Configuring audit policies - Manual configuration
Audit policies must be configured to ensure that events are logged whenever any activity occurs.
Configuring advanced audit policies
Advanced audit policies help administrators exercise granular control over which activities get recorded in the logs, helping cut down on event noise. It is recommended that advanced audit policies are configured on domain controllers running on Windows Server 2008 and above.
- Log in to any computer that has the Group Policy Management Console (GPMC), with Domain Admin credentials → Open GPMC → Right click on Default Domain Controllers Policy → Edit.
Note: If you're hesitant to modify the Default Domain Controllers Policy, you can instead create a new GPO with the same audit settings. Link this new GPO to the Domain Controllers OU with a higher precedence, and follow the steps below. This approach keeps the default policy intact while still applying the necessary audit policies.
- In the Group Policy Management Editor → Computer Configuration → Policies → Windows Settings → Security Settings → Advanced Audit Policy Configuration → Audit Policy, Double-click on the relevant policy setting.
- Navigate to the right pane → Right-click on the relevant Subcategory, and then click Properties → Select Success, Failure, or both; as directed in the table below.
| Category |
Sub Category |
Audit Events |
| Account Logon |
- Audit Kerberos Authentication Service
|
Success and Failure |
| Account Management |
- Audit Computer Account Management
- Audit Distribution Group Management
- Audit Security Group Management
|
Success |
- Audit User Account Management
|
Success and Failure |
| Detailed Tracking |
- Audit Process Creation
- Audit Process Termination
|
Success |
| DS Access |
- Audit Directory Services Changes
- Audit Directory Service Access
|
Success |
| Logon /Logoff |
- Audit Logon
- Audit Network Policy Server
|
Success and Failure |
- Audit Other Logon/Logoff Events
- Audit Logoff
|
Success |
| Object Access |
- Audit Other Object Access Events
|
Success |
| Policy Change |
- Audit Authentication Policy Change
- Audit Authorization Policy Change
|
Success |
| System |
- Audit Security State Change
|
Success |
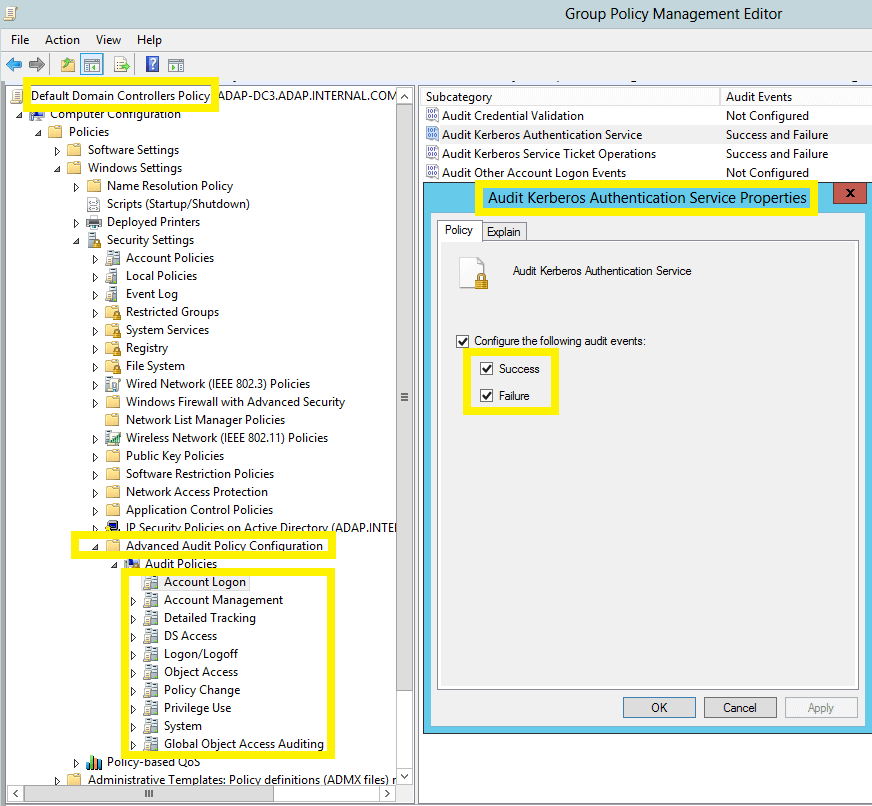
Image showing: Account Logon category → Audit Kerberos Authentication Service subcategory → Both Success and Failure configured.
Enforcing advanced audit policies
When using advanced audit policies, ensure that they are forced over legacy audit policies.
- Log in to any computer that has the Group Policy Management Console (GPMC), with Domain Admin credentials → Open GPMC → Right click on Default Domain Controllers Policy → Edit.
- In the Group Policy Management Editor → Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → Security Options.
- Navigate to the right pane → Right-click on Audit: Force audit policy subcategory settings → Properties → Enable.
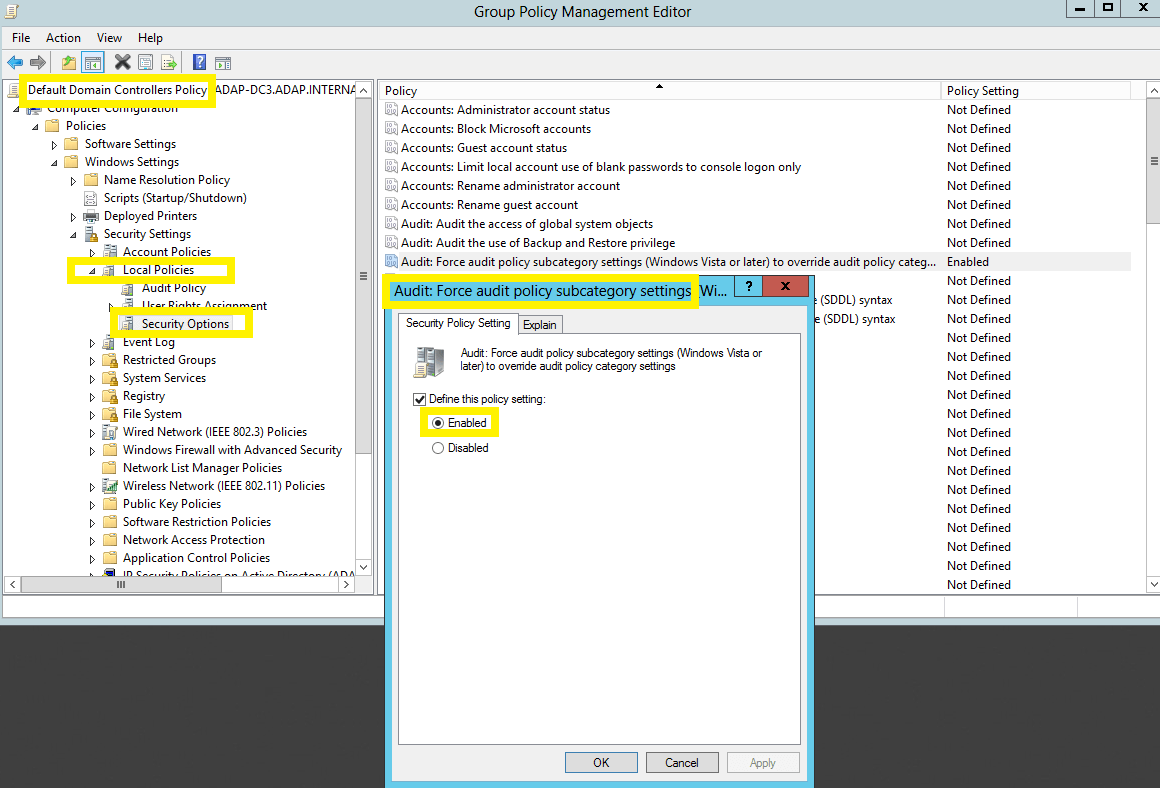
Configuring legacy audit policies
The option to configure advanced audit policies is not available in Windows Server 2003 and below. Therefore for these systems, you need to configure the legacy audit policies.
- Log in to any computer that has the Group Policy Management Console (GPMC), with Domain Admin credentials → Open GPMC → Right click on Default Domain Controllers Policy → Edit.
- In the Group Policy Management Editor → Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → Double click on Audit Policy.
- Navigate to the right pane → Right-click on the relevant policy, and then click Properties → Select Success, Failure, or both; as directed in the table below-
| Category |
Audit Events |
| Account Logon |
Success and Failure |
| Audit Logon / Logoff |
Success and Failure |
| Account Management |
Success |
| Directory Service Access |
Success |
| Process Tracking |
Success |
| Object Access |
Success |
| System Events |
Success |
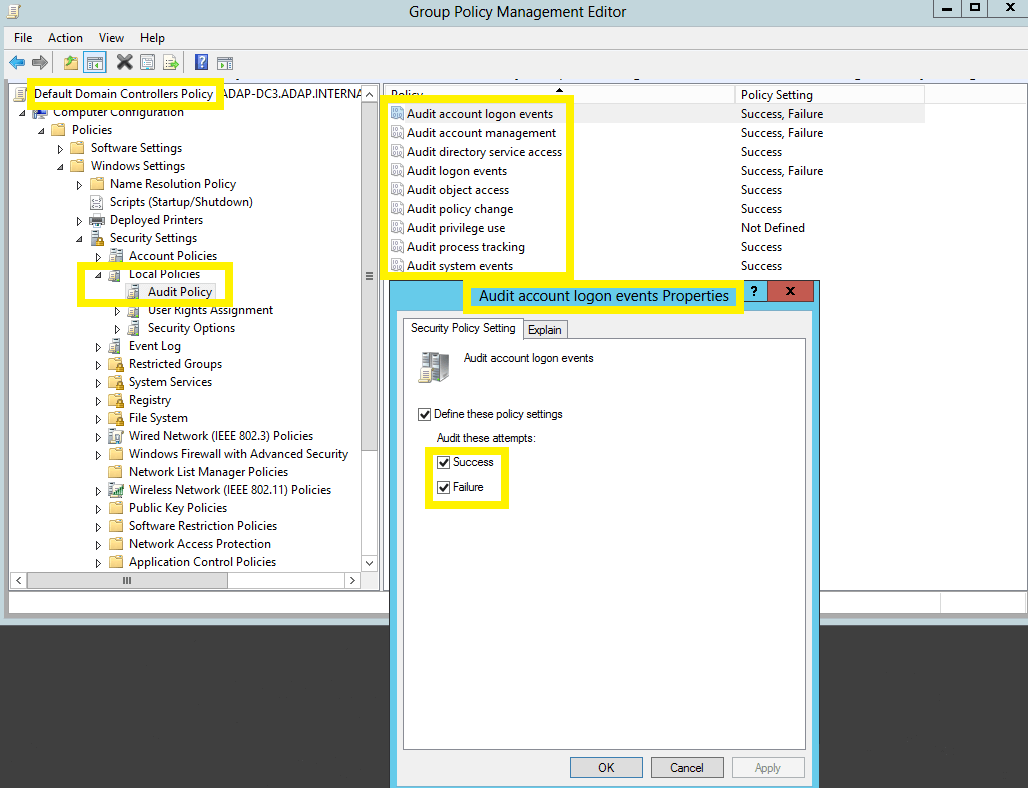
Image showing: Audit account logon events category → Both Success and Failure configured.
Note: To enable auditing of NTLM events, log in to ADAudit Plus' web console → Click on the Support tab > Under Support Info, click on More > Under Configuration, click on Enable/Disable Configuration settings > Enable NTLM Auditing.
Don't see what you're looking for?
-
Visit our community
Post your questions in the forum.
-
Request additional resources
Send us your requirements.
-
Need implementation assistance?
Try OnboardPro

 Click here to expand
Click here to expand


