improving an information security management system (ISMS). It provides a framework for protecting sensitive data, including financial records, intellectual property, and customer information, through the implementation of appropriate security controls. The standard comprises ten core clauses, along with Annex A, which specifies multiple control frameworks. Among these, A.9 Access Control outlines the following key security measures:
- A robust information security policy is in effect to ensure only authorized users have access to critical systems.
- All users are uniquely identified and have established accountability for all privileged activities.
- Access is only allowed to systems through secure mechanisms.
- Sensitive information is protected with cryptographic controls.
What does it Convey?
This report communicates the organization's compliance with ISO/IEC 27001’s Access Control requirements, specifically as outlined in Clause A.9. It assesses factors such as strong password policies for privileged accounts, reliable audit trails, robust authentication mechanisms, secure access for privileged users, and data security measures. A consolidated ISO/IEC 27001 compliance report will cover various controls, including sections A.9.1 to A.9.4.3 (A.9.1, A.9.1.1, A.9.1.2, A.9.2, A.9.2.1, A.9.2.2, A.9.2.3, A.9.2.4, A.9.2.5, A.9.2.6, A.9.3, A.9.3.1, A.9.4, A.9.4.1, A.9.4.2 and A.9.4.3). You also have the option to generate separate reports for each requirement.
This report can be exported as a PDF or spreadsheet, and emailed by clicking Export to PDF/Export to XLS or Email this Report.
Caution
These compliance reports address only specific clauses of the security standards. Full compliance with ISO 27001 requires the implementation of additional tools and security practices.
4.3 NERC CIP Compliance Report
The North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) standards were developed to ensure the security and reliability of the power grid's critical assets, such as electric utilities, generation systems, and transmission systems. NERC CIP contains nine sections that cover physical, virtual, and organizational security measures aimed at securing the bulk power system. Specific clauses, including CIP-004-3a, CIP-005-3a, and CIP-007-3a, mandate:
- A regular review of authorized personnel with access to critical systems.
- Granular access controls based on functional roles.
- Robust authentication methods.
- Comprehensive auditing of security events.
- Monitoring of user activity during privileged sessions.
- Use of strong passwords with reliable complexities.
What does it Convey?
This report evaluates an organization’s compliance with the selected requirements of CIP-004-3a, CIP-005-3a, and CIP-007-3a. It helps auditors understand the implemented security measures, including privileged access policies, authentication checks for privileged users, user activity auditing, session monitoring, and password policies. Separate compliance reports can be generated for each clause, or a consolidated NERC CIP report can be created.
This report can be exported as a PDF or spreadsheet, and emailed by clicking Export to PDF/Export to XLS or Email this Report.
Caution
These compliance reports cover only select clauses of the NERC CIP standards. Full compliance requires the implementation of additional security tools and practices.
4.4 NIS2 Compliance Report
The NIS2 directive outlines over 140+ requirements that aim to strengthen cybersecurity and ensure the resilience of essential services in diverse sectors. These requirements can be broadly categorized as follows:
- Perform regular risk assessments and establish comprehensive information security policies for critical systems.
- Implement processes to assess continuously and monitor the effectiveness of security controls.
- Develop and enforce guidelines for cryptographic methods, including encryption where applicable.
- Establish a robust incident response plan to efficiently manage and mitigate security incidents.
- Ensure secure procurement, development, and operation of systems, including defined processes for vulnerability management and reporting.
- Deliver ongoing cybersecurity awareness training and promote strong cyber hygiene practices across the organization.
- Implement stringent access controls for employees handling sensitive data, ensuring effective data access policies and comprehensive asset management.
- Maintain a business continuity plan with regular, verified backups to ensure system availability during and after incidents.
- Enforce multi-factor authentication (MFA), continuous authentication, and encryption for all communication channels, including voice, video, messaging, and emergency communications, where appropriate.
- Enhance supply chain security by implementing tailored security measures for each supplier and conducting regular assessments of overall supply chain security.
What does it Convey?
The NIS2 compliance report highlights key areas like enforcing strict privileged access controls, ensuring secure credential management, and continuous monitoring of privileged activities. It emphasizes the importance of implementing least-privilege policies, securing supply chain access, and maintaining detailed audit trails to meet the directive’s cybersecurity requirements. Compliance ensures that privileged accounts in critical systems are properly managed and protected, reducing the risk of breaches and improving overall security posture.
These requirements emphasize a holistic approach to cybersecurity, ensuring that organizations maintain a proactive, resilient stance against both internal and external threats while promoting collaboration and compliance across their supply chains and workforce.
These reports can be generated in the form of PDF or spreadsheet and can also be emailed to required recipients. Click the links Export to PDF/Export to XLS/Email this Report to do the required operation.
Caution
These compliance reports help to address requirements only in a few NIS2 directives. To adhere to all the directive requirements of NIS2, other tools and security procedures should be implemented.
4.5 LGPD Compliance Report
The LGPD (Lei Geral de Proteção de Dados) is Brazil's data protection law, designed to regulate the processing of personal data and ensure individual's privacy and security. It specifies guidelines for how organizations should collect, use, store, and share personal data to protect data subjects and ensure accountability. This law mandates specific measures for data governance, security, and transparency, aligning with global data protection standards. To help organizations comply with the LGPD, the LGPD compliance report provides a detailed overview of the implemented security and governance measures for personal data. Key compliance measures addressed by this report include:
- Restricting sensitive data based on roles and responsibilities
- Comprehensive auditing of activities related to personal data processing
- Privileged session monitoring to ensure actions performed on personal data are within compliance boundaries
- Enforcing robust encryption and password policies to safeguard personal data from unauthorized access
- Documenting incidents involving personal data breaches and tracking remediation measures
This report highlights an organization's adherence to the requirements of the LGPD guidelines, offering insights into the measures implemented to ensure data protection and privacy. It helps auditors assess compliance with key aspects, such as access controls, data usage auditing, incident response protocols, and data security. Along with a consolidated LGPD compliance report, there are options to generate separate reports focusing on specific data protection requirements outlined in the LGPD framework, enabling a more detailed analysis of compliance efforts.
These reports can be exported as PDFs or spreadsheets for documentation or emailed directly to the required recipients. Use the Export to PDF/XLS and Email this Report options to perform these actions.
Caution
While these reports highlight critical compliance measures related to the LGPD, organizations may need to implement additional tools and procedures to fully address all aspects of the law and ensure complete compliance.
4.6 HIPPA Compliance Report
The Health Insurance Portability and Accountability Act (HIPAA) is a U.S. federal law that establishes national standards for protecting sensitive patient health information. It governs how healthcare organizations, their business associates, and related entities handle Protected Health Information (PHI), ensuring confidentiality, integrity, and availability of health data. The law enforces strict administrative, technical, and physical safeguards to prevent unauthorized access or disclosure of PHI.
To assist organizations in achieving and maintaining HIPAA compliance, the HIPAA compliance report in PAM360 provides a detailed summary of the controls, policies, and monitoring mechanisms implemented to protect sensitive health data. Key compliance measures addressed by this report include:
- Implementing strong password and encryption policies to secure systems that handle sensitive medical records.
- Enforcing role-based access control to limit access to systems that contain PHI based on job responsibilities.
- Monitoring privileged sessions to systems that contain PHI to ensure compliance with healthcare data handling standards.
- Maintaining detailed audit trails of all privileged actions involving systems that store or process PHI.
What does it Convey?
This report demonstrates the organization’s adherence to HIPAA’s Privacy and Security Rules, offering clear insights into access controls, activity auditing, and data protection measures. It enables compliance officers and auditors to evaluate whether the organization’s security posture aligns with HIPAA requirements. In addition to a consolidated HIPAA report, PAM360 allows generating focused reports on specific safeguards to support targeted compliance assessments.
These reports can be exported as PDFs or spreadsheets for documentation or emailed directly to the required recipients. Use the Export to PDF/XLS and Email this Report options to perform these actions.
Caution
While this compliance report highlight critical compliance measures related to the HIPPA regulations, organizations may need to implement additional tools and procedures to fully address all aspects of the law and ensure complete compliance.
4.6 DORA Compliance Report
The Digital Operational Resilience Act (DORA) is a regulation established by the European Union to strengthen the digital resilience of financial entities against Information and Communication Technology (ICT)-related incidents. It sets comprehensive requirements for risk management, incident reporting, operational continuity, and third-party oversight to ensure the stability of the financial sector’s digital ecosystem.
The DORA compliance report in PAM360 offers a comprehensive view of the security and operational controls in place to meet DORA’s regulatory requirements. It helps financial institutions ensure that their systems, data management, and access practices are resilient, traceable, and well-governed. Key compliance measures addressed by this report include:
- Centralized management of privileged accounts across all critical financial systems.
- Continuous monitoring and auditing of privileged activities to detect and respond to anomalies.
- Enforcing password rotation, encryption, and secure authentication mechanisms to reduce operational risk.
- Ensuring vendor and third-party access is tightly controlled and regularly reviewed.
What does it Convey?
This report showcases how an organization’s privileged access management practices align with DORA’s operational resilience and cybersecurity mandates. It provides auditors and compliance teams with visibility into access controls, event monitoring, and incident response readiness. PAM360 also supports generating focused reports on risk management and operational continuity to help organizations evaluate specific areas of compliance in greater detail.
These reports can be exported as PDFs or spreadsheets for documentation or emailed directly to the required recipients. Use the Export to PDF/XLS and Email this Report options to perform these actions.
Caution
This compliance report helps requirements in select clauses of DORA. Other tools and security procedures should be implemented to fully adhere to all the requirements.
5. SSH Keys Reports
For detailed information regarding the available pre-configured (canned) SSH key reports in PAM360, please refer to this help documentation.
6. Certificates Reports
To explore the various pre-configured certificate reports offered in PAM360, please refer to this help documentation.