ManageEngine named a Challenger in the 2024 Gartner ® Magic Quadrant ™ for Privileged Access Management
The need for two-factor authentication for remote access
Authenticating a user before providing them with access to critical systems is crucial for enterprises to defend against cyberattacks. The username-password combination has long been the traditional method of user authentication, although passwords are rarely unique to the user. However, compromised and weak passwords can be exploited by anyone to access a corporate network, putting organizations at risk. To counter such risks, enterprises need to implement a multi-layered, defense-in-depth approach to user authentication.
Given the nature and scope of remote access activities and the entitlements available to a privileged user, enterprises must include two-factor authentication (2FA) in their remote access strategy to improve security and accountability. Currently, many compliance standards like PCI-DSS, HIPAA, and NERC-CIP specifically require that remote access tools implement 2FA for granting remote access to critical systems. Failure to meet these regulatory standards by any organization could wreck its reputation and incur significant fines.
Access Manager Plus integrates with various tools available on the market for primary and secondary factors of authentication, helping organizations adopt a strong, well-defined 2FA architecture to meet security requirements.
Primary factor of authentication
Active Directory (AD)/Azure AD authentication: Leverage Microsoft’s AD authentication and single sign-on capabilities for Windows-based systems to allow users to log in to Access Manager Plus with their AD or Azure AD credentials. Moreover, users already logged in to their Windows applications with their directory credentials can log in to Access Manager Plus without supplying credentials.
Lightweight Directory Access Protocol (LDAP) authentication: When Access Manager Plus is installed in a Linux/Unix system, administrators can use LDAP to authenticate users from any LDAP-compliant directory. LDAP is operating system (OS)-agnostic; it can talk to any directory service irrespective of the OS, including Windows AD.
RADIUS-based authentication: Administrators using RADIUS as the directory service inside their organization can use it as the primary authentication method to log users into Access Manager Plus. They can import user information from the RADIUS server, sync role information, and also perform user authentication in real time.
Single sign-on (SSO): An SSO system grants access to multiple systems with a single set of login credentials. Access Manager Plus supports SSO through SAML-based authentication for Okta, Azure AD, and Active Directory Federation Services (ADFS), and through NTLM-based authentication for on-prem AD. Upon activation, users already logged in to the system with their Okta, Azure AD, ADFS, or AD credentials will be automatically authenticated into Access Manager Plus using the respective protocols.
Smart card PKI/certificate authentication: Access Manager Plus' web interface supports smart card technology with SSL client certificate authentication. Administrators with a smart card authentication system in their environment can configure Access Manager Plus to authenticate a user with their smart card, mandating them to provide their personal identification number (PIN) and X.509 certificate to login.
Local authentication: Besides the above options, an authentication database is built into Access Manager Plus, making it a local authentication server. Typically, you can create local user accounts for temporary users who do not have accounts on your enterprise servers, and for administrators and privileged users for break glass purposes. The built-in password generator can be used to generate passwords according to the policy enforced by the system administrator.
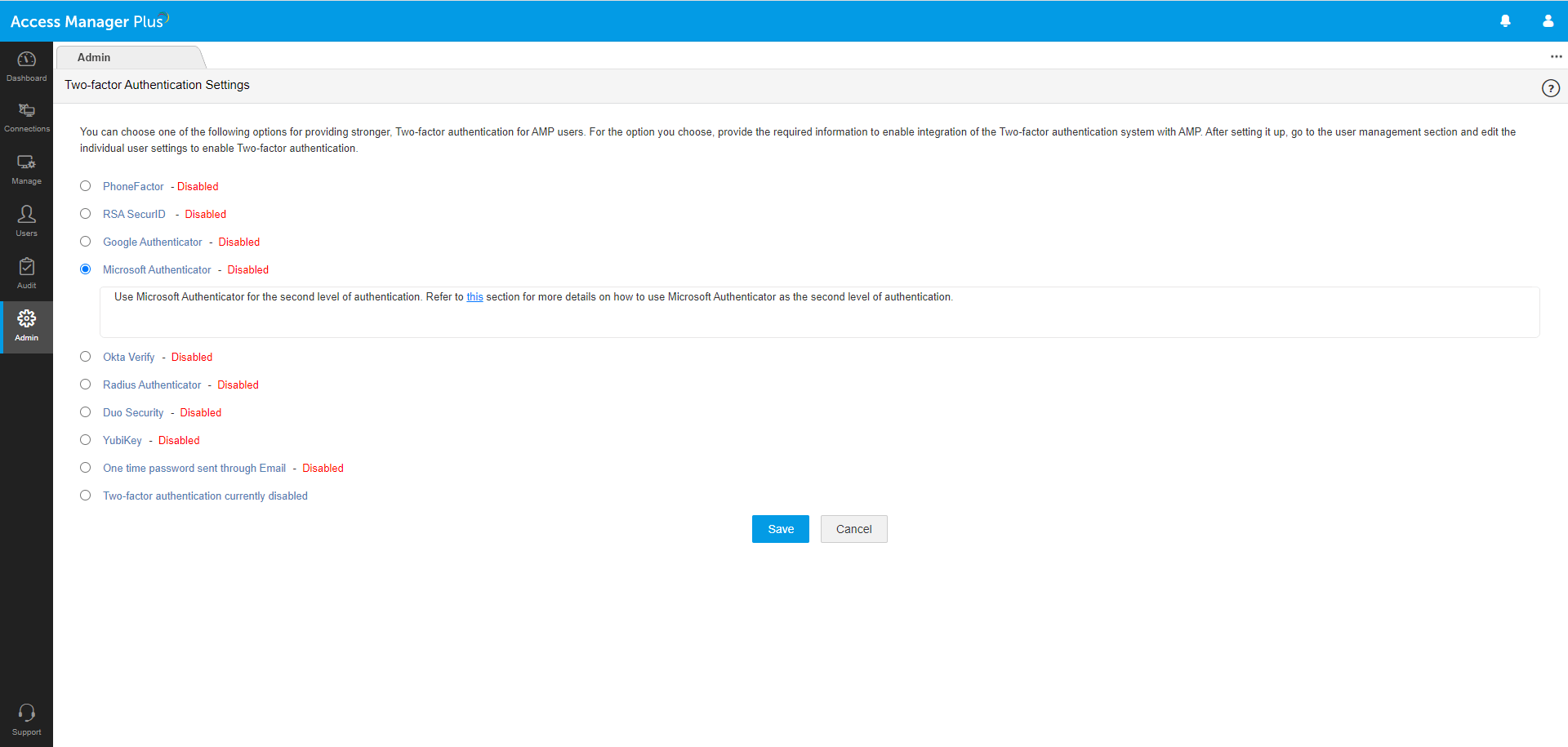
Secondary factor of authentication
Unique password through email: Send a unique one-time password (OTP) to users via email as the secondary factor of authentication. This OTP expires after a stipulated time period.
Windows Azure Multi-Factor Authentication: Formerly called PhoneFactor, this leading global provider of phone-based 2FA enables simple and effective security by placing a confirmation call to a user’s phone during the login process.
RSA SecurID Access: This application generates a software token, which usually changes every 60 seconds. After providing the first factor of authentication, a user needs to enter both a PIN and the corresponding RSA SecurID token code as the secondary factor of authentication.
Time-based one time password (TOTP): TOTP is part of the open authentication (OAuth) security architecture, and is an automatically generated numeric string of characters that authenticates a user and expires after a certain time period. Access Manager Plus supports any third party TOTP-based authenticator, like Google Authenticator, Microsoft Authenticator, and Okta Verify.
RADIUS-based 2FA: Access Manager Plus integrates with any RADIUS-compliant system, like Vasco Digipass, AuthAnvil, or PingIdentity, to accomplish 2FA. Upon successful primary authentication, a user must provide the RADIUS code similar to a TOTP as the secondary factor of authentication.
Security: Duo Security is a vendor of cloud-based 2FA services that lets users log in to Access Manager Plus through a mobile app, a text message, or a phone call.
YubiKey: YubiKey is a hardware key that supports OTPs, public key encryption, and authentication. After the primary authentication, a user needs to insert their YubiKey into the USB port of their laptop or computer to generate an OTP and provide it as the secondary factor for successful authentication.