Vulnerability Management
The Vulnerability assessment process comprises the systematic identification of vulnerabilities, along with a comprehensive analysis of their severity, potential impact, and associated risks. In addition, diligent monitoring is in place to track both publicly disclosed vulnerabilities and zero-day threats, ensuring an up-to-date security posture. Prioritization plays a critical role, with vulnerabilities ranked based on their impact, urgency, and patch availability. A strong emphasis is placed on high risk software, where vulnerabilities within vital assets like databases and web servers are isolated and secured, fortifying the overall cybersecurity of the technical infrastructure.
Vulnerability Management
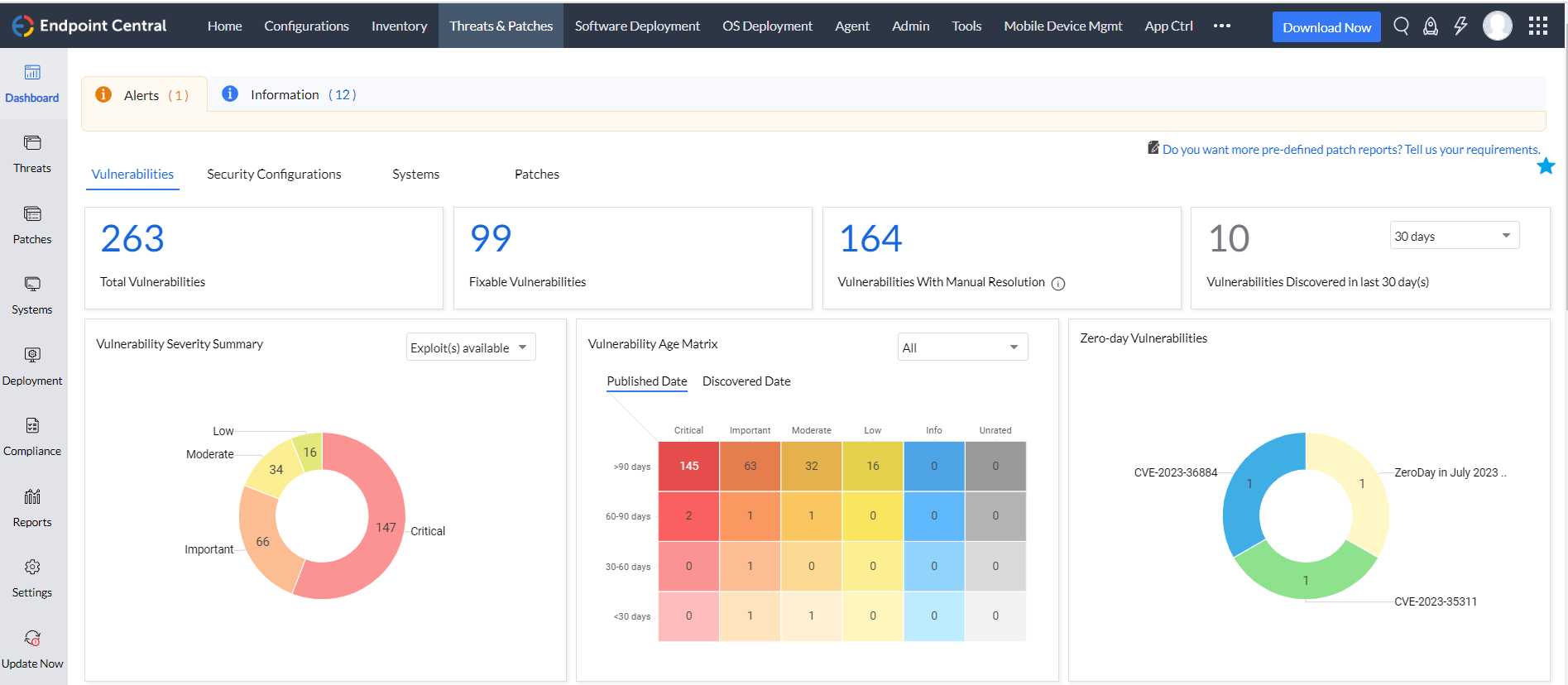
- Zero-day identification and mitigation
Identify zero-days within your software and network infrastructure by leveraging Endpoint Central's real-time threat monitoring and detection capabilities. The unified console also streamlines the mitigation of zero-days by promptly deploying the patches and configurations, once released.
- Immediate response
Implement a rapid-response plan tailored to mitigate zero-day vulnerabilities. This plan includes predefined roles and well-defined procedures to be executed when a confirmed zero-day threat surfaces, allowing for swift and effective countermeasures.
- Workarounds and temporary fixes
Utilize the features of Endpoint Central to develop and implement temporary workarounds and mitigation strategies that reduce the risk of exploitation in the absence of available patches. These measures act as a protective shield, safeguarding critical systems and invaluable data until a permanent solution is accessible.
- Continuous monitoring
Maintain continuous vigilance over the status of zero-day vulnerabilities. Stay informed with real-time updates from vendor announcements and security communities to ensure the enduring security of your systems.
Zero-day mitigation
While patching vulnerabilities is the ultimate goal, there will be times when a fix isn't available right away, like with zero-day vulnerabilities or newly discovered ones. Here's how to fight back in these situations:
- A dedicated view for zero days
Our security team actively searches for new threats online. When they discover zero-day vulnerabilities or publicly disclosed ones, they verify the information and update our central database immediately. This updated data is then synced to your Endpoint Central server.
- Deploy workarounds when permanent fix isn't available yet (mitigation scripts)
Once a zero-day exploit is out in the wild and vendors become aware, they often release temporary workarounds to block the attack while they develop a permanent fix (patch). With Endpoint Central's pre-built mitigation scripts, you can quickly deploy these workarounds to all affected devices. These scripts can harden your systems, adjust registry settings, close vulnerable ports, disable outdated protocols, and more. This helps significantly reduce the risk of attackers exploiting the zero-day vulnerability on your network.
- Get notified when permanent fixes are available
Patches released for vulnerabilities previously identified as zero-days are called zero-day patches. Endpoint Central will notify you through the console's notification bar as soon as a zero-day patch becomes available. You can then use Endpoint Central to remove the temporary workaround you applied earlier and install the patch for a permanent fix.
Security configurations management
Fortify your network by detecting security misconfigurations across the managed endpoints. With a predefined library of security configuration baselines derived from industry standards, this solution swiftly continually monitors and identifies any misconfiguration in the network starting from weaker passwords, firewall audits, user privileges, and more.
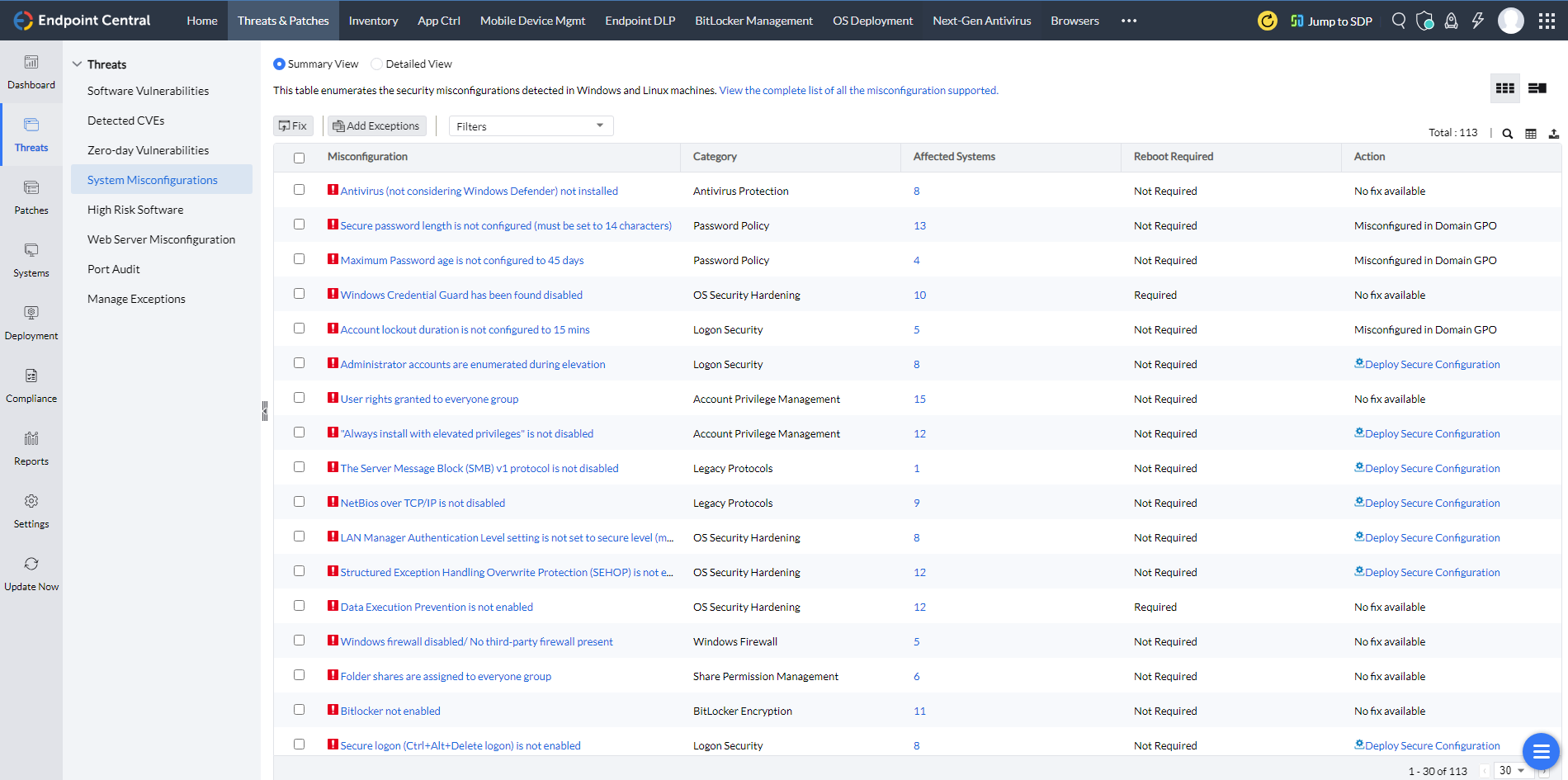
- Comprehensive auditing
Conduct thorough audits of firewalls, antivirus, and BitLocker status to maintain a secure infrastructure.
- Protection against brute-force attacks
Safeguard your network by enforcing robust password policies and secure logon procedures to prevent brute-force attempts.
- Enhanced security settings
Strengthen your systems with advanced memory protection settings and the retirement of legacy protocols, reducing vulnerabilities and enhancing security without disrupting business operations.
Web Server Hardening
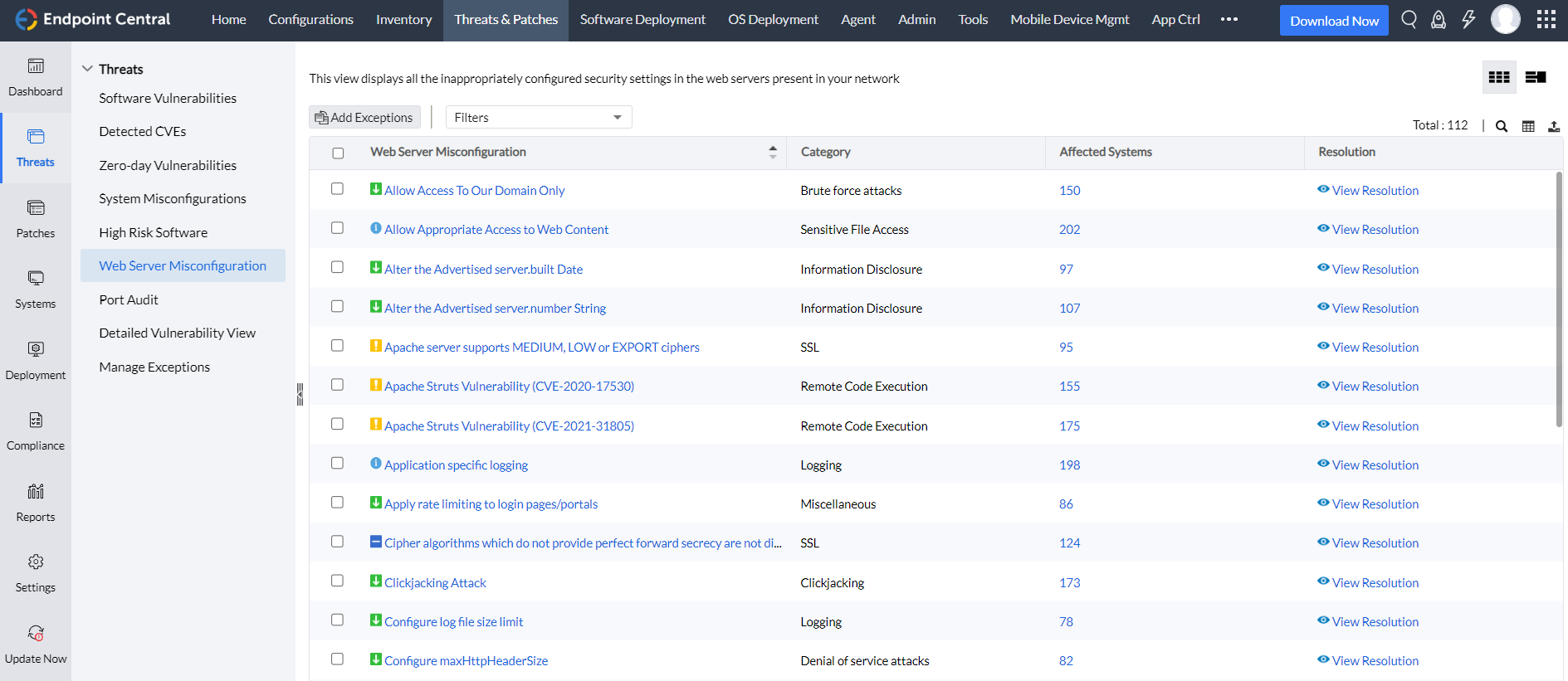
- Proactive configuration monitoring
Benefit from continuous monitoring of your web servers to identify and rectify default and insecure configurations.
- Contextual misconfiguration analysis
Analyze web server misconfigurations with relevant context and receive security recommendations to enhance your server's security posture.
- Secure communication with SSL
Ensure that SSL certificates are correctly configured and HTTPS is enabled, guaranteeing secure and encrypted client-server communication.
- Enhanced Access Control
Verify and enforce restricted permissions on server root directories to prevent unauthorized access and protect your server's integrity.
High-Risk Software Audit
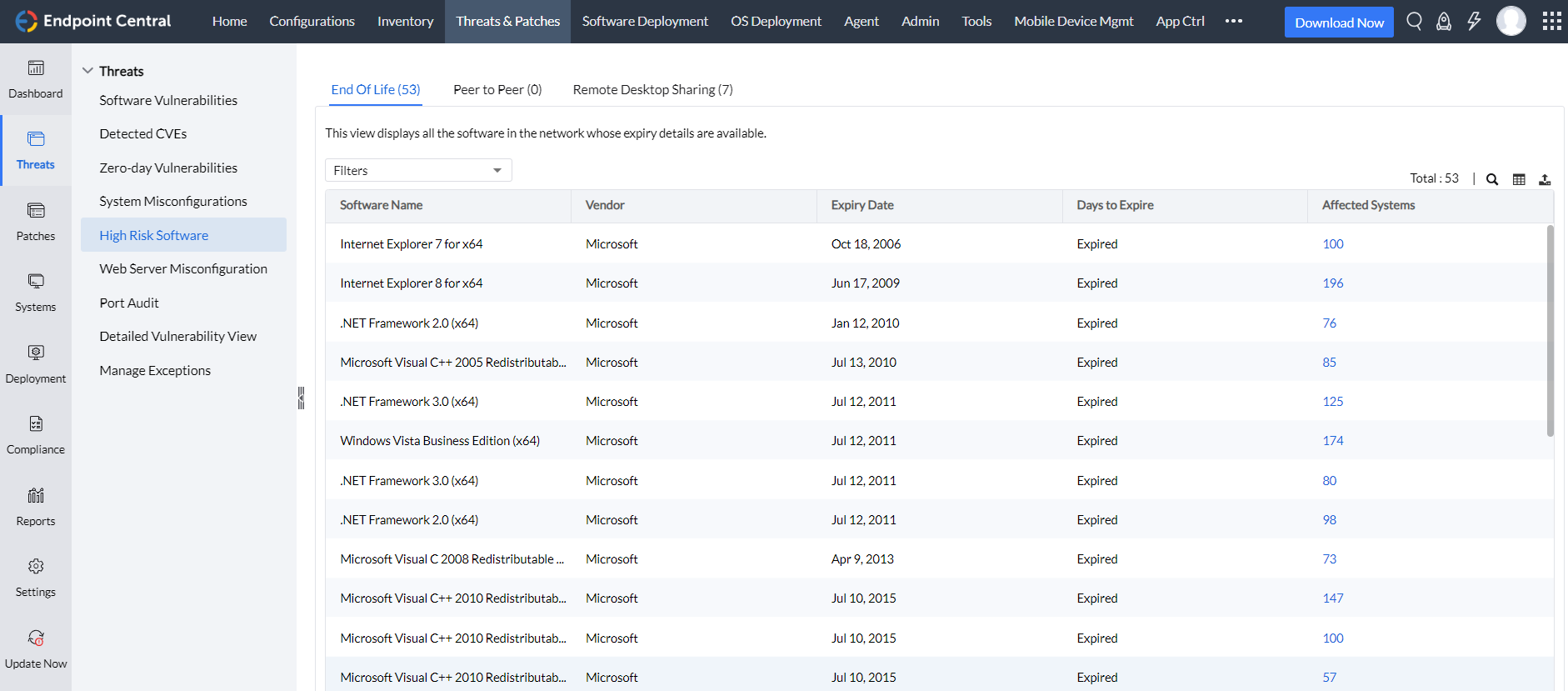
- Legacy software monitoring
Keep a watchful eye on legacy software nearing or already at its end of life, ensuring your systems stay secure and up-to-date.
- Effortless risk mitigation
Access real-time information on unsafe peer-to-peer software and remote sharing tools, and eliminate them with a simple click, bolstering your security instantly.

"The threat and patch management provides exactly what we need, as security is an increasingly significant aspect of our work. A significant requirement of our cybersecurity is the identification of vulnerabilities, and timely patching of software and systems. Endpoint Central provides a comprehensive view of vulnerbilities and patching."
James M,
Review collected by and hosted on G2.