- Home
- Logging Guide
- Enabling firewall logging and monitoring
How to enable firewall logging in Linux
On this page
- What makes firewall logs so important?
- How do I set up firewall logging in Linux?
- The importance of a firewall log analyzer solution to reinforce your firewall management practices
- How EventLog Analyzer helps you stay on top of suspicious network traffic by centralizing all firewall logs and more
A firewall acts as a first line of defense, filtering network traffic to protect systems from unauthorized access and cyberthreats. In Linux, firewall tools like iptables and firewalld are essential for maintaining security because they define rules that allow or deny traffic based on various attributes, such as the source IP, destination port, and protocol.
What makes firewall logs so important?
Firewall logs are crucial in Linux for monitoring network traffic, identifying malicious activities, and verifying firewall rules. They provide insights into attempts to breach security, enabling quick responses to threats. Additionally, analyzing these logs helps you optimize firewall configurations, ensuring only legitimate traffic is allowed and thereby enhancing overall network security.
How do I set up firewall logging in Linux?
You can set up firewall logging in Linux using firewalld and iptables, which are firewall management tools that help you implement and manage firewall rules to ensure you're well-informed of potential threats to your environment.
Here's a guide on how to enable and collect logs using two methods:
Using iptables for log collection
When it comes to Linux systems, iptables, a command-line interface, is used to set up and maintain tables or rules for the netfilter firewall for IPv4 that is included by default in the Linux kernel. When a connection tries to establish itself in the system, iptables looks for a rule in its list to see if the connection should be allowed or denied. If there are no rules, it resorts to the default action. iptables is pre-installed in most of the Linux systems.
iptables uses three different chains—input, forward, and output—to control the traffic coming into the network, rerouted within the network, and going out of the network. Enabling logging in iptables is essential to monitoring the inbound and outbound traffic.
Enable logging
Use the following command to enable logging in iptables:
sudo iptables -A INPUT -j LOG
To enable logging for a specific IP or range, use the command below:
iptables -A INPUT -s 192.168.10.0/24 -j LOG
To log packets, use the command below. This command logs dropped packets with a specific prefix and sets the log level:
sudo iptables -A INPUT -j LOG --log-prefix "IPTables-Dropped: " --log-level 4
To define the level of logs generated by iptables, use -log-level followed by the level number. Refer to the syntax of the command below:
iptables -A INPUT -s 192.168.10.0/24 -j LOG --log-level 4
If you're manually analyzing the logs, it's better to add a prefix in generated logs so that it's easier for you to search the huge number of log files. The command to perform this operation is given below:
iptables -A INPUT -s 192.168.10.0/24 -j LOG --log-prefix '** SUSPECT **'
Alternatively, you can always choose a log management solution, such as ManageEngine EventLog Analyzer, to collect, monitor, analyze, and get actionable insights into firewall logs.
Viewing iptables log s
By default, logs are written to /var/log/messages or /var/log/syslog depending on your distribution. You can view them using the following:
Ubuntu and Debian: tail -f /var/log/kern.logCentOS, RHEL, and Fedora cat /var/log/messages
Enabling firewalld logging for denied packets
Using the configuration file
- Open the firewalld.conf file using the following command:
- Locate the following line:
- Change it to the desired logging level:
- The available logging levels include:
- all: Logs all dropped packets
- unicast: Logs one-to-one communication packets
- broadcast: Logs one-to-many communication packets
- multicast: Logs specific group communications
- Save your changes and exit the editor.
- Reload firewalld to apply the changes using the following command:
sudo nano /etc/firewalld/firewalld.conf
LogDenied=off
LogDenied=<Logging_level>
For example, to log all denied packets:
LogDenied=all
sudo firewall-cmd --reload Using the command-line interface
You can also quickly enable logging using the command-line interface:
sudo firewall-cmd --set-log-denied=<Logging_level>
For example, to set the logging level to broadcast, use the command below:
sudo firewall-cmd --set-log-denied=broadcast
To check the current logging level, use the command below:
sudo firewall-cmd --get-log-denied
Viewing the logged denied packets
To view the logged denied packets, you can use the following command:
journalctl -xe | grep -i rejected
Alternatively, you can check /var/log/firewalld for detailed logs.
By following these methods, you can effectively enable the logging of denied packets in firewalld, enhancing your ability to monitor your Linux system and secure it against unauthorized access.
The importance of a firewall log analyzer solution to reinforce your firewall management practices
As firewalls generate vast amounts of log data, manual analysis becomes impractical and time-consuming.
- A dedicated firewall log analyzer automates this process, transforming raw log data into actionable insights.
- With a firewall log analyzer solution, you can analyze logs in real time and detect suspicious activities promptly. For instance, such a solution can flag abnormal spikes in traffic or unauthorized access attempts, enabling swift responses to mitigate risks.
- A firewall log solution provides reports on successful and failed user logins, helping you correlate events to identify login patterns, which are used as a baseline to unearth threats.
- You can also keep tabs on configuration changes and errors. A firewall log solution provides detailed insights into who has made changes as well as when and where they were done.
- A firewall log analyzer can also facilitate compliance with regulations and standards by maintaining detailed records of network activities. These records are vital for audits and assessments, helping organizations meet legal and industry-specific requirements.
Simplify firewall security auditing with EventLog Analyzer
How EventLog Analyzer helps you stay on top of suspicious network traffic by centralizing all firewall logs and more
EventLog Analyzer is a robust log management and network security tool that is designed to help organizations effectively manage their firewall rules and monitor network activities. It provides comprehensive capabilities for collecting, analyzing, correlating, and archiving logs from various sources, including firewalls, servers, and applications.
EventLog Analyzer is designed to gather logs from endpoints and firewall devices, enabling users to monitor suspicious activities in real time. This proactive approach allows security teams to respond to potential threats before they spiral out of control.
This solution provides reports with deep insights for users to act upon. Some of the insights include:
- Denied connections based on various criteria, such as users, servers, and firewalls, with the solution's intuitive Denied Connections reports.
- All rules, policies, ACLs, and access control entries from firewall devices from providers like Cisco, SonicWall, and Juniper Networks. These details help in identifying active, inactive, and unrestricted rules.
- The ports and protocols that generate a high amount of firewall traffic.
- Rules added, changed, modified, or deleted. This information helps you keep a close eye on individual user activities and flag them if you deem them suspicious (Fig. 1).
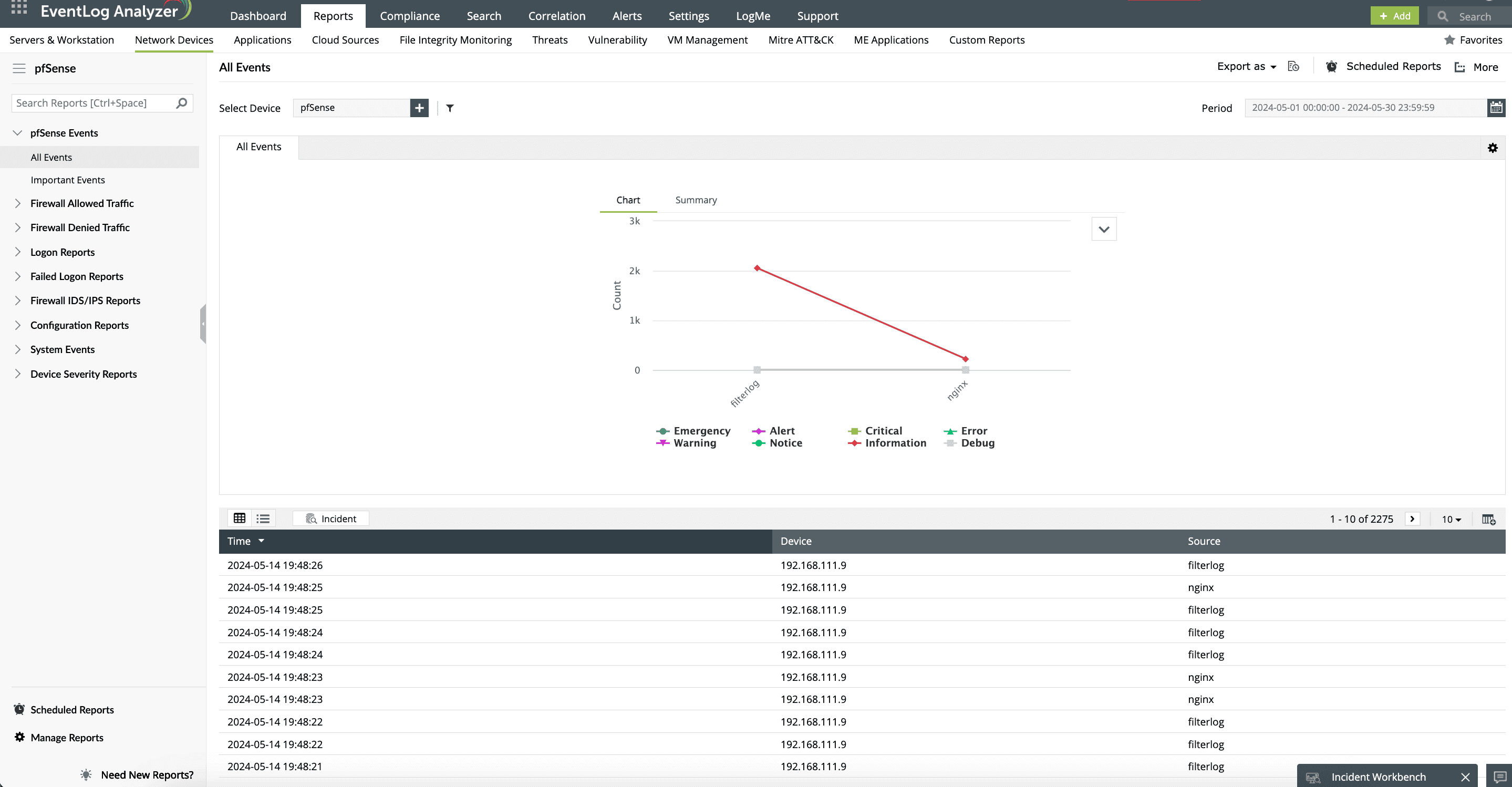
Employ sophisticated correlation rules to connect related events across different logs. This feature empowers you to get the most out of your firewall deployments and identify complex attack patterns, which are otherwise difficult to find when analyzing logs in isolation. You can set up rules for brute-force attacks and data exfiltration attempts, then block the traffic from the identified malicious sources.
Considering the impact of potential security breaches, it is crucial to remain vigilant regarding any suspicious activities within firewall event logs. EventLog Analyzer addresses this need with its alerting system, which is designed to send instant notifications when such activities are detected (Fig. 2)
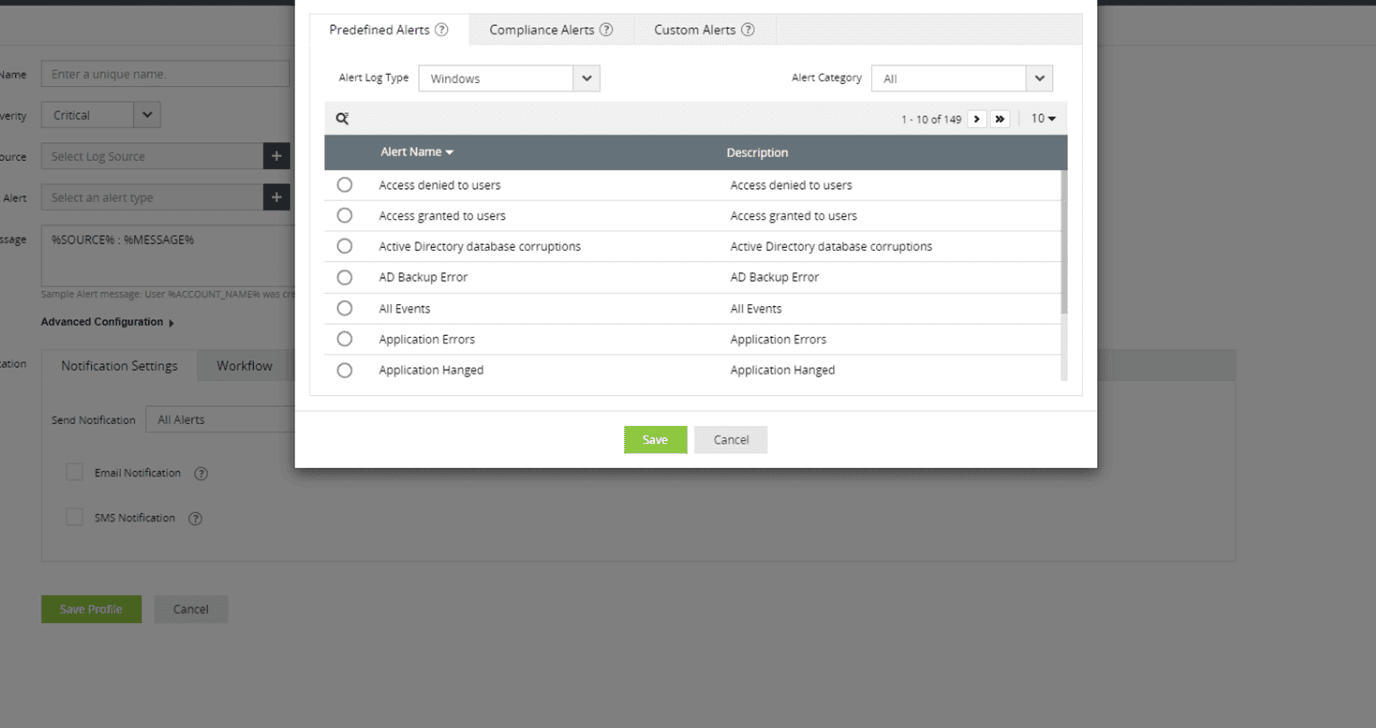
Monitor various metrics, including excessive bandwidth usage, which can indicate potential threats such as denial-of-service attacks. By setting predefined thresholds for bandwidth usage, security administrators can receive alerts in real time, allowing them to investigate and respond promptly to any anomalies.











